2018-05-08 - FAKE BRIGHT!TAX EMAILS DISTRIBUTE XORIST RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the emails: 2018-05-08-fake-Brighttax-malspam-2-examples.zip 14.0 kB (14,012 bytes)
- 2018-05-08-fake-Brighttax-malspam-1144-UTC.eml (21,303 bytes)
- 2018-05-08-fake-Brighttax-malspam-1206-UTC.eml (21,301 bytes)
- 2018-05-08-Xorist-ransomware-infection-from-fake-Brighttax-malspam.pcap 17.9 kB (17,931 bytes)
- 2018-05-08-Brighttax-malspam-attachment-Xorist-ransomware.js.txt (14,815 bytes)
- 2018-05-08-Xorist-ransomware-HOW_TO_DECRYPT_FILES.txt (984 bytes)
- 2018-05-08-Xorsit-ransomware-message-popup.exe (15,360 bytes)
NOTES:
- I originally had the wrong name for this ransomware. It's Xorist (not Scrypt) ransomware. Thanks to @malwrhunterteam for the heads-up on that.
- Post-infection traffic returned an executable that merely displayed a popup window with some ransom payment instructions.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest any URL starting with:
- hxxp[:]//rrglobaltrade[.]com/wp-content/plugins/ubh/
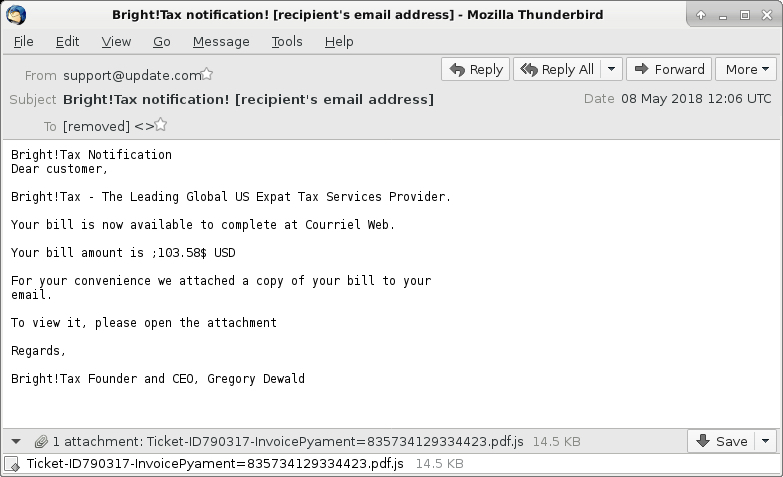
Shown above: Screenshot from one of the emails.
EMAIL HEADER EXAMPLE:
Received: from update[.]com ([117.7.239[.]177]) by [removed] for [removed];
Tue, 08 May 2018 12:06:42 +0000 (UTC)
From: <support@update[.]com>
To: [removed]
Subject: Bright!Tax notification! [recipient's email address]
Date: 08 May 2018 19:06:40 +0700
Message-ID: <20180508190640.74389329CB2C65F0@update[.]com>
MIME-Version: 1.0
Shown above: File attachment from one of the emails.
TRAFFIC
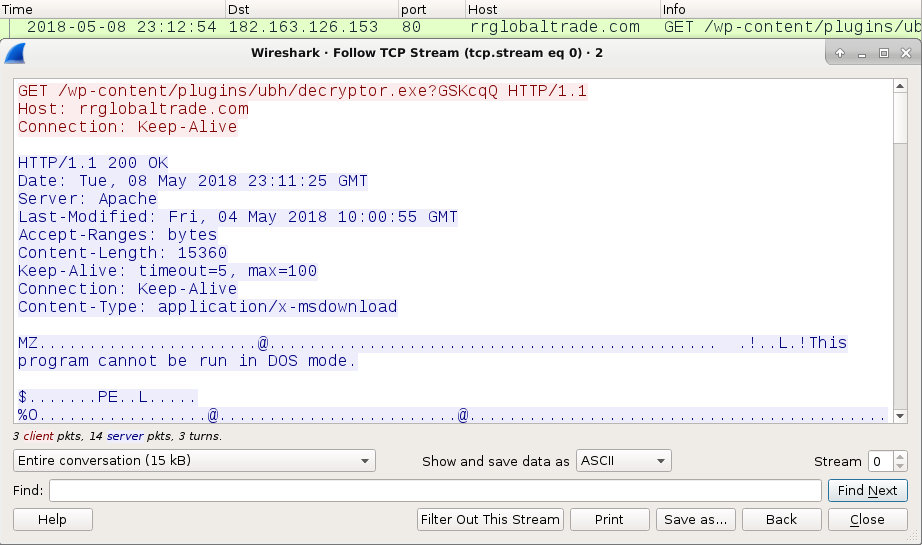
Shown above: Infection traffic filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 182.163.126.153 port 80 - rrglobaltrade[.]com - GET /wp-content/plugins/ubh/decryptor.exe?GSKcqQ
EMAIL FROM THE DECRYPTION INSTRUCTIONS:
- Email_Decryptor_Payment@scryptmail[.]com
Decryption instructions file name:
- HOW TO DECRYPT FILES.txt
Decryption instructions:
All your important files were BLOCKED on this computer.
Encrtyption was produced using unique KEY generated for this computer.
To decrypted files, you need to otbtain private key.
The single copy of the private key, with will allow you to decrypt the files, is locate on a secret server on the internet;
The server will destroy the key within 24 hours after encryption completed.
REMEMBER YOU HAVE ONLY 24 HOURS TO PAY EVERITHING IS AUTOMATICALLY!
To retrieve the private key, you need to pay 700-EURO
PLEASE BE REZONABLE PAYMENT IS LITTLE ONLY 700 EURO
WE ACCEPT ONLY PAYMENT TO BITCOIN!
Bitcoins have to be sent to this address: 3J1MD7EAzdaYeWBDA71t7NShkC64W4a41T
After you've sent the payment send us an email to : Email_Decryptor_Payment@scryptmail[.]com with subject : ERROR-ID-6310700
If you are not familiar with bitcoin you can buy it from here :
SITE : www.localbitcoin[.]com
After we confirm the payment , we send the private key so you can decrypt your system.
Encrypted files all have the following appended to their file names:
....PAY_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_PERMANENTLY_DELETED_PLEASE_BE_REZONABLE_you_have_only_1_single_chance_to_make_the_payment
FILE HASHES
EMAIL ATTACHMENT (XORIST RANSOMWARE):
- SHA256 hash: f769b9f3bd45556e5e1dfc687888ae0ebfae6b63340699a3e047b69350a34ce2
File size: 14,815 bytes
File name: Ticket-ID790317-InvoicePyament=835734129334423.pdf.js
EXECUTABLE SEEN AFTER POST-INFECTION TRAFFIC:
- SHA256 hash: 00133805d692da064e8e47b1d06298998764c5284606bbcd79ef753ca68cac41
File size: 15,360 bytes
File description: Random name somewhere in the user's AppData directory tree
IMAGES FROM AN INFECTION
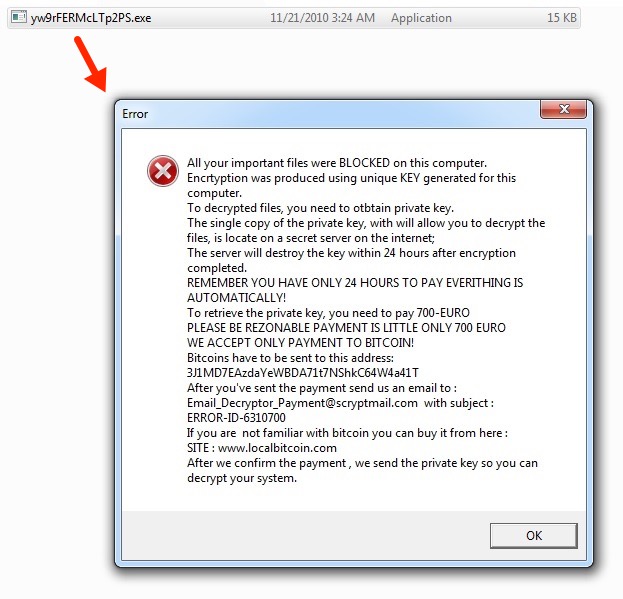
Shown above: Windows executable for the decryption instructions.
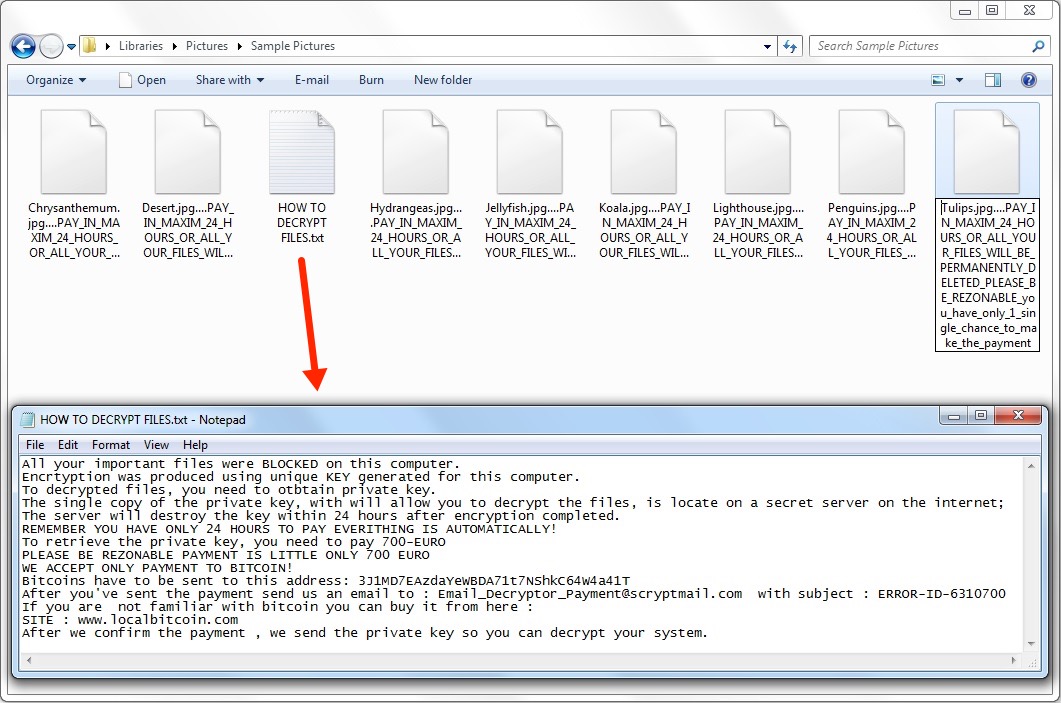
Shown above: Partial screenshot from an infected Windows host.
Click here to return to the main page.
