2018-09-28 - MORE MALSPAM WITH PASSWORD-PROTECTED WORD DOCS PUSHING NYMAIM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-09-28-example-of-Nymaim-malspam.eml.zip 32 kB (32,241 bytes)
- 2018-09-28-Nymaim-infection-traffic.pcap.zip 6.2 MB (6,236,663 bytes)
- 2018-09-28-malware-associated-with-Nymaim-infection.zip 3.2 MB (3,223,671 bytes)
NOTES:
- Still seeing this since the last time I posted about it on 2018-09-21. See that post for more details and a bit more history on this campaign.
- @HerbieZimmerman also tweeted an example earlier. (link to tweet)
- Password for these Word docs is still 1234
EMAILS
SENDING MAIL SERVER INFO FROM THIS MALSPAM:
- Sending mail servers: 46.161.42[.]2 through 46.161.42[.]32
- Received from: simplexhealthcare[.]info ([46.161.42[.]2])
- Received from: 0937[.]org ([46.161.42[.]3])
- Received from: forbetteramerica[.]com ([46.161.42[.]4])
- Received from: managedprintservices-online[.]com ([46.161.42[.]5])
- Received from: 0downdeals[.]com ([46.161.42[.]6])
- Received from: 0human[.]org ([46.161.42[.]7])
- Received from: 0mgmix[.]co[.]uk ([46.161.42[.]8])
- Received from: 10000tables[.]org ([46.161.42[.]9])
- Received from: bulgariantravel[.]org ([46.161.42[.]10])
- Received from: successprogramsunlimited[.]net ([46.161.42[.]11])
- Received from: 121finance[.]in ([46.161.42[.]12])
- Received from: 123dep[.]com ([46.161.42[.]13])
- Received from: 123muaban[.]net ([46.161.42[.]14])
- Received from: thebodycontouringspecialist[.]com ([46.161.42[.]15])
- Received from: gotlube[.]net ([46.161.42[.]16])
- Received from: 1323[.]com ([46.161.42[.]17])
- Received from: 135798[.]com ([46.161.42[.]18])
- Received from: 138365[.]com ([46.161.42[.]19])
- Received from: whygavs[.]net ([46.161.42[.]20])
- Received from: 160h[.]com ([46.161.42[.]21])
- Received from: 16thbit[.]com ([46.161.42[.]22])
- Received from: 18005379327[.]com ([46.161.42[.]23])
- Received from: 180connection[.]org ([46.161.42[.]24])
- Received from: 180therapies[.]info ([46.161.42[.]25])
- Received from: optypo[.]com ([46.161.42[.]26])
- Received from: 1brx[.]com ([46.161.42[.]27])
- Received from: 1buscame[.]com ([46.161.42[.]28])
- Received from: 1jk[.]org ([46.161.42[.]29])
- Received from: 1roll[.]net ([46.161.42[.]30])
- Received from: 1roll[.]org ([46.161.42[.]31])
- Received from: 1tuangou[.]com ([46.161.42[.]32])
VARIOUS SENDERS FROM EACH OF THE ABOVE DOMAINS START WITH:
- From: admin@
- From: billing@
- From: help@
- From: info@
- From: mail@
- From: no-reply@
- From: noreply@
- From: sale@
- From: support@
- From: ticket@
EMAIL HEADERS
EMAIL HEADERS IN TODAY'S EXAMPLE:

Shown above: Screenshot from today's example.
Received: from [46.161.42[.]31] ([46.161.42[.]31:51291] helo=1roll[.]org)
by [removed] (envelope-from <support@1roll[.]org>) [removed];
Thu, 27 Sep 2018 16:14:04 -0400
From: =?utf-8?B?TWlrZSBCcm9tYW4gwqA=?= <support@1roll[.]org>
To: [removed]
Subject: Application
Thread-Topic: Application
Date: Thu, 27 Sep 2018 19:42:18 +0000
Message-ID: <2gew194jz9seuvipzp6ajpvm.1962140182032@1roll[.]org>
Content-Language: en-US
Content-Type: multipart/mixed;
boundary="------------703162491244836653324287"
MIME-Version: 1.0
Errors-To: >bouncechecker@yahoo[.]com>
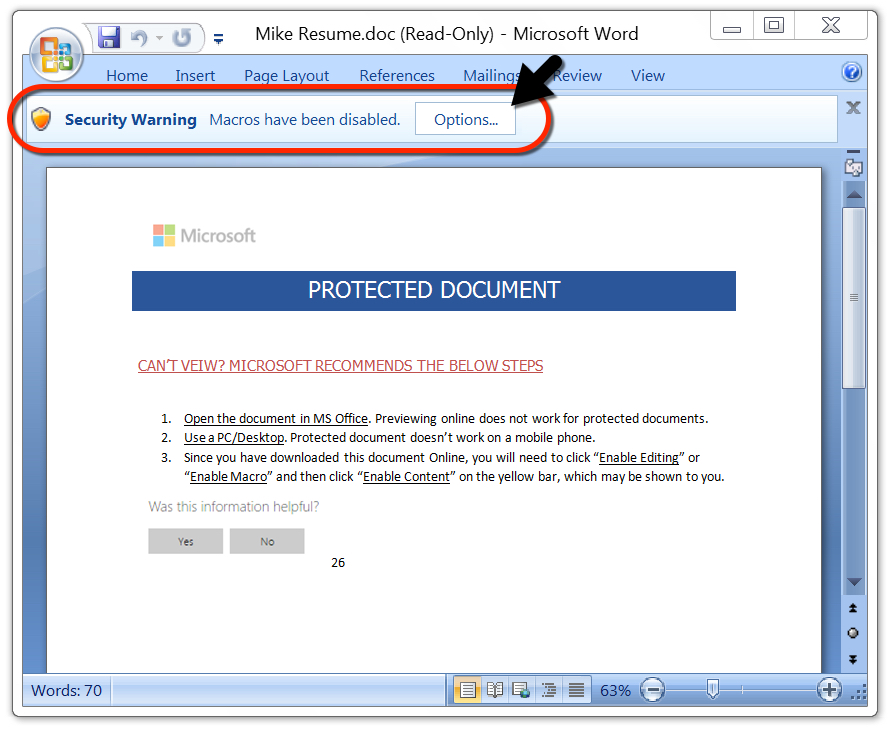
Shown above: To get infected, I had to enable macros after unlocking the Word document.
TRAFFIC
TRAFFIC FROM AN INFECTED WINDOWS HOST:
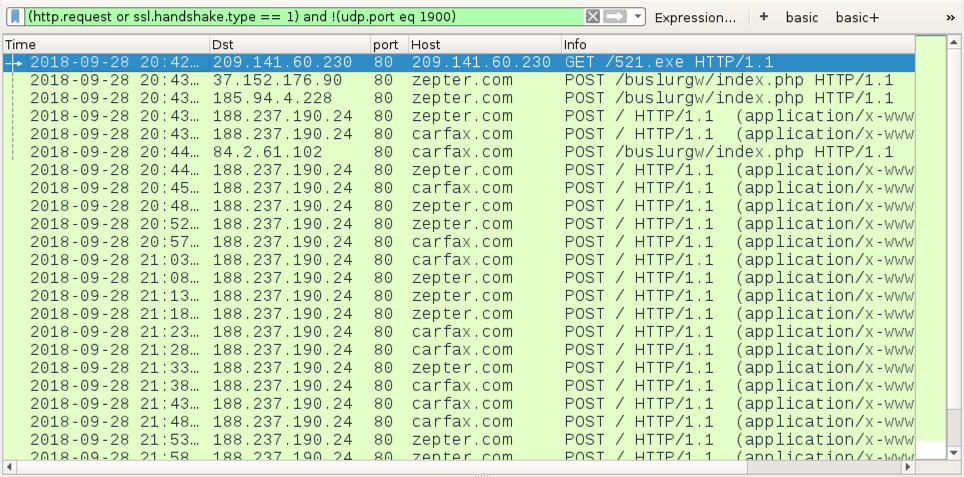
Shown above: Infection traffic filtered in Wireshark.
- 209.141.60[.]230 port 80 - 209.141.60[.]230 - GET /521.exe
- 37.152.176[.]90 port 80 - zepter[.]com - POST /buslurgw/index.php
- 185.94.4[.]228 port 80 - zepter[.]com - POST /buslurgw/index.php
- 84.2.61[.]102 port 80 - carfax[.]com - POST /buslurgw/index.php
- 188.237.190[.]24 port 80 - zepter[.]com - POST /
- 188.237.190[.]24 port 80 - carfax[.]com - POST /
- DNS queries for geisbfreco[.]com to Google DNS (8.8.4[.]4 and 8.8.8[.]8)
- DNS queries for microsoft[.]com to Google DNS (8.8.4[.]4 and 8.8.8[.]8)
- DNS queries for google[.]com to Google DNS (8.8.4[.]4 and 8.8.8[.]8)
- NOTE: carfax[.]com and zepter[.]com are legitimate domains that are being spoofed.
FILE HASHES
ATTACHED WORD DOCUMENT:
- SHA256 hash: a38a15cb84d110b1628626eb2267698f5d23307a59fcc66b49fbe94f04bb053e
File size: 39,424 bytes
File name: Mike Resume.doc
INITIAL NYMAIN BINARY:
- SHA256 hash: 6895cd54fe75529b2f510d8a9a0eb1bbda34e6d8ad29462529edbe977bffb926
File size: 1,327,104 bytes
File location: C:\Users\[username]\AppData\Local\qwerty2.exe
FOLLOW-UP NYMAIM MALWARE:
- SHA256 hash: 8b45578a90cc9ef139e66e2d77dbabc83694d1e89ffed928c65baafa0d4b99f0
File size: 887,808 bytes
Associated shortcut location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
Associated shortcut name: gamma-1.lnk
Shortcut target: C:\Users\[username]\AppData\Roaming\gamma-25\gamma-2.exe -5d
- SHA256 hash: 11eb17a580da49282f7d41f7cebebe5c60c46df6aaefd2283a2741c7afe2dfc5
File size: 887,808 bytes
Associated registry key: HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
Value name: shell
Value type: REG_SZ
Value data: C:\ProgramData\kanal-2\kanal-4.exe -1,explorer.exe
- SHA256 hash: 78fabf339b726203334bb592812ab42c8652ab37535eeccf2e457df257d7a881
File size: 862,720 bytes
Associated registry key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Value name: machine-36
Value type: REG_SZ
Value data: C:\Users\[username]\AppData\Local\machine-27\machine-88.exe -x
Click here to return to the main page.
