2018-07-03 - EMOTET INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-03-Emotet-malspam-12-examples.txt.zip 3.8 kB (3,792 bytes)
- 2018-07-03-Emotet-malspam-12-examples.txt (11,850 bytes)
- 2018-07-03-Emotet-infection-with-Zeus-Panda-Banker.pcap.zip 6.5 MB (6,471,424 bytes)
- 2018-07-03-Emotet-infection-with-Zeus-Panda-Banker.pcap (7,684,057 bytes)/li>
- 2018-07-03-malware-from-Emotet-infection.zip 442.7 kB (442,708 bytes)
- 2018-07-03-Emotet-malware-binary.exe (106,496 bytes)
- 2018-07-03-Zeus-Panda-Banker-caused-by-Emotet.exe (328,704 bytes)
- 2018-07-03-downloaded-Word-doc-with-macro-for-Emotet.doc (260,352 bytes)
NOTES:
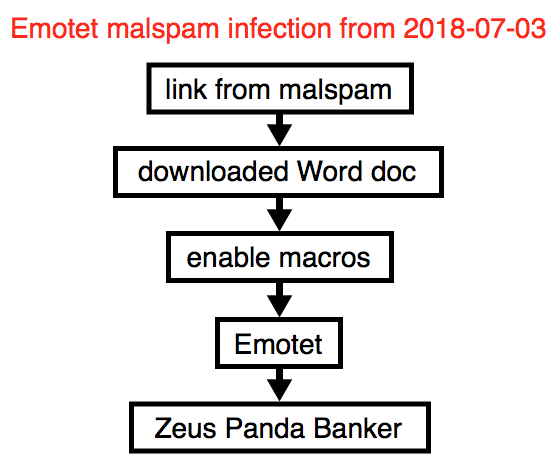
- Emotet followed-up with Zeus Panda Banker today, just like I saw yesterday.
Shown above: Chain of events for today's infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domain:
- hxxp[:]//www.2019voting[.]com/4th-July-2018/
- hxxp[:]//www.anadolu-yapi[.]xyz/INVOICE-STATUS/Direct-Deposit-Notice/
- hxxp[:]//www.bollywoodvillage[.]bid/STATUS/Order-7157584074/
- hxxp[:]//www.codystaffing[.]com/Jul2018/854082/
- hxxp[:]//www.download.viamedia[.]ba/Client/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.farsheazam[.]com/wp-content/US_us/DOC/Pay-Invoice/
- hxxp[:]//www.fuzoneeducations[.]com/Greeting-messages/
- hxxp[:]//www.iamgauravkothari[.]com/IndependenceDay2018/
- hxxp[:]//www.ineds[.]org[.]br/Order/Invoice-3868803421-07-03-2018/
- hxxp[:]//www.kalyoncular[.]com[.]tr/Messages-2018/
- hxxp[:]//www.live-jasmin-com[.]net/Messages-2018/
- hxxp[:]//www.magazine.asifabih[.]com/Greeting-eCard/
- hxxp[:]//www.kotizacija.branding[.]ba/TsUbf7QLJ/
- hxxp[:]//avciogluaydinlatma[.]com/CQAPGgy/
- hxxp[:]//www.elgg.tedzplace[.]ca/srfL4zx0IH/
- hxxp[:]//www.creapackthai[.]com/ECd4TX4iyK/
- hxxp[:]//iclub8[.]hk/Wu6OsKK/
- canariasmotor[.]top
- adshiepkhach[.]top
EMAILS
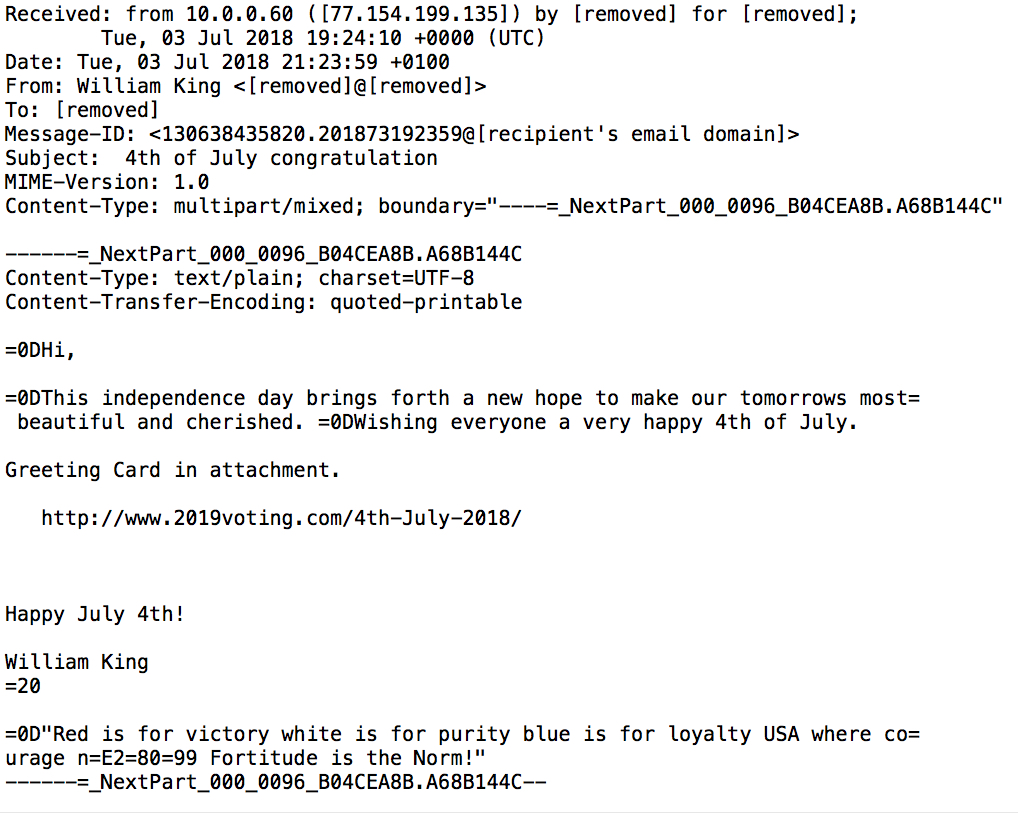
Shown above: Example of the malspam (raw text with headers and formatting).
DATA FROM 12 EMAIL EXAMPLES OF THE MALSPAM:
- Received: from 10.0.0[.]2 ([196.25.35[.]242])
- Received: from 10.0.0[.]9 ([62.77.189[.]201])
- Received: from 10.0.0[.]20([221.163.32[.]101])
- Received: from 10.0.0[.]39 ([201.229.68[.]226])
- Received: from 10.0.0[.]43 ([60.250.207[.]85])
- Received: from 10.0.0[.]52 ([124.29.232[.]31])
- Received: from 10.0.0[.]59 ([221.163.32[.]101])
- Received: from 10.0.0[.]60 ([77.154.199[.]135])
- Received: from ([84.53.85[.]205])
- Received: from ([187.189.74[.]206])
- Received: from ([189.161.92[.]155])
- Received: from ([213.111.22[.]95])
SPOOFED SENDERS:
- From: Amanda Salitsky <[spoofed sending email address]>
- From: Crispin, David J. <[spoofed sending email address]>
- From: Jade Sivell <[spoofed sending email address]>
- From: John Doris <[spoofed sending email address]>
- From: Jon Forrester <[spoofed sending email address]>
- From: Lic. Enrique Alvarez <[spoofed sending email address]>
- From: Michele Davies <[spoofed sending email address]>
- From: Milan Marsic <[spoofed sending email address]>
- From: Nicola mobile <[spoofed sending email address]>
- From: Patrick Bingham <[spoofed sending email address]>
- From: Scott Crowe <[spoofed sending email address]>
- From: William King <[spoofed sending email address]>
SUBJECT LINES:
- Subject: 4th of July congratulation
- Subject: 4th of July eCard
- Subject: 4th of July Greeting eCard
- Subject: Happy 4th of July Greeting Message
- Subject: The Fourth of July wishes
- Subject: ACCOUNT#94895547-Milan Marsic
- Subject: Invoice 897614 from Patrick Bingham
- Subject: Invoices Overdue
- Subject: NYPXV7-16497063849
- Subject: Payment
- Subject: Purchases 2018
- Subject: Scott Crowe The 4th of July Greeting eCard
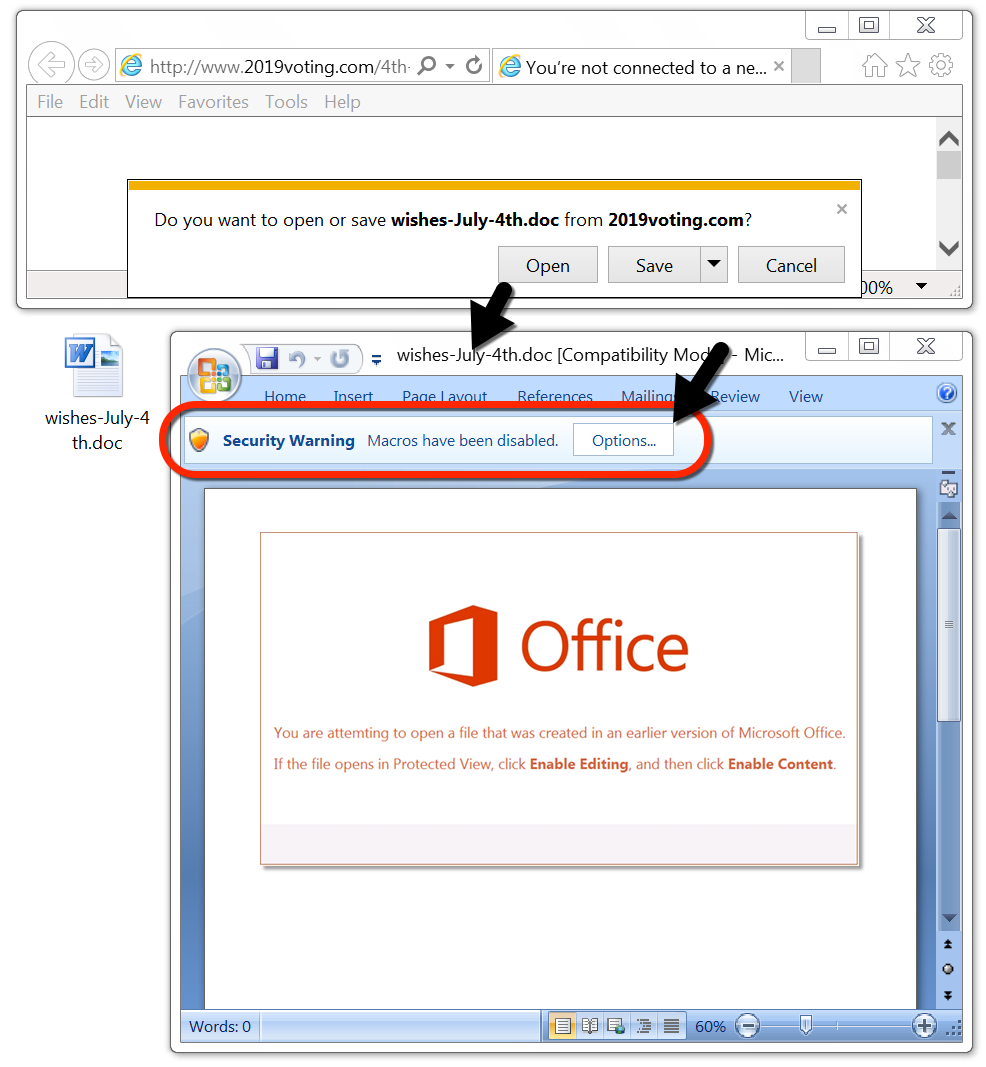
Shown above: Word doc generated from link in the malspam.
INFECTION TRAFFIC
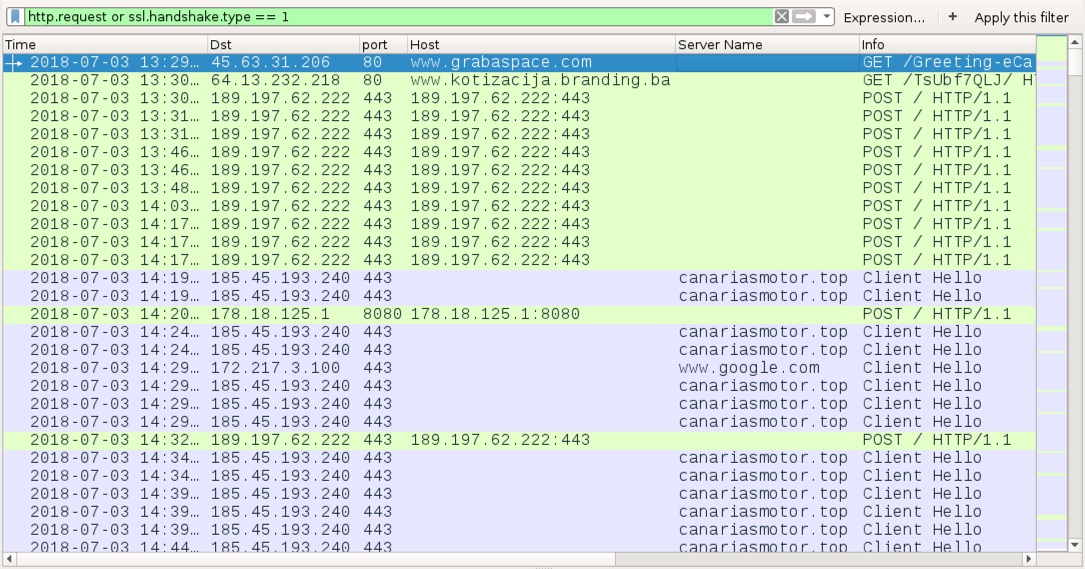
Shown above: Traffic from an infection filtered in Wireshark.
URLS FROM THE MALSPAM TO DOWNLOAD THE INITIAL WORD DOCUMENT:
- hxxp[:]//www.2019voting[.]com/4th-July-2018/
- hxxp[:]//www.anadolu-yapi[.]xyz/INVOICE-STATUS/Direct-Deposit-Notice/
- hxxp[:]//www.bollywoodvillage[.]bid/STATUS/Order-7157584074/
- hxxp[:]//www.codystaffing[.]com/Jul2018/854082/
- hxxp[:]//www.download.viamedia[.]ba/Client/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.farsheazam[.]com/wp-content/US_us/DOC/Pay-Invoice/
- hxxp[:]//www.fuzoneeducations[.]com/Greeting-messages/
- hxxp[:]//www.iamgauravkothari[.]com/IndependenceDay2018/
- hxxp[:]//www.ineds[.]org[.]br/Order/Invoice-3868803421-07-03-2018/
- hxxp[:]//www.kalyoncular[.]com[.]tr/Messages-2018/
- hxxp[:]//www.live-jasmin-com[.]net/Messages-2018/
- hxxp[:]//www.magazine.asifabih[.]com/Greeting-eCard/
URLS FROM MACRO IN THE DOWNLOADED WORD DOC TO GRAB AN EMOTET BINARY:
- hxxp[:]//www.kotizacija.branding[.]ba/TsUbf7QLJ/
- hxxp[:]//avciogluaydinlatma[.]com/CQAPGgy/
- hxxp[:]//www.elgg.tedzplace[.]ca/srfL4zx0IH/
- hxxp[:]//www.creapackthai[.]com/ECd4TX4iyK/
- hxxp[:]//iclub8[.]hk/Wu6OsKK/
EMOTET INFECTION TRAFFIC:
- 45.63.31[.]206 port 80 - www.grabaspace[.]com - GET /Greeting-eCard/ - returned Word doc
- 64.13.232[.]218 port 80 - www.kotizacija.branding[.]ba - GET /TsUbf7QLJ/ - returned Emotet binary
- 189.197.62[.]222 port 443 - 189.197.62[.]222:443 - POST / - caused by Emotet
- 178.18.125[.]1 port 443 - 178.18.125[.]1:8080 - POST / - caused by Emotet
- 187.163.39[.]35 port 80 - attempted TCP connections, but no response from the server (caused by Emotet)
- 177.244.172[.]62 port 80 - attempted TCP connections, but no response from the server (caused by Emotet)
- 200.92.37[.]146 port 443 - attempted TCP connections, but no response from the server (caused by Emotet)
- 185.45.193[.]240 port 443 - canariasmotor[.]top - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- DNS query for adshiepkhach[.]top (response: No such name)
MALWARE
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: 64c273bd9ecd24d41d8b540da31a0a5b906701b7b0ef0e3c4afeac244c38a51f
File size: 260,352 bytes
File name: Greeting-Card-The-Fourth-of-July.doc (random name invloving 4th of July or Independence Day)
File description: Word doc downloaded from link in one of the emails. Has macro to retreive Emotet.
- SHA256 hash: 2162c42b68af7f56590335a0fcead8e19b1b103acdf0bc3d783db17c9c637999
File size: 106,496 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random file name].exe
File description: Emotet malware binary downloaded by macro in downloaded Word doc
- SHA256 hash: bc394ca7b7db058dab18ad8f612fe99c734006f034945b1336682e4728a4e932
File size: 328,704 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random file name].exe
File description: Zeus Panda Banker downloaded by my Emotet-infected host
Click here to return to the main page.