2018-05-03 - TRICKBOT FROM MALSPAM, SUBJECT: BILL PAYMENT ALERT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-05-03-Trickbot-infection-traffic.pcap.zip 2.3 MB (2,290,143 bytes)
- 2018-05-03-Trickbot-infection-traffic.pcap (2,447,254 bytes)
- Zip archive of the email: 2018-05-03-Trickbot-malspam-1022-UTC.eml.zip 25 kB (25,468 bytes)
- 2018-05-03-Trickbot-malspam-1022-UTC.eml (75,642 bytes)
- Zip archive of the malware and artifacts: 2018-05-03-malware-from-Trickbot-infection.zip 198 kB (198,424 bytes)
- 2018-05-03-Trickbot-artifact.bat.txt (303 bytes)
- 2018-05-03-Trickbot-binary.exe (221,184 bytes)
- 2018-05-03-Trickbot-malspam-attached-RTF-file.doc (48,472 bytes)
- 2018-05-03-scheduled-task-to-keep-Trickbot-persistent.txt (3,664 bytes)
NOTES:
- My thanks to @dvk01uk for Today's blog post on Trickbot malspam by My Online Security.
- For the past few weeks, Trickbot malspam has been using RTF attachments exploiting CVE-2017-11882.
- These RTF attachments are disguised as Microsoft Word documents, because they use the .doc file extension.
- Information on today's Trickbot binary's configuration is available at this page on Github by @JR0driguezB.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//silverlinktechnologies[.]com/privacy.bin
- hxxp[:]//narwhaldatapartners[.]com/privacy.bin
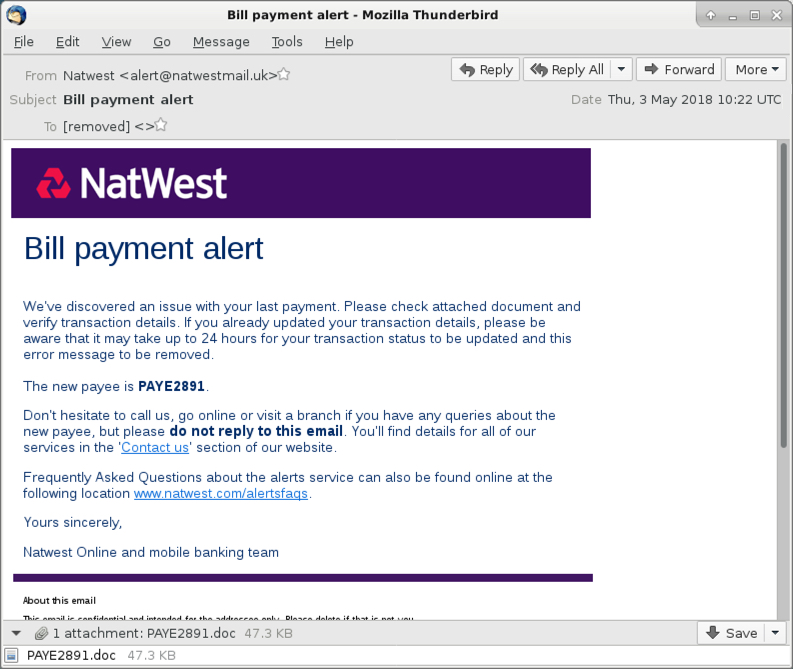
Shown above: Screenshot of the email.
EMAIL HEADERS:
Received: from natwestmail[.]uk (185.236.78[.]101.deltahost-ptr [185.236.78[.]101])by [removed] for [removed]; Thu, 03 May 2018 10:30:28 -0000
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=key; d=natwestmail.uk;
h=Mime-Version:Date:To:Subject:From:Content-Type:Message-ID;
bh=BVbHwBN3bcQQRlwm+gJW43kUGLI=;
b=tO2xlwQEJa4sHJGvyXQZQHfsHZRC/ZjdW6YWGCbENAF77clrh/nggHFvGVDHqTb+Issrrjg0nN3X
0d8dpLn4mmtHrw2Z6Slp2e97V9Yb29/BPHNJPliBT58De4Vp3EhGdQJHCbq65vhmqrllXuZ69KSr
3pzL9c8rnk4w1gGJ3nk=
Received: by natwestmail[.]uk id htbi65oct4o3 for [removed]; Thu, 3 May 2018 06:22:02 -0400 (envelope-from lt;alert-[recipient's email address]@natwestmail[.]uk>)
Mime-Version: 1.0
Date: Thu, 3 May 2018 06:22:02 -0400
To: [removed]
Subject: Bill payment alert
From: "Natwest" <alert@natwestmail[.]uk>
Content-Type: multipart/mixed;
boundary=07fa11edf9f656d391c58e21c9c14d93
Message-ID: <0.0.1.0.1D3E2C89411442C.1D2F1DF4@natwestmail[.]uk>

Shown above: RTF document attached to the malspam.
TRAFFIC
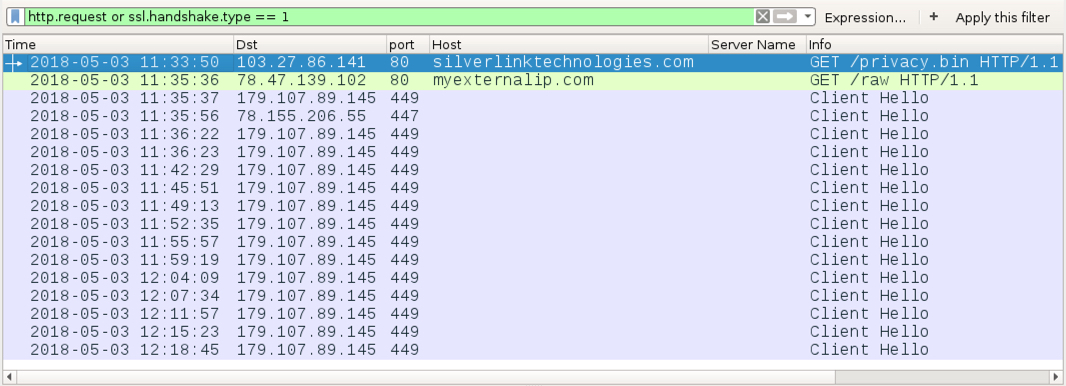
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 103.27.86[.]141 port 80 - silverlinktechnologies[.]com - GET /privacy.bin
- port 80 - myexternalip[.]com - GET /raw (IP address check by the infected host)
- 179.107.89[.]145 port 449 - SSL/TLS traffic caused by Trickbot
- 78.155.206[.]55 port 447 - SSL/TLS traffic caused by Trickbot
FILE HASHES
RTF ATTACHMENT FROM THE MALSPAM:
- SHA256 hash: 76338d11807ec055ff238c0dbfcd9a7d68d8297713a90ee87b07fcfc248ebb53
File size: 48,472 bytes
File name: PAYE2891.doc
File description: RTF attachment with CVE-2017-11882 exploit for Microsoft Office
TRICKBOT BINARY:
- SHA256 hash: bb2e040bb2652fab5eeb175daf2dc69ce2661087e21cebd166bdcc501b2f0986
File size: 221,184 bytes
File location: C:\Users\[username]\AppData\Roaming\mstools\cataloghal.exe
File description: Trickbot malware (Windows executable file)
Click here to return to the main page.
