2018-07-09 - EMOTET INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-09-Emotet-malspam-30-examples.txt.zip 7.5 kB (7,548 bytes)
- 2018-07-09-Emotet-malspam-30-examples.txt (31,493 bytes)
- 2018-07-09-Emotet-infection-with-Zeus-Panda-Banker.pcap.zip 2.7 MB (2,719,555 bytes)
- 2018-07-09-Emotet-infection-with-Zeus-Panda-Banker.pcap (3,001,733 bytes)
- 2018-07-09-malware-associated-with-Emotet-infection.zip 498 kB (497,777 bytes)
- 2018-07-09-Emotet-malware-binary-1-of-2.exe (110,592 bytes)
- 2018-07-09-Emotet-malware-binary-2-of-2.exe (106,496 bytes)
- 2018-07-09-Zeus-Panda-Banker-loaded-by-Emotet.exe (248,832 bytes)
- 2018-07-09-downloaded-Word-doc-with-macro-for-Emotet.doc (236,800 bytes)
NOTES:
- My Emotet infection today was followed-up with Zeus Panda Banker.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domain:
- hxxp[:]//avocap[.]eu/Rechnung/Fakturierung/Rechnung-0846-5845/
- hxxp[:]//calendar.bubnov[.]ru/newsletter/EN_en/DOC/Invoice-93422/
- hxxp[:]//irisoil[.]com/Dokumente/Fakturierung/Rechnung-scan-Nr028435/
- hxxp[:]//stylethemonkey[.]com/newsletter/US/STATUS/Invoice-5225260/
- hxxp[:]//www.adventuredsocks[.]com/sites/En/ACCOUNT/Pay-Invoice/
- hxxp[:]//www.altinbronz[.]com[.]tr/default/En/FILE/Customer-Invoice-CM-3772286/
- hxxp[:]//www.arlab21[.]com/Rechnung/FORM/Rechnung/
- hxxp[:]//www.autoplasrecyclingltd[.]co[.]uk/files/En/New-Order-Upcoming/HRI-Monthly-Invoice/
- hxxp[:]//www.ayvalikfotografcisi[.]com/newsletter/US_us/Client/Invoice-83453/
- hxxp[:]//www.bazaltbezpeka[.]com[.]ua/Rechnungs-Details/RECHNUNG/Unsere-Rechnung-vom-09-Juli-033-880/
- hxxp[:]//www.bursabesevlernakliyat[.]com/Rechnung/Rechnungszahlung/Rechnung-fur-Zahlung-Nr080000/
- hxxp[:]//www.certiagro[.]com/Jul2018/EN_en/Client/Invoice-431495/
- hxxp[:]//www.clean.vanzherke[.]ru/Jul2018/US/Order/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.crackbros[.]com/files/En/FILE/Invoice-157212/
- hxxp[:]//www.dessertcake[.]com[.]ua/files/US/Purchase/Pay-Invoice/
- hxxp[:]//www.dilema[.]si/files/EN_en/OVERDUE-ACCOUNT/Direct-Deposit-Notice/
- hxxp[:]//www.dokassessoria[.]com[.]br/Rechnungs-Details/DETAILS/Erinnerung-an-die-Rechnungszahlung-002817/
- hxxp[:]//www.dom-stroy52[.]ru/default/EN_en/STATUS/20352/
- hxxp[:]//www.eshop9ja[.]com/default/US_us/STATUS/Invoice-574161/
- hxxp[:]//www.hilalkentasm[.]com/sites/En_us/STATUS/Invoices/
- hxxp[:]//www.ingpk[.]ru/sites/EN_en/STATUS/Services-07-09-18-New-Customer-RS/
- hxxp[:]//www.interfrazao[.]com[.]br/pdf/En/DOC/Past-Due-invoice/
- hxxp[:]//www.lutz-nachhilfe[.]de/sites/En_us/Payment-and-address/Invoice-79627/
- hxxp[:]//www.malwaeduskills[.]com/pdf/US/Client/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.missaost[.]com[.]br/files/En_us/FILE/Payment/
- hxxp[:]//www.segmaster.pagina-oficial[.]ws/sites/En/Purchase/Invoice-94754212-070918/
- hxxp[:]//www.sunnybeach05[.]ru/Jul2018/EN_en/ACCOUNT/Invoice-989633/
- hxxp[:]//www.wadhwawisecitypanvel[.]info/default/US/STATUS/New-Invoice-KY95015-UI-9687/
- hxxp[:]//www.xn--dieglcksspirale-3vb[.]net/pdf/En_us/Client/Invoice-533946/
- hxxp[:]//www.yildirimcatering[.]org/newsletter/En/OVERDUE-ACCOUNT/Invoices/
- hxxp[:]//primerplano[.]org/Yb/
- hxxp[:]//ave-ant[.]com/u/
- hxxp[:]//muaithai[.]pl/bdwsab/
- hxxp[:]//jmamusical[.]jp/wordpress/wp-content/Ec0SS/
- hxxp[:]//nagoyamicky[.]com/cacheqblog/bDWJMUD/
- airconhero[.]xyz
EMAILS
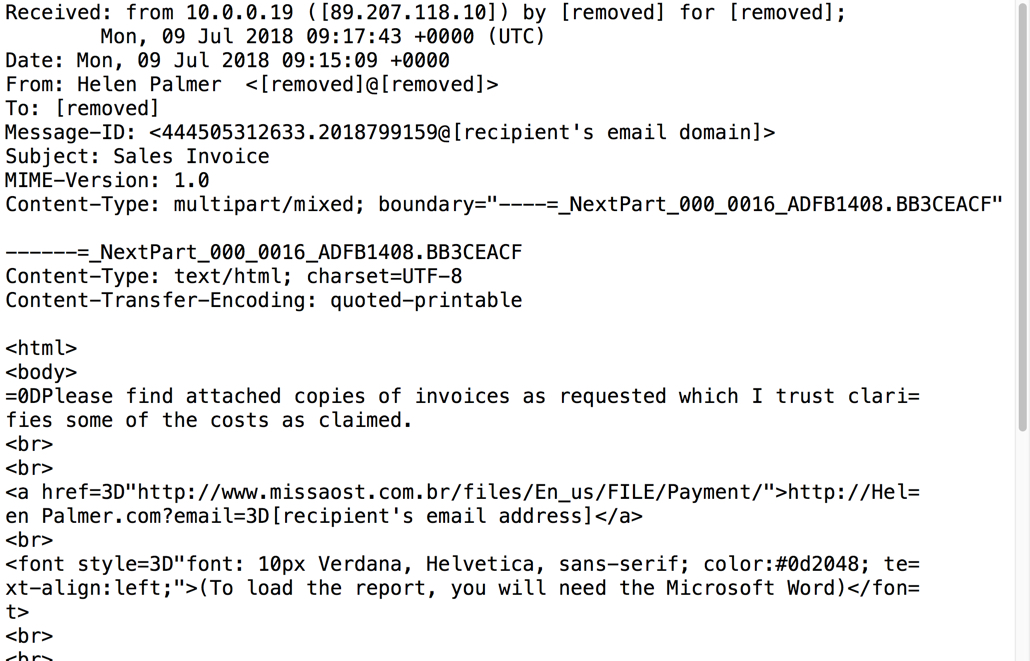
Shown above: Example of the malspam (raw text with headers and formatting).
DATA FROM 30 EMAIL EXAMPLES OF THE MALSPAM:
- Date/Time: Monday 2018-07-09 as early as: 06:48 UTC through 16:08 UTC
- Received: from ([83.61.6[.]192])
- Received: from ([176.203.64[.]58])
- Received: from ([189.165.238[.]227])
- Received: from ([197.234.39[.]146])
- Received: from ([202.189.252[.]90])
- Received: from ([221.163.32[.]101])
- Received: from 10.0.0[.]0 ([185.129.0[.]187])
- Received: from 10.0.0[.]0 ([221.163.32[.]101])
- Received: from 10.0.0[.]3 ([115.42.222[.]210])
- Received: from 10.0.0[.]7 ([118.97.173[.]18])
- Received: from 10.0.0[.]12 ([77.16.77[.]89])
- Received: from 10.0.0[.]16 ([114.143.224[.]98])
- Received: from 10.0.0[.]18 ([178.16.162[.]59])
- Received: from 10.0.0[.]19 ([89.207.118[.]10])
- Received: from 10.0.0[.]20 ([221.163.32[.]101])
- Received: from 10.0.0[.]21 ([221.163.32[.]101])
- Received: from 10.0.0[.]23 ([103.83.245[.]139])
- Received: from 10.0.0[.]23 ([221.163.32[.]101])
- Received: from 10.0.0[.]25 ([103.105.64[.]146])
- Received: from 10.0.0[.]30 ([113.172.215[.]181])
- Received: from 10.0.0[.]40 ([122.161.196[.]95])
- Received: from 10.0.0[.]44 ([221.163.32[.]101])
- Received: from 10.0.0[.]46 ([221.163.32[.]101])
- Received: from 10.0.0[.]49 ([115.135.234[.]201])
- Received: from 10.0.0[.]50 ([203.110.85[.]178])
- Received: from 10.0.0[.]53 ([46.185.230[.]184])
- Received: from 10.0.0[.]54 ([117.240.223[.]250])
- Received: from 10.0.0[.]55 ([83.61.6[.]192])
- Received: from 10.0.0[.]57 ([221.163.32[.]101])
- Received: from 10.0.0[.]59 ([178.22.144[.]86])
SPOOFED SENDERS:
- From: CRAIG@[recipient's email domain] <[spoofed email address]>
- From: Neusser@[recipient's email domain] <[spoofed email address]>
- From: ralf.litschel@[recipient's email domain] <[spoofed email address]>
- From: rketter@caleres[.]com <[spoofed email address]>
- From: rscavello@precisionautomationinc[.]com <[spoofed email address]>
- From: stolz@[recipient's email domain] <[spoofed email address]>
- From: Arroyo, Inaki (CRONIMET Hispania) <[spoofed email address]>
- From: Barbara Knill <[spoofed email address]>
- From: Batterson, Richard <[spoofed email address]>
- From: Bob Murphy <[spoofed email address]>
- From: Bolton Plant <[spoofed email address]>
- From: Catherine Bolton <[spoofed email address]>
- From: Chris Hardy <[spoofed email address]>
- From: Craig Albers <[spoofed email address]>
- From: David Broadhurst <[spoofed email address]>
- From: Dianne Decker <[spoofed email address]>
- From: Helen Palmer <[spoofed email address]>
- From: Jenson Harry <[spoofed email address]>
- From: Joyce Lynch <[spoofed email address]>
- From: Lucas Ezell <[spoofed email address]>
- From: M&CP - Port Health <[spoofed email address]>
- From: Mike Toozer <[spoofed email address]>
- From: Mingkwan Charoenporn <[spoofed email address]>
- From: Nathan Neally <[spoofed email address]>
- From: PEDROSA Mariana Sofia <[spoofed email address]>
- From: PoolCar Sales <[spoofed email address]>
- From: Richard Cartwright <[spoofed email address]>
- From: Sian Moffat <[spoofed email address]>
- From: Tilly Watkins <[spoofed email address]>
- From: Timo Hofstetter <[spoofed email address]>
SUBJECT LINES:
- Subject: Joyce Lynch: 901597
- Subject: CRAIG@[recipient's email domain] / Inv. 3653869422
- Subject: =?UTF-8?B?SWhyZSBSZWNobnVuZyB2b20gMDkuMDcuMjAxOCDihJYwMTM1MzI=?=
- Subject: =?UTF-8?B?UmVjaG51bmcgZsO8ciBaYWhsdW5nIE5yLiAwOTk2NzE=?=
- Subject: =?UTF-8?B?UmVjaG51bmcgZsO8ciBEaWVuc3RsZWlzdHVuZ2VuIA==?=
- Subject: 0999639 Survey questions
- Subject: Awaiting for your confirmation
- Subject: Bezahlen Sie die Rechnung 528924152756594
- Subject: Final Account
- Subject: Invoice
- Subject: Invoice 07.09.18
- Subject: Invoice 73861846 Invoice date 070918 Order no. 43953870628
- Subject: Invoices
- Subject: Invoices Overdue
- Subject: MKN3-97971776420
- Subject: Order Confirmation
- Subject: Outstanding INVOICE TQET/355619/7536
- Subject: Outstanding INVOICE WJLLK/877387/1763
- Subject: Overdue payment
- Subject: Pay Invoice
- Subject: Payment status
- Subject: PoolCar Sales invoice
- Subject: Purchases 2018
- Subject: RE: Outstanding INVOICE LFX/348779/395
- Subject: Rechnung scan 251580728
- Subject: Sales Invoice
- Subject: Seperate Remittance Advice Layout - paper document A4
- Subject: Zahlungserinnerung vom Juli
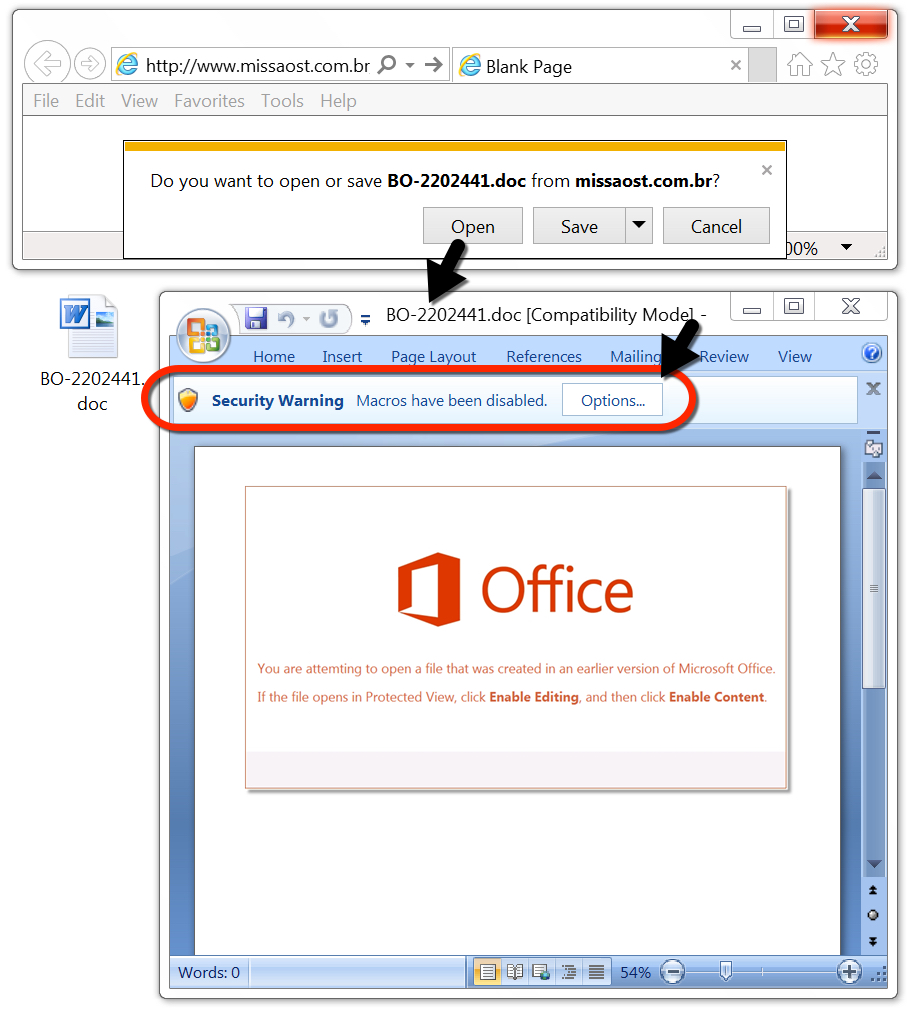
Shown above: Word doc generated from link in the malspam.
INFECTION TRAFFIC
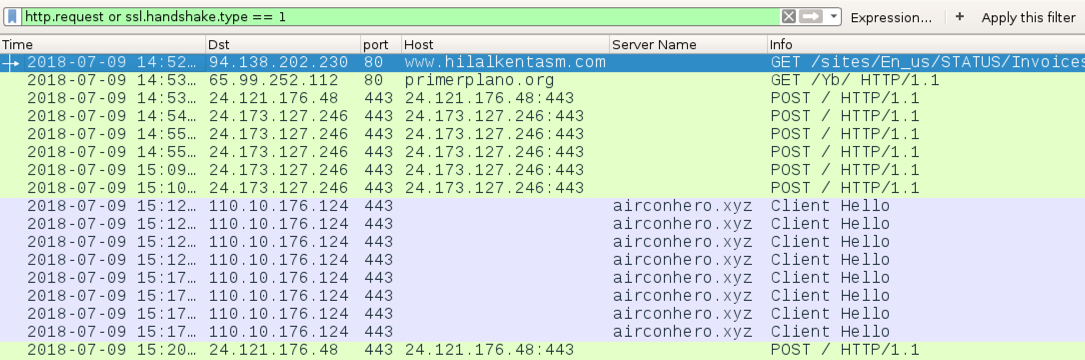
Shown above: Traffic from an infection filtered in Wireshark.
URLS FROM THE MALSPAM TO DOWNLOAD THE INITIAL WORD DOCUMENT:
- hxxp[:]//avocap[.]eu/Rechnung/Fakturierung/Rechnung-0846-5845/
- hxxp[:]//calendar.bubnov[.]ru/newsletter/EN_en/DOC/Invoice-93422/
- hxxp[:]//irisoil[.]com/Dokumente/Fakturierung/Rechnung-scan-Nr028435/
- hxxp[:]//stylethemonkey[.]com/newsletter/US/STATUS/Invoice-5225260/
- hxxp[:]//www.adventuredsocks[.]com/sites/En/ACCOUNT/Pay-Invoice/
- hxxp[:]//www.altinbronz[.]com[.]tr/default/En/FILE/Customer-Invoice-CM-3772286/
- hxxp[:]//www.arlab21[.]com/Rechnung/FORM/Rechnung/
- hxxp[:]//www.autoplasrecyclingltd[.]co[.]uk/files/En/New-Order-Upcoming/HRI-Monthly-Invoice/
- hxxp[:]//www.ayvalikfotografcisi[.]com/newsletter/US_us/Client/Invoice-83453/
- hxxp[:]//www.bazaltbezpeka[.]com[.]ua/Rechnungs-Details/RECHNUNG/Unsere-Rechnung-vom-09-Juli-033-880/
- hxxp[:]//www.bursabesevlernakliyat[.]com/Rechnung/Rechnungszahlung/Rechnung-fur-Zahlung-Nr080000/
- hxxp[:]//www.certiagro[.]com/Jul2018/EN_en/Client/Invoice-431495/
- hxxp[:]//www.clean.vanzherke[.]ru/Jul2018/US/Order/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.crackbros[.]com/files/En/FILE/Invoice-157212/
- hxxp[:]//www.dessertcake[.]com[.]ua/files/US/Purchase/Pay-Invoice/
- hxxp[:]//www.dilema[.]si/files/EN_en/OVERDUE-ACCOUNT/Direct-Deposit-Notice/
- hxxp[:]//www.dokassessoria[.]com[.]br/Rechnungs-Details/DETAILS/Erinnerung-an-die-Rechnungszahlung-002817/
- hxxp[:]//www.dom-stroy52[.]ru/default/EN_en/STATUS/20352/
- hxxp[:]//www.eshop9ja[.]com/default/US_us/STATUS/Invoice-574161/
- hxxp[:]//www.hilalkentasm[.]com/sites/En_us/STATUS/Invoices/
- hxxp[:]//www.ingpk[.]ru/sites/EN_en/STATUS/Services-07-09-18-New-Customer-RS/
- hxxp[:]//www.interfrazao[.]com[.]br/pdf/En/DOC/Past-Due-invoice/
- hxxp[:]//www.lutz-nachhilfe[.]de/sites/En_us/Payment-and-address/Invoice-79627/
- hxxp[:]//www.malwaeduskills[.]com/pdf/US/Client/Auditor-of-State-Notification-of-EFT-Deposit/
- hxxp[:]//www.missaost[.]com[.]br/files/En_us/FILE/Payment/
- hxxp[:]//www.segmaster.pagina-oficial[.]ws/sites/En/Purchase/Invoice=-94754212-070918/
- hxxp[:]//www.sunnybeach05[.]ru/Jul2018/EN_en/ACCOUNT/Invoice-989633/
- hxxp[:]//www.wadhwawisecitypanvel[.]info/default/US/STATUS/New-Invoice-KY95015-UI-9687/
- hxxp[:]//www.xn--dieglcksspirale-3vb[.]net/pdf/En_us/Client/Invoice-533946/
- hxxp[:]//www.yildirimcatering[.]org/newsletter/En/OVERDUE-ACCOUNT/Invoices/
URLS FROM MACRO IN THE DOWNLOADED WORD DOC TO GRAB AN EMOTET BINARY:
- hxxp[:]//primerplano[.]org/Yb/
- hxxp[:]//ave-ant[.]com/u/
- hxxp[:]//muaithai[.]pl/bdwsab/
- hxxp[:]//jmamusical[.]jp/wordpress/wp-content/Ec0SS/
- hxxp[:]//nagoyamicky[.]com/cacheqblog/bDWJMUD/
EMOTET INFECTION TRAFFIC:
- 94.138.202[.]230 port 80 - www.hilalkentasm[.]com - GET /sites/En_us/STATUS/Invoices/ (returned Word doc)
- 65.99.252[.]112 port 80 - primerplano[.]org - GET /Yb/ (returned Emotet malware binary)
- 24.121.176[.]48 port 443 - 24.121.176[.]48:443 - POST / (Emotet post-infection traffic)
- 24.173.127[.]246 port 443 - 24.173.127[.]246:443 - POST / (Emotet post-infection traffic)
- 74.79.26[.]193 port 990 - attempted TCP connections, but no response from the server (Emotet post-infection traffic)
- 110.10.176[.]124 port 443 - airconhero[.]xyz - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
MALWARE
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: 369382490deaf9246e39d07c57db6b56fa3fd9454671ec728bf81a4c4a1a549e
File size: 236,800 bytes
File name: MG-921280152.doc (random file names)
File description: Word doc downloaded from link in one of the emails. Has macro to retrieve Emotet.
- SHA256 hash: 2f93c8c97f99c77880027b149d257268f45bce1255aeaefdc4f21f5bd744573f
File size: 110,592 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random file name].exe
File description: Emotet malware binary (1 of 2)downloaded by macro in downloaded Word doc
- SHA256 hash: e90cbb0729e523bc8647e2437cd7f91ed4dafe131b945599aca1e64058fe76e7
File size: 106,496 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random file name].exe
File description: Updated Emotet malware binary (2 of 2)
- SHA256 hash: f0138f78c1fd8b47be240bb779b32dda0be2e681145b50765f5bb5715be9d5eb
File size: 248,832 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random file name].exe
File description: Zeus Panda Banker downloaded by my Emotet-infected host
Click here to return to the main page.
