2018-06-14 - EMOTET INFECTION WITH TRICKBOT (GTAG: DEL8)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-14-Emotet-malspam-22-examples.zip 295 kB (294,745 bytes)
- 2018-06-14-Emotet-malspam-1137-UTC.eml (161,938 bytes)
- 2018-06-14-Emotet-malspam-1349-UTC.eml (1,351 bytes)
- 2018-06-14-Emotet-malspam-1356-UTC.eml (912 bytes)
- 2018-06-14-Emotet-malspam-1423-UTC.eml (869 bytes)
- 2018-06-14-Emotet-malspam-1429-UTC.eml (928 bytes)
- 2018-06-14-Emotet-malspam-1519-UTC.eml (166,466 bytes)
- 2018-06-14-Emotet-malspam-1642-UTC.eml (1,769 bytes)
- 2018-06-14-Emotet-malspam-1647-UTC.eml (1,626 bytes)
- 2018-06-14-Emotet-malspam-1649-UTC.eml (1,299 bytes)
- 2018-06-14-Emotet-malspam-1657-UTC.eml (1,646 bytes)
- 2018-06-14-Emotet-malspam-1702-UTC.eml (1,689 bytes)
- 2018-06-14-Emotet-malspam-1713-UTC.eml (1,176 bytes)
- 2018-06-14-Emotet-malspam-1722-UTC.eml (1,117 bytes)
- 2018-06-14-Emotet-malspam-1731-UTC.eml (1,757 bytes)
- 2018-06-14-Emotet-malspam-1845-UTC.eml (1,344 bytes)
- 2018-06-14-Emotet-malspam-1943-UTC.eml (1,795 bytes)
- 2018-06-14-Emotet-malspam-1946-UTC.eml (1,681 bytes)
- 2018-06-14-Emotet-malspam-2004-UTC.eml (1,307 bytes)
- 2018-06-14-Emotet-malspam-2057-UTC.eml (168,514 bytes)
- 2018-06-14-Emotet-malspam-2103-UTC.eml (1,803 bytes)
- 2018-06-14-Emotet-malspam-2121-UTC.eml (176,153 bytes)
- 2018-06-14-Emotet-malspam-2151-UTC.eml (1,735 bytes)
- 2018-06-14-Emotet-infection-with-Trickbot.pcap.zip 15.3 MB (15,255,470 bytes)
- 2018-06-14-Emotet-infection-with-Trickbot.pcap (16,313,354 bytes)/li>
- 2018-06-14-malware-associated-with-Emotet-infection.zip 666 kB (666,095 bytes)
- 2018-06-14-Emotet-malware-binary.exe (330,752 bytes)
- 2018-06-14-Trickbot-gtag-del8.exe (457,216 bytes)
- 2018-06-14-attached-PDF-document-1-of-4.pdf (2,692 bytes)
- 2018-06-14-attached-PDF-document-2-of-4.pdf (2,617 bytes)
- 2018-06-14-attached-PDF-document-3-of-4.pdf (7,734 bytes)
- 2018-06-14-attached-PDF-document-4-of-4.pdf (7,702 bytes)
- 2018-06-14-attached-Word-doc-with-macro-for-Emotet-1-of-4.doc (121,856 bytes)
- 2018-06-14-attached-Word-doc-with-macro-for-Emotet-2-of-4.doc (116,224 bytes)
- 2018-06-14-attached-Word-doc-with-macro-for-Emotet-3-of-4.doc (119,808 bytes)
- 2018-06-14-attached-Word-doc-with-macro-for-Emotet-4-of-4.doc (116,480 bytes)
- 2018-06-14-downloaded-Word-doc-with-macro-for-Emotet.doc (105,728 bytes)
NOTES:
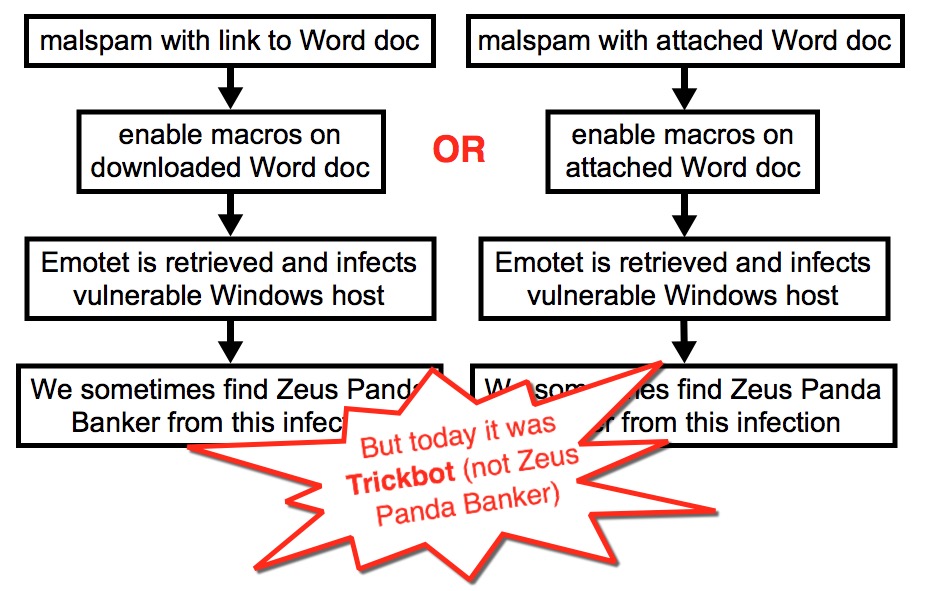
- Today I found 22 examples of malspam pushing Emotet malware.
- I occasionally see Emotet grab Zeus Panda Banker after the initial infection.
- Today, instead of Zeus Panda Banker, Emotet grabbed Trickbot (gtag: del8).
Shown above: Sometimes there's also a PDF document with an attached Word document. In this case, the PDF documents were harmless.
WEB TRAFFIC BLOCK LIST
The following are URLs on legitimate (but compromised) websites serving Emotet Word docs or malware:
- hxxp[:]//mentalmadam[.]com/IRS-Accounts-Transcipts-June-2018-08/91/
- hxxp[:]//minami[.]com[.]tw/IRS-Letters-June-2018-6438/
- hxxp[:]//ryleco[.]com/wp-content/IRS-Transcripts-June-2018-3982/
- hxxp[:]//synergycapital[.]jp/IRS-Tax-Transcipts-062018-042/59/
- hxxp[:]//wbauer[.]com[.]br/IRS-Tax-Transcipts-08/2/
- hxxp[:]//www.abolitionawards[.]com/IRS-Tax-Transcipts-June-2018-058/81/
- hxxp[:]//www.arisetransportation[.]org/IRS-Tax-Transcipts-June-2018-05W/5/
- hxxp[:]//www.azinkart[.]com/IRS-Accounts-Transcipts-00/82/
- hxxp[:]//www.becsystem[.]com[.]tr/IRS-Transcripts-062018-08U/5/
- hxxp[:]//www.chuyenmicro[.]com/ACCOUNT/Invoice-912306/
- hxxp[:]//www.coimbragarcia.adv[.]br/IRS-Tax-Transcipts-June-2018-017/35/
- hxxp[:]//www.decaexpress[.]cl/DOC/Invoices/
- hxxp[:]//www.estepona.dpsoft[.]es/IRS-Letters-062018-956/
- hxxp[:]//www.fieldhockeytravel[.]nl/IRS-Letters-458/
- hxxp[:]//www.harjuinvest.ee/IRS-TRANSCRIPTS-272/
- hxxp[:]//www.horcharoen[.]com/IRS-Tax-Transcipts-062018-871/
- hxxp[:]//www.iphoneteknikservisim[.]net/Client/Invoice-804288/
- hxxp[:]//xn--yyc-jk4buiz50r[.]com/IRS-TRANSCRIPTS-062018-0889/
- hxxp[:]//www.ipgce[.]com/bgj7/
EMAILS
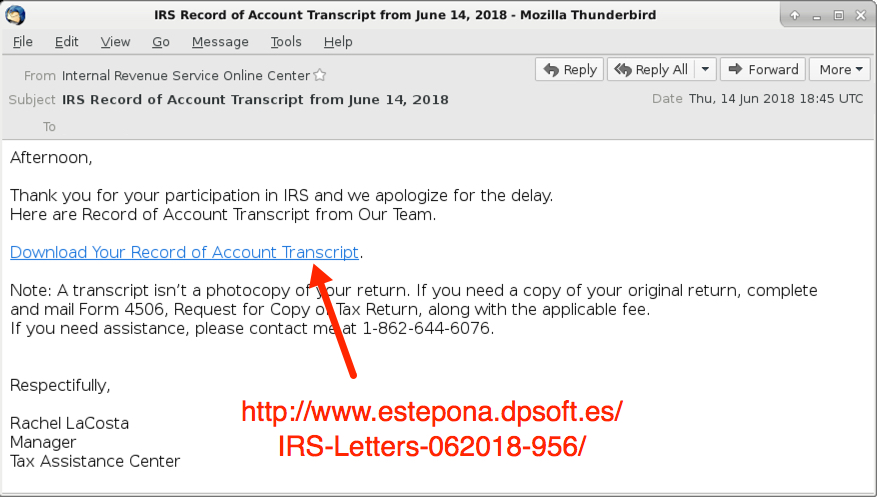
Shown above: Example of the IRS-themed Emotet malspam from today.
DATA FROM 22 EMAIL EXAMPLES OF THE MALSPAM:
- Received: from 10.0.0[.]4 ([124.253.157[.]231])
- Received: from 10.0.0[.]6 ([110.39.189[.]42])
- Received: from 10.0.0[.]6 ([113.140.16[.]77])
- Received: from 10.0.0[.]6 ([201.119.200[.]90])
- Received: from 10.0.0[.]12 ([187.146.55[.]14])
- Received: from 10.0.0[.]16 ([189.223.126[.]226])
- Received: from 10.0.0[.]21 ([109.127.42[.]221])
- Received: from 10.0.0[.]27 ([221.163.32[.]101])
- Received: from 10.0.0[.]28 ([82.219.199[.]27])
- Received: from 10.0.0[.]36 ([190.90.247[.]20])
- Received: from 10.0.0[.]37 ([221.163.32[.]101])
- Received: from 10.0.0[.]39 ([187.194.192[.]252])
- Received: from 10.0.0[.]39 ([189.203.27[.]175])
- Received: from 10.0.0[.]40 ([105.255.193[.]110])
- Received: from 10.0.0[.]42 ([201.229.32[.]86])
- Received: from 10.0.0[.]44 ([82.219.199[.]27])
- Received: from 10.0.0[.]46 ([91.224.6[.]137])
- Received: from 10.0.0[.]48 ([73.110.103[.]3])
- Received: from 10.0.0[.]48 ([81.138.171[.]89])
- Received: from 10.0.0[.]52 ([189.226.230[.]249])
- Received: from 10.0.0[.]53 ([221.163.32[.]101])
- Received: from 10.0.0[.]56 ([90.86.187[.]161])
SPOOFED SENDERS:
- From: Aceль A
- From: Bill Baker
- From: Engr. Abdul Rauf
- From: Future Lines
- From: Internal Revenue Service
- From: Internal Revenue Service Online
- From: Internal Revenue Service Online Center
- From: IRS
- From: IRS <irsonline@treasury[.]gov>
- From: IRS <Transcript@treasury[.]gov>
- From: IRS Online Center
- From: IRS[.]gov
- From: JSPL E Procurement System .
SUBJECT LINES:
- Subject: Record of Account Transcript from June 14, 2018
- Subject: Tax Account Transcript from June 14, 2018
- Subject: Verification of Non-filing Letter
- Subject: Verification of Non-filing Letter from 06/15/2018
- Subject: Wage and Income Transcript
- Subject: IRS Record of Account Transcript
- Subject: IRS Record of Account Transcript from 06/14/2018
- Subject: IRS Record of Account Transcript from June 14, 2018
- Subject: IRS Record of Account Transcript from June 15, 2018
- Subject: IRS Tax Account Transcript
- Subject: IRS Tax Account Transcript from June 15, 2018
- Subject: IRS Tax Return Transcript
- Subject: IRS Verification of Non-filing Letter from June 14, 2018
- Subject: IRS Wage and Income Transcript
- Subject: IRS Wage and Income Transcript from 06/14/2018
- Subject: Engr. Abdul Rauf Invoice 8288592
- Subject: New Invoice / WM2708 / RP# 09648
- Subject: New Payroll Co.
- Subject: Pay Invoice
- Subject: Payroll Tax Payment
ATTACHMENT NAMES (IN EMAILS THAT ONLY HAD ATTACHMENTS):
- Attachment name: IRS_225078136_06152018.doc
- Attachment name: IRS_6957681_06152018.doc
- Attachment name: New Payroll Co..pdf
- Attachment name: New Payroll Co..doc
- Attachment name: Payroll Tax Payment.pdf
- Attachment name: Payroll Tax Payment.doc
- Attachment name: Tax Account Transcript.pdf
- Attachment name: Verification of Non-filing Letter.pdf
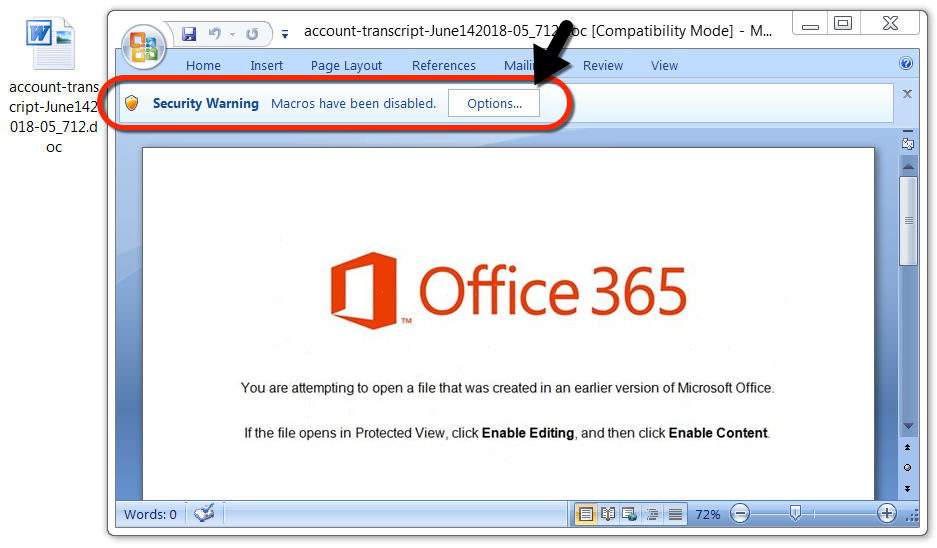
Shown above: One of the downloaded (or attached) Word docs.
INFECTION TRAFFIC
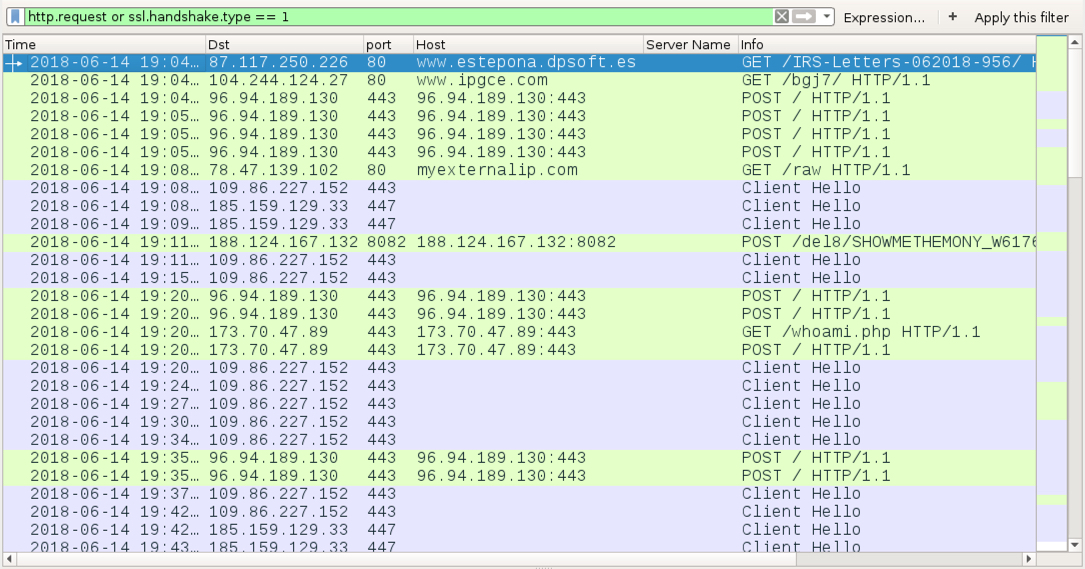
Shown above: Traffic from an infection filtered in Wireshark.
EMOTET INFECTION TRAFFIC:
- 87.117.250[.]226 port 80 - www.estepona.dpsoft[.]es - GET /IRS-Letters-062018-956/
- 104.244.124[.]27 port 80 - www.ipgce[.]com - GET /bgj7/
- 96.94.189[.]130 port 443 - 96.94.189[.]130:443 - POST /
- 173.70.47[.]89 port 443 - 173.70.47[.]89:443 - GET /whoami.php
- 173.70.47[.]89 port 443 - 173.70.47[.]89:443 - POST /
TRICKBOT INFECTION TRAFFIC:
- port 80 - myexternalip[.]com - GET /raw
- 109.86.227[.]152 port 443 - SSL/TLS traffic for Trickbot
- 185.159.129[.]33 port 447 - SSL/TLS traffic for Trickbot
- 188.124.167[.]132 port 8082 - 188.124.167[.]132:8082 - POST /del8/[long string]
- 104.193.252[.]163 port 443 - SSL/TLS traffic for Trickbot
MALWARE
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: a0b6594492b165a07bc81c0943abd49153aeaf7df72978a3e03ed95936153ecb
File size: 105,728 bytes
File name: [random file name].doc
File description: Word doc downloaded from link in one of the emails. Has macro to retreive Emotet.
- SHA256 hash: 5f3598e230c636e06eb292d7cb7180ad3d94d5c96c1f002d2d6c7fde198e0dda
File size: 330,752 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\[random file name].exe
File description: Emotet malware binary persistent on the infected Windows host
- SHA256 hash: f5a80ecd7f6641c99769d8712edf6215fb69755b0b61f9127ae096659715f5c3
File size: 457,216 bytes
File location: C:\Users\[username]\AppData\Roaming\comline\[random file name].exe
File description: Trickbot malware binary (gtag: del8) persistent on the infected Windows host
SHA256 HASHES FOR ATTACHED WORD DOCS IN 4 EMAILS FROM MY 22 MALSPAM SAMPLES:
- 2b41c64b33a9acbf9f5b1774106f12ba6ce8832ef516d52e522281a58b5a78f7 - 121,856 bytes
- 68f3c40093f70ef4523bf32ed36e6782f036e5730082134c62bbabdaf9ba18cb - 116,224 bytes
- b83601767c3baa5206721250a270fc051fa3f407d351d1b25e6d53937dff7048 - 116,480 bytes
- f34bc068ea3437a4fe2d45fa6b2f3e90082ab917db46017cb797f397e43d0e07 - 119,808 bytes
SHA256 HASHES FOR ATTACHED PDF DOCS IN 4 EMAILS FROM MY 22 MALSPAM SAMPLES:
- 2da1157e4288e59b89b052881e96f34ee58e0005ffa210f4cff620da16a8a11f - 7,734 bytes
- 81627d076589ec5c0e2231f7d363f1026dc92379d351dc4b1fe23a3832c39fe9 - 2,617 bytes
- 97d8d710fd96d198735c9adc4c44b5aa654f719d8bacd2b63073651ec4b6629f - 7,702 bytes
- e821e6d42456cd70db7ca78487c7209e6fb21d1ddf7f7b44bd950acd8c0b0a5b - 2,692 bytes
NOTE: These PDFs are all harmless. From what I can tell, they don't contain any malware or exploits.
IMAGES
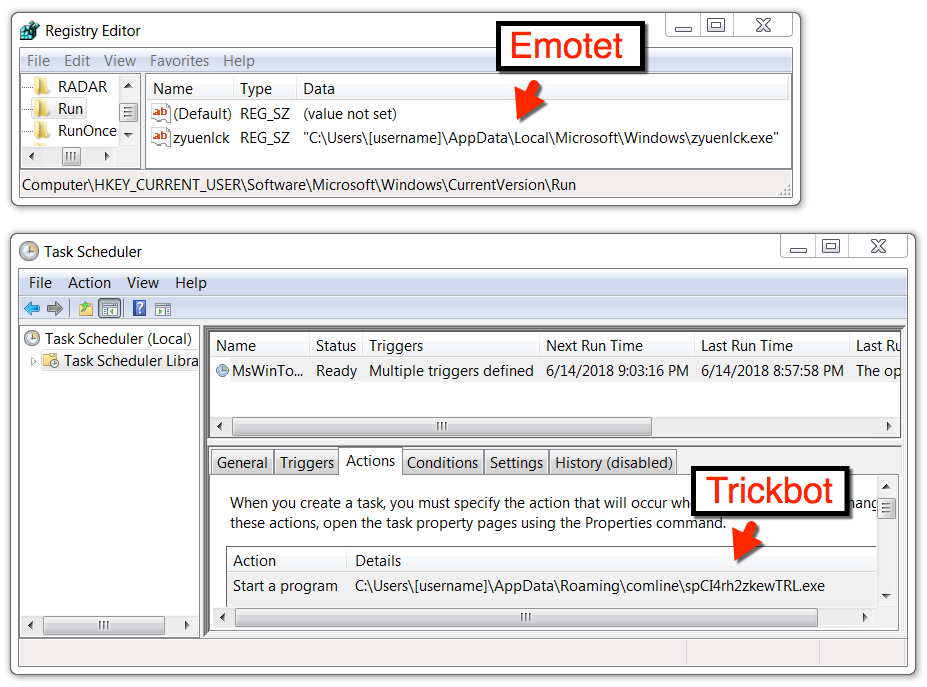
Shown above: Emotet made persistent through the registry and Trickbot through a scheduled task.
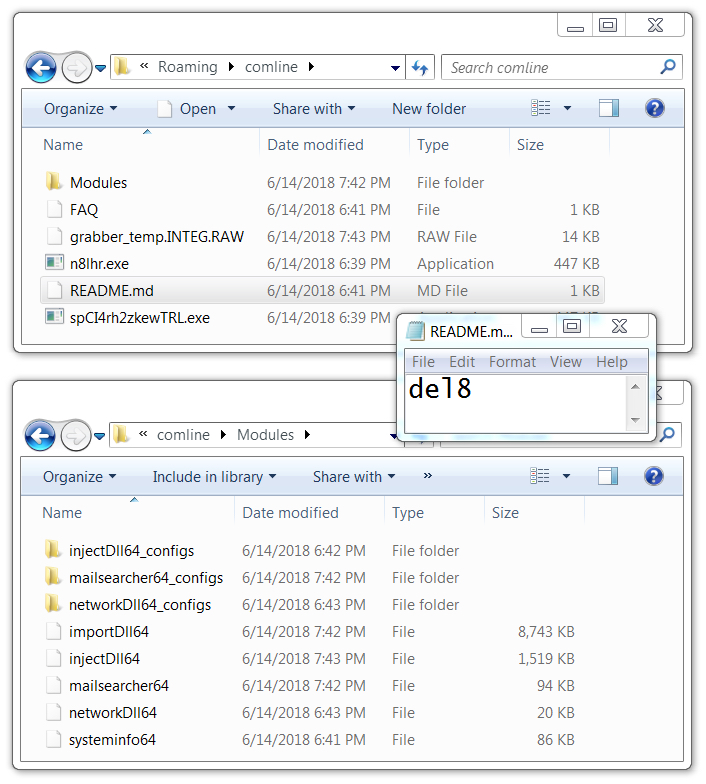
Shown above: Screenshot of directories with Trickbot malware/artifacts.
Click here to return to the main page.
