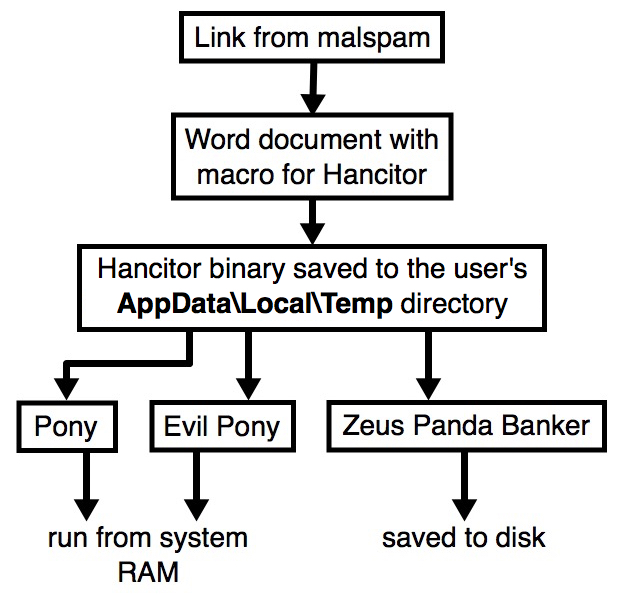
2018-08-16 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-08-16-Hancitor-malspam-example.eml.zip 2 kB (2,031 bytes)
- 2018-08-16-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 526 kB (525,824 bytes)
- 2018-08-16-malware-from-Hancitor-infection.zip 334 kB (333,803 bytes)
NOTES:
- The block list contains additional info first reported in the VirusBay entry for the associated Word document, as well as some other sources.
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- backhomebail[.]com
- biggaybrunch[.]info
- biggaybrunch[.]net
- biggaybrunch[.]org
- clearrochester[.]com
- dtvrochester[.]com
- gaymovetodenver[.]com
- glbtmovetodenver[.]com
- hatcreekurnco[.]com
- lgbtmovetodenver[.]com
- omnibox[.]me
- omnibox[.]mobi
- outcolorado[.]info
- outcolorado[.]net
- outcolorado[.]org
- smarthomeiconnect[.]com
- wildblueny[.]com
- hxxp[:]//alyssaritchey[.]com/wp-content/plugins/title-remover/1
- hxxp[:]//alyssaritchey[.]com/wp-content/plugins/title-remover/2
- hxxp[:]//alyssaritchey[.]com/wp-content/plugins/title-remover/3
- hxxp[:]//community-growth[.]org/wp-content/plugins/cryout-theme-settings/inc/1
- hxxp[:]//community-growth[.]org/wp-content/plugins/cryout-theme-settings/inc/2
- hxxp[:]//community-growth[.]org/wp-content/plugins/cryout-theme-settings/inc/3
- hxxp[:]//taxgals[.]com/wp-content/themes/twentythirteen/inc/1
- hxxp[:]//taxgals[.]com/wp-content/themes/twentythirteen/inc/2
- hxxp[:]//taxgals[.]com/wp-content/themes/twentythirteen/inc/3
- soutmestiho[.]com
- enbetishect[.]ru
- gesinaleft[.]ru
- inghapwilhe[.]ru
HEADERS FROM A MALSPAM EXAMPLE
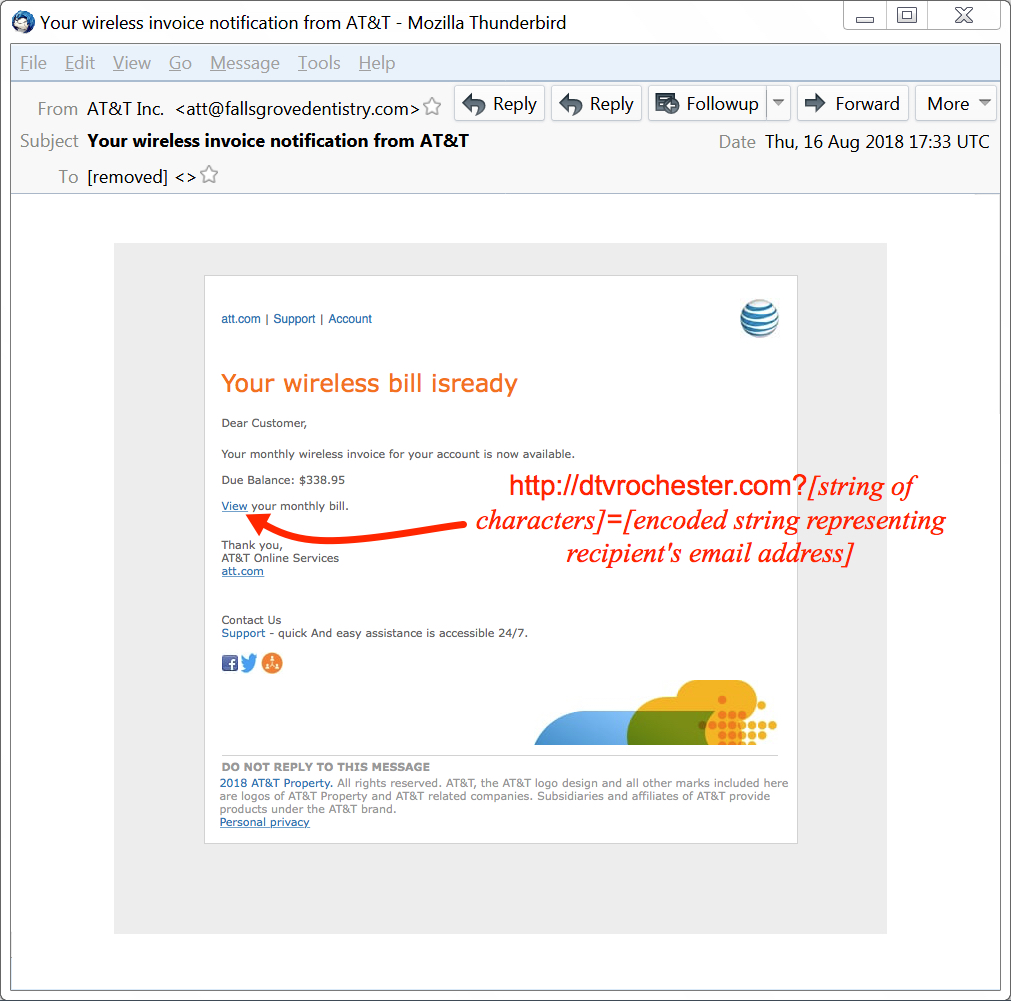
Shown above: Screenshot from one of the emails.
Received: from fallsgrovedentistry[.]com ([65.98.129[.]162]) by [removed] for [removed];
Thu, 16 Aug 2018 17:33:44 +0000 (UTC)
Message-ID: <69C3514D.706FA590@fallsgrovedentistry[.]com>
Date: Thu, 16 Aug 2018 10:33:46 -0700
Reply-To: "AT&T Inc. " <att@fallsgrovedentistry[.]com>
From: "AT&T Inc. " <att@fallsgrovedentistry[.]com>
X-Mailer: iPhone Mail (11D201)
X-Accept-Language: en-us
MIME-Version: 1.0
TO: [removed]
Subject: Your wireless invoice notification from AT&T
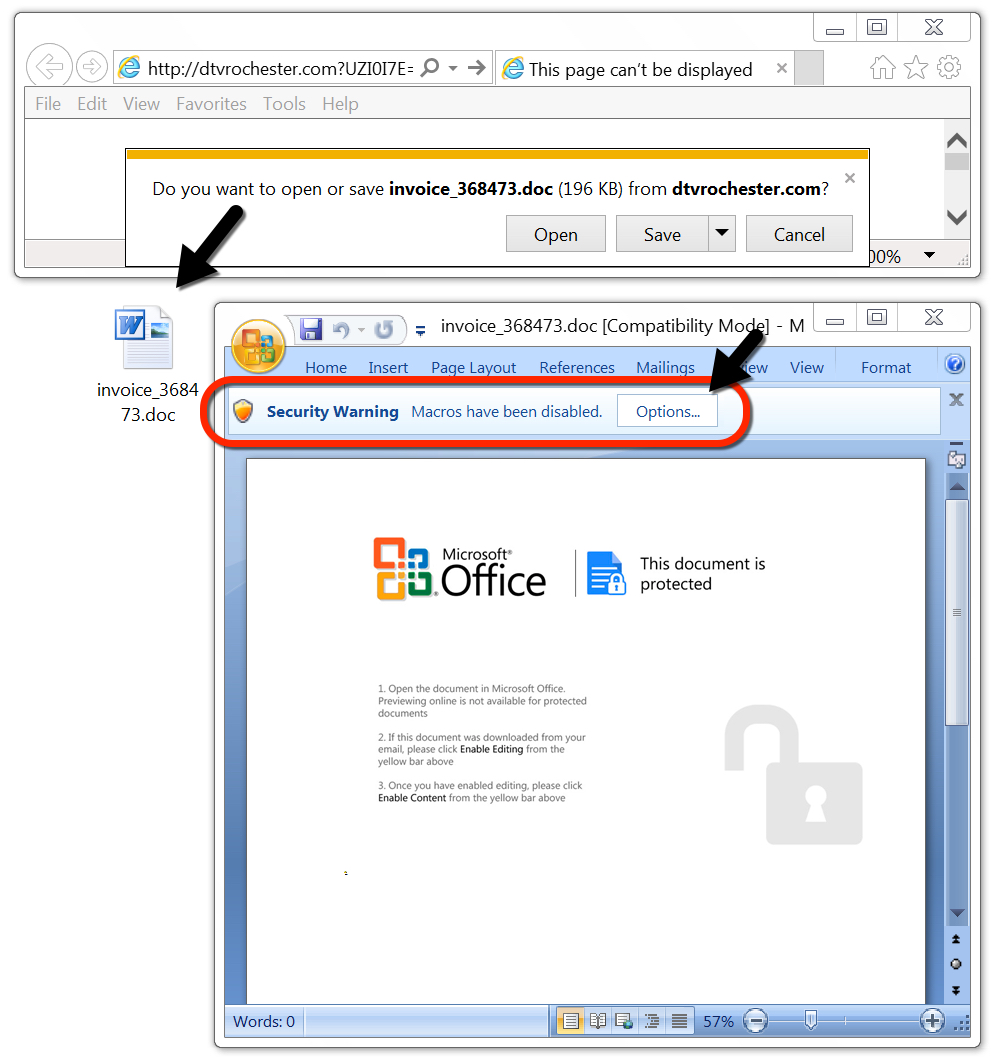
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
LINKS IN THE EMAILS TO DOWNLOAD THE WORD DOCUMENT:
- hxxp[:]//backhomebail[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//biggaybrunch[.]info?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//biggaybrunch[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//biggaybrunch[.]org?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//clearrochester[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//dtvrochester[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//gaymovetodenver[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//glbtmovetodenver[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hatcreekurnco[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//lgbtmovetodenver[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//omnibox[.]me?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//omnibox[.]mobi?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//outcolorado[.]info?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//outcolorado[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//outcolorado[.]org?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//smarthomeiconnect[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//wildblueny[.]com?[string of characters]=[encoded string representing recipient's email address]
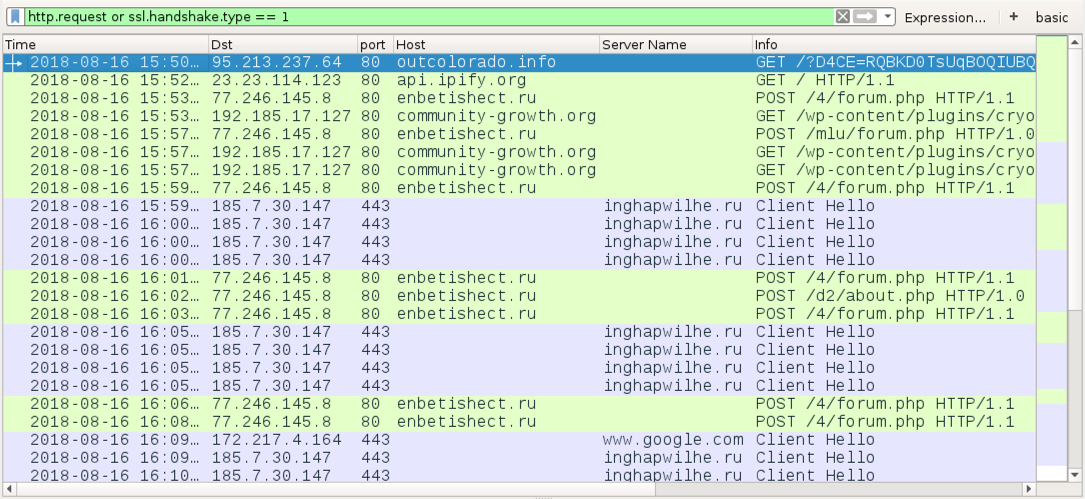
Shown above: Traffic from an infection filtered in Wireshark.
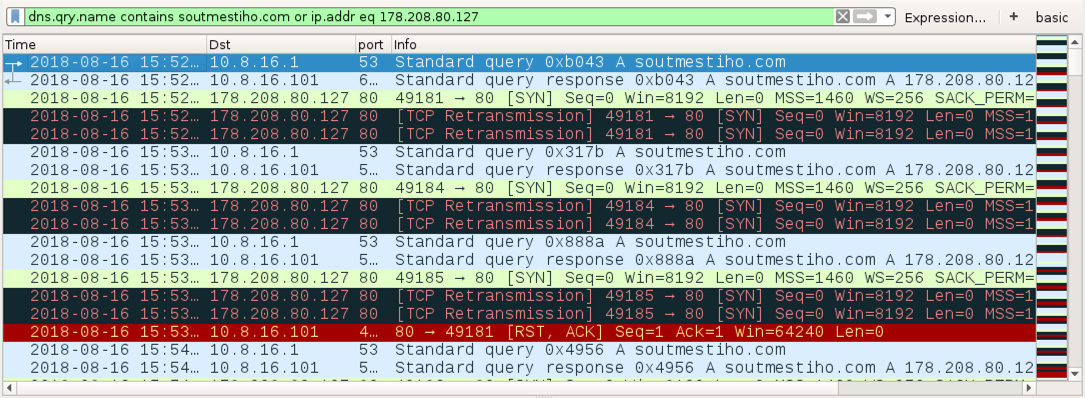
Shown above: Traffic from from failed TCP connections by soutmestiho.com filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 95.213.237[.]64 port 80 - outcolorado[.]info - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 178.208.80[.]127 port 80 - soutmestiho[.]com - Attempted TCP connections, but no response or RST from the server
- 77.246.145[.]8 port 80 - enbetishect[.]ru - POST /4/forum.php
- 77.246.145[.]8 port 80 - enbetishect[.]ru - POST /mlu/about.php
- 77.246.145[.]8 port 80 - enbetishect[.]ru - POST /d2/about.php
- 192.185.17[.]127 port 80 - community-growth[.]org - GET /wp-content/plugins/cryout-theme-settings/inc/1
- 192.185.17[.]127 port 80 - community-growth[.]org - GET /wp-content/plugins/cryout-theme-settings/inc/2
- 192.185.17[.]127 port 80 - community-growth[.]org - GET /wp-content/plugins/cryout-theme-settings/inc/3
- 185.7.30[.]147 port 443 - inghapwilhe[.]ru - HTTPS/SSL/TLS traffic [Zeus Panda Banker]
- port 443 - www.google[.]com - connectivity check by infected Windows host [Zeus Panda Banker]
FILE HASHES
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: e1a2cdab779ee1237c638fea4b9d4dca0591d16f9e4fc208a7486fd6d26523cf
File size: 201,216 bytes
File name: invoice_142098.doc (random file names)
File description: Word doc downloaded from a link in Hancitor malspam. Doc has macro to retreive Hancitor.
- SHA256 hash: a388a50081111d0252eb4c638421ad6b5d13dee6f2e374b0c3a40138227f9ac0
File size: 58,880 bytes
File location: C:\Users\[username]\AppData\Local\Temp\6.exe
File location: C:\Users\[username]\AppData\Local\Temp\6.pif
File description: Hancitor malware binary retrieved by macro in downloaded Word doc
- SHA256 hash: ad7b21f9c14c49ea28f7e98a8e3b44973446342537d9817ec91c13681bae0023
File size: 218,624 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random file name].exe
File description: Zeus Panda Banker on 2018-08-16 caused by Hancitor infection
Click here to return to the main page.