2018-06-26 - QUICK POST: EMOTET INFECTION WITH ICEDID
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-26-ten-examples-of-Emotet-malspam.txt.zip 2.6 kB (2,617 bytes)
- 2018-06-26-Emotet-infection-with-IcedID-in-AD-environment.pcap.zip 2.9 MB (2,923,730 bytes)
- 2018-06-26-malware-from-Emotet-with-IcedID-infection.zip 634 kB (633,709 bytes)
NOTES:
- This infection was generated in an Active Directory environment. The network parameters are:
- LAN segment: 172.16.5[.]0/24
- Gateway: 172.16.5[.]1
- Broadcast address: 172.16.5[.]255
- Domain controller IP address: 172.16.5[.]9
- Domain controller host name: RAPTOR-NAV-DC
- Domain name: raptor-nav[.]com
- Windows client IP address: 172.16.5[.]195
- Windows client host name: Snow-Patrol-PC
- Windows client user account name: raymundo.snow
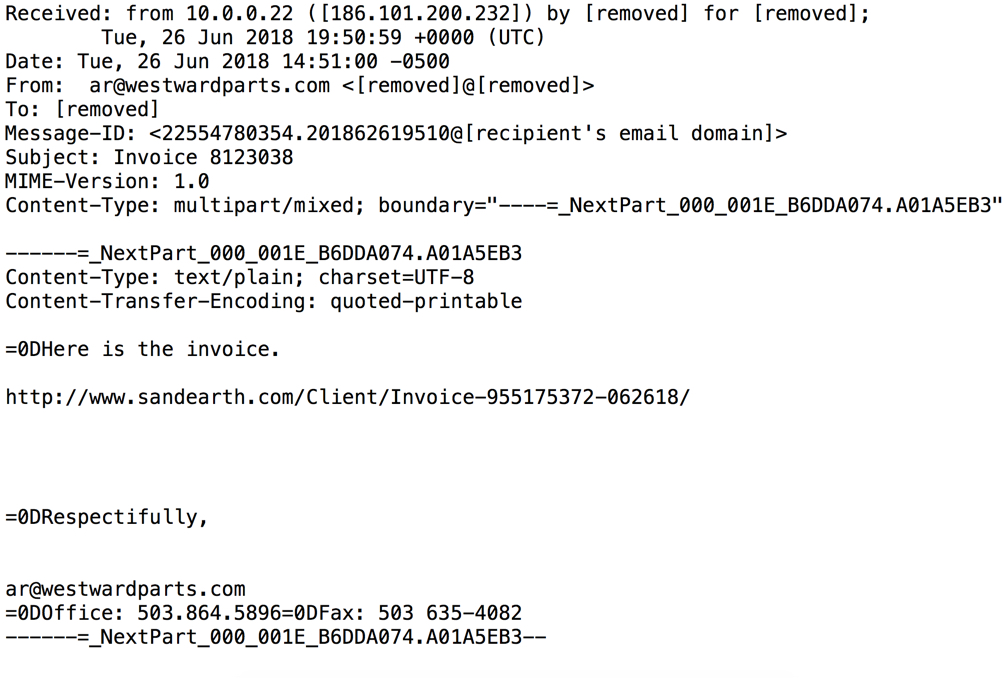
Shown above: One of the emails in raw plain text (.eml format).
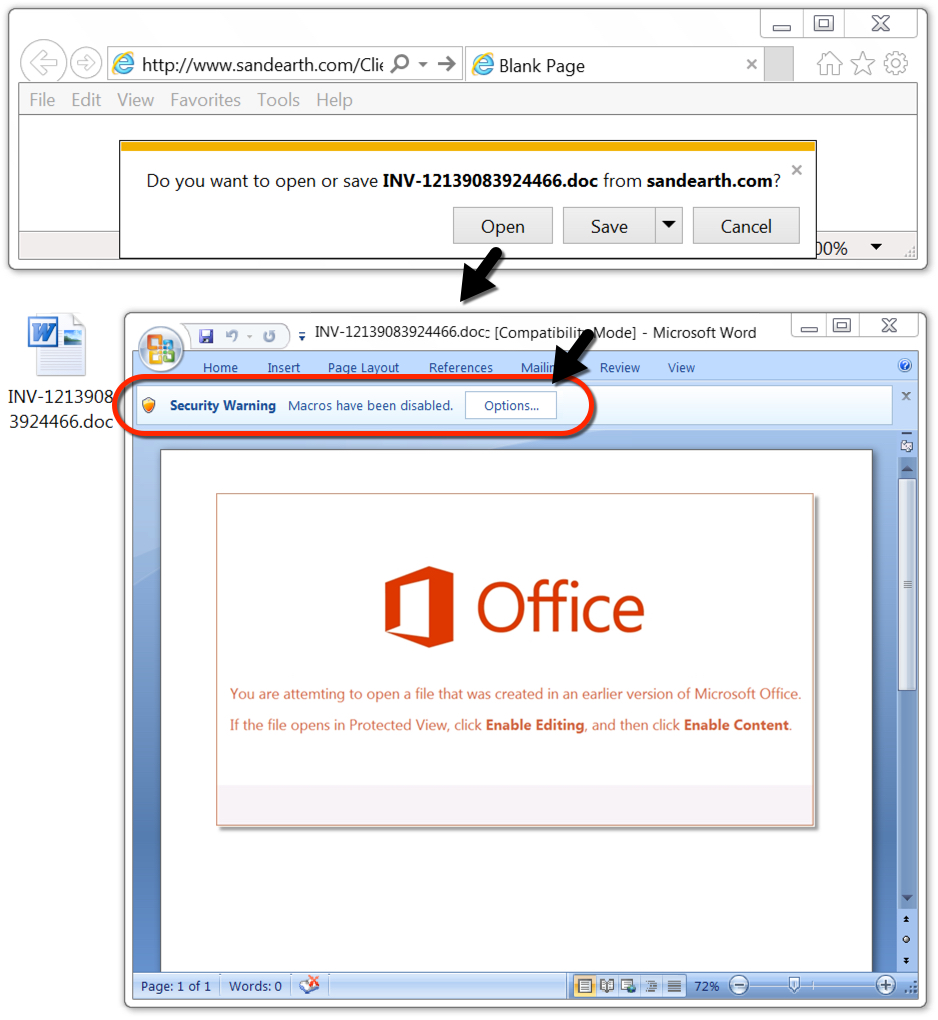
Shown above: Example of a Word document from link in the malspam.
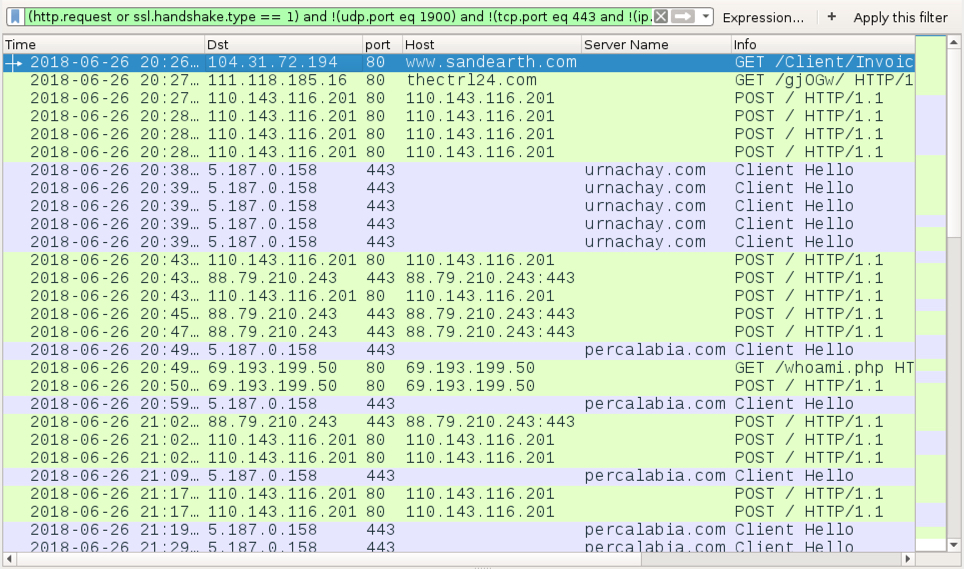
Shown above: Traffic from the infection filtered in Wireshark.
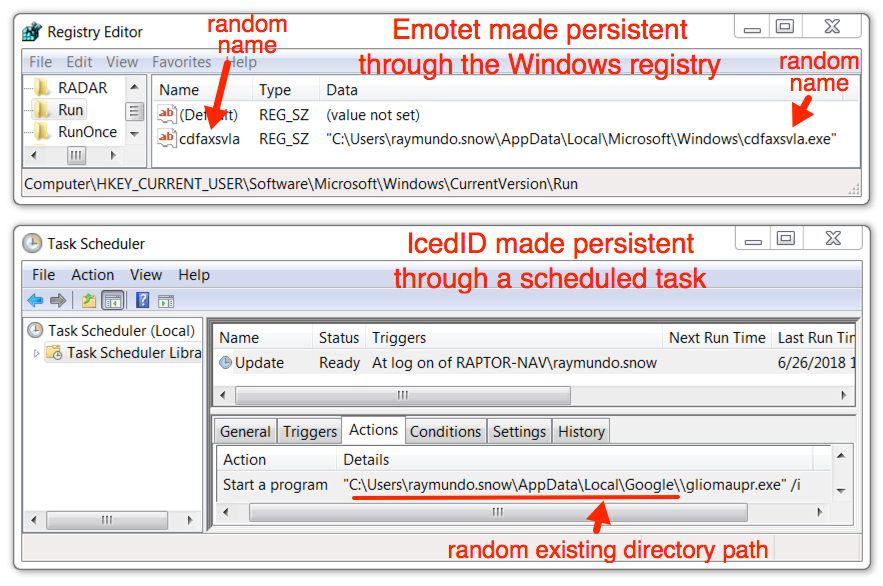
Shown above: Malware persistent on the infected Windows host.
Click here to return to the main page.
