2018-05-31 - FAKE HELLOFAX NOTIFICATION EMAILS LEAD TO HANCITOR WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-05-31-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 516 kB (516,250 bytes)
- 2018-05-31-Hancitor-infection-with-Zeus-Panda-Banker.pcap (708,946 bytes)
- Zip archive of the email example: 2018-05-31-Hancitor-malspam-1618-UTC.eml.zip 2.1 kB (2,085 bytes)
- 2018-05-31-Hancitor-malspam-1618-UTC.eml (6,157 bytes)
- Zip archive of the malware: 2018-05-31-malware-and-artifacts-from-Hancitor-infection.zip 266 kB (266,319 bytes)
- 2018-05-31-Word-doc-with-macro-for-Hancitor.doc (175,104 bytes)
- 2018-05-31-Zeus-Panda-Banker-caused-by-Hanictor-infection.exe (203,264 bytes)
NOTES:
- The block list contains additional info reported by @James_inthe_box in Pastebin link from this Twitter thread.
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
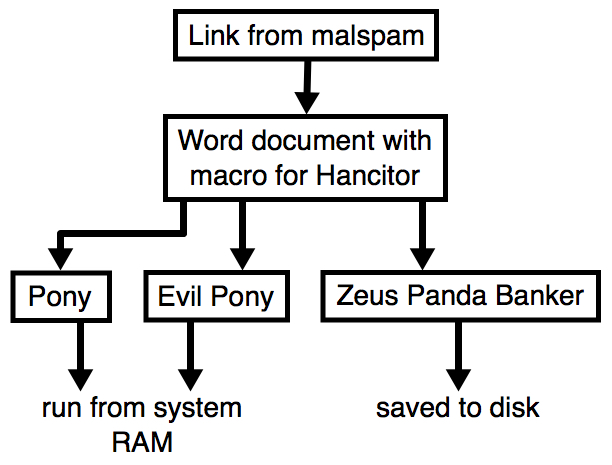
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- beachfrontflamingo[.]info
- beachfrontflamingo[.]net
- clinicamishijos[.]com
- clinicasholadoctora[.]com
- clinicasmishijos[.]com
- flamingobeachparadise[.]com
- holamigenteusa[.]net
- holamishijos[.]com
- holaredusa[.]info
- midoctorausa[.]com
- miplanmedicousa[.]info
- miplanmedicousa[.]net
- mybeachevent[.]com
- mybeachfiesta[.]com
- mybeachfrontcostarica[.]com
- mybeachfrontflamingocostarica[.]com
- mypuravidaparadise[.]com
- puravidamarina[.]com
- butrirepun[.]ru
- enonuseda[.]com
- gedoleftrep[.]ru
- hxxp[:]//aikon[.]ca/wp-content/plugins/breadcrumb-navxt/includes/1
- hxxp[:]//aikon[.]ca/wp-content/plugins/breadcrumb-navxt/includes/2
- hxxp[:]//aikon[.]ca/wp-content/plugins/breadcrumb-navxt/includes/3
- hxxp[:]//ancoprecision[.]com/blog/wp-content/plugins/like-for-tags/1
- hxxp[:]//ancoprecision[.]com/blog/wp-content/plugins/like-for-tags/2
- hxxp[:]//ancoprecision[.]com/blog/wp-content/plugins/like-for-tags/3
- hxxp[:]//ebargains[.]com[.]au/wp-content/plugins/jquery-updater/1
- hxxp[:]//ebargains[.]com[.]au/wp-content/plugins/jquery-updater/2
- hxxp[:]//ebargains[.]com[.]au/wp-content/plugins/jquery-updater/3
- hxxp[:]//kamalala[.]com/wp-content/plugins/favicon-rotator/includes/1
- hxxp[:]//kamalala[.]com/wp-content/plugins/favicon-rotator/includes/2
- hxxp[:]//kamalala[.]com/wp-content/plugins/favicon-rotator/includes/3
- hxxp[:]//lmkpartners[.]com/blog/wp-content/themes/twentythirteen/inc/1
- hxxp[:]//lmkpartners[.]com/blog/wp-content/themes/twentythirteen/inc/2
- hxxp[:]//lmkpartners[.]com/blog/wp-content/themes/twentythirteen/inc/3
- betrephengu[.]ru
EMAILS
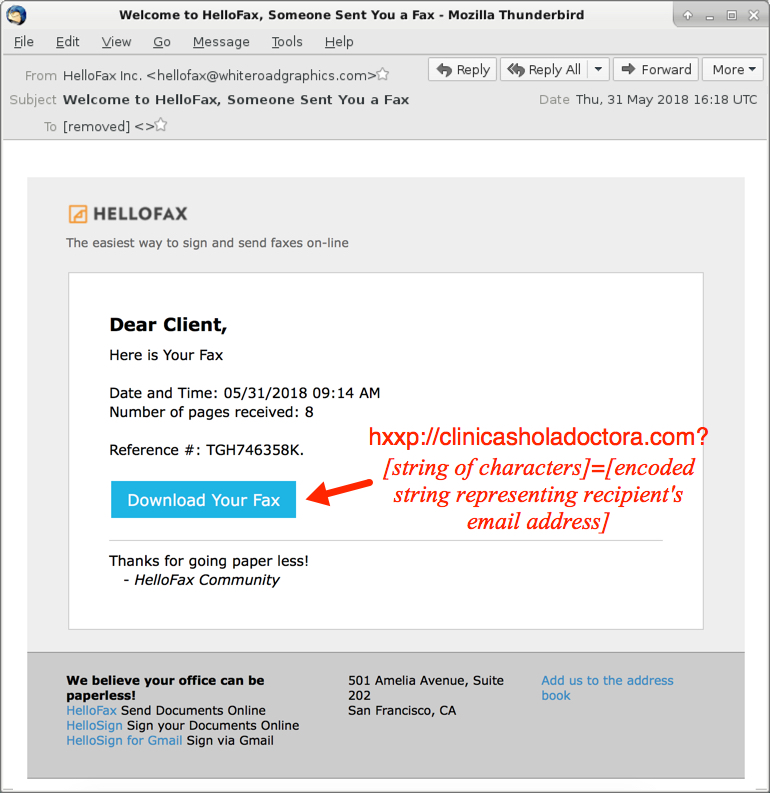
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
Received: from whiteroadgraphics[.]com ([66.51.152[.]18]) by [removed] for [removed];
Thu, 31 May 2018 16:18:27 +0000 (UTC)
Message-ID: <977B1E28.53BBE045@whiteroadgraphics[.]com>
Date: Thu, 31 May 2018 12:18:31 -0400
Reply-To: "HelloFax Inc." <hellofax@whiteroadgraphics[.]com>
From: "HelloFax Inc." <hellofax@whiteroadgraphics[.]com>
X-Mailer: Apple Mail (2.1084)
X-Accept-Language: en-us
MIME-Version: 1.0
TO: [removed]
Subject: Welcome to HelloFax, Someone Sent You a Fax
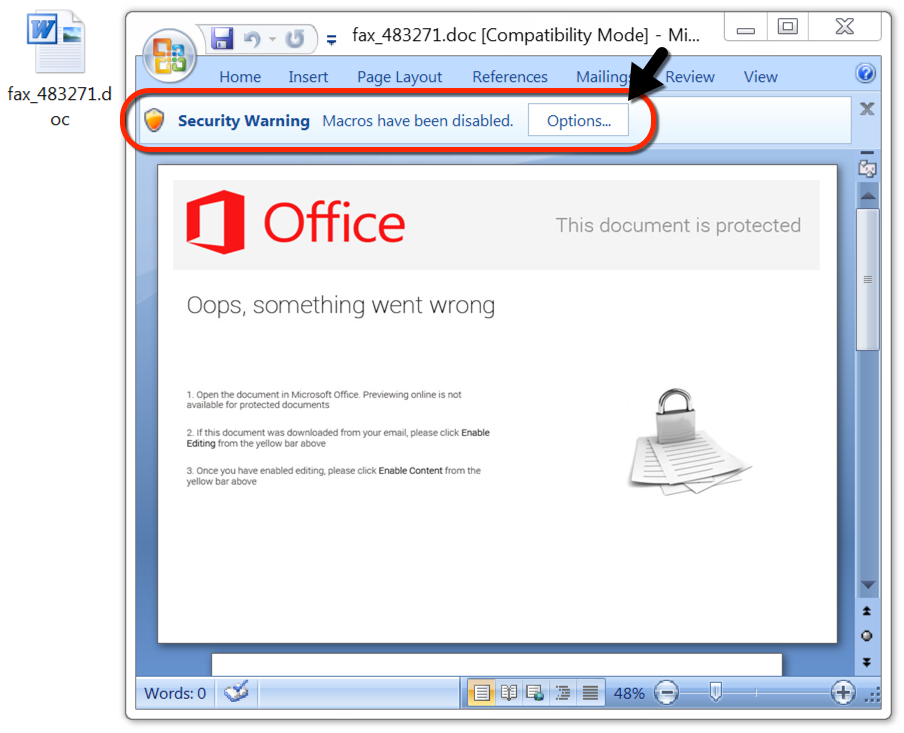
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
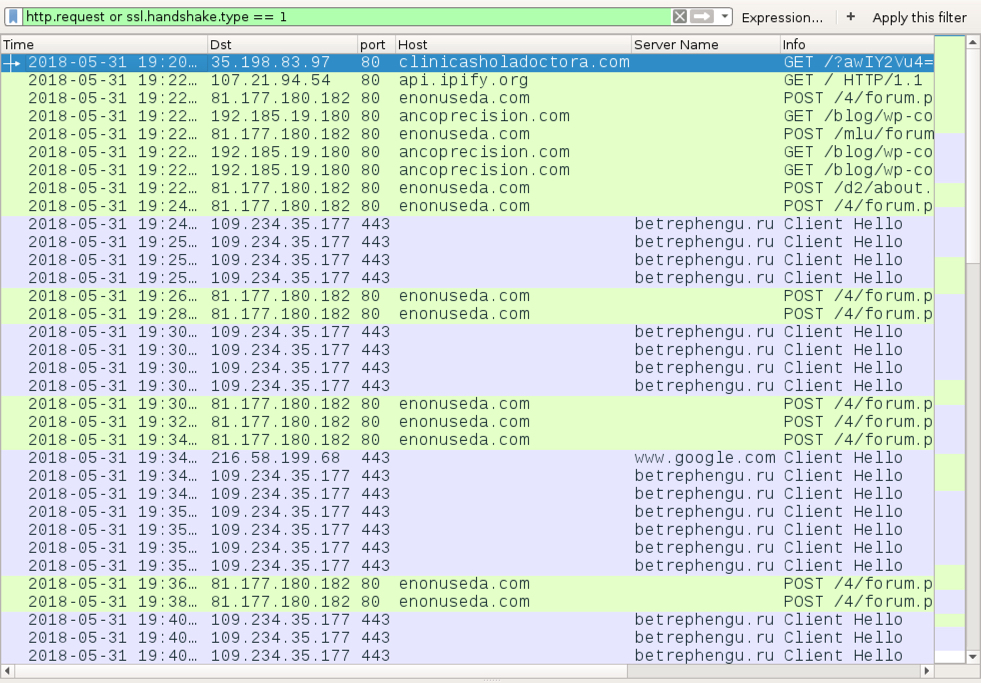
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.198.83[.]97 port 80 - clinicasholadoctora[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 81.177.180[.]182 port 80 - enonuseda[.]com - POST /4/forum.php
- 81.177.180[.]182 port 80 - enonuseda[.]com - POST /mlu/about.php
- 81.177.180[.]182 port 80 - enonuseda[.]com - POST /d2/about.php
- 192.185.19[.]180 port 80 - ancoprecision[.]com - GET /blog/wp-content/plugins/like-for-tags/1
- 192.185.19[.]180 port 80 - ancoprecision[.]com - GET /blog/wp-content/plugins/like-for-tags/2
- 192.185.19[.]180 port 80 - ancoprecision[.]com - GET /blog/wp-content/plugins/like-for-tags/3
- 109.234.35[.]177 port 443 - betrephengu[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- port 80 - www.google[.]com - HTTPS/SSL/TLS traffic - probable connectivity check caused by Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: d39dd0d601b8a3f32c79734fd35322fb2df58a710716409d05e2721ef6a391ca
File size: 175,104 bytes
File name: fax_483271.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 3d164cb4eadc84b05e4a18df52227e0cec4a259a8db9d723bce5a465531c6e71
File size: 203,264 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
Click here to return to the main page.