2018-07-17 - NECURS BOTNET MALSPAM USES .IQY FILES TO PUSH FLAWED AMMYY RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-17-Necurs-Botnet-malspam-2-examples.zip 1.9 kB (1,867 bytes)
- 2018-07-17-Necurs-Botnet-pushes-Flawed-Ammyy.pcap.zip 447 kB (446,718 bytes)
- 2018-07-17-malware-from-Necurs-Botnet-Flawed-Ammyy-infection.zip 321 kB (320,630 bytes)
CHAIN OF EVENTS:
- malspam --> .iqy attachment --> Flawed Ammyy RAT
EMAILS
TWO MALSPAM EXAMPLES:
- Received: from 187-7-37-160.fnses700.ipd.brasiltelecom[.]net[.]br ([187.7.37[.]160])
- Date/Time: 2018-07-17 15:28 UTC
- From: Diann <diann.greenhalgh03@didgeridoo[.]es>
- Subject: PDF_38995
- Attachment: PDF_38995.iqy
- Received: from static-190-25-217-104.static.etb[.]net[.]co ([190.25.217[.]104])
- Date/Time: 2018-07-17 15:28 UTC
- From: Diann <diann.greenhalgh03@didgeridoo[.]es>
- Subject: PDF_38995
- Attachment: PDF_38995.iqy
TRAFFIC
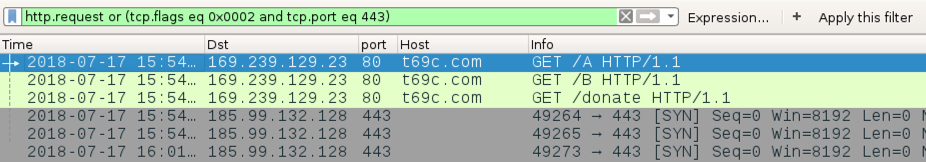
Shown above: Infection traffic filtered in Wirehshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 169.239.129[.]23 port 80 - t99c[.]com - GET/A
- 169.239.129[.]23 port 80 - t99c[.]com - GET/B
- 169.239.129[.]23 port 80 - t99c[.]com - GET/donate
- 185.99.132[.]128 port 443 - Flawed Ammyy post-infection traffic
MALWARE
ASSOCIATED MALWARE:
- SHA256 hash: 727ce79b953cdc1316fbb66decf8e3463dd0c59ac600b3fba77d1cefc35d9871
File size: 25 bytes
File name: PDF_38995.iqy
File description: Malspam attachment, Excel-based Internet Query (.iqy) file
- SHA256 hash: c2080983598643a2498d1f6ef3f1cc9dc58a784a69e3f313f18dc1b8e0afbc17
File size: 659,968 bytes
File location: C:\Users\[username]\AppData\Local\Temp\cls.exe
File description: Windows executable (.exe) file for Flawed Ammyy RAT
Click here to return to the main page.
