2018-09-05 - QUICK POST: HANCITOR MALSPAM STOPS USING PDF ATTACHMENTS AFTER 1 DAY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-09-05-Hancitor-malspam-email-example.eml.zip 2.0 kB (1,955 bytes)
- 2018-09-05-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.1 MB (2,061,194 bytes)
- 2018-09-05-malware-and-artifacts-from-Hancitor-infection.zip 298 kB (297,853 bytes)
NOTES:
- Hancitor malspam went back to normal today, using links in the message text to download the malicious Word doc.
- No more PDF attachments like yesterday.
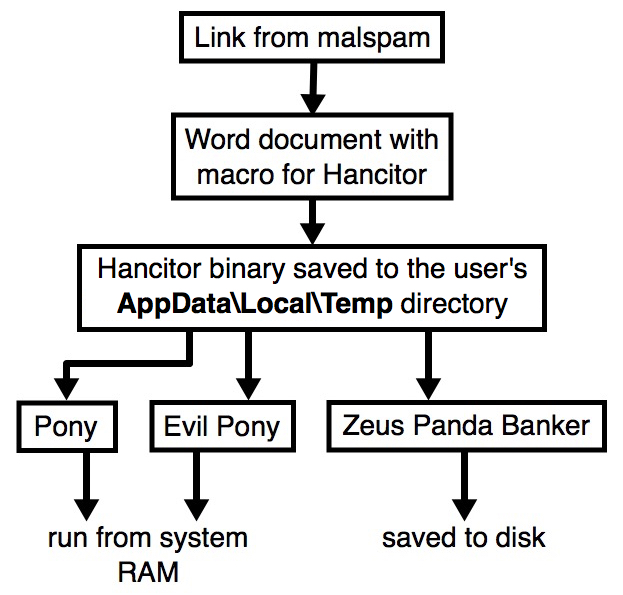
- Time to revert the flow chart back to its normal state...
Shown above: Chain of events for today's Hancitor malspam infection.
IMAGES
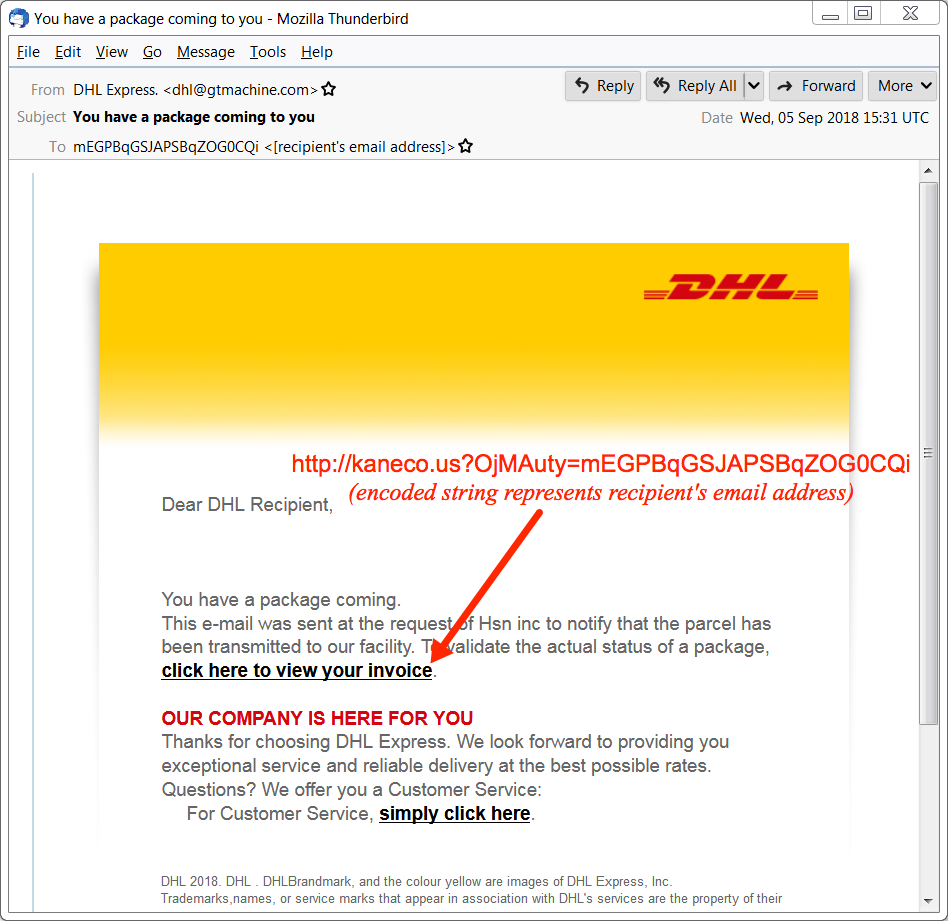
Shown above: Screenshot of an email from today's wave of Hancitor malspam.
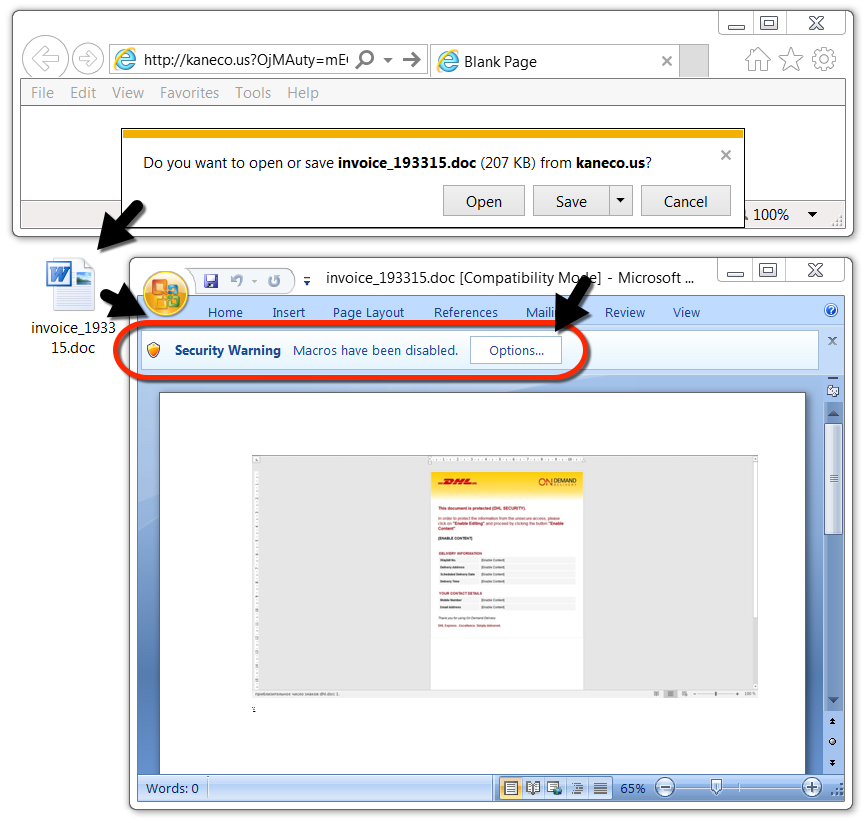
Shown above: After downloading the Word doc, enable macros to infect a vulnerable Windows host.
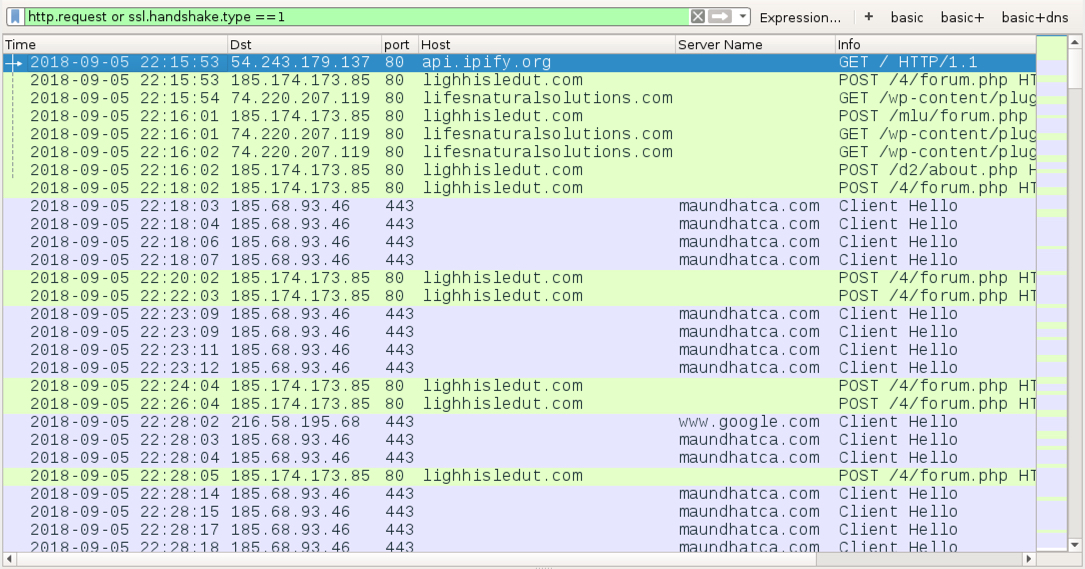
Shown above: Traffic from an infection filtered in Wireshark (domains hosting the Word doc had already been taken off-line by the time I recorded this).
Click here to return to the main page.