2018-06-30 - TRAFFIC ANALYSIS EXERCISE - SORTING THROUGH THE ALERTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2018-06-30-traffic-analysis-exercise.pcap.zip 34.7 MB (34,657,778 bytes)
- Zip archive of the alerts: 2018-06-30-traffic-analysis-exercise-alerts.zip 283 kB (283,380 bytes)
SCENARIO
You're an analyst at a Security Operations Center (SOC) monitoring the Security Information and Events Manager (SIEM). The SIEM indicates suspicious activity on a host in your network at 172.16.2[.]169. You decide this activity requires further investigation.
In order to determine what happened, you retreive data on the associated events, and you acquire a pcap of network traffic from 172.16.2[.]169 during that timeframe. Characteristics of your network are:
- LAN segment: 172.16.2[.]0/24 (172.16.2[.]0 through 172.16.2[.]255)
- Broadcast address: 172.16.2[.]255
- Domain controller: 172.16.2[.]9 (FabulousDuke-DC)
- Domain: fabulousdukes[.]com
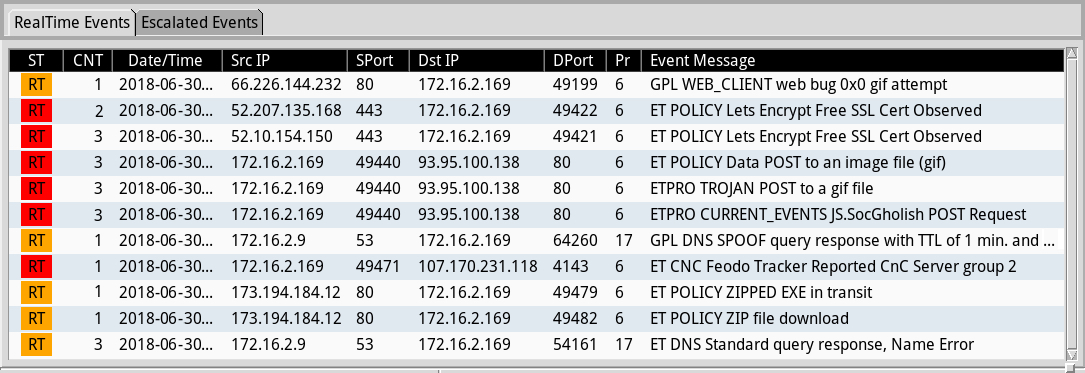
Shown above: The events for 172.16.2[.]169 as seen in Sguil on Security Onion using the EmergingThreats Pro ruleset.
YOUR TASK
Your task is to figure out what happened. You should also determine if the host at 172.16.2[.]169 was actually infected. One of the zip archives for this exercise conains details of the alerts, and it includes associated IP addresses, ports, and times. Keep in mind that policy alerts are not necessarily malicious activity. If you write an incident report, it should include the following:
EXECUTIVE SUMMARY:
- Date/Time of the activity in UTC
- What happened
- Who it happened to
DETAILS:
- The internal IP address you're investigating: 172.16.2[.]169
- The MAC address for 172.16.2[.]169
- The Host name for 172.16.2[.]169
- The Windows account name, if 172.16.2[.]169 is a Windows host
INDICATORS:
- List the IP addresses, ports, and domains directly related to any malicious activity you can verify from the pcap.
ANSWERS
- Click here for the answers.
Click here to return to the main page.
