2018-06-04 - GANDCRAB RANSOMWARE FROM MALSPAM WITH PASSWORD-PROTECTED WORD DOCS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the spreadsheet tracker: 2018-06-04-malspam-spreadsheet-tracker.csv.zip 0.8 kB (815 bytes)
- Zip archive of the infection traffic: 2018-06-04-Gandcrab-ransomware-infection.pcap.zip 254 kB (253,903 bytes)
- Zip archive of the associated files: 2018-06-04-malspam-attachments-and-artifacts-from-Gandcrab-ransomware.zip 2.6 MB (2,588,222 bytes)
NOTES:
- I keep running into this malspam, which I started documenting as early as mid-March of 2018. Previous documentation includes:
- 2018-03-14 - ISC diary - Malspam pushing Sigma ransomware
- 2018-04-20 - ISC diary - Malspam pushing ransomware using two layers of password protection to avoid detection
- 2018-05-09 - malware-traffic-analysis.net - Malspam using password-protected Word docs still active
- So I'm still seeing it. This time it's sending GandCrab ransomware.
- Checking through VirusTotal Intelligence, I saw hundreds of these password-protected Word docs sent through malspam during the past few days.
- When I checked early this morning, I found the following numbers on the parameters tag:doc tag:attachment size:36352
- Tue 2018-05-29 - 146 files
- Wed 2018-05-30 - 9 files
- Thu 2018-05-31 - 116 files
- Fri 2018-06-01 - 181 files
- Sat 2018-06-02 - 311 files
- Sun 2018-06-03 - 43 files
- Mon 2018-06-04 - 69 files and counting
- For today's post, I've collected 12 samples, so you can get an idea of the malspam.
- Most of the associated emails sent to VirusTotal don't have the Received: from lines in the headers.
- Because of this, I don't have a good idea what IP addresses this malspam is coming from.
- The password for all of these Word documents should be: 123123
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain and URLs:
- hxxp[:]//209.141.49[.]93/hello.bin
- carder[.]bit
- gandcrab2pie73et[.]onion
EMAILS
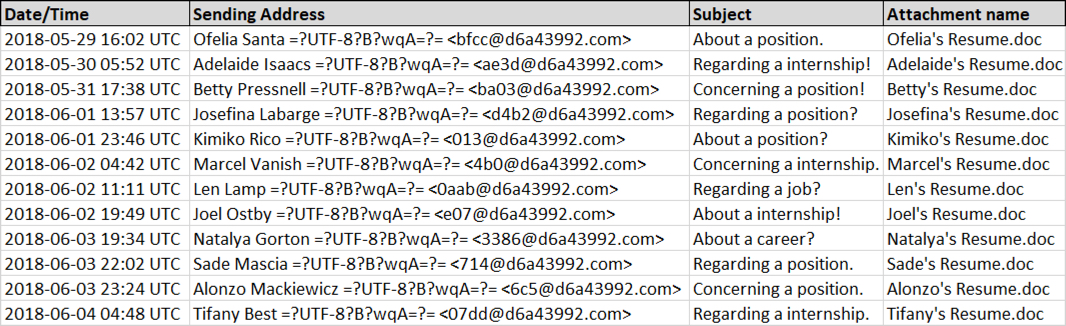
Shown above: Screenshot from the spreadsheet tracker.
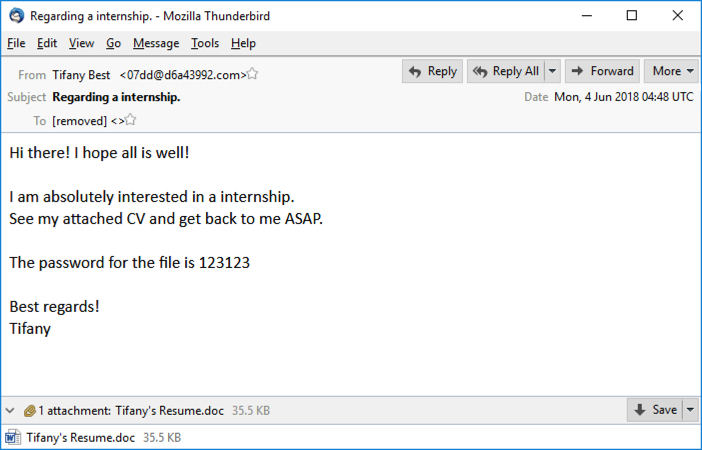
Shown above: Screenshot from one of the emails.
EMAIL EXAMPLES:
(READ: Date/Time -- Sending Address -- Subject -- Attachment name)
- 2018-05-29 16:02 UTC -- Ofelia Santa =?UTF-8?B?wqA=?= <bfcc@d6a43992[.]com> -- About a position. -- Ofelia's Resume.doc
- 2018-05-30 05:52 UTC -- Adelaide Isaacs =?UTF-8?B?wqA=?= <ae3d@d6a43992[.]com> -- Regarding a internship! -- Adelaide's Resume.doc
- 2018-05-31 17:38 UTC -- Betty Pressnell =?UTF-8?B?wqA=?= <ba03@d6a43992[.]com> -- Concerning a position! -- Betty's Resume.doc
- 2018-06-01 13:57 UTC -- Josefina Labarge =?UTF-8?B?wqA=?= <d4b2@d6a43992[.]com> -- Regarding a position? -- Josefina's Resume.doc
- 2018-06-01 23:46 UTC -- Kimiko Rico =?UTF-8?B?wqA=?= <013@d6a43992[.]com> -- About a position? -- Kimiko's Resume.doc
- 2018-06-02 04:42 UTC -- Marcel Vanish =?UTF-8?B?wqA=?= <4b0@d6a43992[.]com> -- Concerning a internship. -- Marcel's Resume.doc
- 2018-06-02 11:11 UTC -- Len Lamp =?UTF-8?B?wqA=?= <0aab@d6a43992[.]com> -- Regarding a job? -- Len's Resume.doc
- 2018-06-02 19:49 UTC -- Joel Ostby =?UTF-8?B?wqA=?= <e07@d6a43992[.]com> -- About a internship! -- Joel's Resume.doc
- 2018-06-03 19:34 UTC -- Natalya Gorton =?UTF-8?B?wqA=?= <3386@d6a43992[.]com> -- About a career? -- Natalya's Resume.doc
- 2018-06-03 22:02 UTC -- Sade Mascia =?UTF-8?B?wqA=?= <714@d6a43992[.]com> -- Regarding a position. -- Sade's Resume.doc
- 2018-06-03 23:24 UTC -- Alonzo Mackiewicz =?UTF-8?B?wqA=?= <6c5@d6a43992[.]com> -- Concerning a position. -- Alonzo's Resume.doc
- 2018-06-04 04:48 UTC -- Tifany Best =?UTF-8?B?wqA=?= <07dd@d6a43992[.]com> -- Regarding a internship. -- Tifany's Resume.doc
EXAMPLE OF THE EMAIL HEADERS:
Received: from mail13.tiranbro[.]com ([46.161.42[.]11]) by [removed] for [removed];
Tue, 29 May 2018 16:03:43 +0000
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=default; d=tiranbro[.]com;
h=From:Content-Type:Mime-Version:Subject:Message-Id:Date:To;[removed];
bh=O/4z7dolnI/WI7L58+Bs3MGxZoU=;
b=KpjNi3cYWiDW07Ohi/xN9ZMJA4bMTBbAgbWHVxExnRYY6JudM+/Ez1+2OZ34FmcHfV5ToRXsqEBe
5LHf2BsyAgAOble+AdM4Q87Kp+FBxivYcmiNrJ2is9vc3eT/nYKrSlJeB/wdb0fcDBKTCG1tEGFp
d1VuCRpbMVhPo6tunQk=
DomainKey-Signature: a=rsa-sha1; c=nofws; q=dns; s=default; d=tiranbro[.]com;
b=OCcl37RY0KZhmSHfjP7N2bmhO4OrK/NQPhqhKHFUesWCsKY80769NgeBEG1OYv0lzVn50Fr3lYx7
iAODzQXYpVNSmu6g9Quyz5NQo+4IC1qZkbZpmZjZPtSDTAc5YZMp/WJ4Vl+p4Od5UF5BkfoRH68k
WUWyvzzWzn+OxKxbrBE=;
From: Ofelia Santa =?UTF-8?B?wqA=?= <bfcc@d6a43992[.]com>
Content-Type: multipart/mixed;
boundary="Apple-Mail-AC4D618F-85BE-43E7-00C6-A3D8FC517F37"
Mime-Version: 1.0 (1.0)
Subject: About a position.
Message-Id: <0749aa26e943021016158642e6e28bb2@d6a43992[.]com>
Date: Tue, 29 May 2018 18:02:10 +0200
To: [removed]
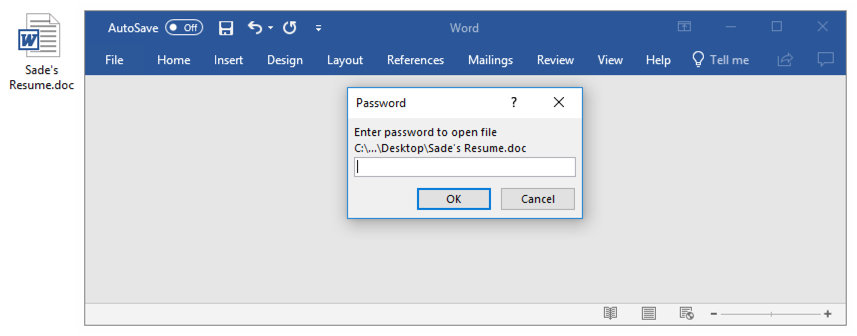
Shown above: Malicious Word document downloaded from link in the malspam.
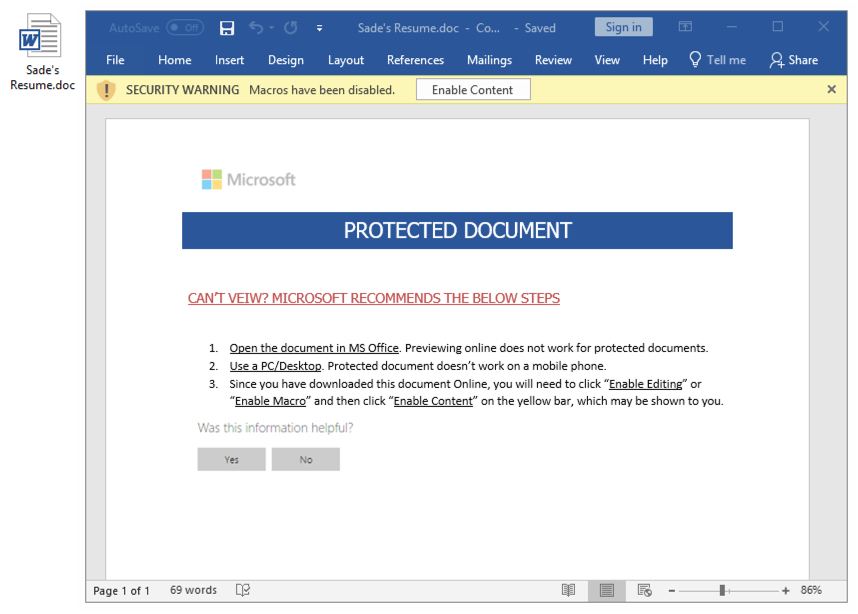
Shown above: Attached Word document after entering the password 123123.
TRAFFIC
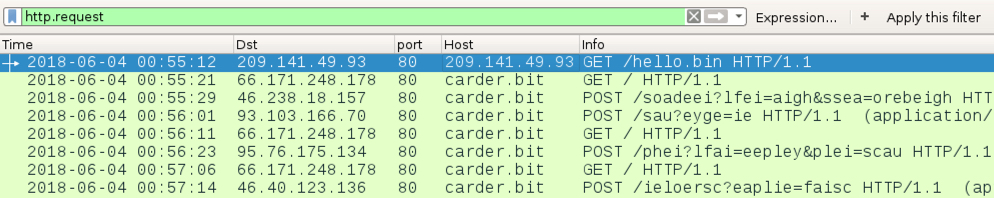
Shown above: Traffic from an infection filtered in Wireshark.
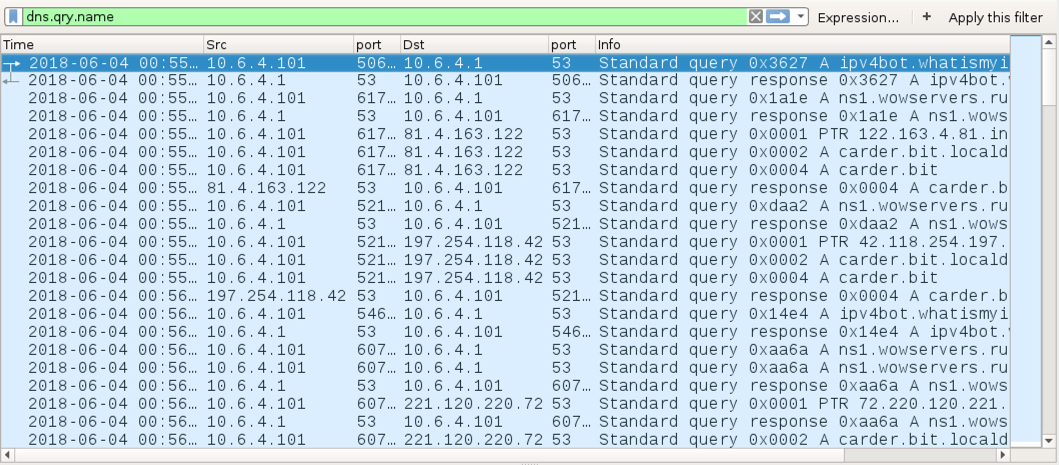
Shown above: DNS Traffic that shows DNS queries for carder[.]bit to some outside DNS server.
HTTP TRAFFIC FROM AN INFECTED LAB HOST:
- 209.141.49[.]93 port 80 - 209.141.49[.]93 - GET /hello.bin
- 66.171.248[.]178 port 80 - carder[.]bit - GET /
- 46.238.18[.]157 port 80 - carder[.]bit - POST /soadeei?lfei=aigh&ssea=orebeigh
- 93.103.166[.]70 port 80 - carder[.]bit - POST /sau?eyge=ie
- 95.76.175[.]134 port 80 - carder[.]bit - POST /phei?lfai=eepley&plei=scau
- 46.40.123[.]136 port 80 - carder[.]bit - POST /ieloersc?eaplie=faisc
DNS TRAFFIC FROM AN INFECTED LAB HOST:
- DNS query for ipv4bot.whatismyipaddress[.]com - returned IP address used for carder[.]bit when doing IP address checks
- DNS query for ns1.wowservers[.]ru and ns1.wowservers[.]ru - returned IP addresses used as a DNS server for DNS queries on carder[.]bit.
- 81.4.163[.]122 UDP port 53 - DNS queries for carder[.]bit
- 197.254.118[.]42 UDP port 53 - DNS queries for carder[.]bit
- 221.120.220[.]72 UDP port 53 - DNS queries for carder[.]bit
- 190.35.242[.]126 UDP port 53 - DNS queries for carder[.]bit
INFORMATION FROM THE DECRYPTION INSTRUCTIONS:
- gandcrab2pie73et[.]onion - Tor domain used to get at the decryption instructions
- ransomware@sj[.]ms Jabber ID that can be used on anonymous Jabber server sj[.]ms.
FILE HASHES
SHA256 HASHES FOR ATTACHMENTS:
- c13962f54a949724c0713a133035de7fbd48d49722ee5805be2ef1f8437d275a - Adelaide's Resume.doc
- 53c98a623d23778770be0273254515786514fae00d11a928f32d43b5a3e33ed5 - Alonzo's Resume.doc
- e9b4d828790e0ee6bbfc0675e09efc212dce7b84e07758a2f0444aeb24914e69 - Betty's Resume.doc
- e7dc7b0fe39c98d63983eac54326bdf60e79a4f3aa0178564a6c905d11033ddf - Joel's Resume.doc
- 5746e9436b95b620e5197ea718a598688fd6a587f8f9c2e9ddb9ec13193329b6 - Josefina's Resume.doc
- 316a9295cf30b759c02b392f0b5b3e1f28ad2f6ed5ad1a11ad079e3dbcb141e1 - Kimiko's Resume.doc
- b0c7057c8467f15e5e4875b696def20fcab892e1d254a369249a3159f0670854 - Len's Resume.doc
- 428ffc236bc0b08d88f2990a3c1aa4dfab715aa90d65f60217e4f3651bc1b0d1 - Marcel's Resume.doc
- f3c921377c73cd3eec1ff5561ba603480f33caea6d49fc79b8fdf0e642d924dd - Natalya's Resume.doc
- e11dcc64efb1ce8b8d5237590754c13e92a455095f7f1f501ce64a200f64ffe2 - Ofelia's Resume.doc
- 6498b44ed0de93353b5b798bb022ec407e85266ca0341e668ef03307d24ceda1 - Sade's Resume.doc
- 97547a45953be24a4261b2fd925748676627112ad53bd3b7240b1643eac4b94f - Tifany's Resume.doc
INFORMATION FOR GANDCRAB RANSOMWARE BINARY:
- SHA256 hash: ae0d1591385c573af2ad6b04816a7d6a30c87ccf40e8f02b3c76e66a4c8450e6
File size: 321,545 bytes
File location: C:\Users\[username]\AppData\Local\Temp\qwerty.exe
File description: GandCrab ransomware binary seen on 2018-06-04 from hxxp[:]//209.141.49[.]93/hello.bin
IMAGES
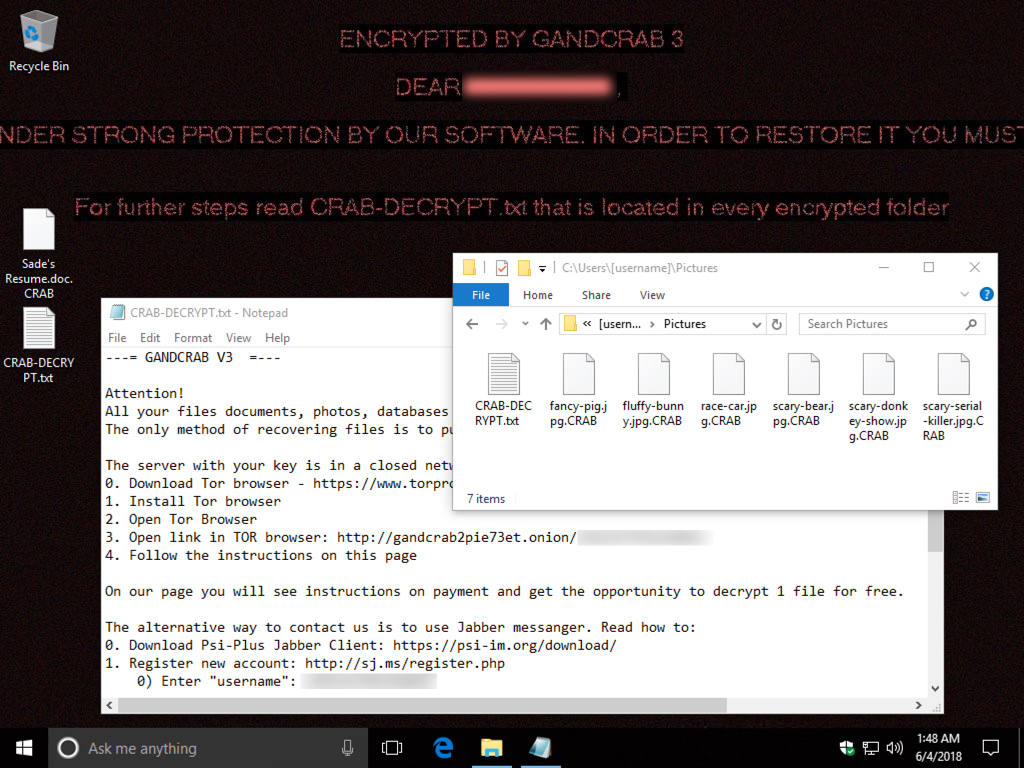
Shown above: Desktop of an infected Windows host.
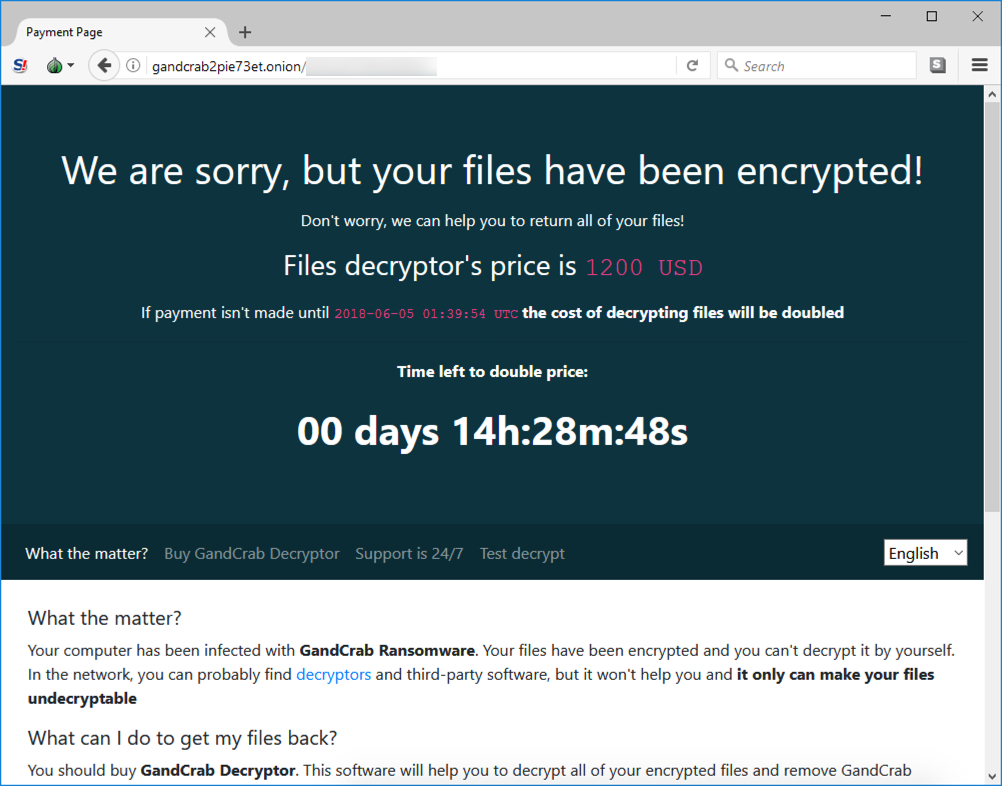
Shown above: GandCrab decryptor (1 of 2).
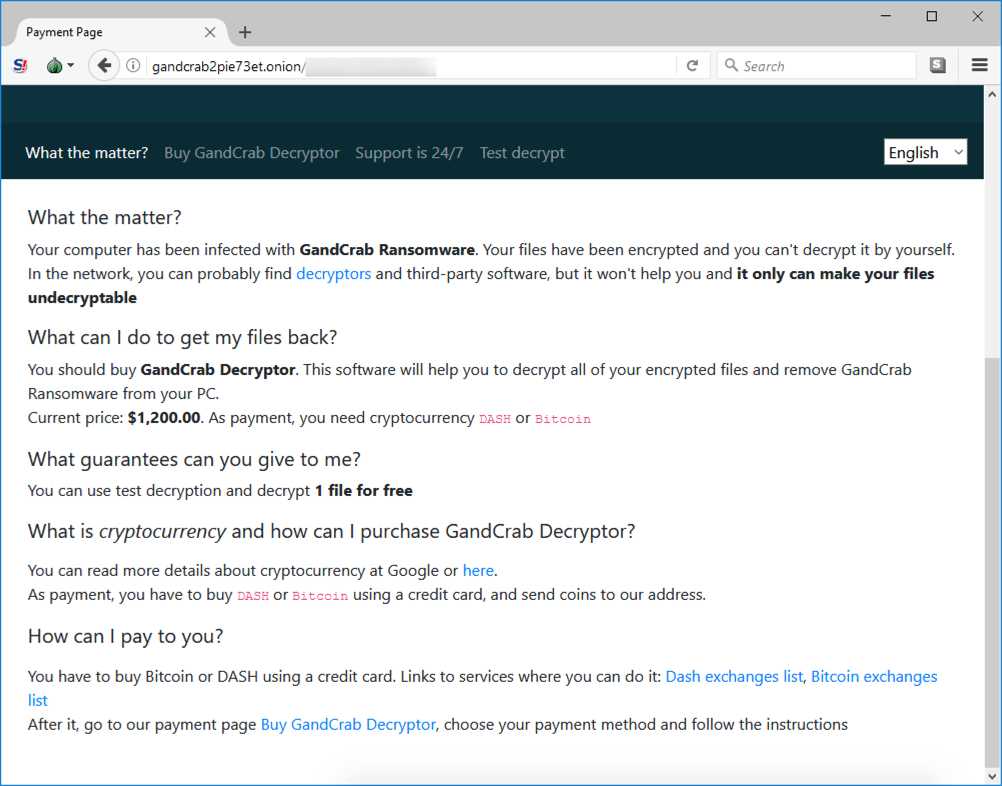
Shown above: GandCrab decryptor (2 of 2).
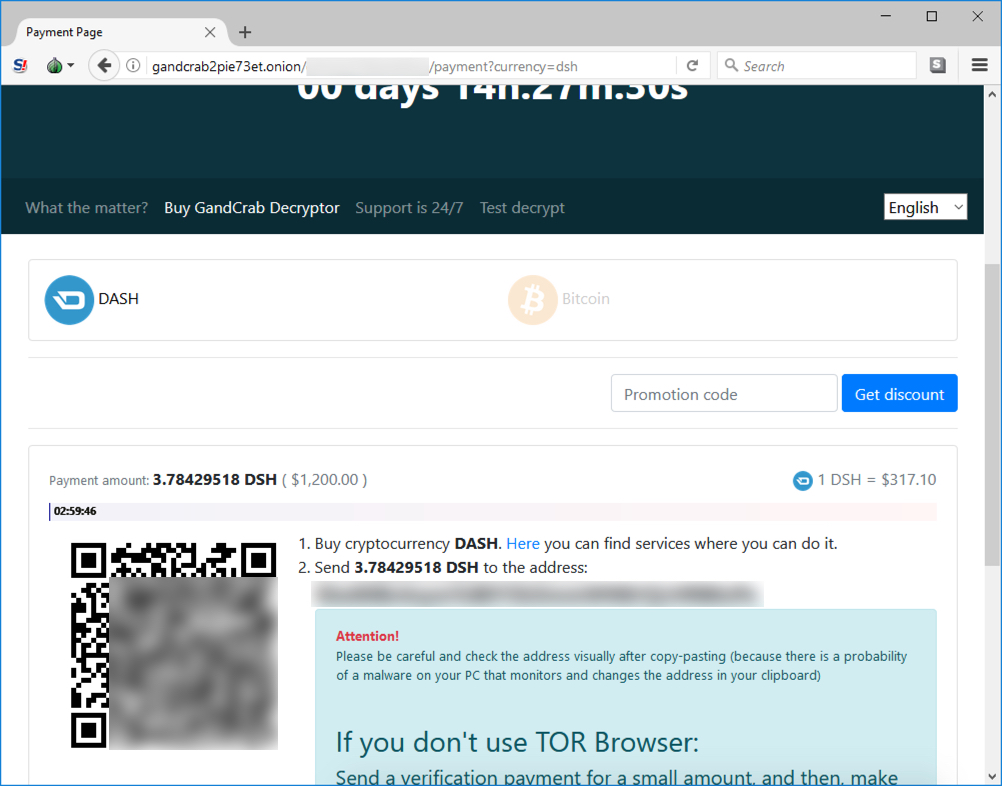
Shown above: GandCrab decryptor showing Dash method of payment.
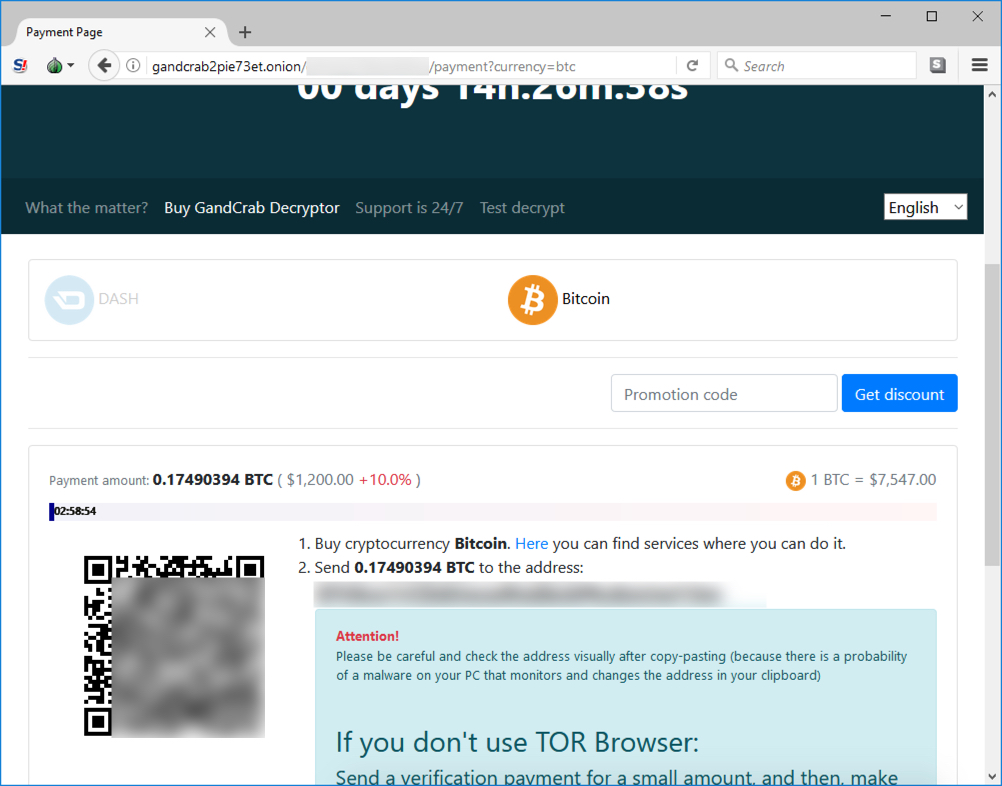
Shown above: GandCrab decryptor showing Bitcoin method of payment.
Click here to return to the main page.
