2018-09-04 - EMOTET INFECTION WITH ICEDID BANKING TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-09-04-Emotet-malspam-with-PDF-attachments-5-examples.zip 13.6 kB (13,560 bytes)
- 2018-09-04-Emotet-infection-with-IcedID.pcap.zip 1.0 MB (1,034,427 bytes)
- 2018-09-04-malware-and-artifacts-from-Emotet-infection-with-IcedID.zip 541 kB (540,923 bytes)
BONUS PCAPS:
- 2018-09-04-Emotet-infection-with-spammer-malware.pcap.zip 9.1 MB (9,111,471 bytes)
- 2018-09-04-Emotet-infection-with-Trickbot.pcap.zip 7.4 MB (7,393,287 bytes)
NOTES:
- This week, I've noticed Emotet malspam with PDF attachments, where there is no link in the message text for an Emotet Word doc.
- Instead, the PDF attachments have a link for the Emotet Word doc.
- Traffic-wise, it's still a typical Emotet infection, where the Word macro grabs an Emotet binary to infect a vulnerable Windows host.
- Today, I generated three examples of Emotet traffic with follow-up malware. One was Trickbot, one was spambot malware, and the last one was IcedID.
- I hadn't seen the IcedID banking Trojan from Emotet since 2018-06-27, so I'm documenting today's example.
- As a reminder that Emotet grabs a variety of follow-up malware, I've included pcaps for the Emotet+spambot infection and the Emotet+Trickbot infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- whoulatech[.]com
- tybalties[.]website
- hxxp[:]//devbyjr[.]com/Payments
- hxxp[:]//devbyjr[.]com/Payments/
- hxxp[:]//boloshortolandia[.]com/ozylgj6Z6
- hxxp[:]//boloshortolandia[.]com/ozylgj6Z6/
EMAILS
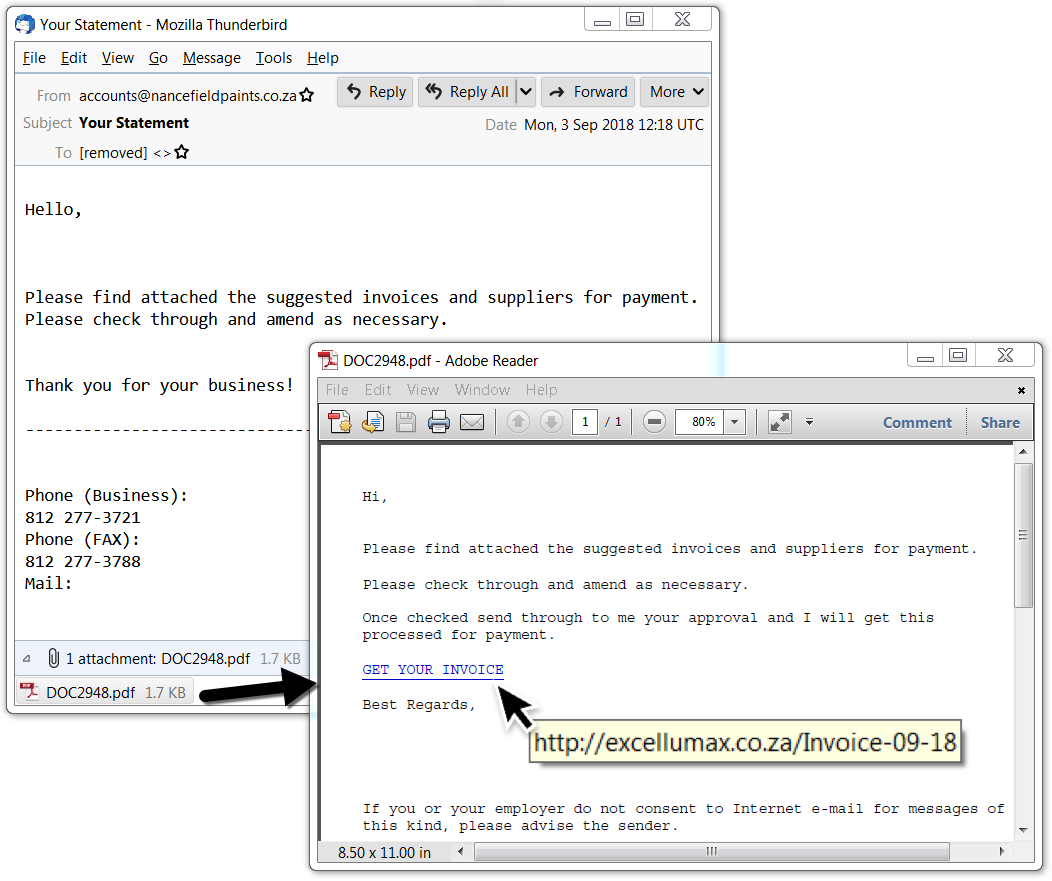
Shown above: Screenshot from a malspam example on Monday 2018-09-03.
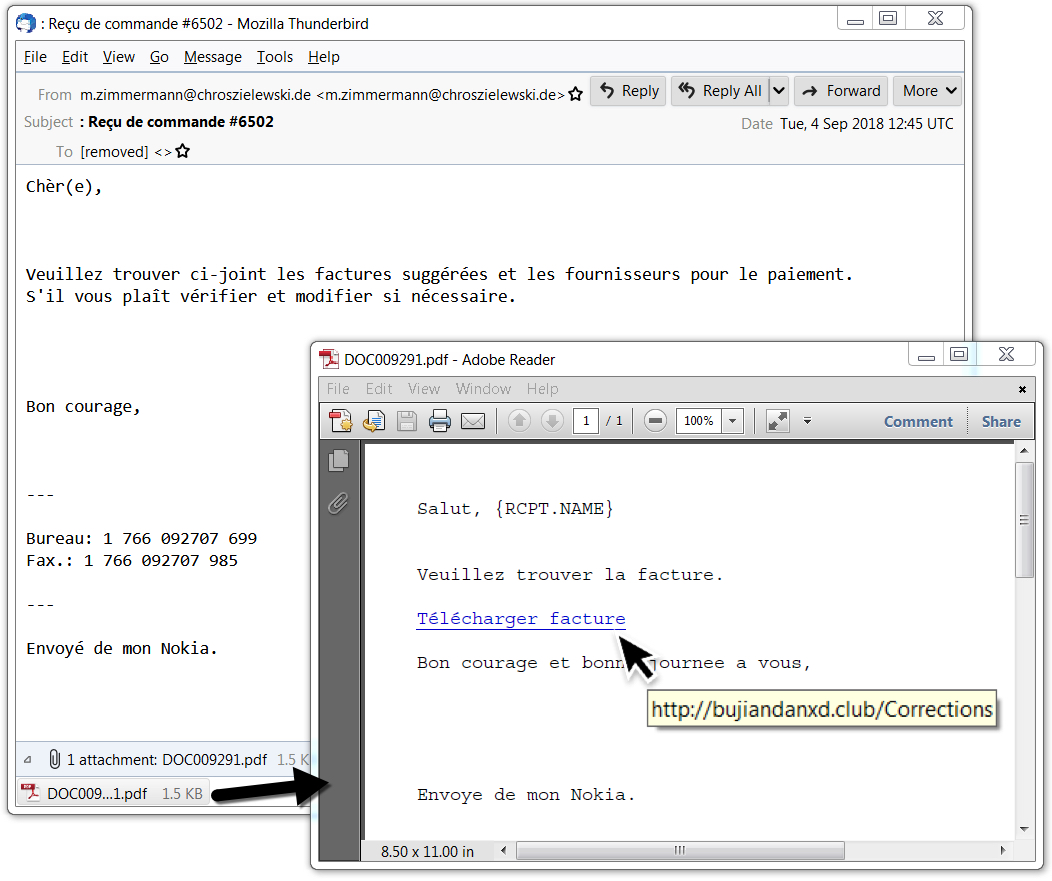
Shown above: Screenshot from a malspam example on Tuesday 2018-09-04.
5 EXAMPLES OF EMOTET MALSPAM WITH PDF ATTACHMENTS:
- 2018-09-03 at 12:18 UTC -- From: accounts@nancefieldpaints[.]co[.]za -- Subject: Your Statement
- 2018-09-03 at 12:19 UTC -- From: deepthi@platinumthree[.]com -- Subject: Invoice L8815 from
- 2018-09-03 at 13:26 UTC -- From: huram.masood@samadrubber[.]com -- Subject: Your Statement
- 2018-09-04 at 10:48 UTC -- From: pedro.ibanez@consorcioppe[.]com -- Subject: Customer Statement
- 2018-09-04 at 12:45 UTC -- From: m.zimmermann@chroszielewski[.]de -- Subject: Reçu de commande #6502
TRAFFIC
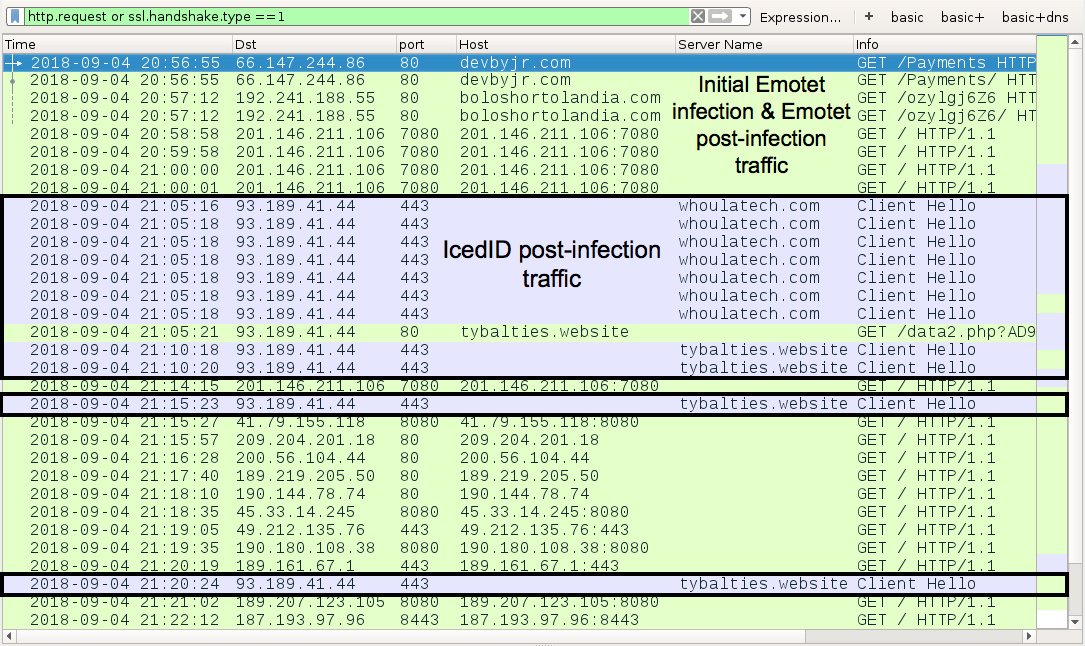
Shown above: Traffic from the infection filtered in Wireshark.
INITIAL INFECTION TRAFFIC (EMOTET WORD DOC AND EXECUTABLE):
- 66.147.244[.]86 port 80 - devbyjr[.]com - GET /Payments
- 66.147.244[.]86 port 80 - devbyjr[.]com - GET /Payments/
- 192.241.188[.]55 port 80 - boloshortolandia[.]com - GET /ozylgj6Z6
- 192.241.188[.]55 port 80 - boloshortolandia[.]com - GET /ozylgj6Z6/
EMOTET POST-INFECTION TRAFFIC:
- 201.146.211[.]106 port 7080 - 201.146.211[.]106:7080 - GET /
- 41.79.155[.]118 port 8080 - 41.79.155[.]118:8080 - GET /
- 209.204.201[.]18 port 80 - 209.204.201[.]18 - GET /
- 200.56.104[.]44 port 80 - 200.56.104[.]44 - GET /
- 189.219.205[.]50 port 80 - 189.219.205[.]50 - GET /
- 190.144.78[.]74 port 80 - 190.144.78[.]74 - GET /
- 45.33.14[.]245 port 8080 - 45.33.14[.]245:8080 - GET /
- 49.212.135[.]76 port 443 - 49.212.135[.]76:443 - GET /
- 190.180.108[.]38 port 8080 - 190.180[.]108.38:8080 - GET /
- 189.161.67[.]1 port 443 - 189.161.67[.]1:443 - GET /
- 189.207.123[.]105 port 8080 - 189.207[.]123.105:8080 - GET /
- 187.193.97[.]96 port 8443 - 187.193.97[.]96:8443 - GET /
ICEDID BANKING TROJAN POST-INFECTION TRAFFIC:
- 93.189.41[.]44 port 443 - whoulatech[.]com - SSL/TLS traffic caused by IcedID banking Trojan
- 93.189.41[.]44 port 80 - tybalties[.]website - GET /data2.php?AD94A3F72C8EBEE9
- 93.189.41[.]44 port 443 - tybalties[.]website - SSL/TLS traffic caused by IcedID banking Trojan
FILE HASHES
PDF ATTACHMENTS FROM THOSE 5 EXAMPLES:
- bb251cba9475d17c04f0eac6213e7e93a6093748caeb6f434b1cca8c1d3d7723 - 1,564 bytes - DOC009291.pdf
- 5bd8f7d93d86c4ab90b6daec2388c1875a2599b10b84944e7a78f1635ca46713 - 1,721 bytes - DOC2948.pdf
- 601fc0ffe6b51a5f3549ece0e0ee9ab03cbb76c0d0f3b3a60d8dc106c543f79c - 1,516 bytes - DOC6971.pdf
- dbcdf3ef7b37038770fa8f281ca982ad78c223be8dc908ba97c30e050716645b - 1,521 bytes - DOC742.pdf
- c75ea730215e5f20b728c9c327df036a7093efdd5ec0fa55168f07f2011c7ef3 - 1,673 bytes - DOC8815.pdf
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: fb984e86dd6a8018a58dff37c13b3aa2b157025c6f11de5249a101da10ceeb90
File size: 66,816 bytes
File description: Downloaded Word doc with macro for Emotet
- SHA256 hash: 80bca6cec3f235547c36c5cf8da9dfae6a1f3c4da71dea4dcf40eac342e293c3
File size: 533,504 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random name].exe
File description: Emotet malware binary retreived from the infected Windows host
- SHA256 hash: 2b1d3a4f2991b147cc0e79d7bcb53bac622e2159addb18446499ac209387ad0e
File size: 297,984 bytes
File location: C:\ProgramData\xoivIJooTef.exe
File location: C:\ProgramData\Sw8D3HIo9FAsV.exe
File description: IcedID malware retreived from the infected Windows host
- SHA256 hash: da7d9687c5776eecc90f7d11dbe32623f9aa1f44fc2eff5088e0540014adcb0e
File size: 297,984 bytes
File location: C:\ProgramData\{D6C9CBCB-24CB-4CD1-AB13-91126EB539C8}\xuvtfy.exe
File description: IcedID malware persistent on the infected Windows host
MORE IMAGES
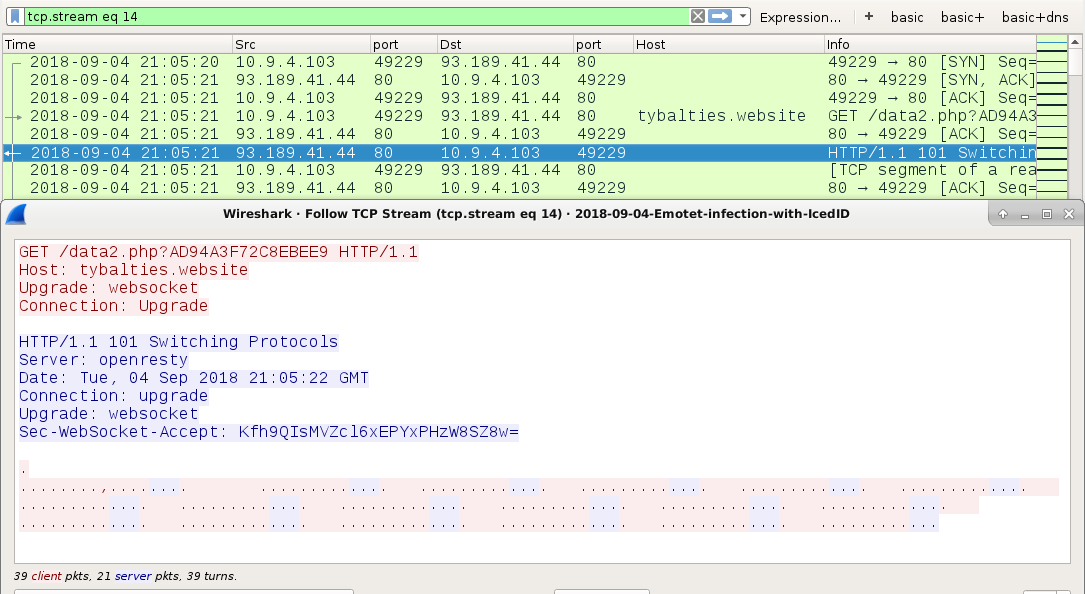
Shown above: Websocket traffic caused by IcedID on the infected Windows host.
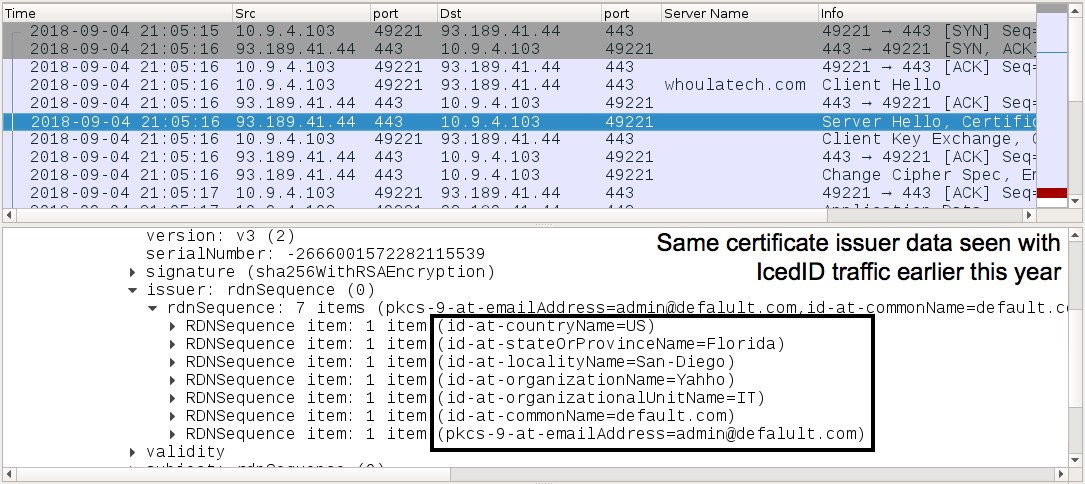
Shown above: SSL/TLS certificate data consistent with previous samples of IcedID banking Trojan (1 of 2).
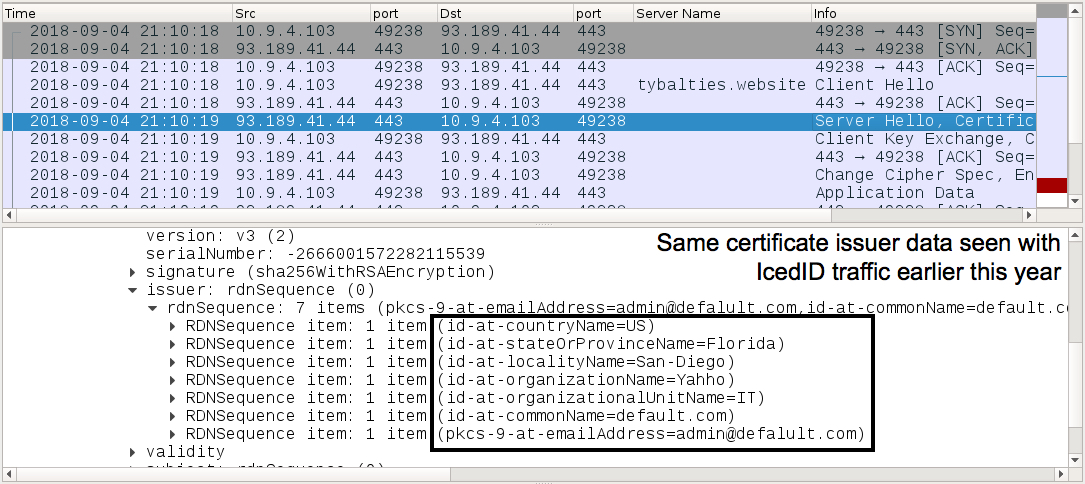
Shown above: SSL/TLS certificate data consistent with previous samples of IcedID banking Trojan (2 of 2).
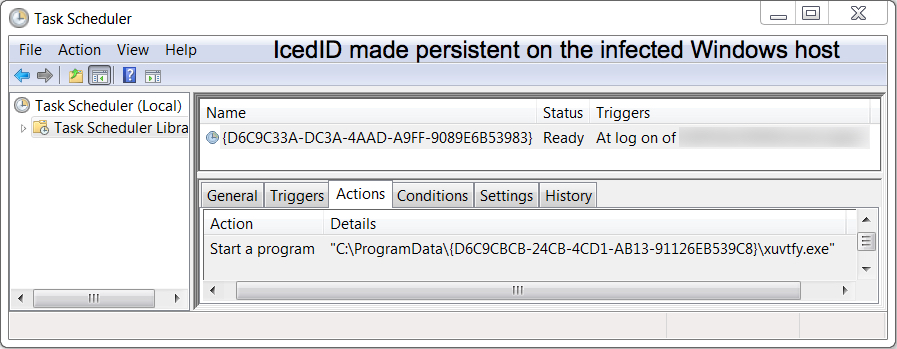
Shown above: Scheduled task to keep IcedID persistent on the infected Windows host.
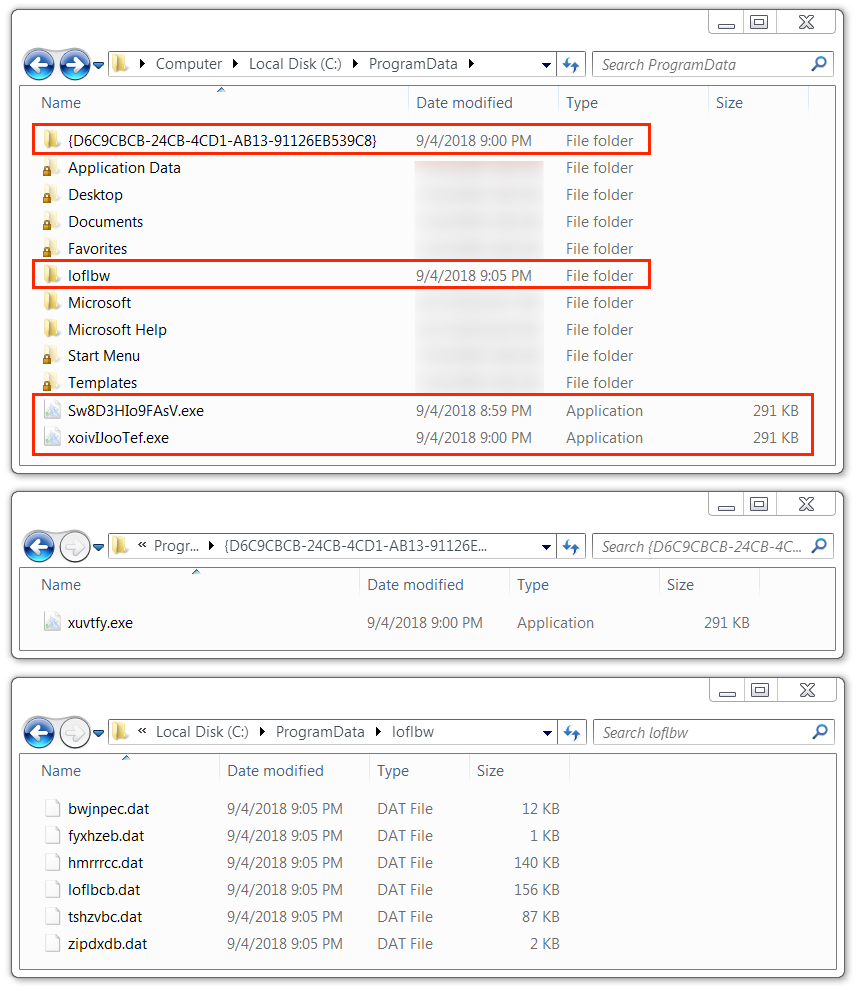
Shown above: Locations of IcedID malware and artifacts on the infected Windows host.
Click here to return to the main page.
