2018-09-21 - EMOTET INFECTIONS WITH TRICKBOT (UK AND US)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-09-21-Emotet-infection-with-Trickbot-from-UK-location.pcap.zip 13.8 MB (13,776,904 bytes)
- 2018-09-21-Emotet-infection-with-Trickbot-from-UK-location.pcap (17,525,561 bytes)
- 2018-09-21-Emotet-infection-with-Trickbot-from-US-location.pcap.zip 3.2 MB (3,202,102 bytes)
- 2018-09-21-Emotet-infection-with-Trickbot-from-US-location.pcap (3,419,428 bytes)
- 2018-09-21-Emotet-and-Trickbot-malware-and-artifacts.zip 1.5 MB (1,515,698 bytes)
- 2018-09-21-downloaded-Word-doc-with-macro-for-Emotet-from-UK-infection.doc (91,008 bytes)
- 2018-09-21-downloaded-Word-doc-with-macro-for-Emotet-from-US-infection.doc (84,864 bytes)
- 2018-09-21-Emotet-malware-binary-from-UK-infection.exe (139,264 bytes)
- 2018-09-21-Emotet-malware-binary-from-US-infection.exe (139,264 bytes)
- 2018-09-21-Trickbot-gtag-arz1-caused-by-Emotet-infection-from-US-location.exe (483,438 bytes)
- 2018-09-21-Trickbot-gtag-del77-caused-by-Emotet-infection-from-UK-location.exe (494,641 bytes)
- 2018-09-21-Trickbot-gtag-jim316-found-on-client-during-UK-infection.exe (536,576 bytes)
- 2018-09-21-Trickbot-gtag-lib316-found-on-DC-during-UK-infection.exe (536,576 bytes)
- 2018-09-21-other-Trickbot-related-binary-found-on-DC-during-UK-infection.exe (115,712 bytes)
- 2018-09-21-scheduled-task-for-Trickbot-on-DC-Msntcs.xml.txt (3,602 bytes)
- 2018-09-21-scheduled-task-for-Trickbot-on-client-Msntcs.xml.txt (3,734 bytes)
NOTES:
- For some background, see this Palo Alto Networks blog post I wrote that was published in July 2018.
- Today's pcap for the UK-based infection also has Trickbot propagating from the Windows client to the domain controller over SMB.
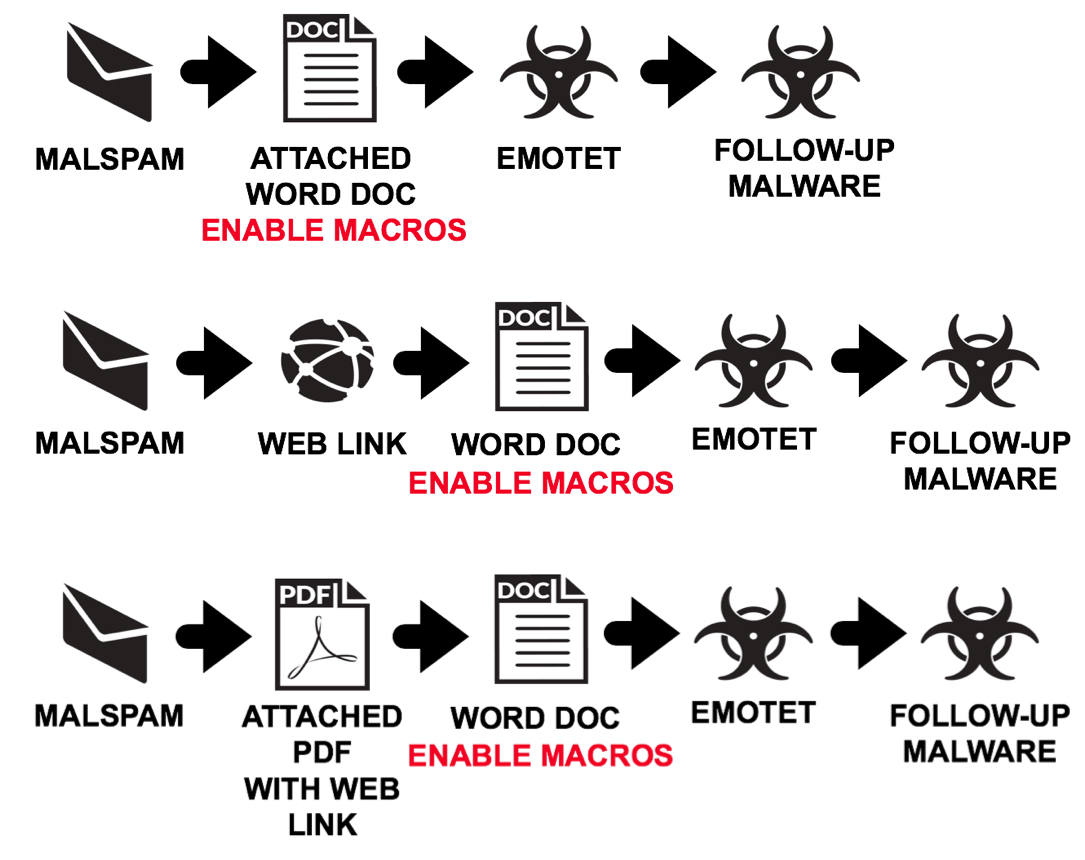
Shown above: Updated flow chart for what I've been seeing from Emotet malspam.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and partial URLs:
- hxxp[:]//artiliriklagudaerah[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//astroxh[.]ru/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//bahoma[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//bamarketing[.]ru/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//bernee[.]net/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018/
- hxxp[:]//bfxplode[.]de/newfolde_r/389CJSP/PAYMENT/Commercial
- hxxp[:]//blondesalons[.]in/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//cahayaprint[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//canetafixa[.]com[.]br/142WBMS/PAYROLL/Smallbusiness
- hxxp[:]//ccdwdelaware[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//classbrain[.]net/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//coocihem[.]ru/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//cosmictone[.]com.au/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//cukkuc[.]net/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//danforshaw[.]com/63SMSMM/biz/Business
- hxxp[:]//dat24h[.]vip/4797SDVCPDS/WIRE/US
- hxxp[:]//deckenhoff[.]de/743208ZSA/BIZ/Personal
- hxxp[:]//eletelephant[.]com/2KGZSVMIW/SWIFT/Commercial
- hxxp[:]//emicontrol[.]com/7FBPPXLW/PAY/Personal
- hxxp[:]//enhancepotential[.]com/39FEH/com/US
- hxxp[:]//esteticabrasil[.]com[.]br/logssite/9391814NAVSB/WIRE/US
- hxxp[:]//flashhospedagem[.]com[.]br/31OVJJL/SWIFT/US
- hxxp[:]//fpc-partner[.]ru/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018/
- hxxp[:]//gaun[.]de/typo3conf/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//georgew[.]com[.]br/00390WTU/SEP/Smallbusiness
- hxxp[:]//gsverwelius[.]nl/26581BRMJO/ACH/Smallbusiness
- hxxp[:]//hannael[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//hciot[.]net/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//imcfilmproduction[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//infoges[.]es/41906JK/PAYROLL/Business
- hxxp[:]//jimmyphan[.]net/63003FSTWJNUN/oamo/US
- hxxp[:]//johnscevolaseo[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//kh-ghohestan.ir/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//kinebydesign[.]com/9T/biz/Personal
- hxxp[:]//klezmerpodcast[.]com/35BIKT/oamo/Business
- hxxp[:]//lukomore-alupka[.]ru/wp-content/uploads/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18/
- hxxp[:]//madisonda[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//mitsuobrasil[.]com[.]br/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//na-alii[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//neurocoachingkm[.]com[.]br/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//nigelkarikari[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18/
- hxxp[:]//nurulquraan[.]net/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//old.gkinfotechs[.]com/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//pancare-sd[.]org/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18/
- hxxp[:]//pembi[.]net/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- hxxp[:]//pnsolco[.]com/3683DPDQ/biz/US
- hxxp[:]//rethinkpylons[.]org/16YZTG/BIZ/Business/
- hxxp[:]//soldeyanahuara[.]com/9035QQNXD/BIZ/Commercial
- hxxp[:]//webartikelbaru[.]web[.]id/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//www.omelhordeportoalegre[.]com[.]br/82TMPB/PAYROLL/Personal
- hxxp[:]//www.ultigamer[.]com/wp-admin/includes/urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018
- hxxp[:]//yblfood[.]com[.]au/workmode/FUNC/40KVCX/BIZ/Business
- hxxp[:]//www.gymbolaget[.]se/4IQcsWOes
- hxxps://www.gymbolaget[.]se/4IQcsWOes
- hxxp[:]//fenja[.]com/wwvvv/xIGjcbS5Pc
- hxxp[:]//thepinkonionusa[.]com/G54zZtja
- hxxp[:]//192.161.54[.]60/radiance.png
- hxxp[:]//192.161.54[.]60/table.png
- hxxp[:]//192.161.54[.]60/worming.png
- hxxp[:]//173.32.244[.]79:8082/arz1/
- hxxp[:]//173.32.244[.]79:8082/del77/
- hxxp[:]//173.32.244[.]79:8082/lib316/
- hxxp[:]//31.167.248[.]50:443/whoami.php
TRAFFIC
TRAFFIC FROM AN INFECTED WINDOWS HOST IN THE UK - EMOTET:
- 185.94.99[.]3 port 80 - kh-ghohestan[.]ir - GET /urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/092018/
- 132.148.61[.]184 port 80 - thepinkonionusa[.]com - GET /G54zZtja
- 132.148.61[.]184 port 80 - thepinkonionusa[.]com - GET /G54zZtja/
- 95.6.64[.]119 port 8080 - attempted TCP connections
- 187.193.161[.]58 port 8080 - attempted TCP connections
- 201.242.55[.]19 port 8080 - attempted TCP connections
- 77.86.23[.]44 port 8443 - attempted TCP connections
- 100.17.27[.]26 port 80 - 100.17.27[.]26 - GET /
- 201.111.8[.]75 port 50000 - attempted TCP connections
- 31.167.248[.]50 port 443 - 31.167.248[.]50:443 - GET /whoami.php
- 31.167.248[.]50 port 443 - 31.167.248[.]50:443 - POST /
TRAFFIC FROM AN INFECTED WINDOWS HOST IN THE UK - TRICKBOT:
- port 80 - myexternalip[.]com - GET /raw [IP address check by infected client]
- port 80 - icanhazip[.]com - GET / [IP address check by infected DC]
- 47.49.168[.]50 port 443 - SSL/TLS traffic generated by Trickbot
- 95.154.80[.]154 port 449 - SSL/TLS traffic generated by Trickbot
- 107.175.46[.]219 port 447 - SSL/TLS traffic generated by Trickbot
- 109.199.231[.]116 port 443 - SSL/TLS traffic generated by Trickbot
- 192.161.54[.]60 port 80 - 192.161.54[.]60 - GET /radiance.png
- 192.161.54[.]60 port 80 - 192.161.54[.]60 - GET /worming.png
- 192.161.54[.]60 port 80 - 192.161.54[.]60 - GET /table.png
- 173.32.244[.]79 port 8082 - 173.32.244[.]79:8082 - POST /del77/[long string with infected host's info]
- 173.32.244[.]79 port 8082 - 173.32.244[.]79:8082 - POST /lib316/[long string with infected DC's info]
TRAFFIC FROM AN INFECTED WINDOWS HOST IN THE US - EMOTET:
- 192.254.237[.]11 port 80 - bahoma[.]com - GET /urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18
- 192.254.237[.]11 port 80 - bahoma[.]com - GET /urldefense_proofpoint/billpay_bankofamerica_com/PaymentCenter_Index/09_18/
- 213.115.245[.]123 port 80 - gymbolaget[.]se - GET /4IQcsWOes
- 213.115.245[.]123 port 443 - www.gymbolaget[.]se - HTTPS/SSL/TLS traffic caused by previous HTTP request
- 87.118.13[.]222 port 80 - fenja[.]com - GET /wwvvv/xIGjcbS5Pc
- 87.118.13[.]222 port 80 - fenja[.]com - GET /wwvvv/xIGjcbS5Pc/
- 95.6.64[.]119 port 8080 - attempted TCP connections
- 187.193.161[.]58 port 8080 - attempted TCP connections
- 201.242.55[.]19 port 8080 - attempted TCP connections
- 77.86.23[.]44 port 8443 - 77.86.23[.]44:8443 - GET /
- 100.17.27[.]26 port 80 - 100.17.27[.]26 - GET /
TRAFFIC FROM AN INFECTED WINDOWS HOST IN THE US - TRICKBOT:
- port 80 - icanhazip[.]com - GET / [IP address check by infected client]
- 51.254.241[.]249 port 447 - attempted TCP connections
- 96.43.142[.]42 port 447 - attempted TCP connections
- 107.181.174[.]177 port 447 - attempted TCP connections
- 155.94.239[.]167 port 447 - attempted TCP connections
- 89.46.223[.]139 port 447 - SSL/TLS traffic generated by Trickbot
- 92.223.105[.]95 port 447 - SSL/TLS traffic generated by Trickbot
- 178.116.83[.]49 port 443 - SSL/TLS traffic generated by Trickbot
- 190.145.74[.]84 port 449 - SSL/TLS traffic generated by Trickbot
- 173.32.244[.]79 port 8082 - 173.32.244[.]79:8082 - POST /arz1/[long string with infected DC's info]
MALWARE
MALWARE FROM THE INFECTED WINDOWS HOSTS:
- SHA256 hash: d40f5ae2f85b62351f2e8b0f068a8c3695d228b0f06b8015a513eb919b70f5bb
- File description: Downloaded Word doc with macro for Emotet
- SHA256 hash: fa4f251ef1152b59d5a66b1148202ead8cffd57140ac8cc8b5ce9ec9ffb32c9c
- File description: Downloaded Word doc with macro for Emotet
- SHA256 hash: 48fedd8eb8fd95b1c3f3a43fe0ed4ff6e769902b1b7db1f07953455b5ff2c662
- File description: Emotet malware binary
- SHA256 hash: f5abca2b0bad74970347f9f4ed09eff1df1dd9f6ee1866e76b2a3003e06ebaae
- File description: Trickbot gtag: arz1 caused by Emotet infection from US location
- SHA256 hash: 1407a8aec04f8f1ce801602d132d420220191e2194e3d7e7895c8fe3d726d717
- File description: Trickbot gtag: del77 caused by Emotet infection from UK location
- SHA256 hash: 8e14cd3e9f8070f1d7966043bf988b5f6708eaa40f584077a0a6eec754ca6f5a
- File description: Trickbot gtag: jim316 found on client during UK infection
- SHA256 hash: 57fe92b7c8c19a22c158bc941895fa5ab33f87d4b16b01d0dab6751c75ae6990
- File description: Trickbot gtag: lib316 found on DC during UK infection
- SHA256 hash: cf99990bee6c378cbf56239b3cc88276eec348d82740f84e9d5c343751f82560
- File description: Other Trickbot-related binary found on DC during UK infection
IMAGES
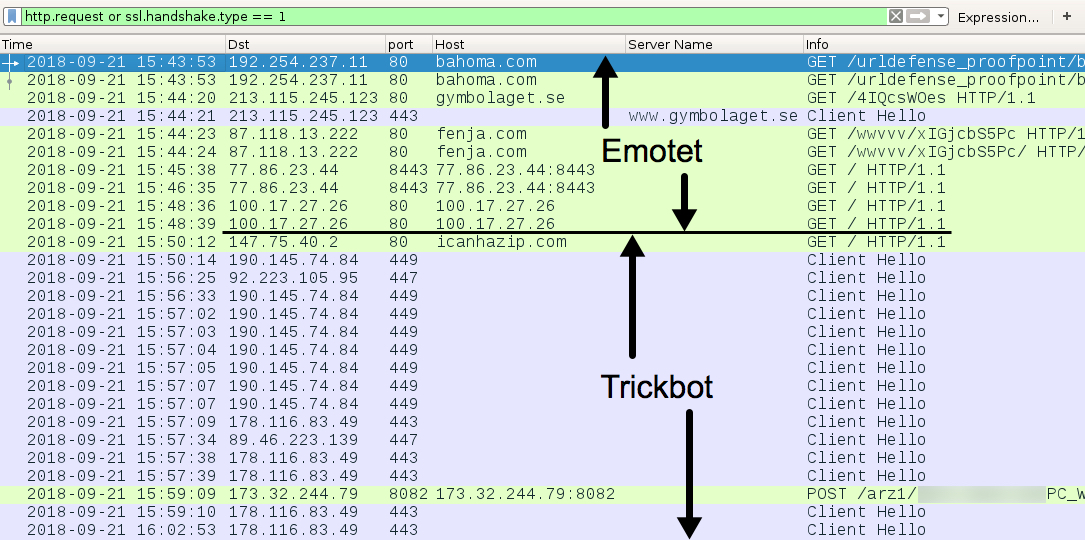
Shown above: Traffic from the US-based infection filtered in Wireshark.
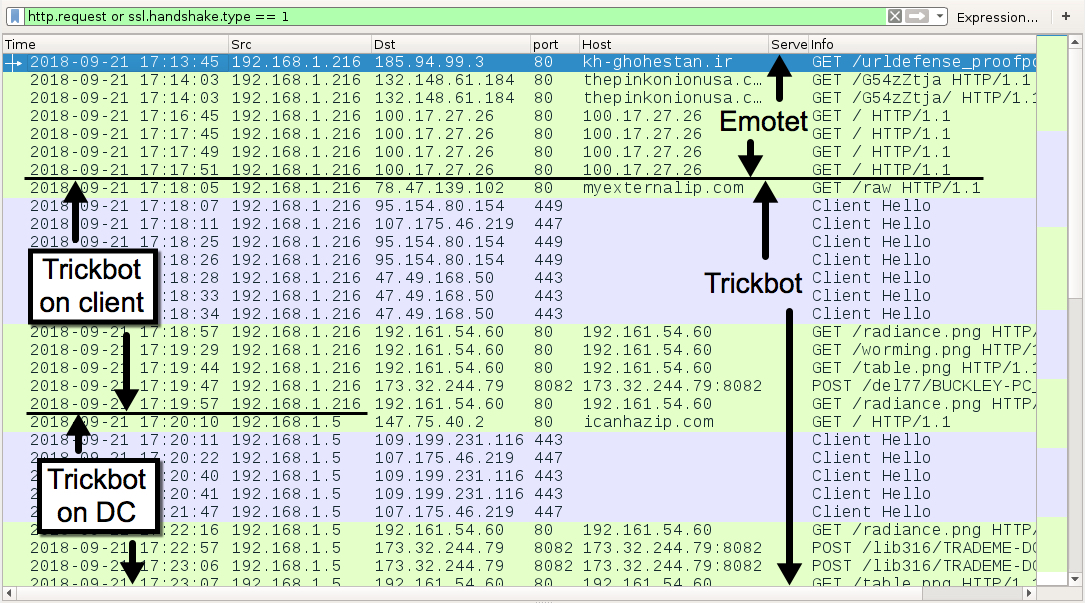
Shown above: Traffic from the UK-based infection filtered in Wireshark.
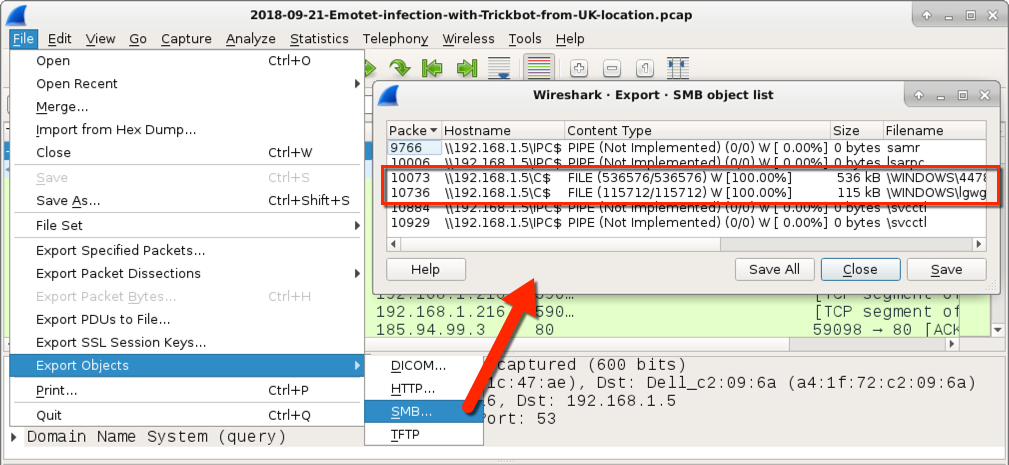
Shown above: Using Wireshark to export Trickbot malware binaries from SMB traffic in the UK-based pcap.
Click here to return to the main page.
