2018-06-18 - QUICK POST: EMOTET INFECTION WITH ICEDID
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-18-Emotet-malspam-9-examples.zip 157 kB (157,299 bytes)
- 2018-06-18-Emotet-malspam-1218-UTC.eml (780 bytes)
- 2018-06-18-Emotet-malspam-1239-UTC.eml (877 bytes)
- 2018-06-18-Emotet-malspam-1447-UTC.eml (895 bytes)
- 2018-06-18-Emotet-malspam-1448-UTC.eml (850 bytes)
- 2018-06-18-Emotet-malspam-1644-UTC.eml (843 bytes)
- 2018-06-18-Emotet-malspam-1712-UTC.eml (727 bytes)
- 2018-06-18-Emotet-malspam-1741-UTC.eml (875 bytes)
- 2018-06-18-Emotet-malspam-1928-UTC.eml (174,831 bytes)
- 2018-06-18-Emotet-malspam-2020-UTC.eml (169,517 bytes)
- 2018-06-18-pcaps-from-Emotet-infections.zip 1.8 MB (1,837,781 bytes)
- 2018-06-18-Emotet-infection-traffic-example-1-of-3.pcapp (367,086 bytes)/li>
- 2018-06-18-Emotet-infection-traffic-example-2-of-3.pcapp (346,489 bytes)/li>
- 2018-06-18-Emotet-infection-traffic-example-3-of-3.pcapp (1,283,477 bytes)/li>
- 2018-06-18-IcedID-sample-post-infection-traffic.pcap (333,315 bytes)/li>
- 2018-06-18-Emotet-and-IcedID-malware.zip 1.04 MB (1,036,580 bytes)
- 2018-06-18-downloaded-Word-doc-with-macro-for-Emotet-sample-1-of-3.doc (128,000 bytes)
- 2018-06-18-downloaded-Word-doc-with-macro-for-Emotet-sample-2-of-3.doc (124,672 bytes)
- 2018-06-18-downloaded-Word-doc-with-macro-for-Emotet-sample-3-of-3.doc (114,176 bytes)
- 2018-06-18-Emotet-malware-binary-sample-1-of-3.exe (192,512 bytes)
- 2018-06-18-Emotet-malware-binary-sample-2-of-3.exe (190,464 bytes)
- 2018-06-18-Emotet-malware-binary-sample-3-of-3.exe (190,464 bytes)
- 2018-06-18-follow-up-IcedID-malware-seen-during-Emotet-infection.exe (580,096 bytes)
NOTES:
- Today, instead of seeing Trickbot or Zeus Panda Banker after my Emotet malspam infection, I saw IcedID banking malware.
- I had to run the IcedID on another Windows host before it executed properly.
- See the images below for details on the IcedID infection.
- Thanks to @mesa_matt for identifying the IcedID sample, when I had trouble figuring out what it was (Twitter thread).
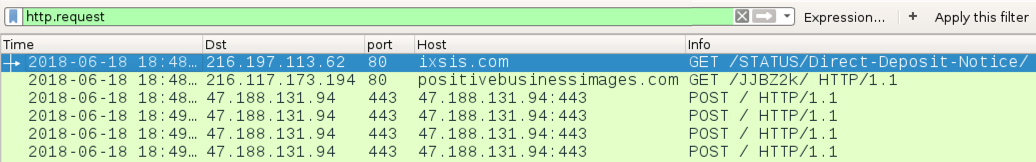
Shown above: Traffic from an Emotet infection filtered in Wireshark.
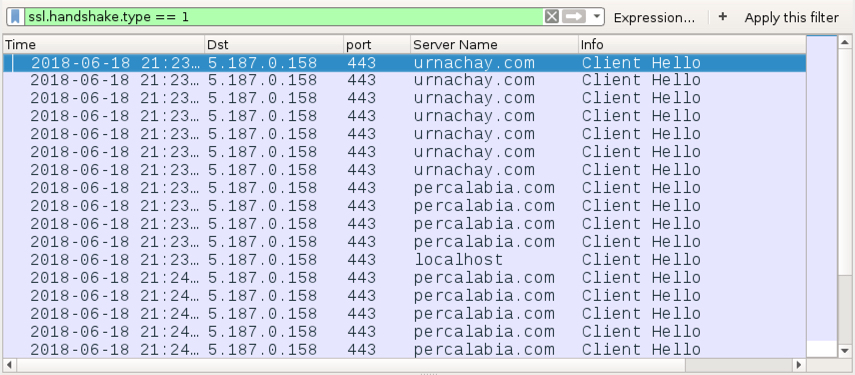
Shown above: Traffic generated by the IcedID sample from the infected Windows host.
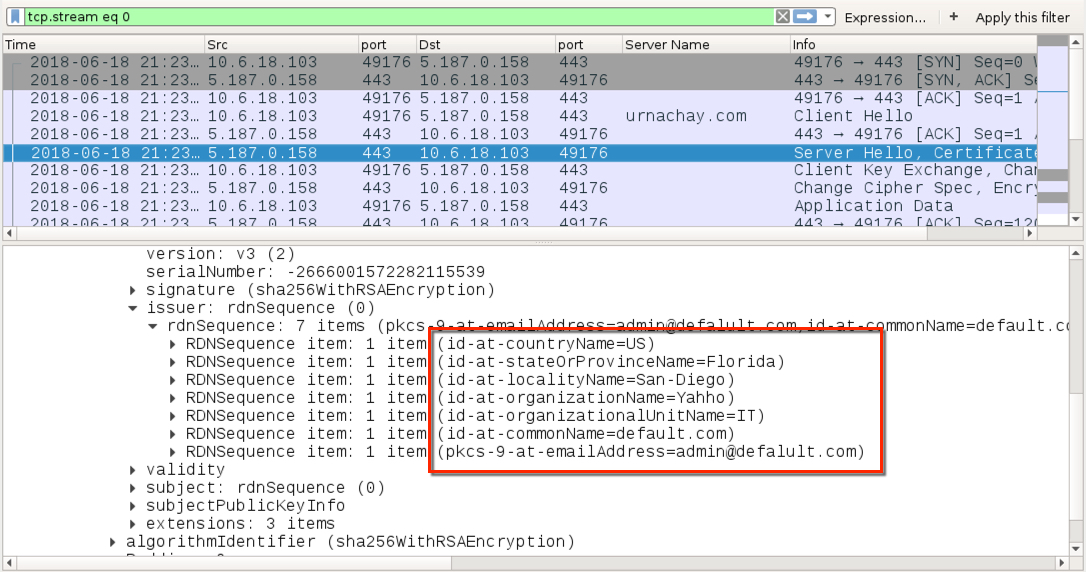
Shown above: Certificate data from IcedID post-infection domain urnachay.com.
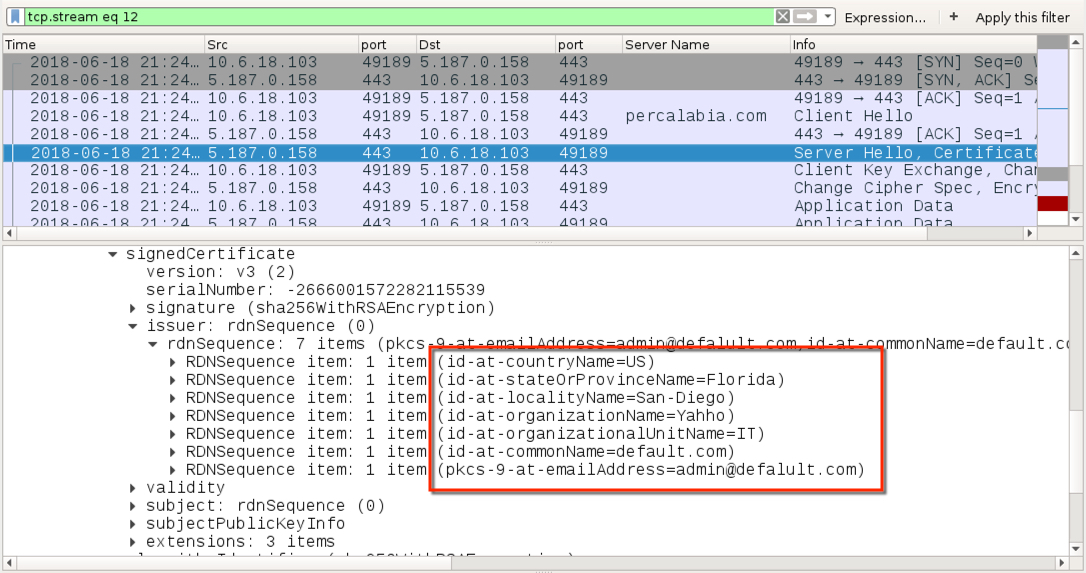
Shown above: Certificate data from IcedID post-infection domain percalabia.com.
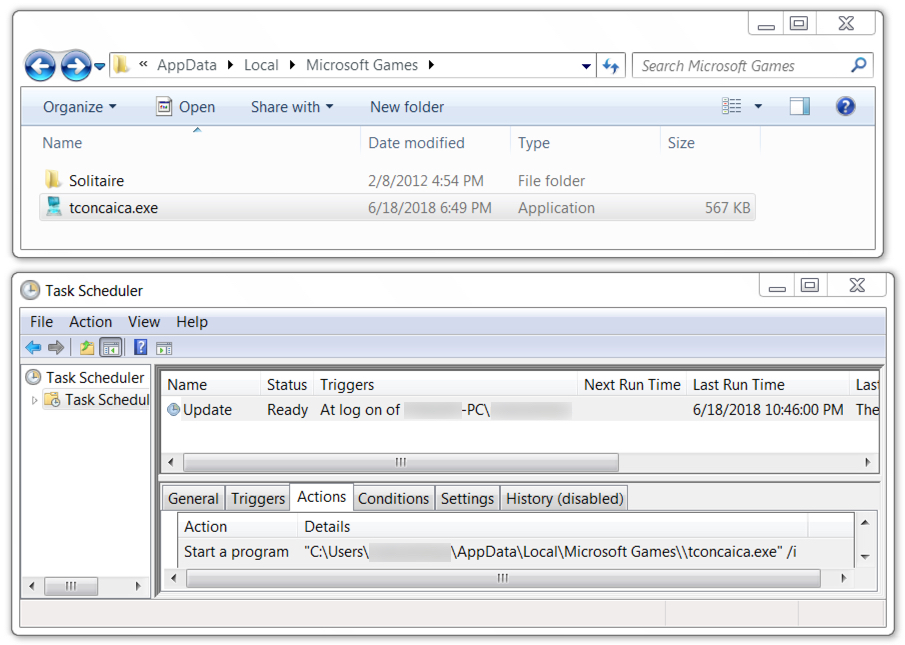
Shown above: IcedID banking malware persistent on the infected host.
Click here to return to the main page.
