2018-08-16 - TWO EMOTET INFECTIONS WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-08-16-Emotet-malspam-9-email-examples.zip 421 kB (421,071 bytes)
- Aug 16 2018 2018-08-14-Emotet-malspam-0942-UTC.eml (164987 bytes)
- 2018-08-14-Emotet-malspam-1028-UTC.eml (159686 bytes)
- 2018-08-14-Emotet-malspam-1430-UTC.eml (4390 bytes)
- 2018-08-15-Emotet-malspam-0523-UTC.eml (169307 bytes)
- 2018-08-15-Emotet-malspam-0730-UTC.eml (165977 bytes)
- 2018-08-15-Emotet-malspam-1055-UTC.eml (187631 bytes)
- 2018-08-15-Emotet-malspam-1236-UTC.eml (2027 bytes)
- 2018-08-15-Emotet-malspam-1457-UTC.eml (2862 bytes)
- 2018-08-16-Emotet-malspam-0905-UTC.eml (125152 bytes)
- 2018-08-16-Emotet-infections-with-Zeus-Panda-Banker-2-pcaps.zip 5.6 MB (5,578,029 bytes)
- 2018-08-15-Emotet-infection-traffic-with-Zeus-Panda-Banker.pcap (1,583,713 bytes)
- 2018-08-16-Emotet-infection-traffic-with-Zeus-Panda-Banker.pcap (4,929,206 bytes)
- 2018-08-16-malware-from-Emotet-infections.zip 1.2 MB (1,153,676 bytes)
- 2018-08-15-Emotet-malwre-binary.exe (176,128 bytes)
- 2018-08-15-Zeus-Panda-Banker-caused-by-Emotet-infection.exe (249,344 bytes)
- 2018-08-15-downloaded-Word-doc-with-macro-for-Emotet.doc (166,016 bytes)
- 2018-08-16-Emotet-malwre-binary-1-of-2.exe (172,032 bytes)
- 2018-08-16-Emotet-malwre-binary-2-of-2.exe (176,128 bytes)
- 2018-08-16-Zeus-Panda-Banker-caused-by-Emotet-infection.exe (225,280 bytes)
- 2018-08-16-downloaded-Word-doc-with-macro-for-Emotet.doc (93,056 bytes)
- 9P3018_2018_08_15.doc (135,936 bytes)
- IF80406_2018_08_14.doc (119,296 bytes)
- MCO891938097_2018_08_15.doc (119,680 bytes)
- Rech 44177315677.doc (90,496 bytes)
- Rechnung 06521887908.doc (115,712 bytes)
- Rechnungs-Details TOAS - 011-AT0212.doc (122,240 bytes)
NOTES:
- Still seeing Zeus Panda Banker caused by Emotet, very similar to what I posted earlier this week on 2018-08-14.
- This ties into a recent Unit 42 blog I wrote last month, Malware Team Up: Malspam Pushing Emotet + Trickbot.
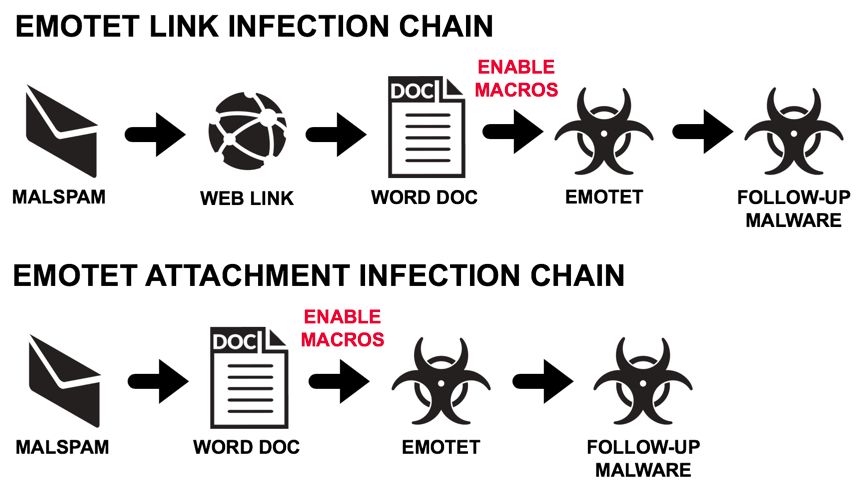
Shown above: Flow chart typical Emotet malspam infections.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//whybowl.thebotogs[.]com/Wellsfargo/Commercial/Aug-15-2018
- hxxp[:]//sharpconstructiontx[.]com/Wellsfargo/Business/Aug-14-2018
- hxxp[:]//akademia.gnatyshyn[.]pl/WellsFargo/Smallbusiness/Aug-15-2018
- hxxp[:]//akademia.gnatyshyn[.]pl/WellsFargo/Smallbusiness/Aug-15-2018
- hxxp[:]//soportek[.]cl/FAm4eZY
- hxxp[:]//duncanfalk[.]com/Wellsfargo/biz/Commercial/Aug-16-2018
- hxxp[:]//psychedelicsociety[.]org[.]au/3mw
- theeunload[.]website
- mykeeptake[.]xyz
- hxxp[:]//206.188.160[.]216:443/whoami.php
DATA FROM 9 MALSPAM EXAMPLES

Shown above: An example of Emotet malspam from Tuesday 2018-08-14.
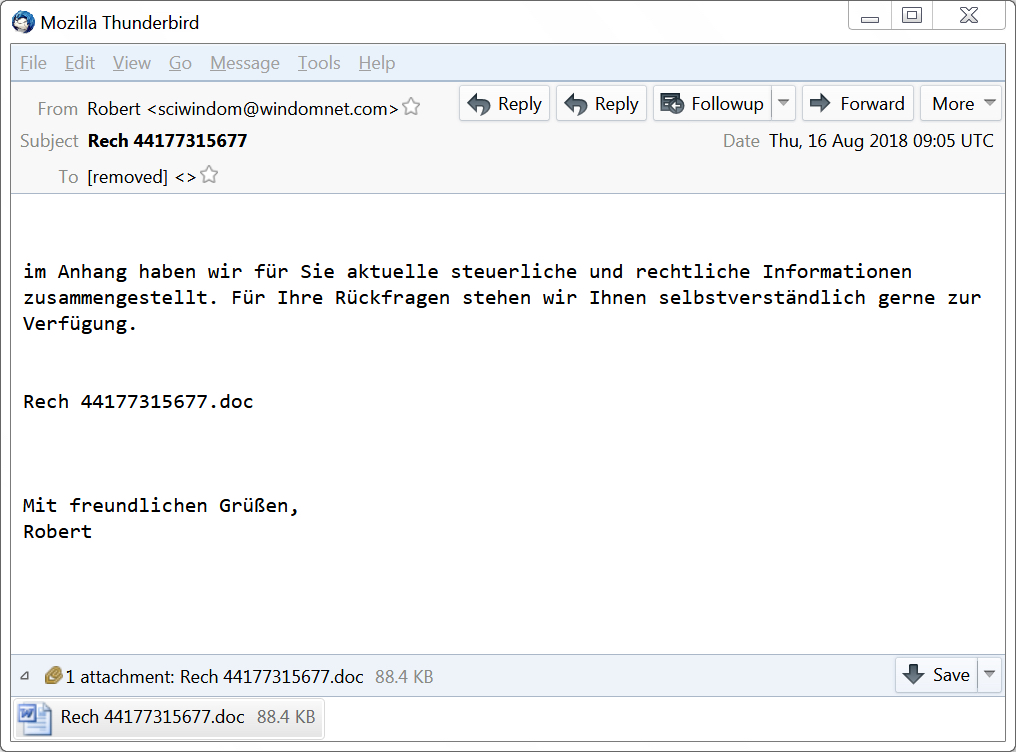
Shown above: An example of Emotet malspam from Thursday 2018-08-16.
DATA FROM THE EMAILS:
- Date: Tue, 2018-08-14 09:42 UTC
- Date: Tue, 2018-08-14 10:28 UTC
- Date: Tue, 2018-08-14 14:30 UTC
- Date: Wed, 2018-08-15 05:23 UTC
- Date: Wed, 2018-08-15 07:30 UTC
- Date: Wed, 2018-08-15 10:55 UTC
- Date: Wed, 2018-08-15 12:36 UTC
- Date: Wed, 2018-08-15 14:57 UTC
- Date: Thu, 2018-08-16 09:05 UTC
- From: "[info removed]" <psanford@mhsi[.]us>
- From: "[info removed]" <psanford@mhsi[.]us>
- From: "Wellsfargo" <chefs@sevenseashotel[.]com>
- From: "Danielle Houliston" <ashish@greatlogicsinc[.]com>
- From: "Danielle Houliston" <farhan@revesoft[.]com>
- From: "[info removed]" <jesse@affolders[.]com>
- From: "Wells Fargo Personal" <factelectronica@impacsa[.]com>
- From: "Wells Fargo" <e.wendlandt@cablesurf[.]de>
- From: Robert <sciwindom@windomnet[.]com>
- Subject: Invoice Confirmation IF80406
- Subject: Rechnung 06521887908 [recipient's name]
- Subject: Account Alert - Due balance paid
- Subject: Rechnungs-Details TOAS - 011-AT0212
- Subject: Billing Invoice - Job # 8034344
- Subject: Your Reception - HPH invoice is ready
- Subject: Activity Alert: Due balance paid
- Subject: Activity Alert: Wire transfer info
- Subject: Rech 44177315677
- Attachment name: IF80406_2018_08_14.doc
- Attachment name: Rechnung 06521887908.doc
- URL for Word doc: hxxp[:]//sharpconstructiontx[.]com/Wellsfargo/Business/Aug-14-2018
- Attachment name: Rechnungs-Details TOAS - 011-AT0212.doc
- Attachment name: MCO891938097_2018_08_15.doc
- Attachment name: 9P3018_2018_08_15.doc
- URL for Word doc: hxxp[:]//whybowl.thebotogs[.]com/Wellsfargo/Commercial/Aug-15-2018
- URL for Word doc: hxxp[:]//akademia.gnatyshyn[.]pl/WellsFargo/Smallbusiness/Aug-15-2018
- Attachment name: Rech 44177315677.doc
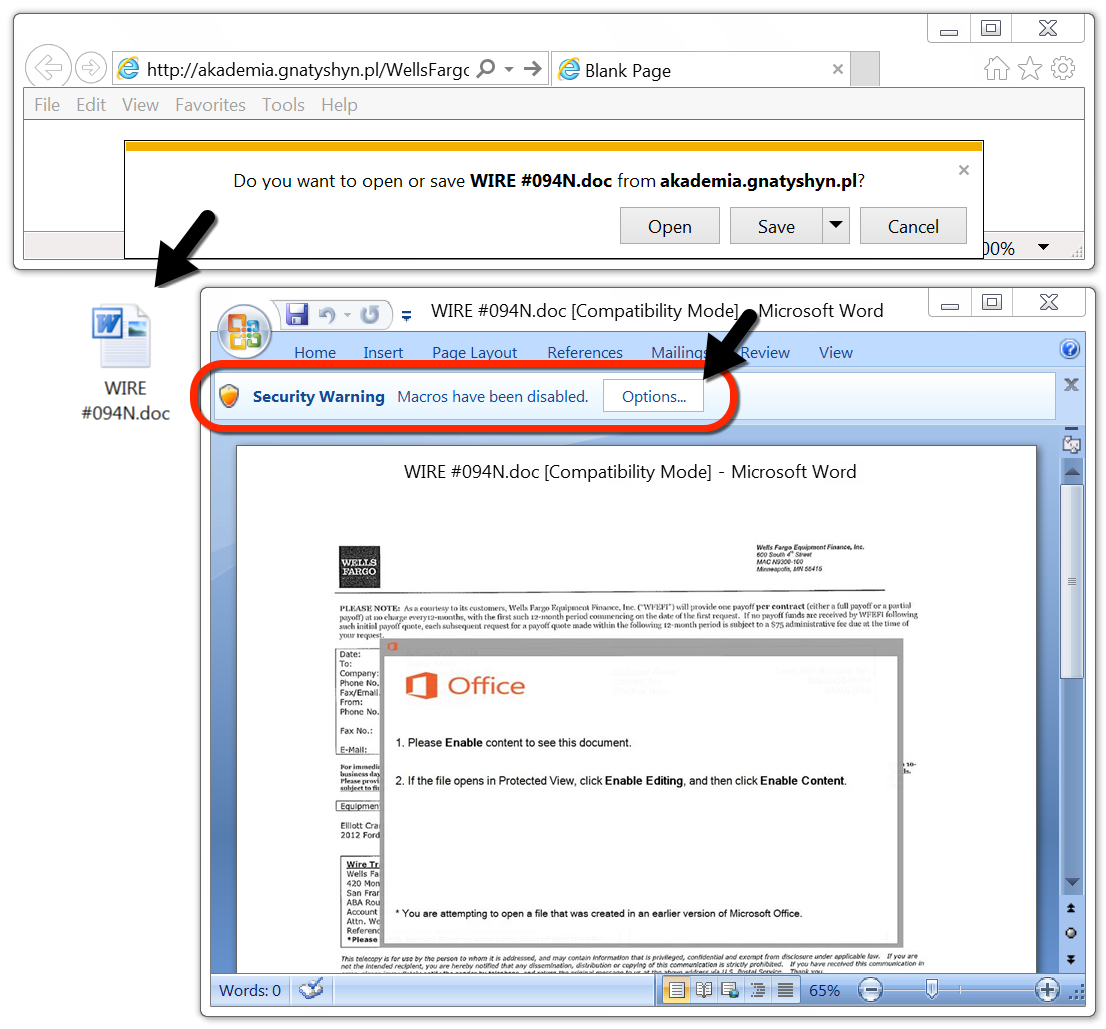
Shown above: Malicious Word doc downloaded from link in the malspam on Wednesday 2018-08-15.
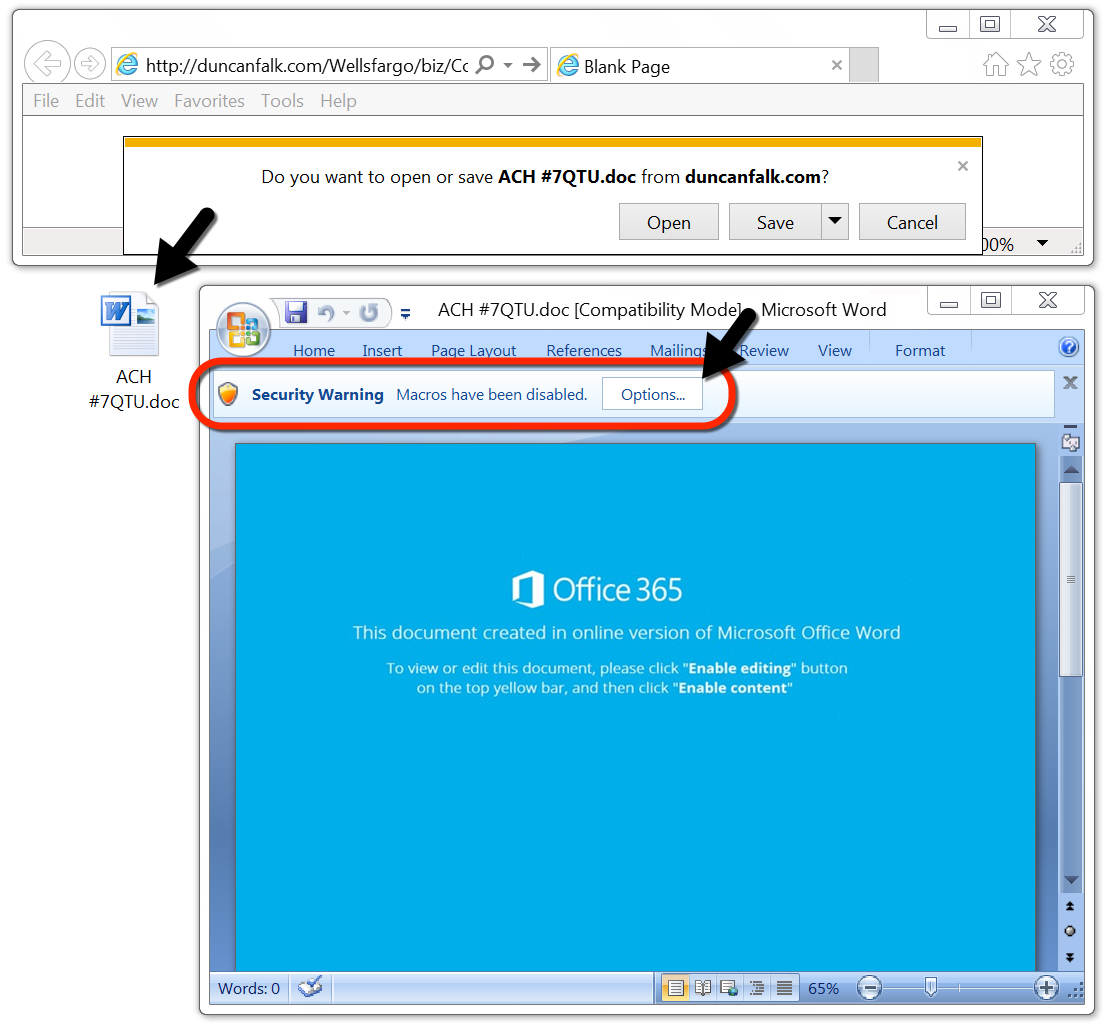
Shown above: Malicious Word doc downloaded from link in the malspam on Thursday 2018-08-16.
TRAFFIC
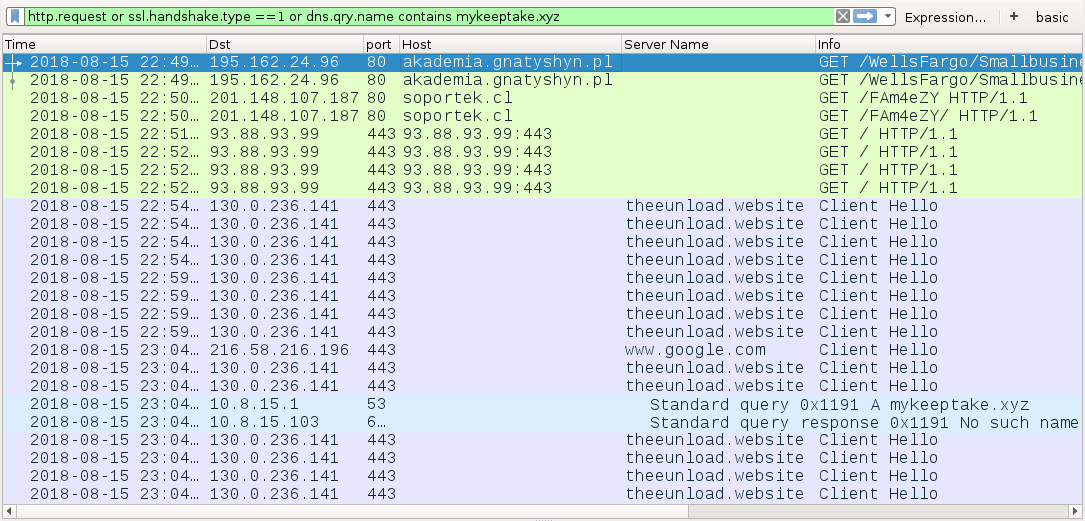
Shown above: Traffic from an infection on Wednesday 2018-08-15 filtered in Wireshark.
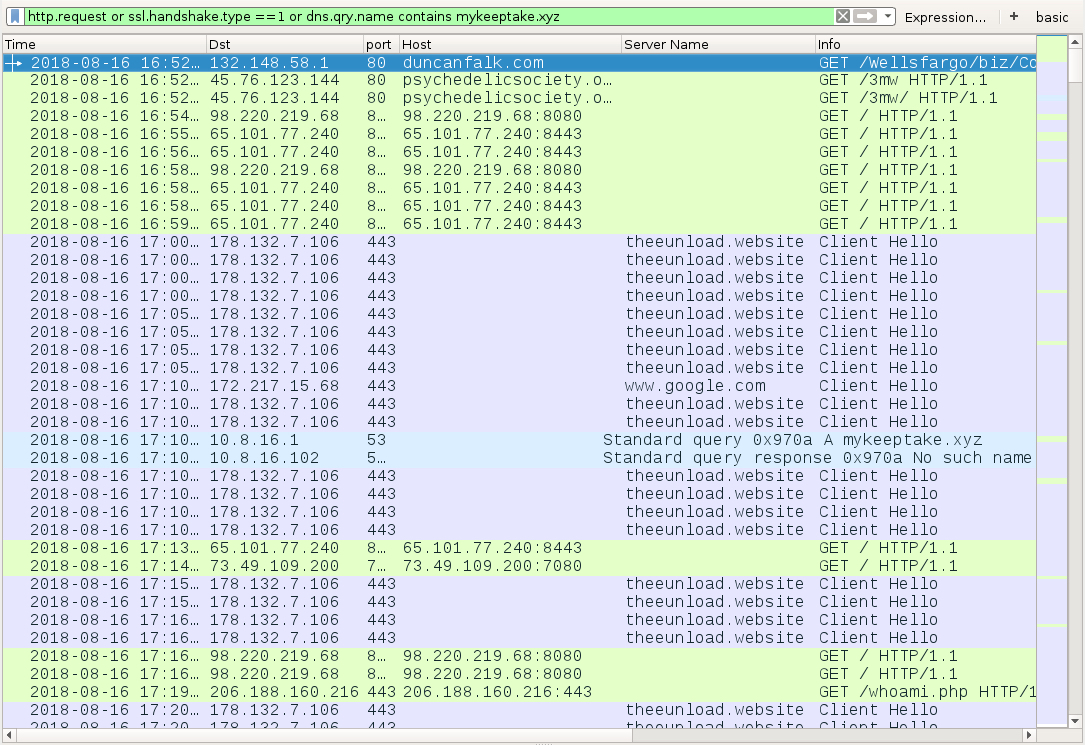
Shown above: Traffic from an infection on Thursday 2018-08-16 filtered in Wireshark.
INFECTION TRAFFIC FROM WEDNESDAY 2018-08-15:
- 195.162.24[.]96 port 80 - akademia.gnatyshyn[.]pl - GET /WellsFargo/Smallbusiness/Aug-15-2018
- 195.162.24[.]96 port 80 - akademia.gnatyshyn[.]pl - GET /WellsFargo/Smallbusiness/Aug-15-2018/
- 201.148.107[.]187 port 80 - soportek[.]cl - GET /FAm4eZY
- 201.148.107[.]187 port 80 - soportek[.]cl - GET /FAm4eZY/
- 203.94.66[.]109 port 8080 - attempted TCP connections, but no response from the server
- 93.88.93[.]99 port 443 - 93.88.93[.]99:443 - GET /
- 130.0.236[.]141 port 443 - theeunload[.]website - HTTPS/SSL/TLS traffic [Zeus Panda Banker]
- port 443 - www.google[.]com - connectivity check by infected Windows host [Zeus Panda Banker]
- DNS query for mykeeptake[.]xyz - response: No such name A mykeeptake[.]xyz SOA ns0.centralnic[.]net
INFECTION TRAFFIC FROM THURSDAY 2018-08-16:
- 132.148.58[.]1 port 80 - duncanfalk[.]com - GET /Wellsfargo/biz/Commercial/Aug-16-2018/
- 45.76.123[.]144 port 80 - psychedelicsociety[.]org[.]au - GET /3mw
- 45.76.123[.]144 port 80 - psychedelicsociety[.]org[.]au - GET /3mw/
- 203.94.66[.]109 port 8080 - attempted TCP connections, but no response from the server
- 93.88.93[.]99 port 443 - attempted TCP connections, but no response from the server
- 98.220.219[.]68 port 8080 - 98.220.219[.]68:8080 - GET /
- 65.101.77[.]240 port 8443 - 65.101.77[.]240:8443 - GET /
- 178.132.7[.]106 port 443 - theeunload[.]website - HTTPS/SSL/TLS traffic [Zeus Panda Banker]
- port 443 - www.google[.]com - connectivity check by infected Windows host [Zeus Panda Banker]
- DNS query for mykeeptake[.]xyz - response: No such name A mykeeptake.xyz SOA ns0.centralnic.net
FILE HASHES
MALWARE FROM THE INFECTED WINDOWS HOSTS:
- SHA256 hash: fa24a0c05815300726dd268426b28397471f067cdedcdb2f3258df75af169c28
File size: 166,016 bytes
File description: Downloaded Word doc with macro for Emotet seen on 2018-08-15
- SHA256 hash: e6ffa5ea51404503dff2ed0a29efea67d086f4fdf8a62b63ebb0ec6935f97f60
File size: 93,056 bytes
File description: Downloaded Word doc with macro for Emotet seen on 2018-08-16
- SHA256 hash: 280e188cb3e5e0e8b541bab6a27ddd4d22b89060dcfe03efa21ba7d2d9a1702f
File size: 176,128 bytes
File description: Emotet malware binary seen on 2018-08-15
- SHA256 hash: 0e6ca1d86245ca02cd271555d1d776705e7f66fa52e953655eb34653b4f55997
File size: 172,032 bytes
File description: Emotet malware binary seen on 2018-08-16 (1 of 2)
- SHA256 hash: 713a749206310f2c848ecf477b3903475eaf8f30454ec3e2312efbba8ba674a6
File size: 176,128 bytes
File description: Emotet malware binary seen on 2018-08-16 (2 of 2)
- SHA256 hash: dd4ff33e8853e34480e820a3d2d11e6fc87bc75efbeebfe324664d4013dee0b0
File size: 249,344 bytes
File description: Zeus Panda Banker caused by Emotet infection on 2018-08-15
- SHA256 hash: 45c7c91ebb315a77dd28e0092913184cb6a4a8d0387d29384b273ebf9bce9a74
File size: 225,280 bytes
File description: Zeus Panda Banker caused by Emotet infection on 2018-08-16
MALICIOUS WORD DOCS ATTACHED TO THE EMAILS:
- SHA256 hash: e93367edd903d593c0ed475e31e8b433a5c5eaf3ec2472a0a31c758b4a85082f
File size: 135,936 bytes
File name: 9P3018_2018_08_15.doc
- SHA256 hash: 6c08db14bf40b0244a069834b523d8aac53caab33095b7d3f744615e15661cfd
File size: 119,296 bytes
File name: IF80406_2018_08_14.doc
- SHA256 hash: 55bdd3ff511c7751663cb3d95384fb0e583d47ab534d641f0953fda32f16dfca
File size: 119,680 bytes
File name: MCO891938097_2018_08_15.doc
- SHA256 hash: 63bd976a37fe2e7cdc3e3a53bd81b21c296a23626aa8aebe34624790552f62a6
File size: 90,496 bytes
File name: Rech 44177315677.doc
- SHA256 hash: c0101bfdea779570b17dbff46177664736788f46de6c4bcce5774a3546fdeced
File size: 115,712 bytes
File name: Rechnung 06521887908.doc
- SHA256 hash: 1a4ca08fb00aedb3b45ec4418539472eea22761aabe719e0e8021947305c4e6e
File size: 122,240 bytes
File name: Rechnungs-Details TOAS - 011-AT0212.doc
Click here to return to the main page.