2018-07-21 - QUICK POST: TRICKBOT INFECTION WITH POWERSHELL EMPIRE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-21-Trickbot-infection-with-PowerShell-Empire.pcap.zip 16.3 MB (16,255,900 bytes)
- 2018-07-21-malware-and-artifacts-from-Trickbot-infection.zip 380 kB (379,681 bytes)
NOTE:
- I started this Trickbot infection in the evening on 2018-07-21 at 03:02 UTC and let it run throughout the night.
- More than 7 1/2 hours later at 10:42 UTC, I saw PowerShell Empire traffic on my infected Windows host.
- I also noticed some non-HTTP traffic on TCP port 80 starting at 07:12 UTC (see images below).
IMAGES
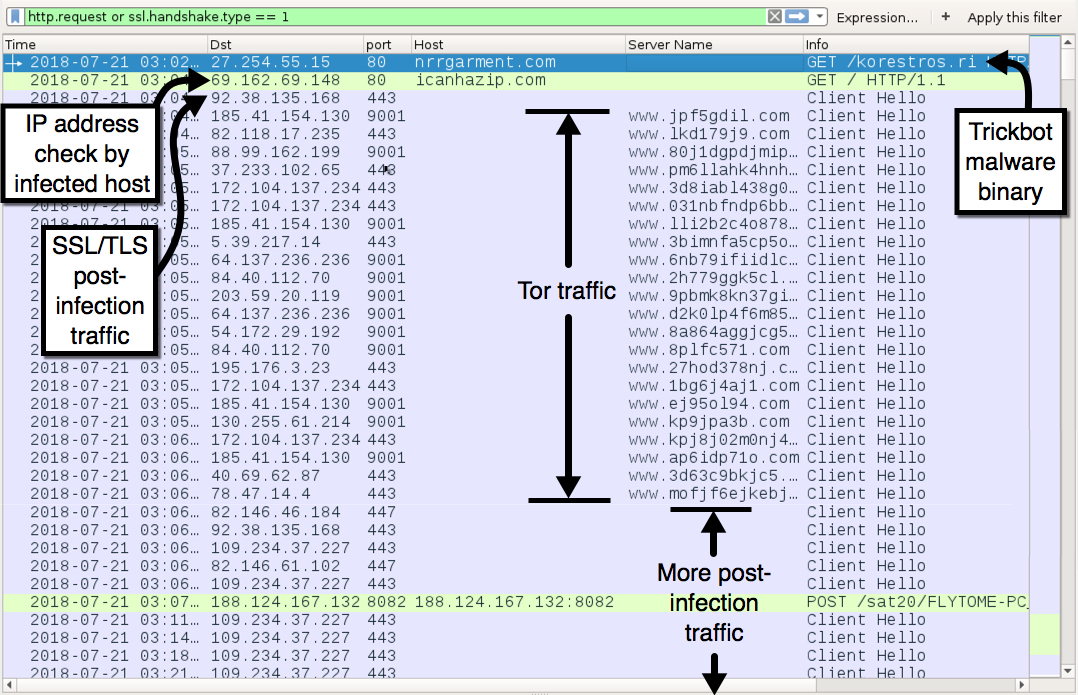
Shown above: Traffic from the infection filtered in Wireshark (1 of 3).
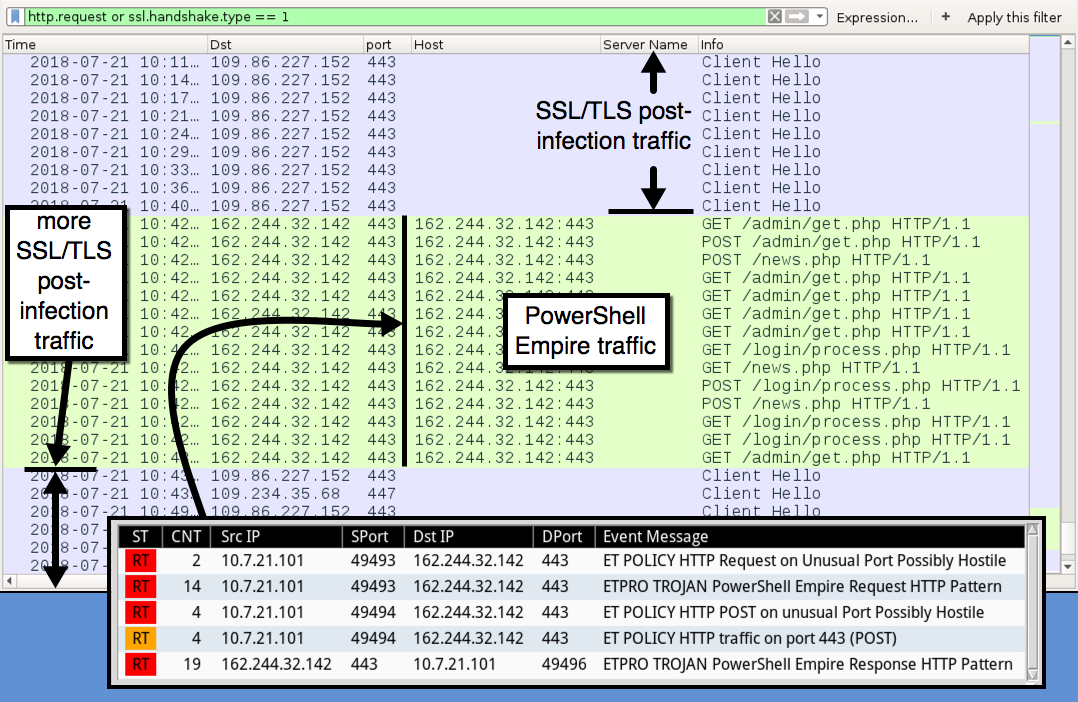
Shown above: Traffic from the infection filtered in Wireshark (2 of 3).
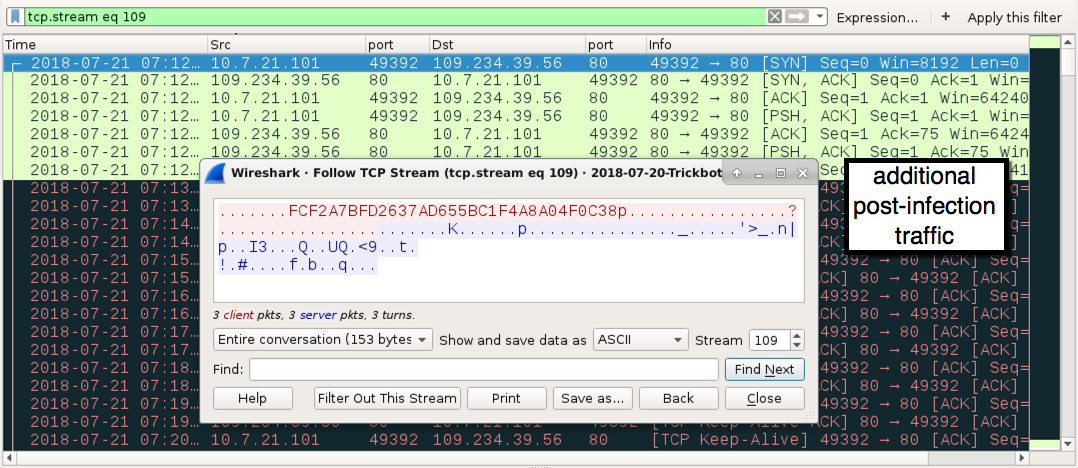
Shown above: Traffic from the infection filtered in Wireshark (3 of 3).
OTHER NOTES
SOME OF THE POST INFECTION TRAFFIC:
- 109.234.39[.]56 port 80 - post-infection traffic (not HTTP) related to this Trickbot infection
- 162.244.32[.]142 port 443 - 162.244.32[.]142:443 - GET /admin/get.php - PowerShell Empire traffic
- 162.244.32[.]142 port 443 - 162.244.32[.]142:443 - POST /admin/get.php - PowerShell Empire traffic
- 162.244.32[.]142 port 443 - 162.244.32[.]142:443 - GET /login/process.php - PowerShell Empire traffic
- 162.244.32[.]142 port 443 - 162.244.32[.]142:443 - POST /login/process.php - PowerShell Empire traffic
- 162.244.32[.]142 port 443 - 162.244.32[.]142:443 - GET /news.php - PowerShell Empire traffic
- 162.244.32[.]142 port 443 - 162.244.32[.]142:443 - POST /news.php - PowerShell Empire traffic
- There are several Trickbot-specific indicators for this infection not listed above. Review the pcap and malware archives for more details.
Click here to return to the main page.
