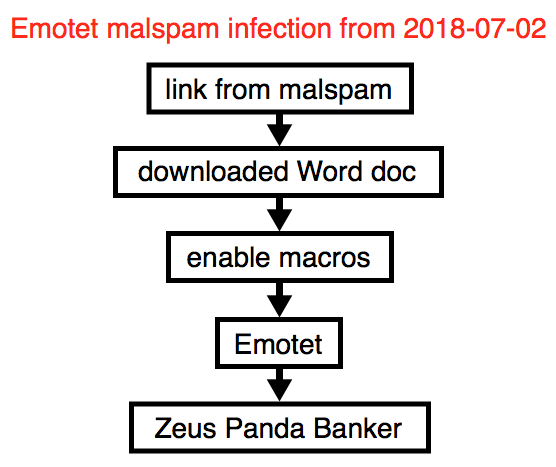
2018-07-02 - EMOTET INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-02-Emotet-malspam-16-examples.txt.zip 4.8 kB (4,755 bytes)
- 2018-07-02-Emotet-malspam-16-examples.txt (15,796 bytes)
- 2018-07-02-Emotet-infection-with-Zeus-Panda-Banker.pcap.zip 4.6 MB (4,620,324 bytes)
- 2018-07-02-Emotet-infection-with-Zeus-Panda-Banker.pcap (5,303,730 bytes)/li>
- 2018-07-02-malware-associated-with-Emotet-infection.zip 542 kB (542,110 bytes)
- 2018-07-02-downloaded-Word-doc-with-macro-for-Emotet.doc (232,192 bytes)
- 2018-07-02-Emotet-malware-binary-1-of-2.exe (208,896 bytes)
- 2018-07-02-Emotet-malware-binary-2-of-2.exe (203,776 bytes)
- 2018-07-02-Zeus-Panda-Banker-caused-by-Emotet.exe (223,744 bytes)
NOTES:
- Generated this infection in an Active Directory (AD) environment, just to see if anything unusual happened.
- So the traffic in today's pcap is a little messier than in my normal blog posts.
- From what I can tell, nothing unusual happened, other than the expected infection traffic.
Shown above: Chain of events for today's infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domain:
- hxxp[:]//all4mums[.]ru/Client/Past-Due-invoice/
- hxxp[:]//chinaspycam[.]com/includes/languages/english/html_includes/En/DOC/Account-20064/
- hxxp[:]//chouett-vacances[.]com/Payment-and-address/Invoice-70195027-070118/
- hxxp[:]//cqfsbj[.]cn/DOC/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//minami[.]com[.]tw/DOC/Account-55907/
- hxxp[:]//nagoyamicky[.]com/cacheqblog/Payment-and-address/Invoice-3838804/
- hxxp[:]//own-transport[.]com/pub/OVERDUE-ACCOUNT/tracking-number-and-invoice-of-your-order/
- hxxp[:]//www.caglarturizm[.]com[.]tr/INVOICE-STATUS/Please-pull-invoice-47924/
- hxxp[:]//www.customaccessdatabase[.]com/En/Purchase/HRI-Monthly-Invoice/
- hxxp[:]//www.gracetexpro[.]com/Greeting-eCard/
- hxxp[:]//www.jxprint[.]ru/Order/Payment/
- hxxp[:]//www.legionofboomfireworks[.]com/Statement/Direct-Deposit-Notice/
- hxxp[:]//www.marcoantoniocasares[.]com/Purchase/Pay-Invoice/
- hxxp[:]//www.perezdearceycia.cl/wp-content/FILE/Invoice-23382229-070218/
- hxxp[:]//www.sewamobilbengkulu.web[.]id/4th-July-2018/
- hxxp[:]//zlc-aa[.]org/New-Order-Upcoming/588052/
- hxxp[:]//clubvolvoitalia[.]it/r3z6/
- hxxp[:]//ericconsulting[.]com/7I3eUNF/
- hxxp[:]//www.goldenfell[.]ru/media/5DzF30jL/
- hxxp[:]//jmamusical[.]jp/wordpress/wp-content/L8J0igh/
- hxxp[:]//www.mobsterljud[.]se/VJkuLg/
- hxxp[:]//74.79.26[.]193:990/whoami.php
- canariasmotor[.]top
EMAILS
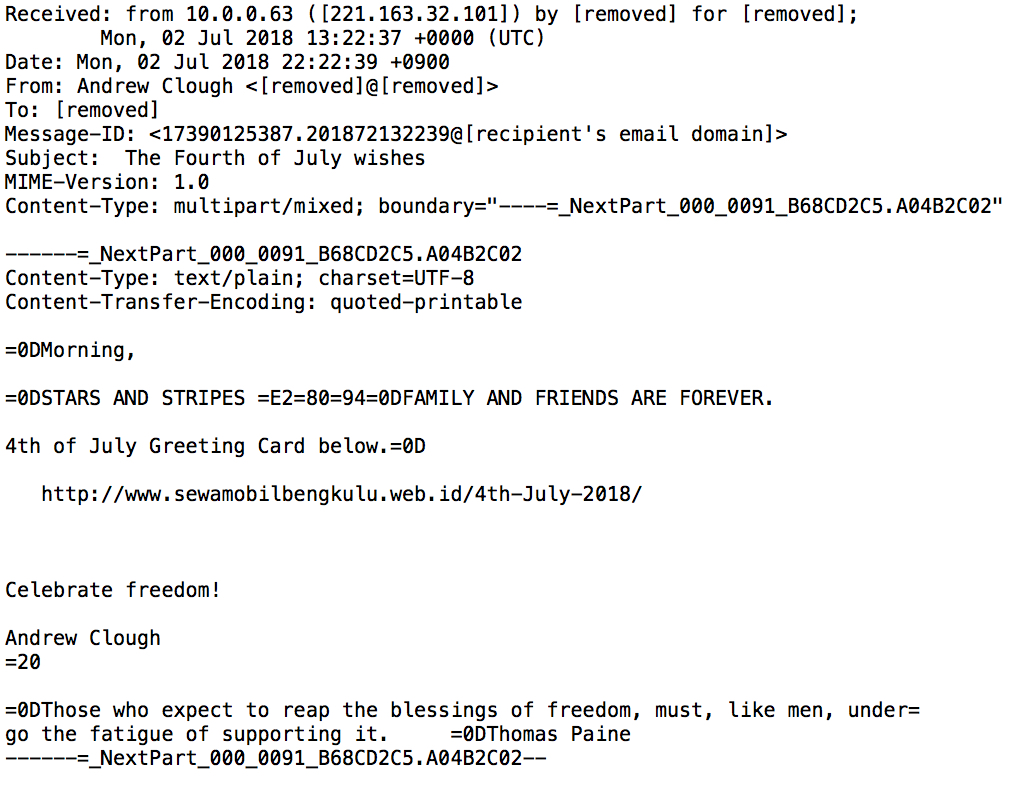
Shown above: Example of the malspam (raw text with headers and formatting).
DATA FROM 16 EMAIL EXAMPLES OF THE MALSPAM:
- Received: from ([80.14.105[.]108])
- Received: from ([103.55.69[.]138])
- Received: from ([137.59.225[.]35])
- Received: from ([196.250.41[.]105])
- Received: from ([221.163.32[.]101])
- Received: from 10.0.0[.]0 ([119.148.37[.]228])
- Received: from 10.0.0[.]16 ([211.221.155[.]202])
- Received: from 10.0.0[.]20 ([117.240.219[.]106])
- Received: from 10.0.0[.]28 ([189.194.248[.]28])
- Received: from 10.0.0[.]28 ([220.249.72[.]99])
- Received: from 10.0.0[.]30 ([221.163.32[.]101])
- Received: from 10.0.0[.]36 ([14.51.231[.]1])
- Received: from 10.0.0[.]40 ([187.144.210[.]26])
- Received: from 10.0.0[.]49 ([122.160.85[.]51])
- Received: from 10.0.0[.]59 ([90.86.57[.]136])
- Received: from 10.0.0[.]63 ([221.163.32[.]101])
SPOOFED SENDERS:
- From: alexa.ballantine@gmail[.]com <[spoofed sending email address]>
- From: Jamacapq@sbcglobal[.]net <[spoofed sending email address]>
- From: ramakrishna3sbc32@gmail[.]com <[spoofed sending email address]>
- From: Amanda Fisher <[spoofed sending email address]>
- From: Andrew Clough <[spoofed sending email address]>
- From: andy <[spoofed sending email address]>
- From: Beacon Systems <[spoofed sending email address]>
- From: CYNTHIA HARRY <[spoofed sending email address]>
- From: Darren Hamm <[spoofed sending email address]>
- From: Kira Holden <[spoofed sending email address]>
- From: Marina Eckert <[spoofed sending email address]>
- From: Mike Andrews <[spoofed sending email address]>
- From: Phil Gibson <[spoofed sending email address]>
- From: Priyanka Kapadia <[spoofed sending email address]>
- From: robert biggs <[spoofed sending email address]>
- From: Terry Nelson <[spoofed sending email address]>
SUBJECT LINES:
- Subject: The Fourth of July wishes
- Subject: =?UTF-8?B?Vm9zIGZhY3R1cmVzIGltcGF5w6llcyBkdSAwMi8wNy8yMDE4ICMwMTUtNTgyMQ==?=
- Subject: Darren Hamm 4th of July Greeting Card
- Subject: Final Account
- Subject: INCORRECT INVOICE
- Subject: Invoice Number 13915
- Subject: Invoice Number 55057
- Subject: Invoice# 3988726
- Subject: Outstanding INVOICE FQOVN/2773110/730
- Subject: Outstanding INVOICE XOJR/7763411/6403
- Subject: Please send copy invoice
- Subject: RE: Outstanding INVOICE BIA/066250/5423
- Subject: RTZM3-9044531941
- Subject: Sales Invoice
- Subject: Seperate Remittance Advice Layout - paper document A4
- Subject: Votre facture du 02 juillet Nr. 08296866
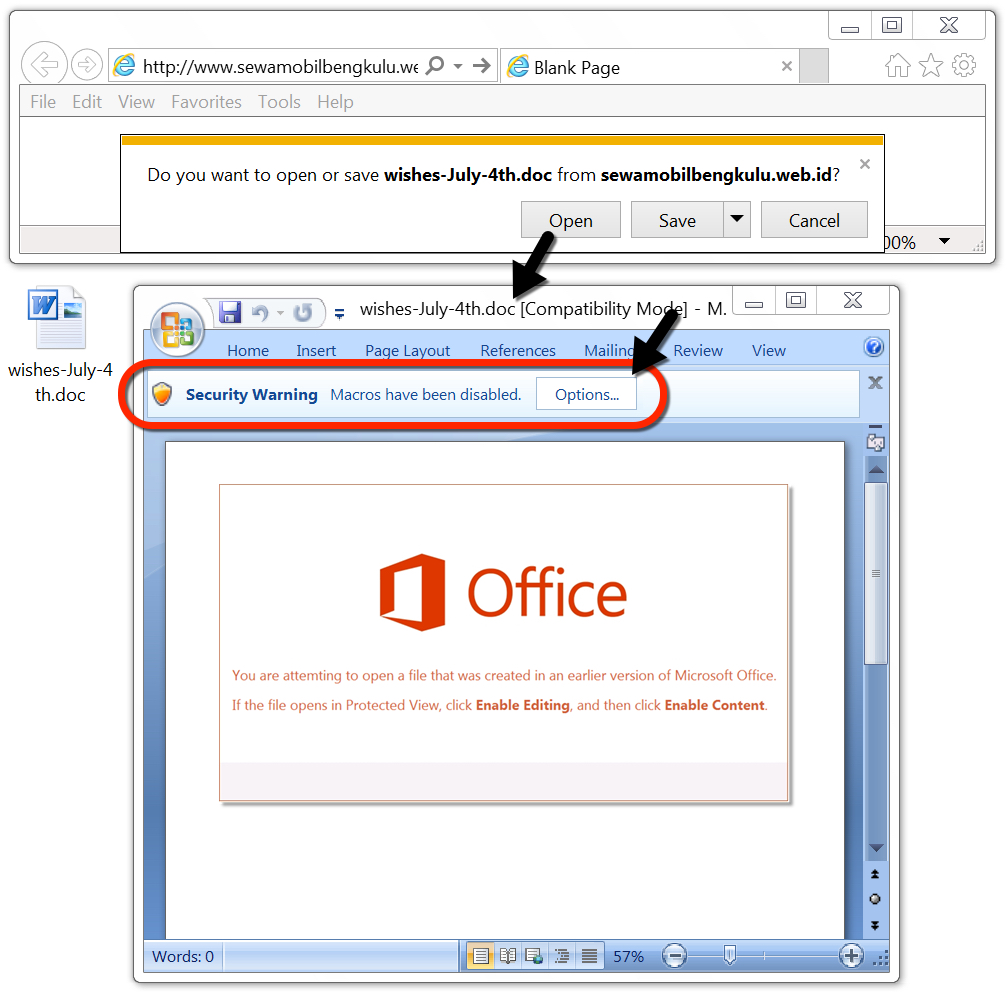
Shown above: Word doc generated from link in the malspam.
INFECTION TRAFFIC
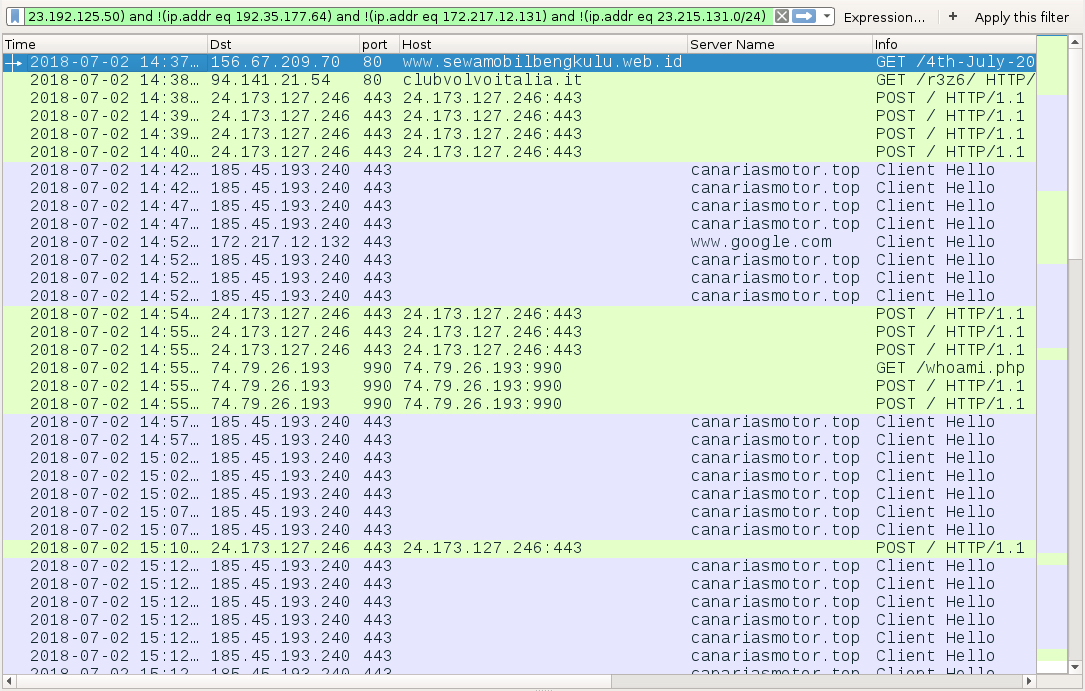
Shown above: Traffic from an infection filtered in Wireshark.
URLS FROM THE MALSPAM TO DOWNLOAD THE INITIAL WORD DOCUMENT:
- hxxp[:]//all4mums[.]ru/Client/Past-Due-invoice/
- hxxp[:]//chinaspycam[.]com/includes/languages/english/html_includes/En/DOC/Account-20064/
- hxxp[:]//chouett-vacances[.]com/Payment-and-address/Invoice-70195027-070118/
- hxxp[:]//cqfsbj[.]cn/DOC/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//minami[.]com[.]tw/DOC/Account-55907/
- hxxp[:]//nagoyamicky[.]com/cacheqblog/Payment-and-address/Invoice-3838804/
- hxxp[:]//own-transport[.]com/pub/OVERDUE-ACCOUNT/tracking-number-and-invoice-of-your-order/
- hxxp[:]//www.caglarturizm[.]com[.]tr/INVOICE-STATUS/Please-pull-invoice-47924/
- hxxp[:]//www.customaccessdatabase[.]com/En/Purchase/HRI-Monthly-Invoice/
- hxxp[:]//www.gracetexpro[.]com/Greeting-eCard/
- hxxp[:]//www.jxprint[.]ru/Order/Payment/
- hxxp[:]//www.legionofboomfireworks[.]com/Statement/Direct-Deposit-Notice/
- hxxp[:]//www.marcoantoniocasares[.]com/Purchase/Pay-Invoice/
- hxxp[:]//www.perezdearceycia[.]cl/wp-content/FILE/Invoice-23382229-070218/
- hxxp[:]//www[.]sewamobilbengkulu.web[.]id/4th-July-2018/
- hxxp[:]//zlc-aa[.]org/New-Order-Upcoming/588052/
URLS FROM MACRO IN THE DOWNLOADED WORD DOC TO GRAB AN EMOTET BINARY:
- hxxp[:]//clubvolvoitalia[.]it/r3z6/
- hxxp[:]//ericconsulting[.]com/7I3eUNF/
- hxxp[:]//www.goldenfell[.]ru/media/5DzF30jL/
- hxxp[:]//jmamusical[.]jp/wordpress/wp-content/L8J0igh/
- hxxp[:]//www.mobsterljud[.]se/VJkuLg/
EMOTET INFECTION TRAFFIC:
- 156.67.209[.]70 port 80 - www.sewamobilbengkulu.web[.]id - GET /4th-July-2018/ - returned Word doc
- 94.141.21[.]54 port 80 - clubvolvoitalia[.]it - GET /r3z6/ - returned Emotet binary
- 92.27.116[.]104 port 80 - attempted TCP connections, but no response from the server (caused by Emotet)
- 24.173.127[.]246 port 443 - 24.173.127[.]246:443 - POST / - caused by Emotet
- 185.45.193[.]240 port 443 - canariasmotor[.]top - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- 74.79.26[.]193 port 990 - 74.79.26[.]193:990 - GET /whoami.php - caused by Emotet
- 74.79.26[.]193 port 990 - 74.79.26[.]193:990 - POST / - caused by Emotet
MALWARE
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: 4b3159ce83df623e093304b48ebf600a4932a2dc8067792b5dec5248d29c4ccf
File size: 232,192 bytes
File name: wishes-July-4th.doc (random name invloving 4th of July or Independence Day)
File description: Word doc downloaded from link in one of the emails. Has macro to retreive Emotet.
- SHA256 hash: da4e4afbc50adfaa1b0e3d9288ec77346d9b4ebc6bc8538c7801ef4412b19b71
File size: 208,896 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random file name].exe
File description: Emotet malware binary downloaded by macro in downloaded Word doc
- SHA256 hash: 47280253fad49f9f5ebacb420b30985fc68f22fd3a6e51f41571648ce77a8edd
File size: 203,776 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random file name].exe
File description: Updated Emotet malware binary after the host was infected for a while
- SHA256 hash: 2527c9eb597bd85c4ca2e7a6550cc7480dbb3129dd3d6033e66e82b0988ee061
File size: 223,744 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random file name].exe
File description: Zeus Panda Banker downloaded by my Emotet-infected host
Click here to return to the main page.