2018-05-27 - SLYIP CAMPAIGN USES GRANDSOFT EK TO PUSH URSNIF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive with pcaps of the traffic: 2018-05-27-SlyIP-Grandsoft-EK-pcaps.zip 24.9 MB (24,862,201 bytes)
- 2018-05-27-1st-run-SlyIP-Grandsoft-EK-with-post-infection-traffic.pcap (10,428,474 bytes)
- 2018-05-27-2nd-run-SlyIP-Grandsoft-EK-with-post-infection-traffic.pcap (16,254,665 bytes)
- Zip archive of the malware and artifacts: 2018-05-27-SlyIP-Grandsoft-EK-malware-and-artifacts.zip 830 kB (830,461 bytes)
- 2018-05-27-1st-run-SlyIP-Grandsoft-EK-payload-Ursnif.exe (558,592 bytes)
- 2018-05-27-2nd-run-SlyIP-Grandsoft-EK-payload-Ursnif.exe (522,240 bytes)
- 2018-05-27-both-runs-Grandsoft-EK-CVE-2016-0189.txt (25,393 bytes)
- 2018-05-27-both-runs-Grandsoft-EK-dwie.hta.txt (2,031 bytes)
- 2018-05-27-both-runs-Grandsoft-EK-fake-DLL-from-VBscript-in-CVE-2016-0189.dll (4,429 bytes)
- 2018-05-27-both-runs-Grandsoft-EK-landing-page.txt (530 bytes)
NOTES:
- Since 2018-05-11, @nao_sec has been documenting an exploit kit (EK) campaign called "SlyIP" at traffic.moe.
- It's called the SlyIP campaign, because the URL redirecting to the EK has a domain ending with "slyip[.]com" or "slyip[.]net".
- Original reference in this tweet, and more examples are available at traffic.moe.
- These SlyIP URLs have led to Grandsoft EK or Rig EK, and this campaign has been documented pushing Ursnif malware or Gandcrab ransomware.
- Today's SlyIP example has Grandsoft EK pushing Ursnif.
- I recorded two infection runs to show the minor differences in Grandsoft EK domains (from .xyz to .tk) and the post-infection traffic.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- fasthosting.slyip[.]com
- fasthosting.slyip[.]net
- vzdnprediction.project-x-adminko-test[.]tk
- owkhdharshness.ebxseoccupationeclr[.]xyz
- hxxp[:]//www.dalmo[.]cz/files/AZE.bin
- hxxp[:]//5.64.157[.]228/a3.sign
- u55.evama[.]at
- work.a-poster[.]info
TRAFFIC
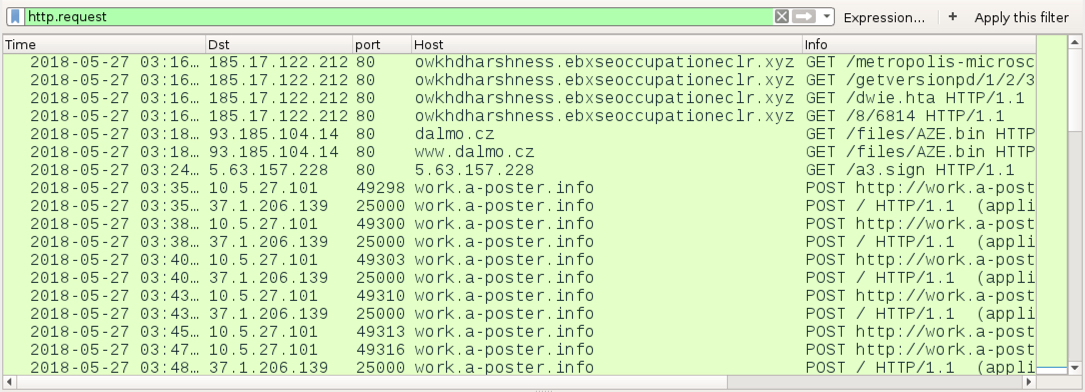
Shown above: Some of the HTTP requests from an infection filtered in Wireshark.
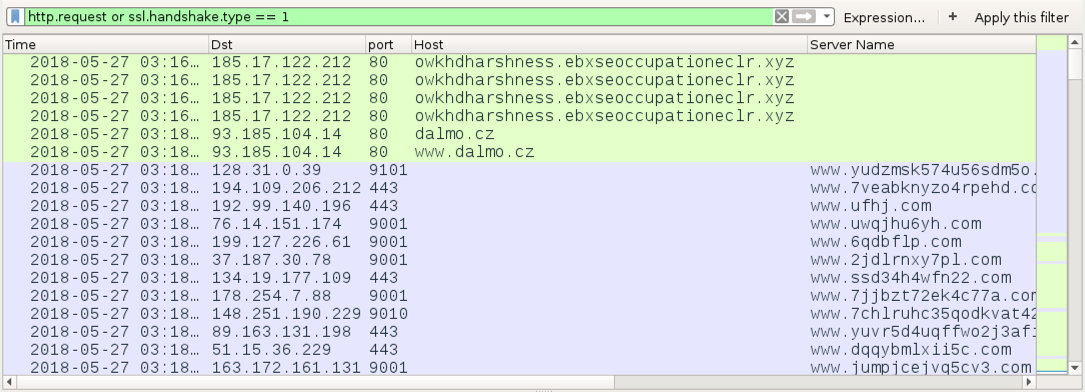
Shown above: Some of the Tor traffic with the HTTP requests from an infection filtered in Wireshark.
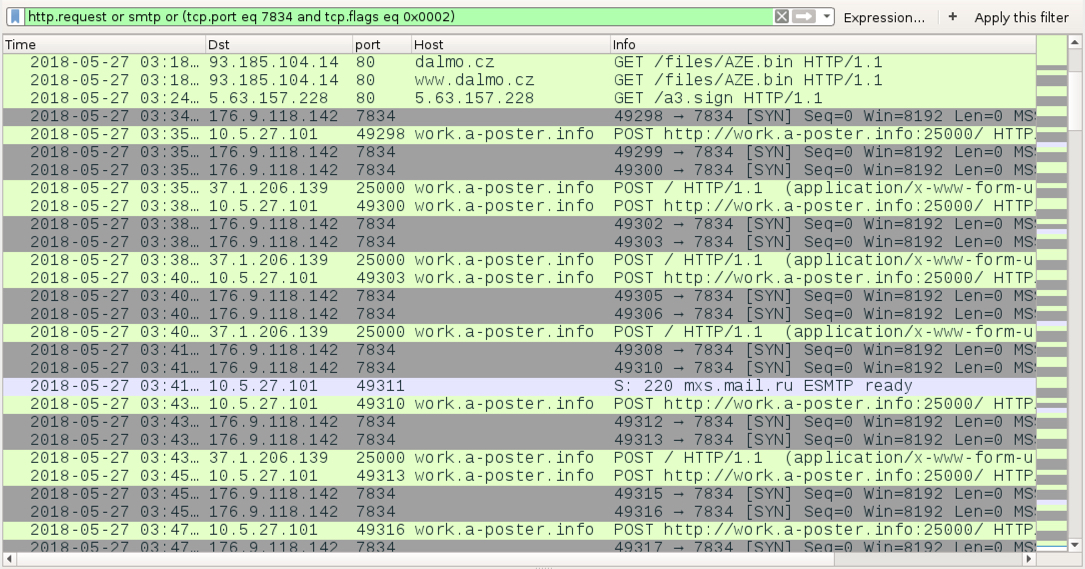
Shown above: More filtering in Wireshark to for a better idea of the SMTP traffic and HTTP traffic on non-standard ports.
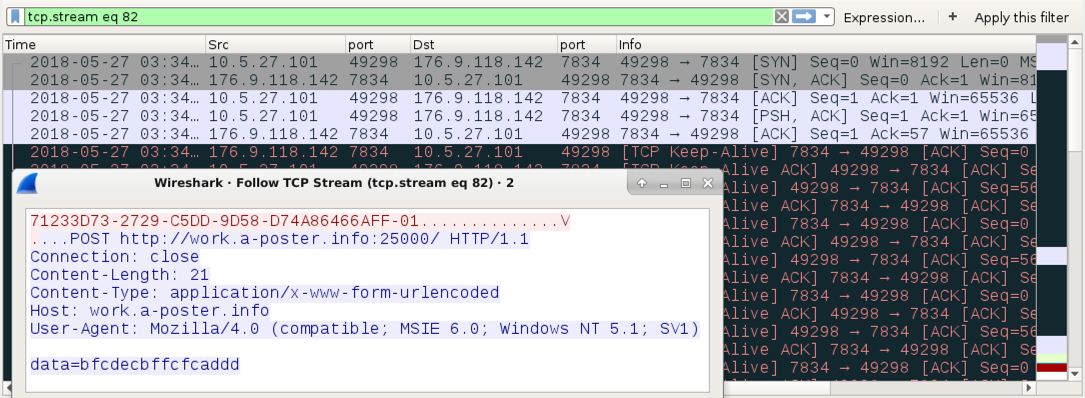
Shown above: One of the HTTP POST requests related to work.a-poster.info.
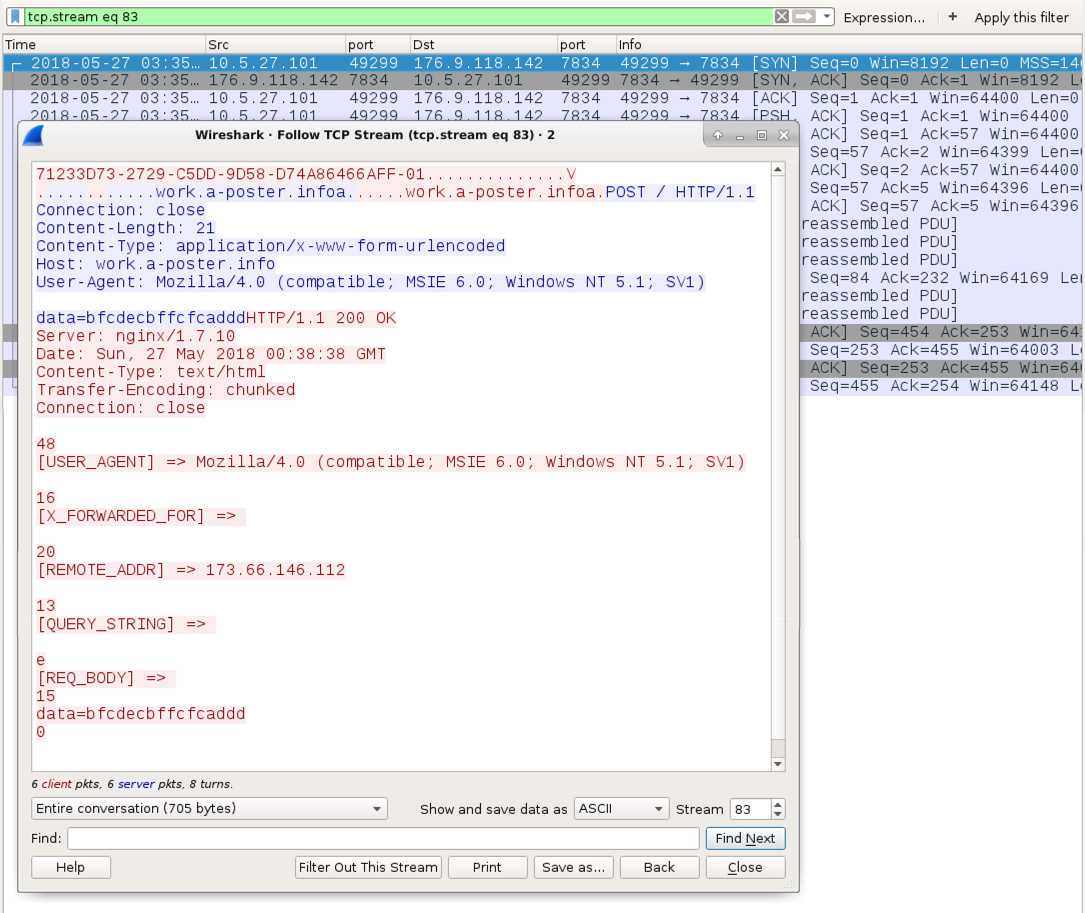
Shown above: Another one of the HTTP POST requests related to work.a-poster.info.
GRANDSOFT EK TRAFFIC:
- 185.17.122[.]212 port 80 - owkhdharshness.ebxseoccupationeclr[.]xyz - Grandsoft EK (1st run)
- 185.17.122[.]212 port 80 - vzdnprediction.project-x-adminko-test[.]tk - Grandsoft EK (2nd run)
POST-INFECTION TRAFFIC CAUSED BY THE URSNIF MALWARE:
- 185.17.122[.]212 port 80 - owkhdharshness.ebxseoccupationeclr[.]xyz - Grandsoft EK (1st run)
- 185.17.122[.]212 port 80 - vzdnprediction.project-x-adminko-test[.]tk - Grandsoft EK (2nd run)
- 93.185.104[.]14 port 80 - dalmo[.]cz - GET /files/AZE.bin (legitimate domain, bad URL)
- 93.185.104[.]14 port 80 - www.dalmo[.]cz - GET /files/AZE.bin (legitimate domain, bad URL)
- 5.63.157[.]228 port 80 - 5.63.157[.]228 - GET /a3.sign (from 1st run post-infection traffic)
- 45.113.71[.]16 port 80 - u55.evama[.]at - GET wpapi/[long string of characters] (from 2nd run post-infection traffic)
- 176.9.118[.]142 port 7834 - [from my infected Windows host] - POST hxxp[:]//work.a-poster.info:25000/
- 37.1.206[.]139 port 25000 - work.a-poster[.]info - POST /
- 81.19.77[.]166 port 465 - smtp.rambler[.]ru - Encrypted SSL/TLS traffic, not inherently malicious
- 94.100.180[.]104 port 25 - mxs.mail[.]ru - SMTP traffic, not inherently malicious
FILE HASHES
GRANDSOFT EK LANDING PAGE:
- SHA256 hash: 01bc0fb55ee9a0fbf4f40960cbac630fc24635e9879c46c2ba32262570065152
File size: 530 bytes
WEB PAGE WITH CVE-2016-0189 VBSCRIPT EXPLOIT FROM GRANDSOFT EK:
- SHA256 hash: 679d55e794db279b6d61a8aa8dec4faf8bc75a1a560d9644e1cbbb07516441f9
File size: 25,393 bytes
FAKE DLL FROM CVE-2016-0189 VBSCRIPT EXPLOIT:
- SHA256 hash: eaaec1a4c62b2124f4109da5e630f08c114ff75637b06db8970935da9fbfb860
File size: 4,429 bytes
DWIE.HTA FILE SENT BY GRANDSOFT EK:
- SHA256 hash: c19a5be261a51ef22c76eea90242128904a66801557d313df012417c202baa62
File size: 2,031 bytes
SLYIP GRANDSOFT EK PAYLOAD (URSNIF) - 1ST RUN:
- SHA256 hash: 52dc47e8c5a0028bbf9ea24fdadb9bf343a74ab4ee4d306282292ed36ca2d803
File size: 558,592 bytes
SLYIP GRANDSOFT EK PAYLOAD (URSNIF) - 2ND RUN:
- SHA256 hash: c00e775af8ec1fb973bbfed3d68753b13f2d3e0254daa9454ed27a075c0203a9
File size: 522,240 bytes
Click here to return to the main page.
