2018-06-20 - MALSPAM PUSHES EMOTET & EMOTET PUSHES ICEDID (AGAIN)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-20-Emotet-malspam-101-email-examples.txt.zip 17.4 kB (17,384 bytes)
- 2018-06-20-Emotet-IOCs-and-notes.txt.zip 6.8 kB (6,782 bytes)
- 2018-06-20-Emotet-malware-and-artifacts.zip 647 kB (647,418 bytes)
- 2018-06-20-Emotet-infection-traffic-both-pcaps.zip 3.3 MB (3,253,793 bytes)
NOTES:
- This one is a quick post. IOCs are in one of the above archives.
- I generated 2 pcaps of infection traffic.
- One pcap is as a normal home user on an isolated Windows host.
- The other pcap is on a Windows client logged into a domain controller in an Active Directory (AD) environment.
- Today, I only saw IcedID in the pcap with the AD environment.
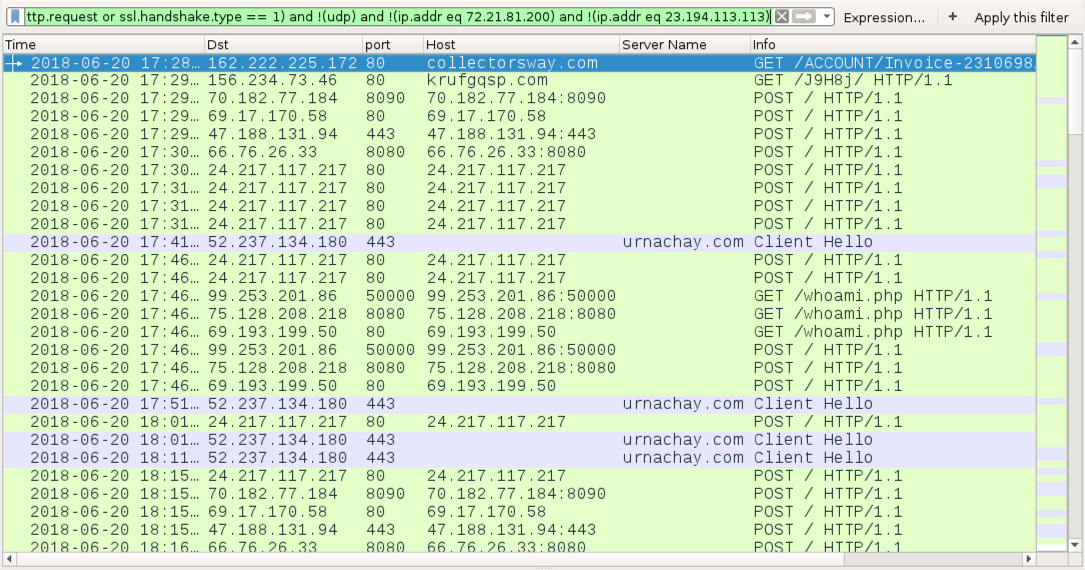
Shown above: Traffic from an infection filtered in Wireshark.
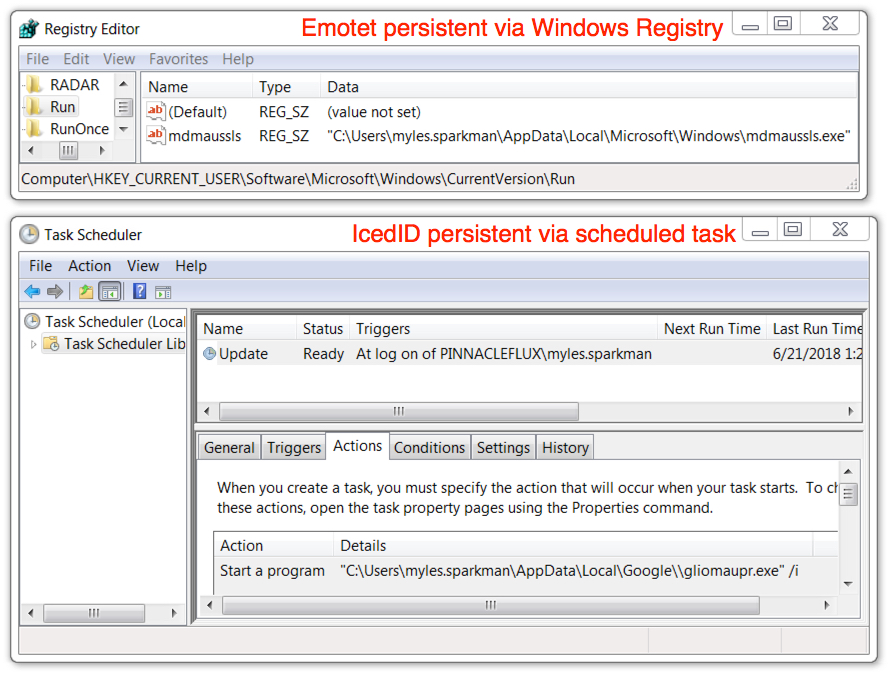
Shown above: Malware from this infection persistent on the infected Windows host.
Click here to return to the main page.
