2018-05-31 - END OF MONTH ROUND-UP: EMOTET MALSPAM AND INFECTION TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the spreadsheet tracker: 2018-05-31-Emotet-malspam-tracker.csv.zip 1.4 kB (1,362 bytes)
- 2018-05-31-Emotet-malspam-tracker.csv (2,411 bytes)
- Zip archive of 12 email examples: 2018-05-31-Emotet-malspam-12-examples.zip 382.6 kB (382,590 bytes)
- 2018-05-28-Emotet-malspam-0655-UTC.eml (144,069 bytes)
- 2018-05-28-Emotet-malspam-0725-UTC.eml (176,276 bytes)
- 2018-05-28-Emotet-malspam-1311-UTC.eml (882 bytes)
- 2018-05-28-Emotet-malspam-1436-UTC.eml (135,700 bytes)
- 2018-05-28-Emotet-malspam-1453-UTC.eml (137,755 bytes)
- 2018-05-29-Emotet-malspam-1934-UTC.eml (1,264 bytes)
- 2018-05-30-Emotet-malspam-0518-UTC.eml (144,525 bytes)
- 2018-05-31-Emotet-malspam-0500-UTC.eml (141,913 bytes)
- 2018-05-31-Emotet-malspam-1733-UTC.eml (1,124 bytes)
- 2018-05-31-Emotet-malspam-1812-UTC.eml (723 bytes)
- 2018-05-31-Emotet-malspam-1849-UTC.eml (1,141 bytes)
- 2018-05-31-Emotet-malspam-1853-UTC.eml (1,262 bytes)
- Zip archive with 3 examples of infection traffic: 2018-05-31-Emotet-infection-traffic-3-pcaps.zip 14.1 MB (14,056,104 bytes)
- 2018-05-28-Emotet-infection-traffic.pcap (2,042,912 bytes)
- 2018-05-29-Emotet-infection-traffic.pcap (16,325,445 bytes)
- 2018-05-31-Emotet-infection-traffic.pcap (5,484,485 bytes)
- Zip archive with the associated Word docs and malware binaries: 2018-05-31-Emotet-word-docs-and-malware-binaries.zip 930 kB (929,999 bytes)
- 2018-05-28-Emotet-malware-binary.exe (172,032 bytes)
- 2018-05-28-Zeus-Panda-Banker-caused-by-Emotet-infection.exe (226,816 bytes)
- 2018-05-28-downloaded-Word-doc-with-macro-for-Emotet.doc (121,344 bytes)
- 2018-05-29-Emotet-malware-binary-1-of-2.exe (200,704 bytes)
- 2018-05-29-Emotet-malware-binary-2-of-2.exe (196,608 bytes)
- 2018-05-29-downloaded-Word-doc-with-macro-for-Emotet.doc (126,464 bytes)
- 2018-05-31-Emotet-malware-binary.exe (274,432 bytes)
- 2018-05-31-downloaded-Word-doc-with-macro-for-Emotet.doc (96,256 bytes)
- COMET SIGNS PAYMENT NOTIFICATION 05.28.2018.doc (99,840 bytes)
- Facture-impayee0359594-0516-6306826.doc (104,704 bytes)
- INV #97046 FOR PO #143948250965.doc (98,048 bytes)
- MODIF-FACTURE0185982-06039-877324.doc (102,400 bytes)
- Rechnung_2018_05_033339468066239.doc (104,448 bytes)
- Rechnung_2018_05_5126136674.doc (128,000 bytes)
NOTES:
- Half of the email examples I gathered have links to the malicious Word docs.
- The other half have malicious Word doc attatchments and no link.
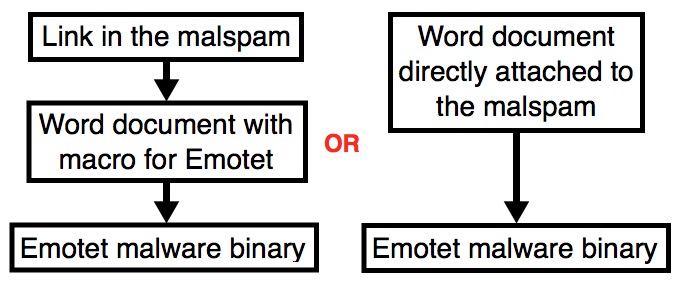
Shown above: Two infection paths.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- adshiepkhach[.]top
- hxxp[:]//alicicek[.]com[.]tr/9DK4OC/
- hxxp[:]//charcalla[.]com/BjmQyaB/
- hxxp[:]//dgnet[.]com[.]br/t5wb/
- hxxp[:]//foodstyle[.]de/kNKqO/
- hxxp[:]//ginca[.]jp/9wBp2v8c/
- hxxp[:]//grupoaire[.]com[.]ar/ups.com/WebTracking/EAP-74807878/
- hxxp[:]//heuveling[.]net/v6jtVz0i/
- hxxp[:]//innervation[.]com/0RtgC6R/
- hxxp[:]//jamesddunn[.]com/FbXTIwq/
- hxxp[:]//jpol[.]com/li8CyWi/
- hxxp[:]//lidoconchiglie[.]com/Tqqk/
- hxxp[:]//lucasweb[.]com[.]br/eQJO3Dr/
- hxxp[:]//muzykomani[.]pl/lenqx/
- hxxp[:]//myorganicflowers[.]com/sJXE/
- hxxp[:]//ncpll1392[.]ir/5p24y/
- hxxp[:]//novaplaza[.]com/ups.com/WebTracking/OWN-4968735410370/
- hxxp[:]//onlychild[.]org/Z3QNxOMmX2/
- hxxp[:]//pjbuys[.]co[.]za/n9yk1/
- hxxp[:]//prokeyboardist[.]com/cciXI/
- hxxp[:]//raffaelli[.]com[.]br/Y3CVrb/
- hxxp[:]//reborntechnology[.]co[.]uk/STATUS/Direct-Deposit-Notice/
- hxxp[:]//slytec[.]com/0FzJB/
- hxxp[:]//smpadvance[.]com/fHOIVS2/
- hxxp[:]//sr-design[.]com/ups.com/WebTracking/KJ-465732741078/
- hxxp[:]//stormny[.]com/zsYYd/
- hxxp[:]//thebluefront[.]com/u5kTmV/
- hxxp[:]//thebluefront[.]com/ups.com/WebTracking/EK-76505310/
- hxxp[:]//timetopatent[.]com/djjgFG1/
- hxxp[:]//transitraum[.]de/NXkK7n/
- hxxp[:]//triadic[.]com/HZToLm/
- hxxp[:]//uhlandstrasse[.]de/67Vl28/
- hxxp[:]//uptondesignbuild[.]com/Jvw0ZX/
- hxxp[:]//utopiaroad[.]com/ups.com/WebTracking/AV-65238624/
- hxxp[:]//136.243.206[.]64:8080/whoami.php
- hxxp[:]//138.68.13[.]161:8080/whoami.php
EMAILS
12 EMAIL EXAMPLES:
(Read: date/time - sending address -- subject)
- 2018-05-28 06:55 UTC -- Telekom Leiter Kundenservice <[removed]@[removed]> -- Ihre Telekom Mobilfunk RechnungOnline Monat Mai 2018 (Nr. 033339468066239)
- 2018-05-28 07:25 UTC -- Kundenservice Rechnungonline Telekom <[removed]@[removed]> -- Rechnung 5126136674
- 2018-05-28 13:11 UTC -- UPS View <[removed]@[removed]> -- UPS Express Domestic
- 2018-05-28 14:36 UTC -- Kenneth Strohmeyer <[removed]@[removed]> -- Kenneth Strohmeyer invoice is available
- 2018-05-28 14:53 UTC -- matt guler <[removed]@[removed]> -- Your Monthly Statement Is Now Available for Review
- 2018-05-29 19:34 UTC -- UPS View <[removed]@[removed]> -- UPS Ship Notification, Tracking Number 9VCC40073620813573
- 2018-05-30 05:18 UTC -- [removed] -- Vos facture impayee du 30 mai 0359594
- 2018-05-31 05:00 UTC -- sandro.mannarino@sheratonparco[.]com <[removed]@[removed]> -- Facturation du 31 mai 0185982
- 2018-05-31 17:33 UTC -- UPS <[removed]@[removed]> -- UPS Delivery Notification, Tracking Number 7LR31170567701951
- 2018-05-31 18:12 UTC -- Microvellum <[removed]@[removed]> -- New Invoice / BD9259 / VX# 5642
- 2018-05-31 18:49 UTC -- UPS Quantum View <[removed]@[removed]> -- UPS Invoice Notification
- 2018-05-31 18:53 UTC -- UPS Quantum View <[removed]@[removed]> -- Your UPS Invoice is Ready
TRAFFIC
URLS FROM THE EMAILS:
- hxxp[:]//grupoaire[.]com[.]ar/ups.com/WebTracking/EAP-74807878/
- hxxp[:]//novaplaza[.]com/ups.com/WebTracking/OWN-4968735410370/
- hxxp[:]//reborntechnology[.]co[.]uk/STATUS/Direct-Deposit-Notice/
- hxxp[:]//sr-design[.]com/ups.com/WebTracking/KJ-465732741078/
- hxxp[:]//thebluefront[.]com/ups.com/WebTracking/EK-76505310/
- hxxp[:]//utopiaroad[.]com/ups.com/WebTracking/AV-65238624/
URLS GENERATED BY THE WORD MARCOS:
- hxxp[:]//alicicek[.]com[.]tr/9DK4OC/
- hxxp[:]//charcalla[.]com/BjmQyaB/
- hxxp[:]//dgnet[.]com[.]br/t5wb/
- hxxp[:]//foodstyle[.]de/kNKqO/
- hxxp[:]//ginca[.]jp/9wBp2v8c/
- hxxp[:]//heuveling[.]net/v6jtVz0i/
- hxxp[:]//innervation[.]com/0RtgC6R/
- hxxp[:]//jamesddunn[.]com/FbXTIwq/
- hxxp[:]//jpol[.]com/li8CyWi/
- hxxp[:]//lidoconchiglie[.]com/Tqqk/
- hxxp[:]//lucasweb[.]com[.]br/eQJO3Dr/
- hxxp[:]//muzykomani[.]pl/lenqx/
- hxxp[:]//myorganicflowers[.]com/sJXE/
- hxxp[:]//ncpll1392[.]ir/5p24y/
- hxxp[:]//onlychild[.]org/Z3QNxOMmX2/
- hxxp[:]//pjbuys[.]co[.]za/n9yk1/
- hxxp[:]//prokeyboardist[.]com/cciXI/
- hxxp[:]//raffaelli[.]com[.]br/Y3CVrb/
- hxxp[:]//slytec[.]com/0FzJB/
- hxxp[:]//smpadvance[.]com/fHOIVS2/
- hxxp[:]//stormny[.]com/zsYYd/
- hxxp[:]//thebluefront[.]com/u5kTmV/
- hxxp[:]//timetopatent[.]com/djjgFG1/
- hxxp[:]//transitraum[.]de/NXkK7n/
- hxxp[:]//triadic[.]com/HZToLm/
- hxxp[:]//uhlandstrasse[.]de/67Vl28/
- hxxp[:]//uptondesignbuild[.]com/Jvw0ZX/
TRAFFIC FROM AN INFECTED WINDOWS HOST ON 2018-05-28:
- 209.59.186[.]42 port 80 - novaplaza[.]com - GET /ups.com/WebTracking/OWN-4968735410370/
- 197.242.78[.]3 port 80 - pjbuys[.]co[.]za - GET /n9yk1/
- 216.105.170[.]139 port 4143 - 216.105.170[.]139:4143 - GET /
- 136.243.206[.]64 port 8080 - 136.243.206[.]64:8080 - GET /whoami.php
- 136.243.206[.]64 port 8080 - 136.243.206[.]64:8080 - GET /
- 91.243.81[.]13 port 443 - adshiepkhach[.]top - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- port 443 - www.google[.]com - probable connectivity check caused by Zeus Panda Banker
TRAFFIC FROM AN INFECTED WINDOWS HOST ON 2018-05-29 (PCAP RAN FOR SEVERAL HOURS):
- 74.220.207[.]118 port 80 - utopiaroad[.]com - GET /ups.com/WebTracking/AV-65238624/
- 69.89.31[.]120 port 80 - uptondesignbuild[.]com - GET /Jvw0ZX/
- 69.89.31[.]120 port 80 - uptondesignbuild[.]com - GET /cgi-sys/suspendedpage.cgi
- 81.169.145[.]93 port 80 - uhlandstrasse[.]de - GET /67Vl28/
- 24.217.117[.]217 port 80 - 24.217.117[.]217 - GET /
- 138.68.13[.]161 port 8080 - 138.68.13[.]161:8080 - GET /whoami.php
- 138.68.13[.]161 port 8080 - 138.68.13[.]161:8080 - GET /
- 62.159.33[.]122 port 20 - 62.159.33[.]122:20 - GET /
- 216.105.170[.]139 port 4143 - 216.105[.]170.139:4143 - GET /
- 72.52.216[.]110 port 8080 - 72.52.216[.]110:8080 - GET /
- 205.178.137[.]221 port 8080 - 205.178[.]137.221:8080 - GET /
- 149.62.173[.]247 port 8080 - 149.62.173[.]247:8080 - GET /
- 50.84.95[.]206 port 80 - 50.84.95[.]206 - GET /
- 199.189.228[.]60 port 80 - 199.189.228[.]60 - GET /
- 158.181.186[.]171 port 8080 - 158.181.186[.]171:8080 - GET /
- 179.42.195[.]195 port 80 - 179.42.195[.]195 - GET /
- 98.191.195[.]92 port 8080 - 98.191.195[.]92:8080 - GET /
- 74.139.102[.]161 port 443 - 74.139.102[.]161:443 - GET /
- 50.84.214[.]74 port 8080 - 50.84.214[.]74:8080 - GET /
- 98.172.71[.]14 port 80 - 98.172.71[.]14 - GET /
- 65.34.131[.]135 port 80 - 65.34.131[.]135 - GET /
- 24.248.225[.]107 port 80 - 24.248.225[.]107 - GET /
- 66.61.15[.]55 port 80 - 66.61.15[.]55 - GET /
- 207.68.223[.]75 port 8080 - 207.68.223[.]75:8080 - GET /
- 70.183.98[.]85 port 8080 - 70.183.98[.]85:8080 - GET /
- 173.78.254[.]86 port 8080 - 173.78.254[.]86:8080 - GET /
- 125.129.212[.]89 port 8080 - 125.129.212[.]89:8080 - GET /
- 5.9.252[.]80 port 8080 - 5.9.252[.]80:8080 - GET /
- 46.4.100[.]178 port 8080 - 46.4.100[.]178:8080 - GET /
- 139.162.216[.]32 port 8080 - 139.162.216[.]32:8080 - GET /
- 46.38.238[.]8 port 8080 - 46.38.238[.]8:8080 - GET /
- 23.239.2[.]11 port 8080 - 23.239.2[.]11:8080 - GET /
- 50.31.146[.]101 port 8080 - 50.31.146[.]101:8080 - GET /
- 166.63.0[.]27 port 8080 - 166.63.0[.]27:8080 - GET /
- 46.101.205[.]45 port 4143 - 46.101.205[.]45:4143 - GET /
- various IP addresses on TCP ports 25, 465 or 587 - various domains - SMTP or encrypted SMTP traffic
TRAFFIC FROM AN INFECTED WINDOWS HOST ON 2018-05-31:
- 200.43.192[.]5 port 80 - grupoaire[.]com[.]ar - GET /ups.com/WebTracking/EAP-74807878/
- 46.245.165[.]4 port 80 - alicicek[.]com[.]tr - GET /9DK4OC/
- 24.217.117[.]217 port 80 - 24.217.117[.]217 - GET /
- 216.105.170[.]139 port 4143 - 216.105.170[.]139:4143 - GET /
- 138.68.13[.]161 port 8080 - 138.68.13[.]161:8080 - GET /whoami.php
- 166.63.0[.]27 port 8080 - 166.63.0[.]27:8080 - GET /
- various IP addresses on TCP ports 25, 465 or 587 - various domains - SMTP or encrypted SMTP traffic
FILE HASHES
SHA256 HASHES FOR WORD DOCS WITH MACRO FOR EMOTET:
- 5694549a92dcc6caf112623531aa90c5dac914e5ff11d64cd5f3072a75fc5555 -- 121,344 bytes -- Downloaded Word doc on 2018-05-28
- 6302ab4b2f00b904a2f3dc9a003525646b6d836aa71b52cd6531b325b4c7674a -- 126,464 bytes -- Downloaded Word doc on 2018-05-29
- 3a39ef1275746d1ada47d5902f0ae8c08230a38c4b0e6ff9a17050141c9bdb92 -- 96,256 bytes -- Downloaded Word doc on 2018-05-31
- d0377f18aaf57aa4e772de6417d16ef9f49a82cbec30508cc26fb38048d7aa7c -- 99,840 bytes -- COMET SIGNS PAYMENT NOTIFICATION 05.28.2018.doc
- c2f1ced730a6cc7ae64c9e4c753145a54f8e1fbdd6bf55c7c79ebde9d24637c7 -- 104,704 bytes -- Facture-impayee0359594-0516-6306826.doc
- 07ba0789841e71d4c4c030bd30768eab9ae52a0555276c3c2d97f5c38ea6dc79 -- 98,048 bytes -- INV #97046 FOR PO #143948250965.doc
- d51aa2a02a96775c8ac40795248154ed6dd745472c2e7595c8c8dda938df6e8c -- 102,400 bytes -- MODIF-FACTURE0185982-06039-877324.doc
- 32e2219517c127435fa66775ffa5c5abcf40a197d10d73556066a363cd991221 -- 104,448 bytes -- Rechnung_2018_05_033339468066239.doc
- cd35cb4686a14264a70890c9e4cd1852f85104c61ce6441b86ddbf67fe120af6 -- 128,000 bytes -- Rechnung_2018_05_5126136674.doc
EMOTET MALWARE BINARIES:
- 9ffa5669fdc8dca6a46f33a098c01382e3a12c00ff7bb3d1360ad8f1ca422408 -- 172,032 bytes -- Emotet malware binary on 2018-05-28
- a79b185a903ea50f52c0262d58e9cf25aed90c2af6ef8484bbc4a243077d278e -- 226,816 bytes -- Emotet malware binary (1 of 2) on 2018-05-29
- 102be05e2d4824a18ccbd7a898ef267760957fba7263169cf966d8efc961ffbf -- 200,704 bytes -- Emotet malware binary (2 of 2) on 2018-05-29
- dfb0164104a02cfa58ab14fefc48c38425daa1866d898baf49450fca066aa22e -- 196,608 bytes -- Emotet malware binary on 2018-05-31
- Location I saw for the above files on my infected Windows hosts: C:\Users\[username]\AppData\Local\Microsoft\Windows\vsdgbatt.exe
ZEUS PANDA BANKER CAUSED BY EMOTET INFECTION:
- SHA256 hash: 1e2753d3e917e1bb3fd0ace5320df965f18c8e49660e3814ddc5d1c4048affca
File size: 226,816 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker binary caused by Emotet infection on 2018-05-28
IMAGES
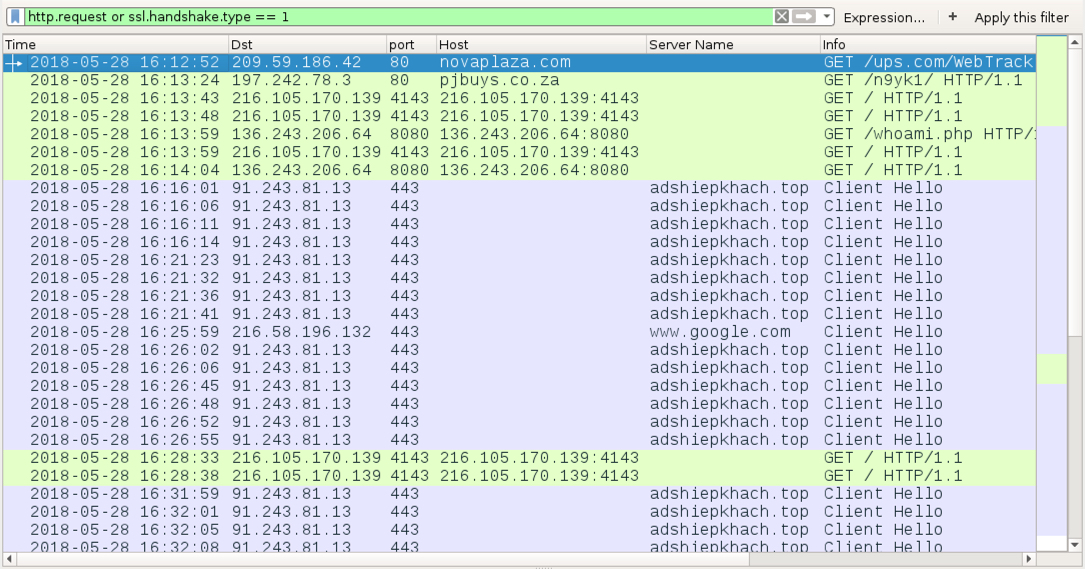
Shown above: Traffic from the 2018-05-28 infection filtered in Wireshark--Emotet, which also caused Zeus Panda Banker.
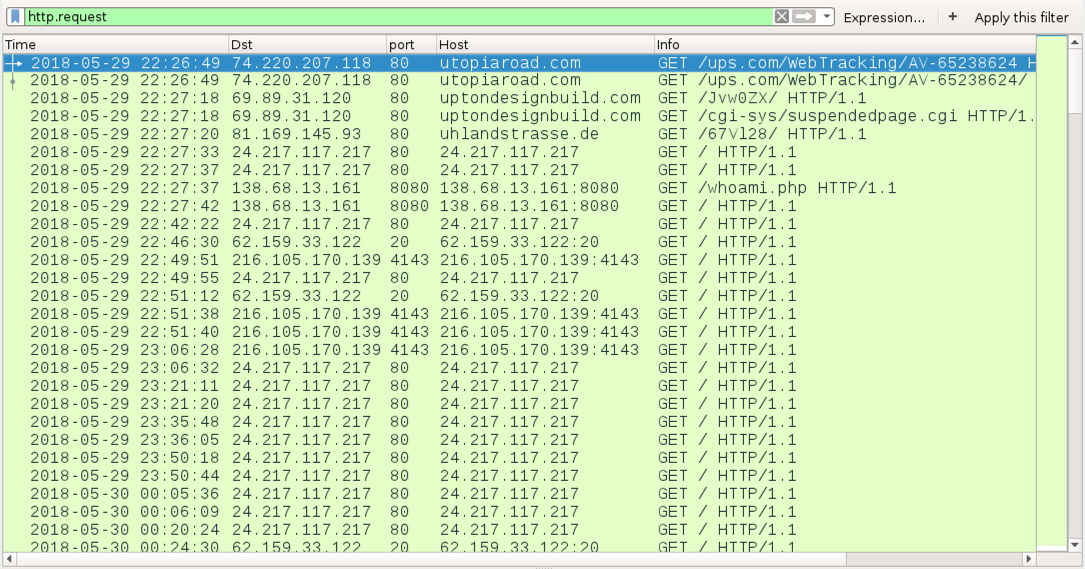
Shown above: Traffic from the 2018-05-29 infection filtered in Wireshark--Emotet, which turned the infected host into an Emotet malspambot.
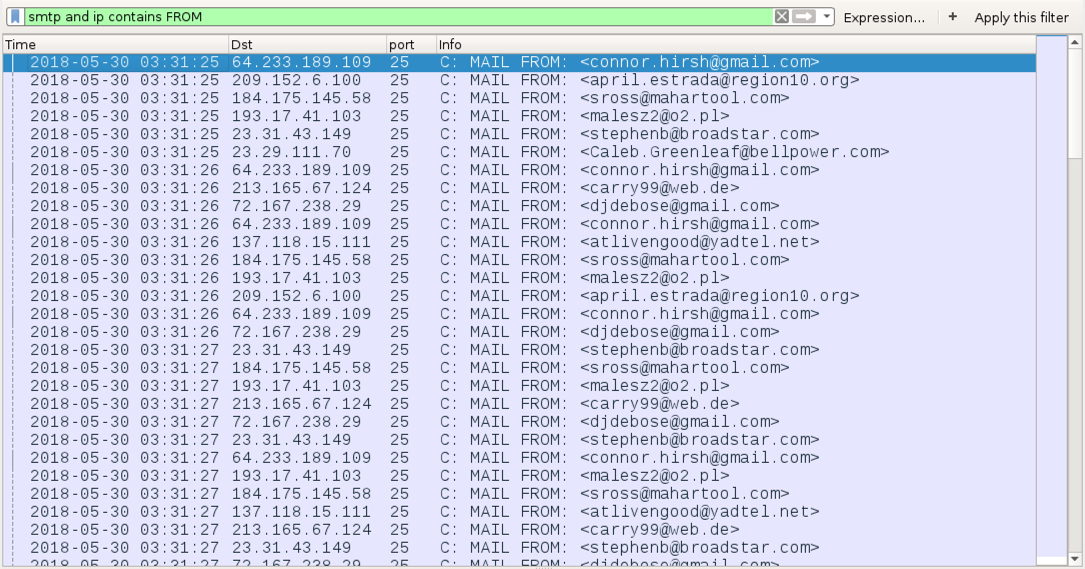
Shown above: Traffic from the 2018-05-29 infection filtered in Wireshark to show sending addresses of the SMTP traffic from my infected Windows host.
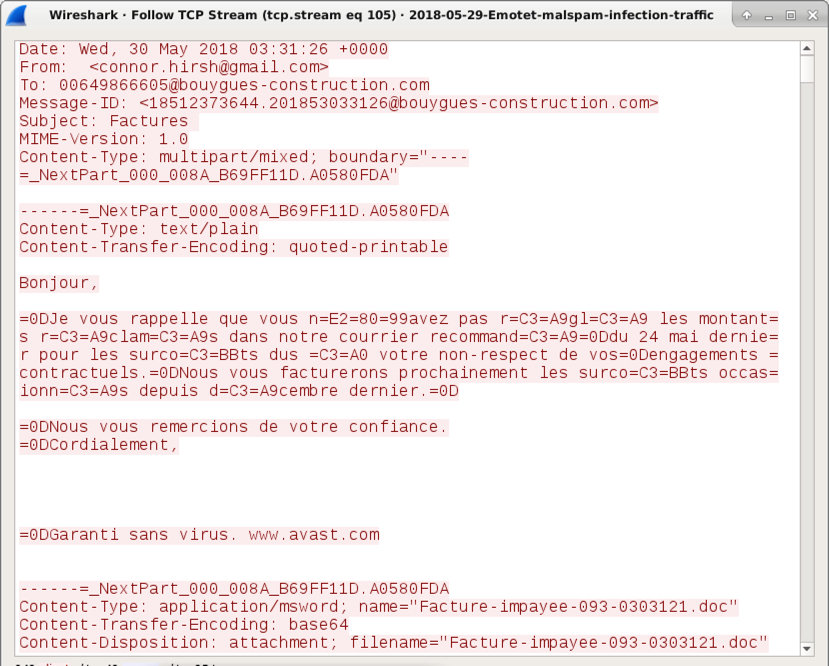
Shown above: An example of the emails from my infected Windows host on 2018-05-29.
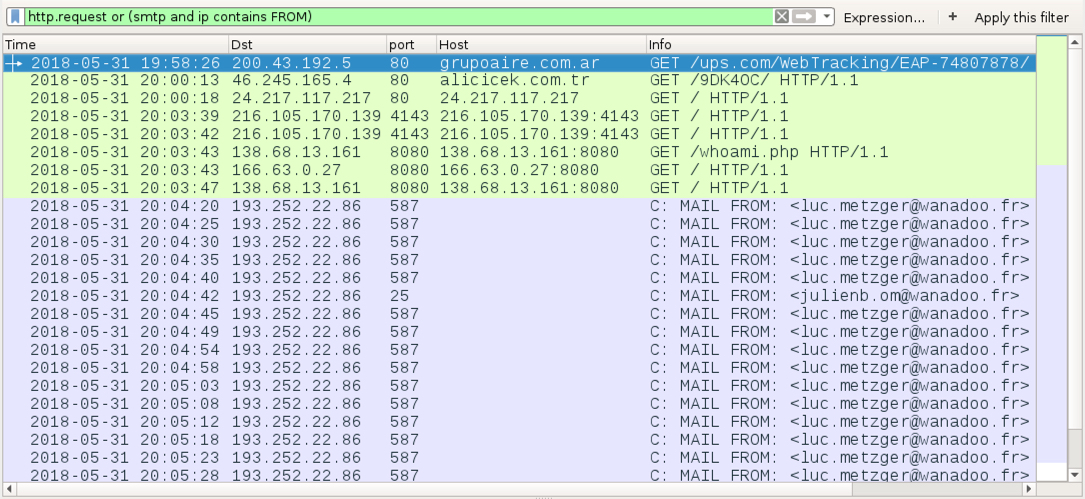
Shown above: Traffic from the 2018-05-31 infection filtered in Wireshark--Emotet, which turned the infected host into an Emotet malspambot.
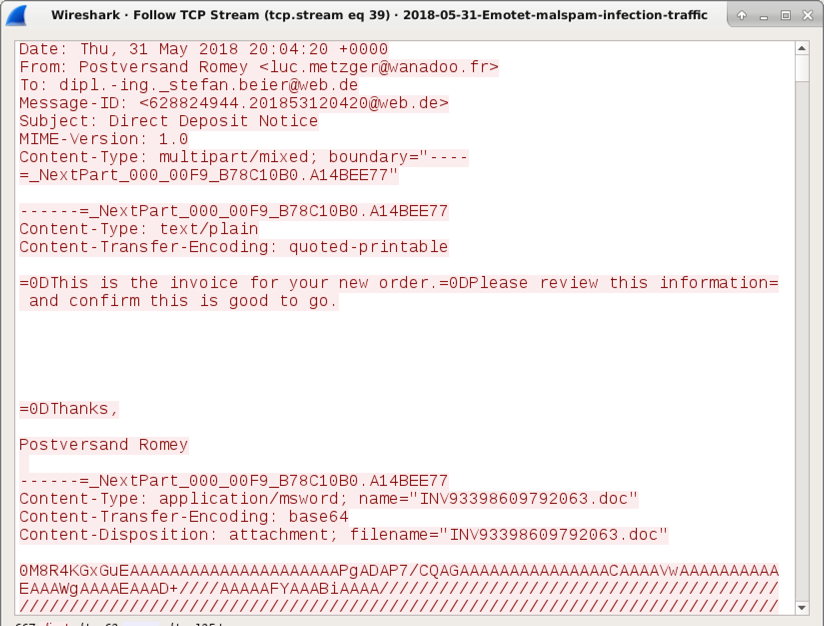
Shown above: An example of the emails from my infected Windows host on 2018-05-31.
Click here to return to the main page.