2018-07-09 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-09-Hancitor-malspam-1506-UTC.eml.zip 2.0 kB (2,040 bytes)
- 2018-07-09-Hancitor-malspam-1506-UTC.eml (6.048 bytes)
- 2018-07-09-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.4 MB (2,358,376 bytes)
- 2018-07-09-Hancitor-infection-with-Zeus-Panda-Banker.pcap (2,963,326 bytes)/li>
- 2018-07-09-malware-from-Hancitor-infection.zip 271 kB (270,874 bytes)
- 2018-07-09-Hancitor-binary-6C.pif.exe (56,320 bytes)
- 2018-07-09-Zeus-Panda-Banker-caused-by-Hancitor-infection.exe (172,544 bytes)
- 2018-07-09-downloaded-Word-doc-with-macro-for-Hancitor.doc (181,760 bytes)
NOTES:
- As always, thanks to @Techhelplist, @James_inthe_box, and the many others who keep a close eye on this. Their info helps make my blog posts more complete.
- And thanks to everyone who contributed to the discussion thread on Twitter when I was having problems downloading the initial Word document.
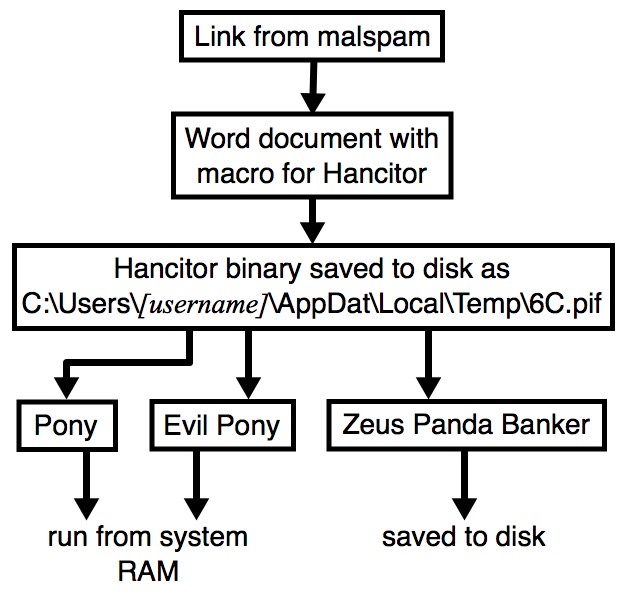
Shown above: Flow chart for today's Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain and URLs:
- altilium[.]com
- altilium[.]net
- dryerventwizardcanada[.]biz
- getlintout[.]biz
- getthelintout[.]info
- pbtmail[.]com
- pbtmail[.]net
- thedryerventwizard[.]biz
- thedryerventwizard[.]ca
- wegetthelintout[.]ca
- wegetthelintout[.]net
- hinwasslysed[.]com
- harforusero[.]ru
- berofaked[.]ru
- hxxp[:]//realeverydaybusiness[.]com/wp-content/plugins/jetpack-popular-posts/1
- hxxp[:]//realeverydaybusiness[.]com/wp-content/plugins/jetpack-popular-posts/2
- hxxp[:]//realeverydaybusiness[.]com/wp-content/plugins/jetpack-popular-posts/3
- hxxp[:]//ourfamilyhome[.]biz/wp-content/plugins/formget-contact-form/inc/1
- hxxp[:]//ourfamilyhome[.]biz/wp-content/plugins/formget-contact-form/inc/2
- hxxp[:]//ourfamilyhome[.]biz/wp-content/plugins/formget-contact-form/inc/3
- hxxp[:]//scientificservicesinc[.]com/wp-content/plugins/themestarta/1
- hxxp[:]//scientificservicesinc[.]com/wp-content/plugins/themestarta/2
- hxxp[:]//scientificservicesinc[.]com/wp-content/plugins/themestarta/3
- hxxp[:]//psychprofiler[.]com/wp-content/plugins/limit-login-attempts/1
- hxxp[:]//psychprofiler[.]com/wp-content/plugins/limit-login-attempts/2
- hxxp[:]//psychprofiler[.]com/wp-content/plugins/limit-login-attempts/3
- hxxp[:]//thewordspoken[.]org/wp-content/plugins/backupwordpress/1
- hxxp[:]//thewordspoken[.]org/wp-content/plugins/backupwordpress/2
- hxxp[:]//thewordspoken[.]org/wp-content/plugins/backupwordpress/3
- myaningmuchme[.]ru
EMAILS
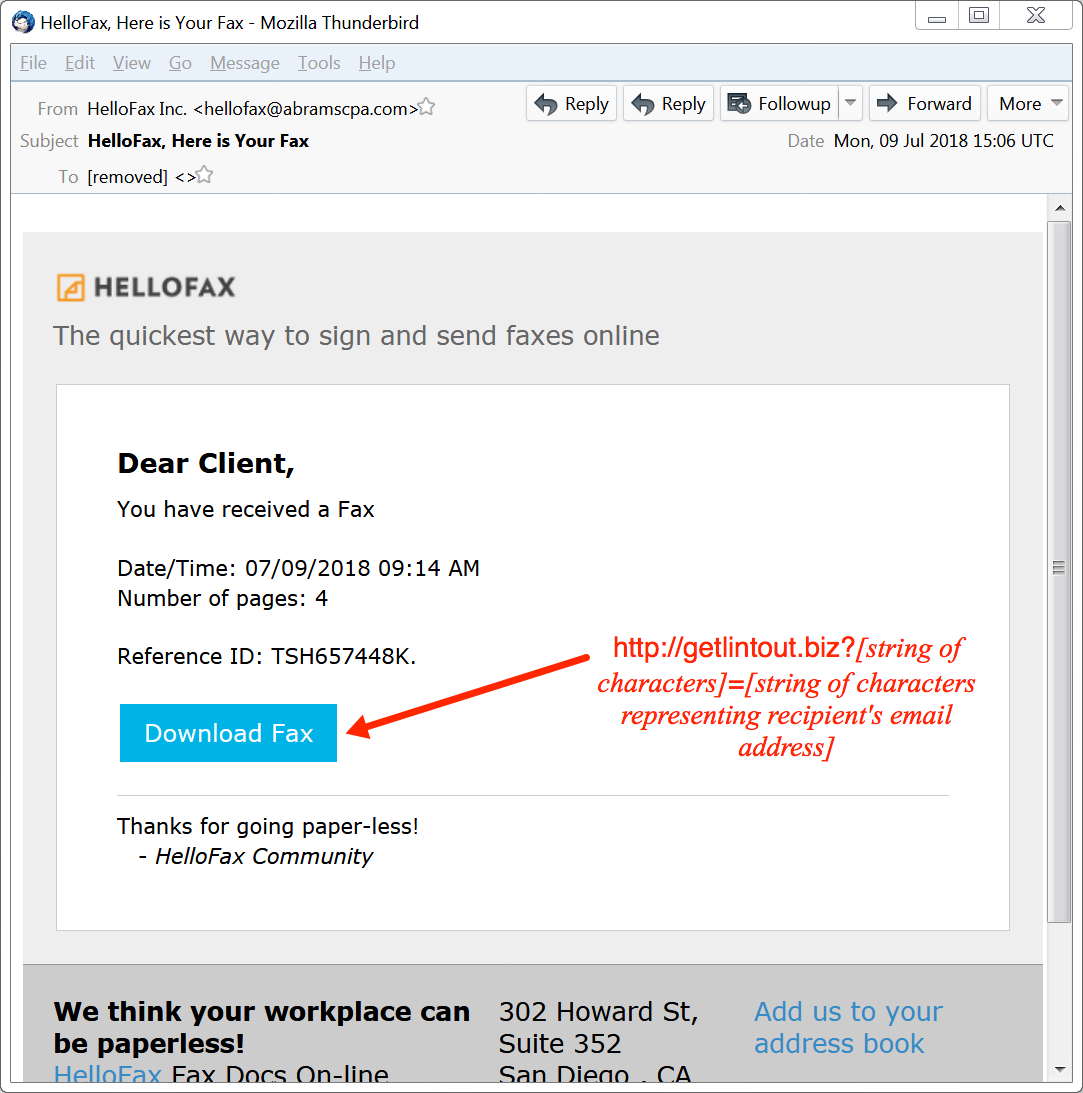
Shown above: Example of the malspam.
EMAIL HEADERS FROM TODAY'S HANCITOR MALSPAM EXAMPLE:
Received: from abramscpa[.]com ([173.51.132[.]44]) by [removed] for [removed];
Mon, 09 Jul 2018 15:06:40 +0000 (UTC)
Message-ID: <1C2ED6EA.ACEFB0C6@abramscpa[.]com>
Date: Mon, 09 Jul 2018 08:06:43 -0700
Reply-To: "HelloFax" <hellofax@abramscpa[.]com>
From: "HelloFax Inc." <hellofax@abramscpa[.]com>
X-Mailer: Apple Mail (2.1990.1)
MIME-Version: 1.0
TO: [removed]
Subject: HelloFax, Here is Your Fax
Content-Type: text/html;
charset="utf-8"
Content-Transfer-Encoding: 7bit
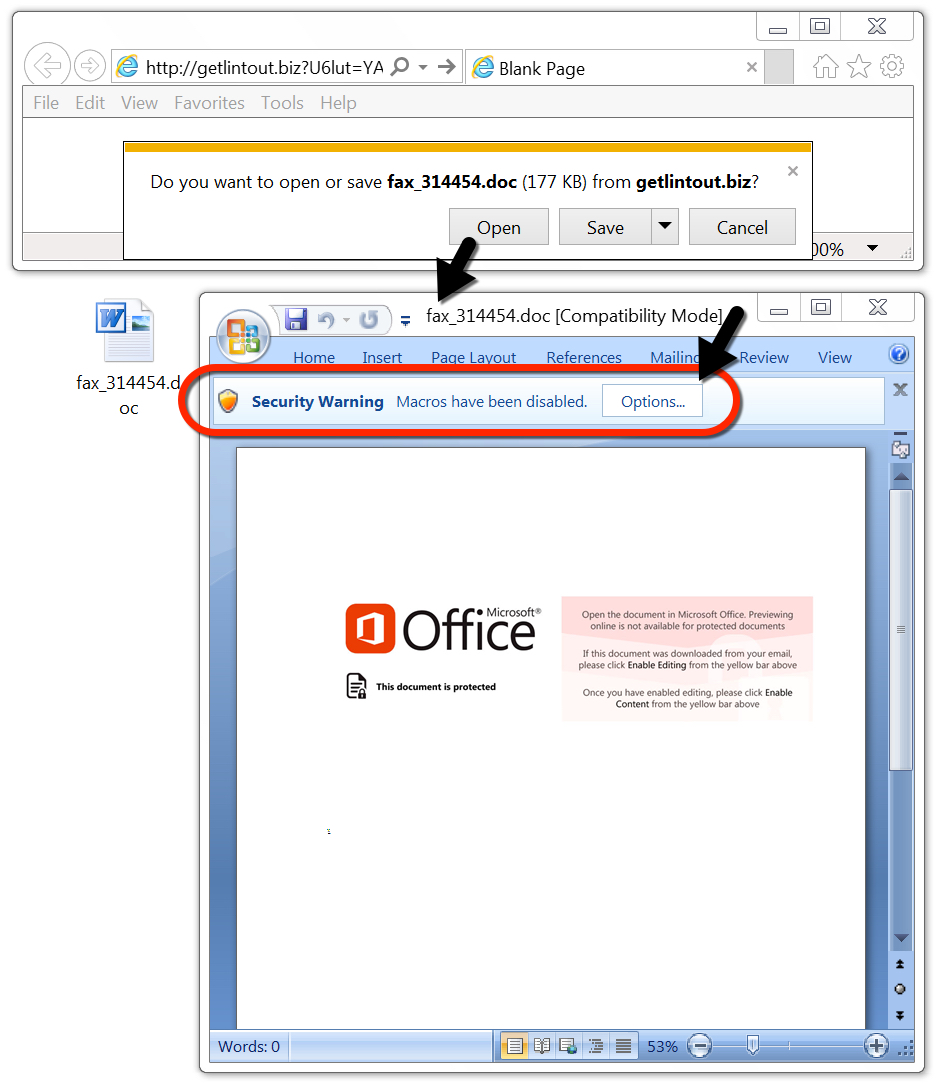
Shown above: Word doc downloaded from link in the malspam.
INFECTION TRAFFIC
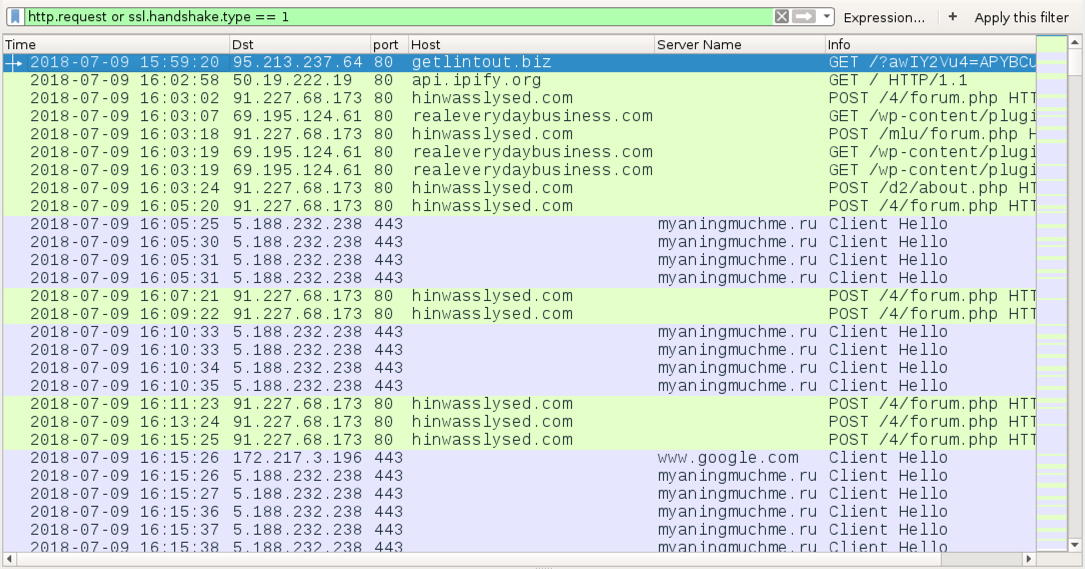
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO DOWNLOAD THE MALICIOUS WORD DOCUMENT:
- hxxp[:]//altilium[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//altilium[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//dryerventwizardcanada[.]biz?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//getlintout[.]biz?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//getthelintout[.]info?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//pbtmail[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//pbtmail[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//thedryerventwizard[.]biz?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//thedryerventwizard[.]ca?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//wegetthelintout[.]ca?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//wegetthelintout[.]net?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 95.213.237[.]64 port 80 - getlintout[.]biz - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 91.227.68[.]173 port 80 - hinwasslysed[.]com - POST /4/forum.php
- 91.227.68[.]173 port 80 - hinwasslysed[.]com - POST /mlu/about.php
- 91.227.68[.]173 port 80 - hinwasslysed[.]com - POST /d2/about.php
- 69.195.124[.]61 port 80 - realeverydaybusiness[.]com - GET /wp-content/plugins/jetpack-popular-posts/1
- 69.195.124[.]61 port 80 - realeverydaybusiness[.]com - GET /wp-content/plugins/jetpack-popular-posts/2
- 69.195.124[.]61 port 80 - realeverydaybusiness[.]com - GET /wp-content/plugins/jetpack-popular-posts/3
- 5.188.232[.]238 port 443 - myaningmuchme[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- port 80 - www.google[.]com - HTTPS/SSL/TLS traffic - probable connectivity check caused by Zeus Panda Banker
MALWARE
MALWARE RETRIEVED FROM MY INFECTED LAB HOST:
- SHA256 hash: 687582d32b7c7603a334f5e30d5f5a335624a1a19200980ec2951a205a88acb2
File size: 181,760 bytes
File name: fax_[six random digits].doc
File description: Downloaded Word doc with macro for Hancitor
- SHA256 hash: 4ba21629c84a89c6d2d5c52abcd110c551a5f9fe9008c7f0e6b43ecde0cca1f0
File size: 56,320 bytes
File location: C:\Users\[username]\AppData\Local\Temp\6C.pif
File description: Hancitor malware binary
- SHA256 hash: 111b67b802426c2e94e933761cbb6168a6730c99849244e518d11e1474218088
File size: 172,544 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda banker caused by Hancitor infection
Click here to return to the main page.