2018-05-08 - GRANDSOFT EK LEADS TO QUANTLOADER AND URSNIF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2018-05-08-Grandsoft-EK-leads-to-QuantLoader-and-Ursnif.pcap.zip 6.99 MB (6,987,437 bytes)
- 2018-05-08-Grandsoft-EK-leads-to-QuantLoader-and-Ursnif.pcap 7.73 MB (7,725,979 bytes)
- 2018-05-08-Grandsoft-EK-landing-page.txt (530 bytes)
- 2018-05-08-Grandsoft-EK-second-page.txt (22,067 bytes)
- 2018-05-08-Grandsoft-EK.hta-file.txt (5,069 bytes)
- 2018-05-08-QuantLoader.exe (264,832 bytes)
- 2018-05-08-Ursnif.exe (431,250 bytes)
NOTES:
- I was informed of a malvertising chain that led to Grandsoft EK, and the final URL of that chain is included in today's pcap.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- whitepages[.]bid
- bggtbm.saliva.gbi-dminstructormbw[.]xyz
- lagginfo[.]com
- hxxp[:]//viscircuskoning[.]nl/v2/images/header/5.exe
- hxxp[:]//dcsautomation[.]net/wp-content/themes/rocco/images/xx1.jpg
- hxxp[:]//brotherstradingbd[.]com/wp-content/themes/storefront/assets/images/customizer/controls/xx1.jpg
TRAFFIC
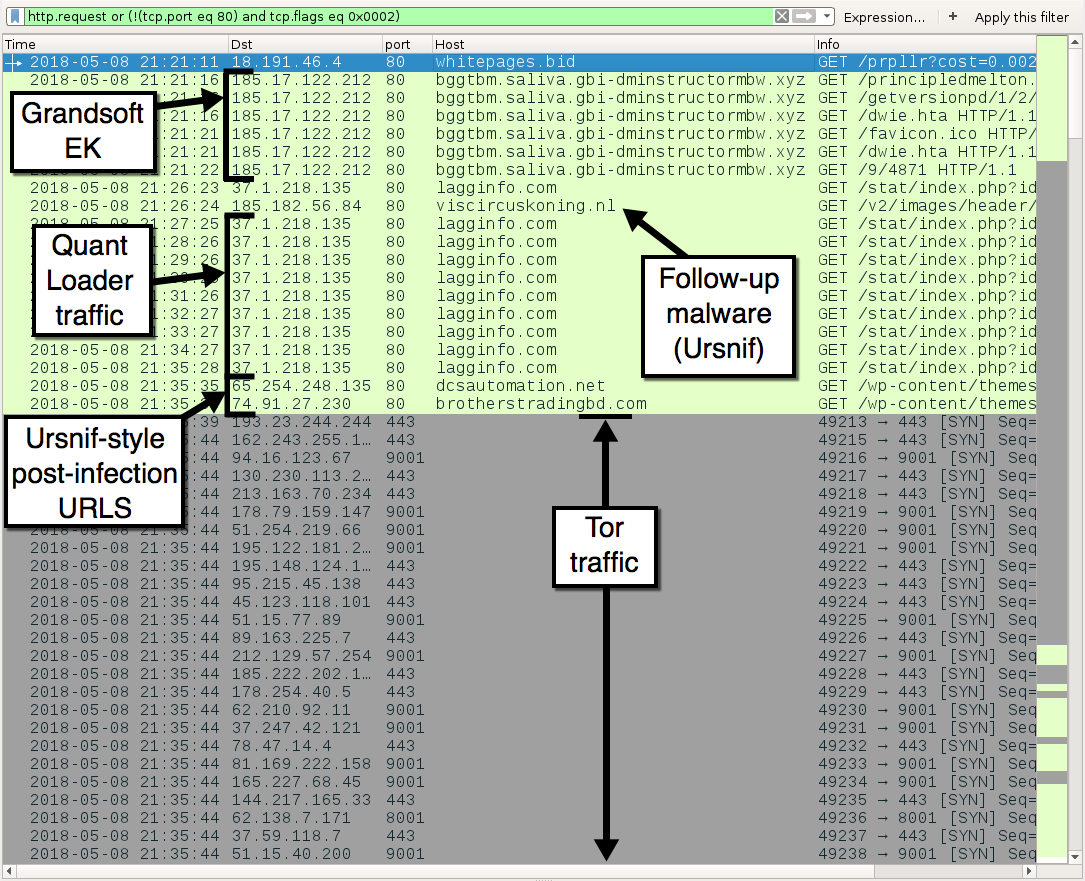
Shown above: Infection traffic filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 18.191.46[.]4 port 80 - whitepages[.]bid - malvertizing URL that led to Grandsoft EK
- 185.17.122[.]212 port 80 - bggtbm.saliva.gbi-dminstructormbw[.]xyz - Grandsoft EK
- 37.1.218[.]135 port 80 - lagginfo[.]com - Quantloader callback traffic
- 185.182.56[.]84 port 80 - viscircuskoning[.]nl - GET /v2/images/header/5.exe (returned Ursnif binary)
- 65.254.248[.]135 port 80 - dcsautomation[.]net - GET /wp-content/themes/rocco/images/xx1.jpg (Ursnif-style post-infection URL)
- 74.91.27[.]230 port 80 - brotherstradingbd[.]com - GET /wp-content/themes/storefront/assets/images/customizer/controls/xx1.jpg (Ursnif-style post-infection URL)
- Various IP addresses over various TCP ports - Tor traffic
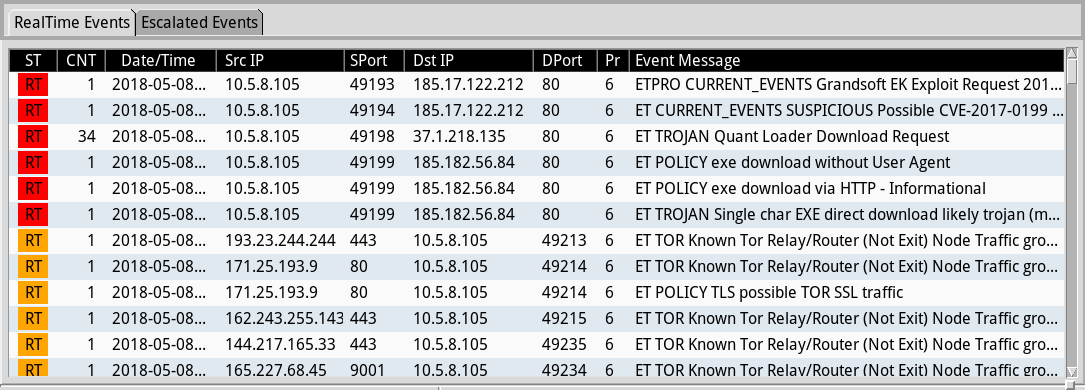
Shown above: Some alerts from Sguil in Security Onion using Suricata with the EmergingThreats Pro (ETPRO) ruleset.
FILE HASHES
GRANDSOFT EK PAYLOAD - QUANTLOADER (VERSION 1.75):
- SHA256 hash: 9ed95f9e2600aafbd73366f4d862dd8a9cda89b5262ad7c1c89d9331b57ac0fb
File size: 264,832 bytes
File location: C:\Users\[username]\AppData\Roaming\70685129\csrss.exe
URSNIF (OR AN URSNIF VARIANT) RETRIEVED BY QUANTLOADER:
- SHA256 hash: 300b1cf25e20f54451081534b86a850e4bedf236cd0f0ec8785af3359de5c0c0
File size: 431,250 bytes
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Dmdlaext\api-kend.exe
Click here to return to the main page.
