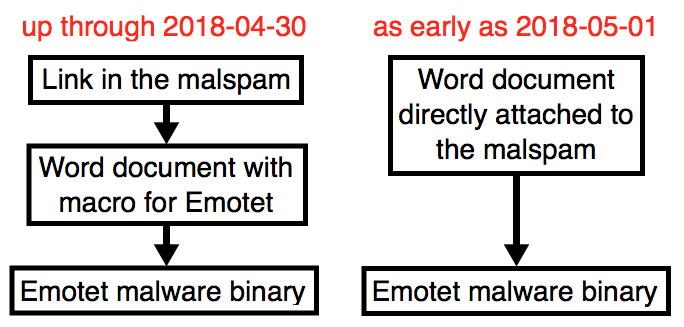
2018-05-04 - MALSPAM PUSHING EMOTET MOVED FROM LINKS TO ATTACHMENTS THIS WEEK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-05-04-Emotet-infection-traffic.pcap.zip 1.03 MB (1,029,174 bytes)
- 2018-05-04-Emotet-infection-traffic.pcap (1,148,850 bytes)
- Zip archive of the emails: 2018-05-04-two-examples-of-Emotet-malspam.zip 170 kB (170,104 bytes)
- 2018-05-03-Emotet-malspam-1537-UTC.eml (178,234 bytes)
- 2018-05-03-Emotet-malspam-1627-UTC.eml (178,116 bytes)
- Zip archive of the malware: 2018-05-04-malware-from-Emotet-infection.zip 175 kB (174,688 bytes)
- 2018-05-03-attached-Word-doc-with-macro-for-Emotet.doc (129,536 bytes)
- 2018-05-04-downloaded-Emotet-binary.exe (142,848 bytes)
NOTES:
- I hadn't found any new Emotet since Monday 2018-04-30, but @mesa_matt told me this campaign was still active.
- After searching around, I found two examples from Thursday 2018-05-03 using attachments instead links to the Word documents.
- Two email examples I found showed ACH-related subject lines, but I saw other examples with various subject lines common to Emotet malspam.
- Unfortunately, I couldn't find emails for any of those other examples.
- Otherwise, this seems like more of the same, execpt it's extremely limited in distribution compared to previous weeks.
- Examples of Emotet malspam from last week (ones with links instead of attachments) are in my data dumps posted on 2018-04-25, 2018-04-26, and 2018-04-27.
Shown above: Flow chart for recent Emotet malspam infections.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//alian[.]de/4wBYki/
- hxxp[:]//againstperfection[.]net/6kWq0/
- hxxp[:]//globalreachadvertising[.]com/zfFgSQ/ &bnsp; (taken off line by the time I checked)
- hxxp[:]//www.fanoff[.]com/ZVljVr/
- hxxp[:]//thurtell[.]com/TCyk/
- hxxp[:]//72.67.198[.]45/whoami.php
- hxxp[:]//216.110.246[.]70/whoami.php
EMAILS
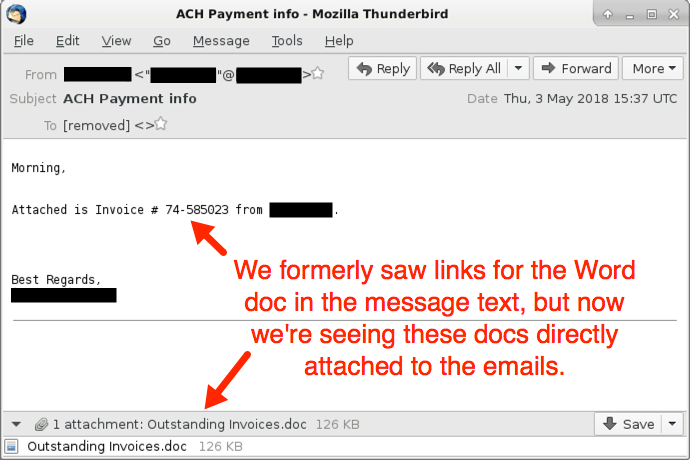
Shown above: Screenshot from one of the emails.
EMAIL HEADERS, EXAMPLE 1 OF 2:
Received: from 10.0.0[.]22 (60.247.97[.]180) by [removed] for [removed];
Thu, 3 May 2018 11:37:53 -0400
Date: Thu, 3 May 2018 23:37:53 +0800
From: "[removed]" <[removed]@[removed]>
To: [removed]
Message-ID: <134428643353.201853153753@[recipient's email domain]>
Subject: ACH Payment info
Attachment name: Outstanding Invoices.doc
EMAIL HEADERS, EXAMPLE 2 OF 2:
Received: from 10.0.0[.]52 ([200.94.97[.]237]) by [removed] for [removed];
Thu, 03 May 2018 08:27:31 -0700
Date: Thu, 03 May 2018 10:27:30 -0600
From: "[removed]" <[removed]@[removed]>
To: [removed]
Message-ID: <16037604816.201853152730@[recipient's email domain]>
Subject: ACH Payment Advice
Attachment name: Scan.doc
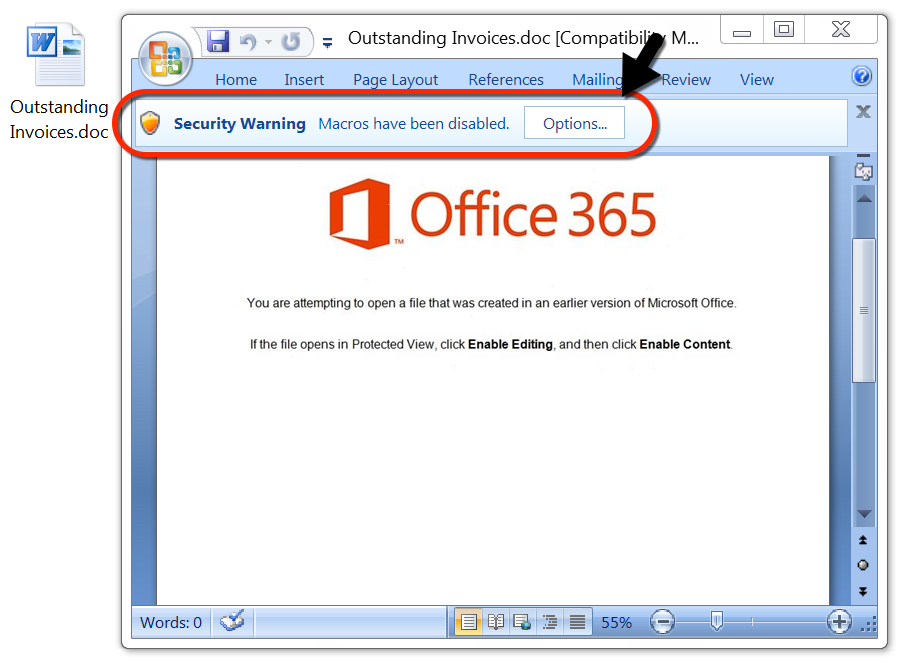
Shown above: Malicious Word document attached to one of the emails.
TRAFFIC
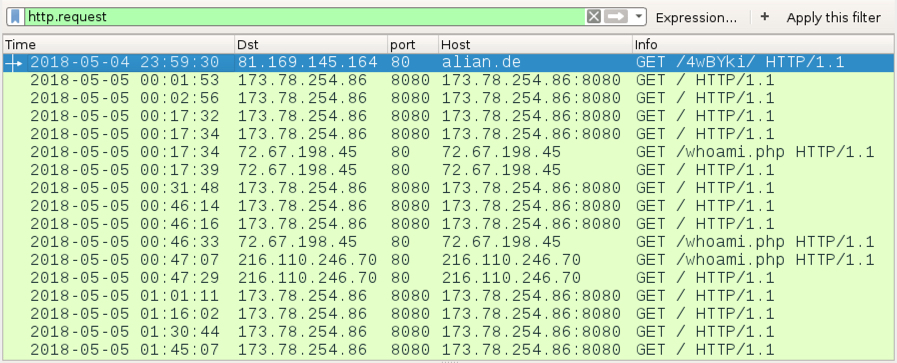
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 81.169.145[.]164 port 80 - alian[.]de - GET /4wBYki/
- 173.11.129[.]38 - SYN packets with RST from server
- 75.128.208[.]218 port 80 - SYN packets with RST from server
- 208.102.59[.]69 port 80 - SYN packets with RST from server
- 146.88.218[.]179 port 443 - SYN packets with RST from server
- 66.42.182[.]18 port 443 - SYN packets with RST from server
- 156.212.247[.]178 port 80 - SYN packets with RST from server
- 104.157.254[.]106 port 8080 - SYN packets with RST from server
- 69.41.8[.]88 port 8080 - SYN packets with RST from server
- 173.78.254[.]86 port 8080 - 173.78.254[.]86:8080 - GET /
- 72.67.198[.]45 port 80 - 72.67.198[.]45 - GET /whoami.php
- 72.67.198[.]45 port 80 - 72.67.198[.]45 - GET /
- 216.110.246[.]70 port 80 - 216.110.246[.]70 - GET /whoami.php
- 216.110.246[.]70 port 80 - 216.110.246[.]70 - GET /
FILE HASHES
MALWARE FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: b26fa7e3f85d5bd8ccca12d893dea59e60bca6bbdf035a2cc516c5da51d00d9a
File size: 129,536 bytes
File name: Scan.doc, Outstanding Invoices.doc, or [any random name].doc
File description: Word document with macro to download and install Emotet
- SHA256 hash: 9982f6f51b44d7651ef644cb181b979deed85933967d5cc6b55fb3e316b03836
File size: 142,848 bytes
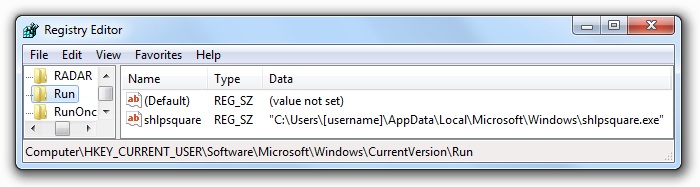
File location: C:\Users\[username]\AppData\Local\Temp\Microsoft\Windows\[random name].exe
File description: Emotet malware binary
Shown above: Emotet malware persistent on my infected Windows host.
Click here to return to the main page.