2018-07-31 - TWO INFECTIONS: EMOTET WITH TRICKBOT & EMOTET WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-31-three-Emotet-malspam-examples.zip 4.4 kB (4,417 bytes)
- 2018-07-30-Emotet-malspam-0825-UTC.eml (967 bytes)
- 2018-07-30-Emotet-malspam-2031-UTC.eml (7,116 bytes)
- 2018-07-31-Emotet-malspam-0945-UTC.eml (1,347 bytes)
- 2018-07-31-Emotet-infection-traffic-both-pcaps.zip 7.5 MB (7,527,624 bytes)
- 2018-07-31-Emotet-infection-with-Trickbot.pcap (5,767,774 bytes)
- 2018-07-31-Emotet-infection-with-Zeus-Panda-Banker.pcap (2,336,550 bytes)
- 2018-07-31-malware-associated-with-Emotet-infection.zip 881 kB (881,027 bytes)
- 2018-07-31-Emotet-malware-binary-1-of-3.exe (131,584 bytes)
- 2018-07-31-Emotet-malware-binary-2-of-3.exe (131,584 bytes)
- 2018-07-31-Emotet-malware-binary-3-of-3.exe (133,120 bytes)
- 2018-07-31-Trickbot-retrieved-suing-Emotet-infection.exe (327,168 bytes)
- 2018-07-31-Zeus-Panda-Banker-retrieved-suing-Emotet-infection.exe (136,704 bytes)
- 2018-07-31-downloaded-Word-doc-with-macro-for-Emotet-1-of-4.doc (101,248 bytes)
- 2018-07-31-downloaded-Word-doc-with-macro-for-Emotet-2-of-4.doc (93,440 bytes)
- 2018-07-31-downloaded-Word-doc-with-macro-for-Emotet-3-of-4.doc (100,224 bytes)
- 2018-07-31-downloaded-Word-doc-with-macro-for-Emotet-4-of-4.doc (88,576 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain and URLs:
- humoronoff[.]top
- hxxp[:]//aktuelldata-ev[.]de/files/US/Address-Update/
- hxxp[:]//bodycorporatecollective[.]com[.]au/newsletter/EN_en/Address-Update/
- hxxp[:]//canadary[.]com/JyblntYRbo/
- hxxp[:]//connievoigt[.]cl/sites/Rechnung/FORM/Rechnung-UX-31-60671/
- hxxp[:]//consultorialyceum[.]com[.]br/loDjMtPpTaavXhB3pME9/
- hxxp[:]//eco3academia[.]com[.]br/default/de/Zahlung/RechnungsDetails-DW-03-40777/
- hxxp[:]//elkasen.szczecin[.]pl/newsletter/En_us/OVERDUE-ACCOUNT/invoice/
- hxxp[:]//hostile-gaming[.]fr/DHL-Express/US/
- hxxp[:]//it-club[.]kg/doc/En/Payment-details/
- hxxp[:]//kermain-valley[.]com/default/Rechnungs-Details/FORM/RechnungScan-BBK-64-93981/
- hxxp[:]//khanandmuezzin[.]com/doc/En/Invoice-for-sent/Account-35484/
- hxxp[:]//klvanrental[.]com[.]my/djwVH7ITcXQs63j0Nu/
- hxxp[:]//milesaway[.]pl/Jul2018/US/Payment-with-a-new-address/
- hxxp[:]//myworkathomesite[.]com/files/US_us/Payment-details/
- hxxp[:]//new.allfn[.]com/sites/En/New-Address/
- hxxp[:]//nz.dilmah[.]com/doc/US/Change-of-Address/
- hxxp[:]//ordos[.]su/DHL-Express/En_us/
- hxxp[:]//prosourcedpartners[.]com/Jul2018/US/New-payment-details-and-address-update/
- hxxp[:]//relib[.]fr/Jul2018/Rech/Fakturierung/RechnungsDetails-YQ-22-72307/
- hxxp[:]//restauracja.wislaa[.]pl/newsletter/EN_en/New-payment-details-and-address-update/
- hxxp[:]//satyam[.]cl/plugins/doc/Rechnungs-Details/Rechnungszahlung/Erinnerung-an-die-Rechnungszahlung-LMW-42-41967/
- hxxp[:]//sesisitmer[.]com/wp-content/Q90wNLaF01HWQa6oHAp/
- hxxp[:]//sevgidugunsalonu[.]net/files/En_us/Address-Changed/
- hxxp[:]//shopinterbuild[.]com/sqlbak/9rSN69yzI4Vdv894/
- hxxp[:]//silver-n-stone[.]com/default/En/Payment-details/
- hxxp[:]//solvensplus[.]co[.]rs/DHL-Express/En/
- hxxp[:]//theboomworks[.]com/default/En_us/Address-and-payment-info/
- hxxp[:]//thonglorpetblog[.]com/petcare/DHL-Tracking/EN_en/
- hxxp[:]//tiendaepica[.]com/newsletter/US/Address-Update/
- hxxp[:]//www.ultigamer[.]com/wp-admin/includes/Jul2018/Dokumente/Hilfestellung/Rechnungszahlung-TY-65-37307/
- hxxp[:]//weliketomoveit[.]ca/default/EN_en/Address-Update/
- hxxp[:]//www.shopinterbuild[.]com/sqlbak/9rSN69yzI4Vdv894/
- hxxp[:]//agrocoeli[.]com/chfEBi
- hxxp[:]//canevazzi[.]com[.]br/R7v
- hxxp[:]//challengerballtournament[.]com/E
- hxxp[:]//consultoresyempresas[.]com/QQRLe5a
- hxxp[:]//cranmorelodge[.]co[.]uk/aU0o0
- hxxp[:]//fundacionafanic[.]com/TsZLHoZU
- hxxp[:]//fufu[.]com[.]mx/UQANpB
- hxxp[:]//nonglek[.]net/7CR
- hxxp[:]//tonysmarineservice[.]co[.]uk/gbsi00
- hxxp[:]//www.leathershop77[.]com/bweFbo9
- hxxp[:]//188.124.167[.]132:8082/mon1/
- hxxp[:]//71.202.205[.]235/whoami.php
EMAILS
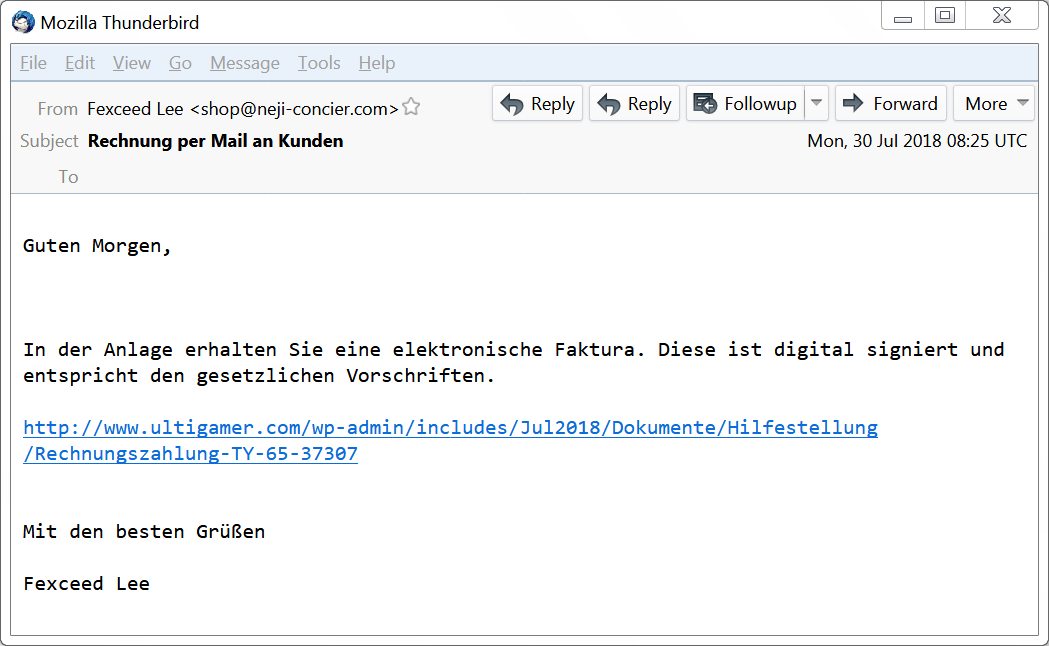
Shown above: Example of the malspam (1 of 3).

Shown above: Example of the malspam (2 of 3).

Shown above: Example of the malspam (3 of 3).
INFECTION TRAFFIC
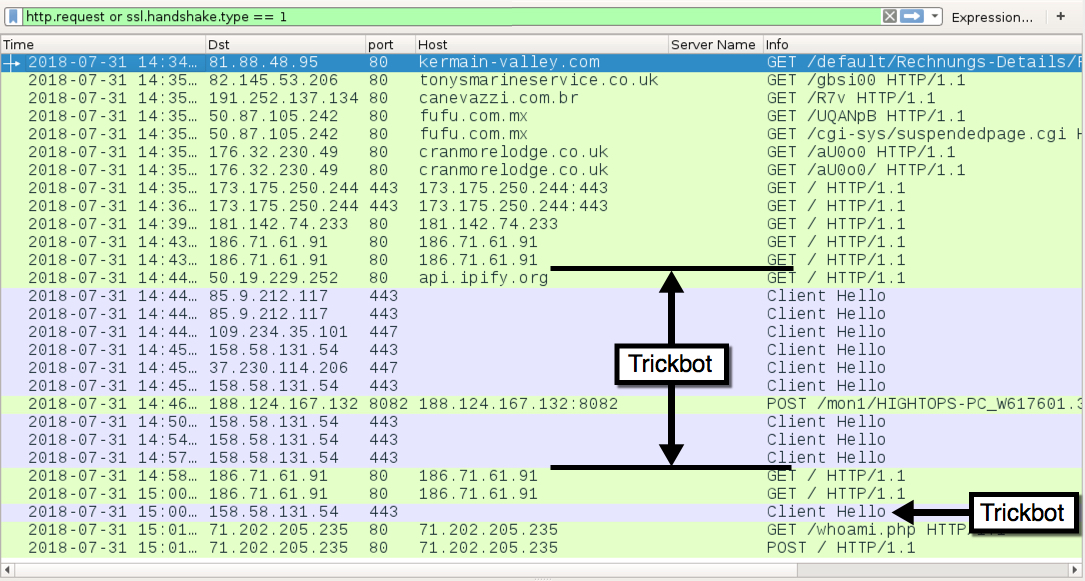
Shown above: Traffic from an infection filtered in Wireshark (Emotet + Trickbot).
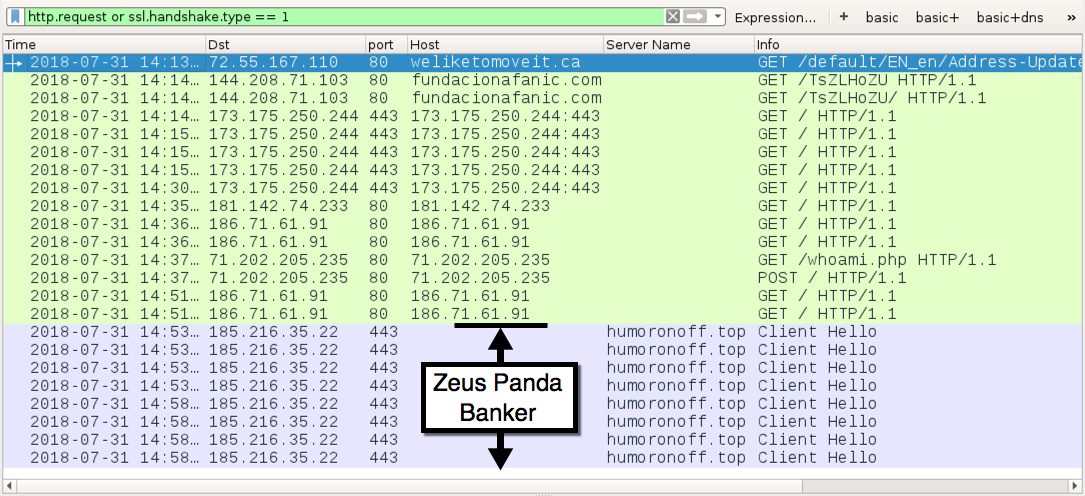
Shown above: Traffic from an infection filtered in Wireshark (Emotet + Zeus Panda Banker).
LINKS IN THE EMAILS TO DOWNLOAD THE MALICIOUS WORD DOCUMENT:
- hxxp[:]//aktuelldata-ev[.]de/files/US/Address-Update/
- hxxp[:]//bodycorporatecollective[.]com[.]au/newsletter/EN_en/Address-Update/
- hxxp[:]//canadary[.]com/JyblntYRbo/
- hxxp[:]//connievoigt[.]cl/sites/Rechnung/FORM/Rechnung-UX-31-60671/
- hxxp[:]//consultorialyceum[.]com[.]br/loDjMtPpTaavXhB3pME9/
- hxxp[:]//eco3academia[.]com[.]br/default/de/Zahlung/RechnungsDetails-DW-03-40777/
- hxxp[:]//elkasen.szczecin[.]pl/newsletter/En_us/OVERDUE-ACCOUNT/invoice/
- hxxp[:]//hostile-gaming[.]fr/DHL-Express/US/
- hxxp[:]//it-club[.]kg/doc/En/Payment-details/
- hxxp[:]//kermain-valley[.]com/default/Rechnungs-Details/FORM/RechnungScan-BBK-64-93981/
- hxxp[:]//khanandmuezzin[.]com/doc/En/Invoice-for-sent/Account-35484/
- hxxp[:]//klvanrental[.]com[.]my/djwVH7ITcXQs63j0Nu/
- hxxp[:]//milesaway[.]pl/Jul2018/US/Payment-with-a-new-address/
- hxxp[:]//myworkathomesite[.]com/files/US_us/Payment-details/
- hxxp[:]//new.allfn[.]com/sites/En/New-Address/
- hxxp[:]//nz.dilmah[.]com/doc/US/Change-of-Address/
- hxxp[:]//ordos[.]su/DHL-Express/En_us/
- hxxp[:]//prosourcedpartners[.]com/Jul2018/US/New-payment-details-and-address-update/
- hxxp[:]//relib[.]fr/Jul2018/Rech/Fakturierung/RechnungsDetails-YQ-22-72307/
- hxxp[:]//restauracja.wislaa[.]pl/newsletter/EN_en/New-payment-details-and-address-update/
- hxxp[:]//satyam[.]cl/plugins/doc/Rechnungs-Details/Rechnungszahlung/Erinnerung-an-die-Rechnungszahlung-LMW-42-41967/
- hxxp[:]//sesisitmer[.]com/wp-content/Q90wNLaF01HWQa6oHAp/
- hxxp[:]//sevgidugunsalonu[.]net/files/En_us/Address-Changed/
- hxxp[:]//shopinterbuild[.]com/sqlbak/9rSN69yzI4Vdv894/
- hxxp[:]//silver-n-stone[.]com/default/En/Payment-details/
- hxxp[:]//solvensplus[.]co[.]rs/DHL-Express/En/
- hxxp[:]//theboomworks[.]com/default/En_us/Address-and-payment-info/
- hxxp[:]//thonglorpetblog[.]com/petcare/DHL-Tracking/EN_en/
- hxxp[:]//tiendaepica[.]com/newsletter/US/Address-Update/
- hxxp[:]//www.ultigamer[.]com/wp-admin/includes/Jul2018/Dokumente/Hilfestellung/Rechnungszahlung-TY-65-37307/
- hxxp[:]//weliketomoveit[.]ca/default/EN_en/Address-Update/
- hxxp[:]//www.shopinterbuild[.]com/sqlbak/9rSN69yzI4Vdv894/
URLS FOR THE FOLLOW-UP EMOTET MALWARE:
- hxxp[:]//agrocoeli[.]com/chfEBi
- hxxp[:]//canevazzi[.]com[.]br/R7v
- hxxp[:]//challengerballtournament[.]com/E
- hxxp[:]//consultoresyempresas[.]com/QQRLe5a
- hxxp[:]//cranmorelodge[.]co[.]uk/aU0o0
- hxxp[:]//fundacionafanic[.]com/TsZLHoZU
- hxxp[:]//fufu[.]com[.]mx/UQANpB
- hxxp[:]//nonglek[.]net/7CR
- hxxp[:]//tonysmarineservice[.]co[.]uk/gbsi00
- hxxp[:]//www.leathershop77[.]com/bweFbo9
TRAFFIC FROM AN INFECTED WINDOWS HOST (EMOTET + TRICKBOT):
- 81.88.48[.]95 port 80 - kermain-valley[.]com - GET /default/Rechnungs-Details/FORM/RechnungScan-BBK-64-93981/
- 82.145.53[.]206 port 80 - tonysmarineservice[.]co[.]uk - GET /gbsi00
- 191.252.137[.]134 port 80 - canevazzi[.]com[.]br - GET /R7v
- 50.87.105[.]242 port 80 - fufu[.]com[.]mx - GET /UQANpB
- 50.87.105[.]242 port 80 - fufu[.]com[.]mx - GET /cgi-sys/suspendedpage.cgi
- 176.32.230[.]49 port 80 - cranmorelodge[.]co[.]uk - GET /aU0o0
- 176.32.230[.]49 port 80 - cranmorelodge[.]co[.]uk - GET /aU0o0/
- 173.175.250[.]244 port 443 - 173.175[.]250.244:443 - GET /
- 181.142.74[.]233 port 80 - 181.142.74[.]233 - GET /
- 186.71.61[.]91 port 80 - 186.71.61[.]91 - GET /
- 50.19.229[.]252 port 80 - api.ipify[.]org - GET / (IP address check caused by Trickbot)
- 85.9.212[.]117 port 443 - SSL/TLS traffic caused by Trickbot
- 109.234.35[.]101 port 447 - SSL/TLS traffic caused by Trickbot
- 158.58.131[.]54 port 443 - SSL/TLS traffic caused by Trickbot
- 37.230.114[.]206 port 447 - SSL/TLS traffic caused by Trickbot
- 188.124.167[.]132 port 8082 - 188.124.167[.]132:8082 - POST /mon1/[string with Trickbot-infected host info]
- 74.141.205[.]116 port 443 - attempted TCP connections, but no response from the server
- 71.202.205[.]235 port 80 - 71.202.205[.]235 - GET /whoami.php
- 71.202.205[.]235 port 80 - 71.202.205[.]235 - POST /
TRAFFIC FROM AN INFECTED WINDOWS HOST (EMOTET + ZEUS PANDA BANKER):
- 72.55.167[.]110 port 80 - weliketomoveit[.]ca - GET /default/EN_en/Address-Update/
- 144.208.71[.]103 port 80 - fundacionafanic[.]com - GET /TsZLHoZU
- 144.208.71[.]103 port 80 - fundacionafanic[.]com - GET /TsZLHoZU/
- 173.175.250[.]244 port 443 - 173.175.250[.]244:443 - GET /
- 181.142.74[.]233 port 80 - 181.142.74[.]233 - GET /
- 186.71.61[.]91 port 80 - 186.71.61[.]91 - GET /
- 74.141.205[.]116 port 443 - attempted TCP connections, but no response from the server
- 71.202.205[.]235 port 80 - 71.202.205[.]235 - GET /whoami.php
- 71.202.205[.]235 port 80 - 71.202.205[.]235 - POST /
- 186.71.61[.]91 port 80 - 186.71.61[.]91 - GET /
- 185.216.35[.]22 port 443 - humoronoff[.]top - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
MALWARE
SHA256 HASHES FOR THE INITIAL WORD DOCUMENTS:
- 84e0cff85d83a1b143026811ff2963411f7d91f54520a6a5ac9e2dce47d0c97f
- db8419615c36095c6d01676af677a983827a52ed6d2d42335308b3cfc5c7b7ea
- dec66f17d2a766f0eba273d27f53155a81818a28425318a07055ae79f94337f9
- e82e999ee89cb83818e29fece183fe8649671e8bfad1e042d347fed827177765
SHA256 HASHES FOR THE FOLLOW-UP EMOTET MALWARE:
- 10810ac39fa23e7e64330b95724cd649040729705b9fbeba03064fb81ab6346a
- e0295b10fb3dd50e67a54d05ebd20e6b5367d47c5e4baf3cacddb24845fd570b
- e28f181c92cb68931972ec0b7c61b3fe54ba76d12c5cd251777bde6f9f01ce09
SHA256 HASH FOR TRICKBOT CAUSED BY EMOTET INFECTION (GTAG: MON1):
- 3dc3fa64dd957bfe083203a98e6a7af8494bf5de444428ad6fa2da55b9891436
SHA256 HASH FOR ZEUS PANDA BANKER CAUSED BY EMOTET INFECTION:
- 20f4445b40dc0cd1830dee6031a7342284e51dc4c399d331507b28f74ba0727b
Click here to return to the main page.
