2018-07-03 - HANCITOR INFECTION WITH ZEUS PANDA BANKER AND SEND SAFE ENTERPRISE (SSE) SPAMBOT MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-03-Hancitor-malspam-1701-UTC.eml.zip 2.0 kB (1,990 bytes)
- 2018-07-03-Hancitor-malspam-1701-UTC.eml (3,788 bytes)
- 2018-07-03-Hancitor-infection-with-Zeus-Panda-Banker-and-SSE-spambot-malware.pcap.zip 2.2 MB (2,173,176 bytes)
- 2018-07-03-Hancitor-infection-with-Zeus-Panda-Banker-and-SSE-spambot-malware.pcap (2,781,537 bytes)
- 2018-07-03-malware-from-Hancitor-infection.zip 1.9 MB (1,902,893 bytes)
- 2018-07-03-Hancitor-malware-binary-6C.pif.exe (73,216 bytes)
- 2018-07-03-Send-Safe-SSE-spambot-malware-from-Hancitor-infection.exe (1,870,096 bytes)
- 2018-07-03-Zeus-Panda-Banker-caused-by-Hancitor.exe (170,496 bytes)
- 2018-07-03-downloaded-Word-doc-with-macro-for-Hancitor.doc (202,240 bytes)
NOTES:
- The block list contains additional info reported by @James_inthe_box, @Techhelplist, and @hazmalware.
- Today, I also saw follow-up malware for the Send Safe Enterprise (SSE) spambot installer.
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
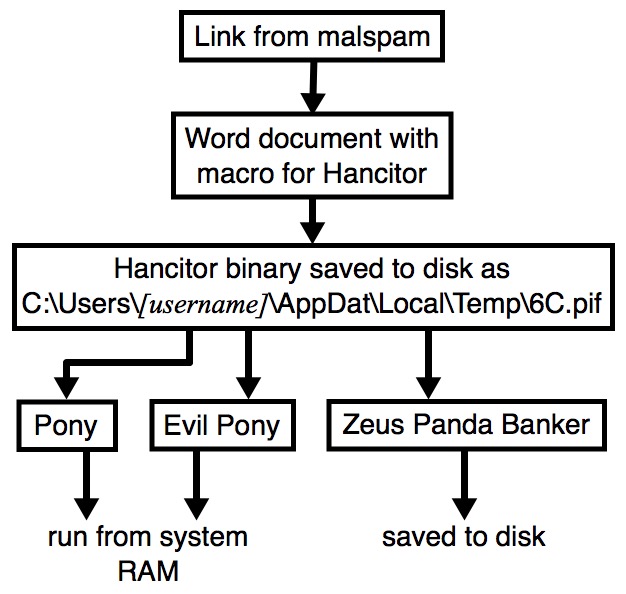
Shown above: Flow chart for today's Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- dudz[.]biz
- golfdudz[.]biz
- golfdudz[.]com
- johnstontrav[.]com
- kickasstrophe[.]org
- mmmfrecklespbctw[.]com
- myidaz[.]com
- positivereinforcementdogtraining[.]com
- singleadultstravel[.]org
- singleadulttravel[.]com
- teachingpositively[.]com
- thezeilerfamily[.]com
- trainingpositively[.]com
- victoriastilwellacademy[.]com
- vspdt[.]net
- vspdt[.]org
- hxxp[:]//aerotransgroup[.]com[.]au/wp-content/plugins/breadcrumbs/1
- hxxp[:]//aerotransgroup[.]com[.]au/wp-content/plugins/breadcrumbs/2
- hxxp[:]//aerotransgroup[.]com[.]au/wp-content/plugins/breadcrumbs/3
- hxxp[:]//fiveamwakeupcall[.]com[.]au/wp-content/plugins/growmap-anti-spambot-plugin/1
- hxxp[:]//fiveamwakeupcall[.]com[.]au/wp-content/plugins/growmap-anti-spambot-plugin/2
- hxxp[:]//fiveamwakeupcall[.]com[.]au/wp-content/plugins/growmap-anti-spambot-plugin/3
- hxxp[:]//theluggagelady[.]com/wp-content/plugins/elegantbuilder/includes/1
- hxxp[:]//theluggagelady[.]com/wp-content/plugins/elegantbuilder/includes/2
- hxxp[:]//theluggagelady[.]com/wp-content/plugins/elegantbuilder/includes/3
- hxxp[:]//5amers[.]com[.]au/wp-content/plugins/backupbuddy/lib/1
- hxxp[:]//5amers[.]com[.]au/wp-content/plugins/backupbuddy/lib/2
- hxxp[:]//5amers[.]com[.]au/wp-content/plugins/backupbuddy/lib/3
- hxxp[:]//wingedspurproductions[.]com[.]au/wp-content/plugins/easy-paypal-lte/lib/1
- hxxp[:]//wingedspurproductions[.]com[.]au/wp-content/plugins/easy-paypal-lte/lib/2
- hxxp[:]//wingedspurproductions[.]com[.]au/wp-content/plugins/easy-paypal-lte/lib/3
- lingrewlighrat[.]com
- tititbutha[.]ru
- woherstinsof[.]ru
- myaningmuchme[.]ru
- hxxp[:]//nec-dsx-programming[.]com/blog/wp-content/plugins/socializer/59.exe
- orsileci[.]com
EMAILS

Shown above: Example of the malspam.
EMAIL HEADERS FROM TODAY'S HANCITOR MALSPAM EXAMPLE:
Received: from psi4jobs[.]com ([209.64.58[.]226]) by [removed] for [removed];
Tue, 03 Jul 2018 17:01:30 +0000 (UTC)
Message-ID: <FB3EC39B.47DDD340@psi4jobs[.]com>
Date: Tue, 03 Jul 2018 13:01:30 -0400
From: "eFax " <message@psi4jobs[.]com>
X-Mailer: Molto foriPad (2.1.0.8604)
MIME-Version: 1.0
TO: [removed]
Subject: This is efax Notification
Content-Type: text/html;
charset="utf-8"
Content-Transfer-Encoding: 7bit
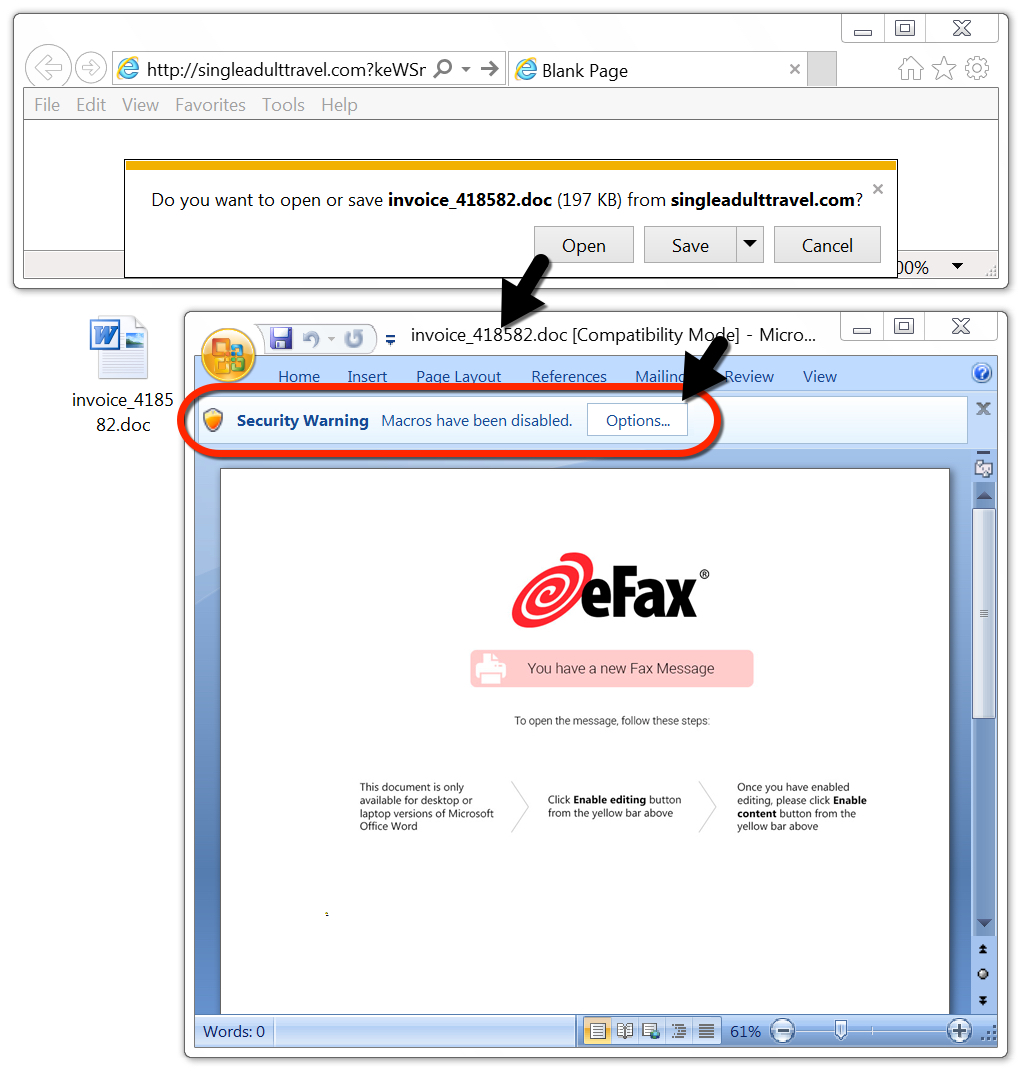
Shown above: Word doc downloaded from link in the malspam.
INFECTION TRAFFIC
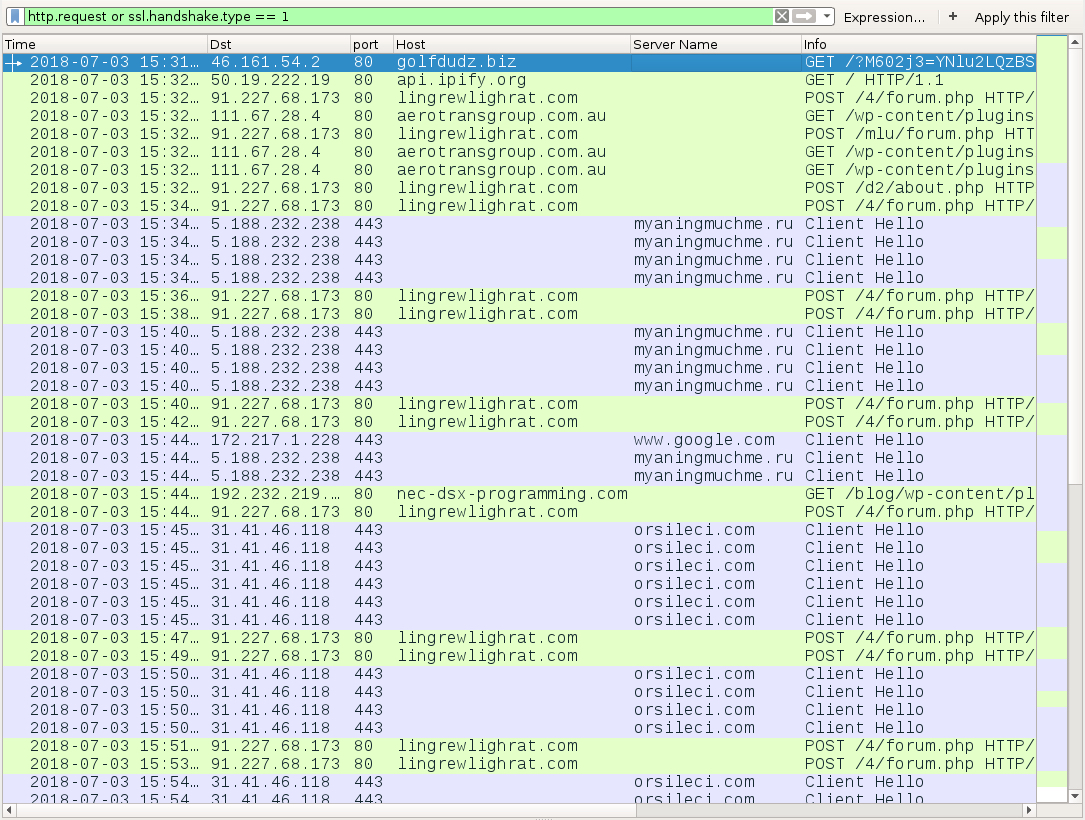
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO DOWNLOAD THE MALICIOUS WORD DOCUMENT:
- hxxp[:]//dudz[.]biz?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//golfdudz[.]biz?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//golfdudz[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//johnstontrav[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//kickasstrophe[.]org?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//mmmfrecklespbctw[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//myidaz[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//positivereinforcementdogtraining[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//singleadultstravel[.]org?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//singleadulttravel[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//teachingpositively[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//thezeilerfamily[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//trainingpositively[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//victoriastilwellacademy[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//vspdt[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//vspdt[.]org?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 46.161.54[.]2 port 80 - golfdudz[.]biz - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 91.227.68[.]173 port 80 - lingrewlighrat[.]com - POST /4/forum.php
- 91.227.68[.]173 port 80 - lingrewlighrat[.]com - POST /mlu/about.php
- 91.227.68[.]173 port 80 - lingrewlighrat[.]com - POST /d2/about.php
- 111.67.28[.]4 port 80 - aerotransgroup[.]com[.]au - GET /wp-content/plugins/breadcrumbs/1
- 111.67.28[.]4 port 80 - aerotransgroup[.]com[.]au - GET /wp-content/plugins/breadcrumbs/2
- 111.67.28[.]4 port 80 - aerotransgroup[.]com[.]au - GET /wp-content/plugins/breadcrumbs/3
- 5.188.232[.]238 port 443 - myaningmuchme[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- port 80 - www.google[.]com - HTTPS/SSL/TLS traffic - probable connectivity check caused by Zeus Panda Banker
- 192.232.219[.]242 port 80 - nec-dsx-programming[.]com - GET /blog/wp-content/plugins/socializer/59.exe
- 31.41.46[.]118 port 443 - orsileci[.]com - HTTPS/SSL/TLS traffic (caused by Zeus Panda Banker?)
- 31.44.184[.]59 UDP port 50016 - SSE spambot UDP beacon
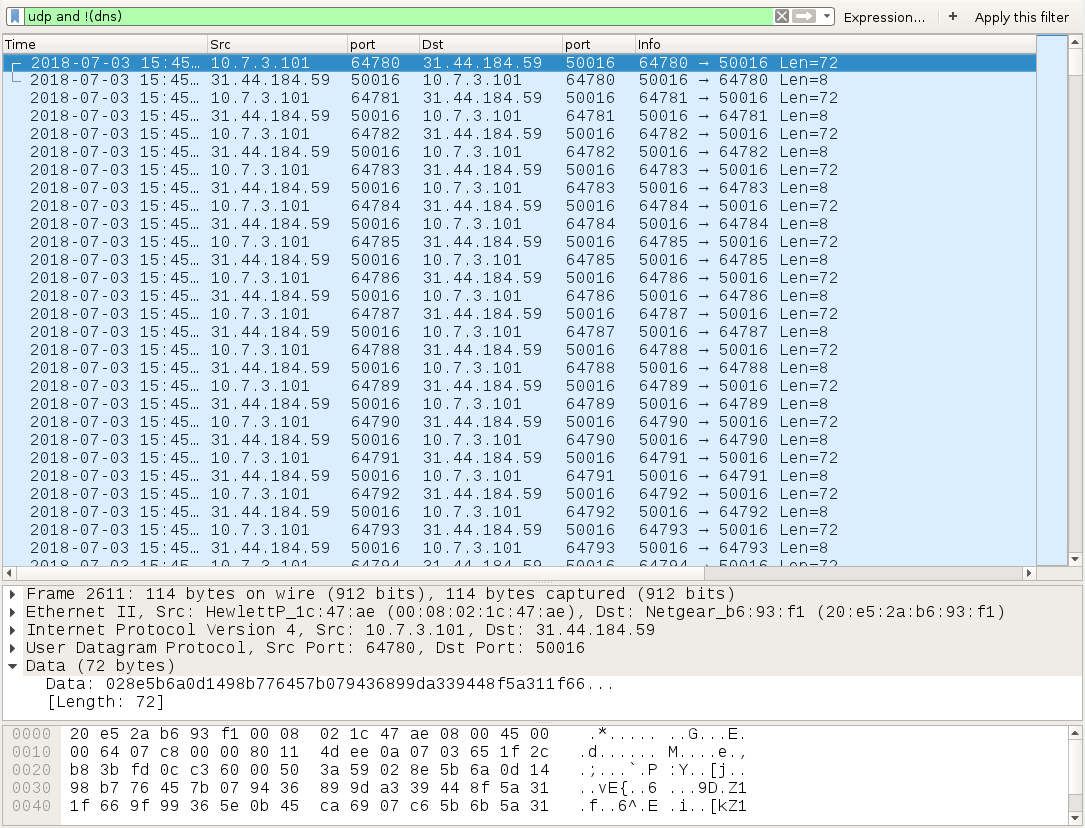
Shown above: SSE spambot UDP beacon traffic from my infected lab host.
MALWARE
MALWARE RETRIEVED FROM MY INFECTED LAB HOST:
- SHA256 hash: 0068b73a8d1b3b962fb2292aaf0d17ed3ebc4590cdeaa03de52e32e2c3f2b186
File size: 202,240 bytes
File name: invoice_[six random digits].doc
File description: Downloaded Word doc with macro for Hancitor
- SHA256 hash: 67f3865b714b0d62d96899311b5c1137f194e9bc7599ab21d565663068b91260
File size: 73,216 bytes
File location: C:\Users\[username]\AppData\Local\Temp\6C.pif
File description: Hancitor malware binary
- SHA256 hash: 415a9e41259f52a38df6f7207519d7e239880ac8e419e3a3e478a64fbf3207b8
File size: 170,496 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda banker caused by Hancitor infection
- SHA256 hash: 64797369a915d3ecb614db4f889b88626020fc4c4b4723c69118d913d6a03a5a
File size: 397,312 bytes
File location: C:\Users\[username]\AppData\Local\Temp\upd6683d399\59.exe
File location: hxxp[:]//nec-dsx-programming[.]com/blog/wp-content/plugins/socializer/59.exe
File description: Send Safe Enterprise (SSE) spambot installer
Click here to return to the main page.