2018-08-07 - QUICK POST: TRICKBOT (GTAG: TOT284) MOVES FROM CLIENT TO DC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2018-08-07-Trickbot-moves-from-client-to-DC.pcap.zip 11.7 MB (11,747,471 bytes)
- Zip archive of the malware & artifacts: 2018-08-07-Trickbot-malware.zip 607 kB (606,950 bytes)
NOTES:
- Found today's Trickbot gtag tot284 sample on VirusTotal, but I don't know where it originally came from.
- Today's example spread from an infected Windows client on 172.16.10[.]191 to its domain controller at 172.16.10[.]2.
IMAGES
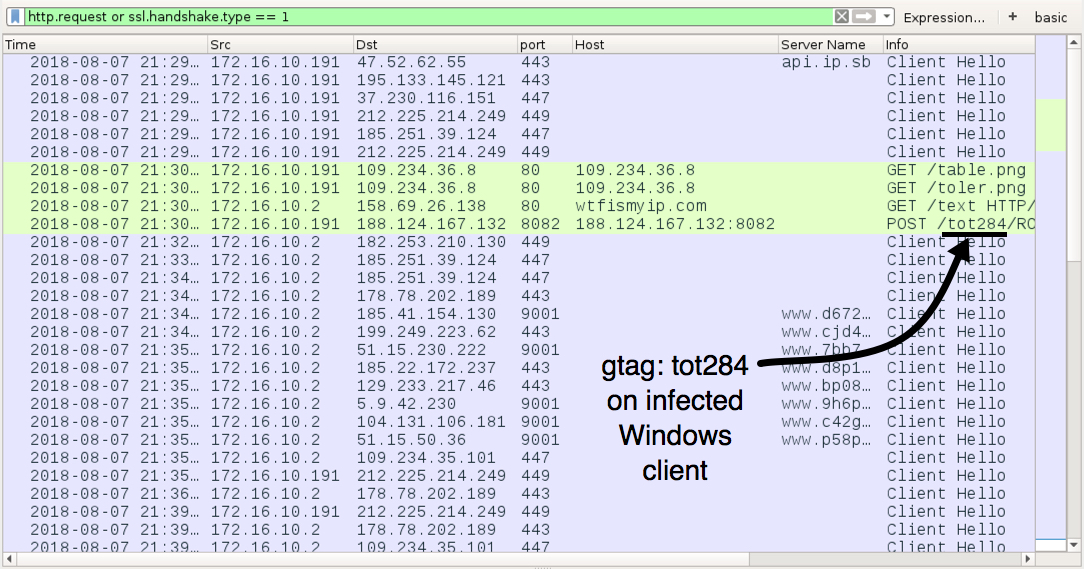
Shown above: Traffic from the infection filtered in Wireshark.
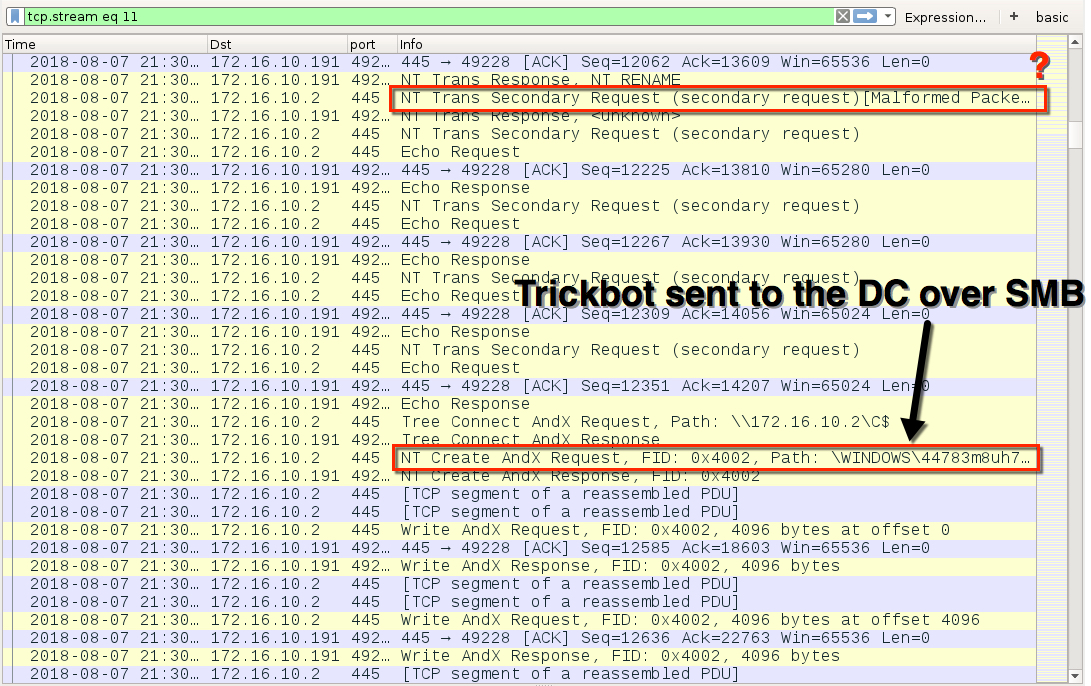
Shown above: Trickbot sent from Windows client to the DC over SMB on TCP port 445.
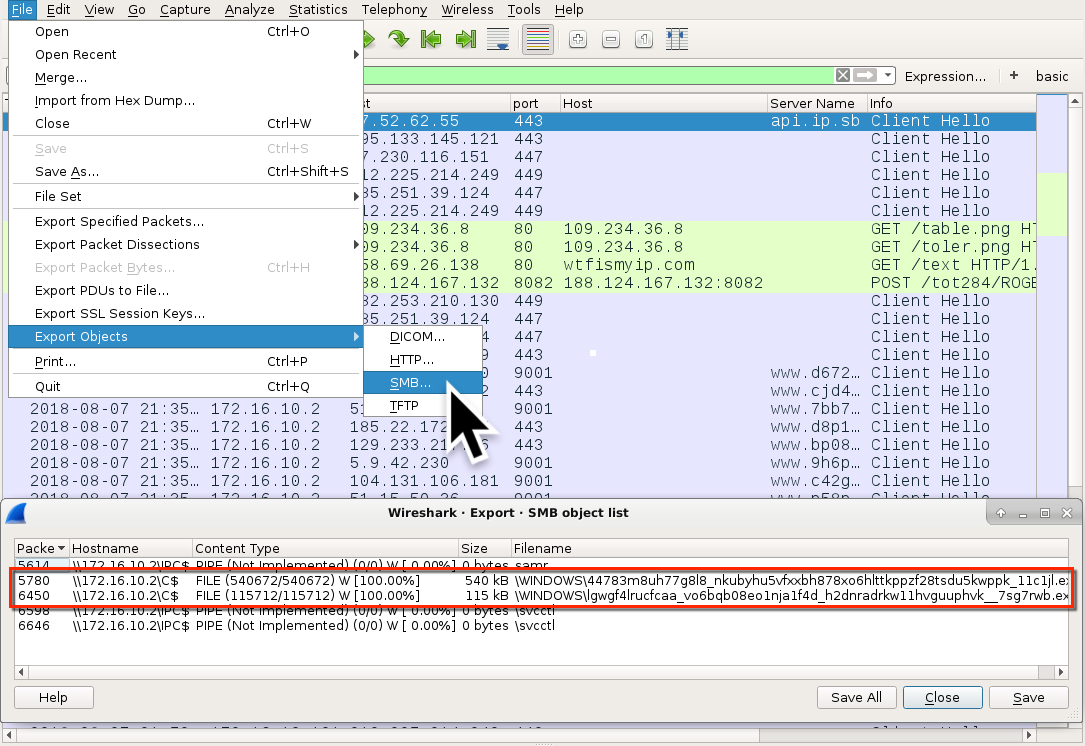
Shown above: In Wireshark, you can export the Trickbot malware from the SMB traffic as shown above.
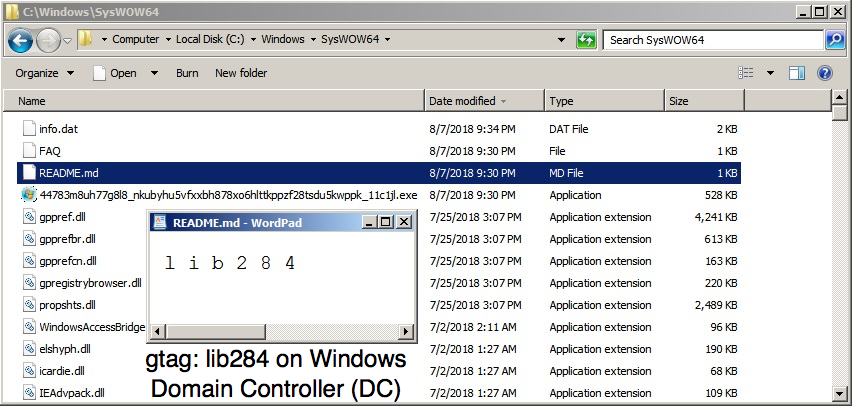
Shown above: Trickbot on the DC shows as gtag lib284.
Click here to return to the main page.
