2018-10-10 - MALSPAM LINK LEADS TO FAKE UPDATER MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2018-10-10-fake-updater-infection-traffic.pcap.zip 2.5 MB (2,510,897 bytes)
- 2018-10-10-fake-updater-infection-traffic.pcap (2,813,365 bytes)
- Malware: 2018-10-10-malware-from-fake-updater-traffic.zip 283 kB (283,144 bytes)
- 2018-10-10-follow-up-fake-updater-update_v1201.exe (48,192 bytes)
- 2018-10-10-follow-up-malware-1st-decoded-binary.dll (59,392 bytes)
- 2018-10-10-follow-up-malware-2nd-decoded-binary.dll (62,464 bytes)
NOTES:
- Thanks to the reader who tipped me off to this information. You know who you are!
- Unfortunately, I do not have a copy of the original message to share.
- I also don't have a positive identification on this malware. It's either a Tofsee variant or TinyNuke/TiNukeBot.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs or partial URLs:
- hxxp[:]//gfafoods[.]com/v5/report/id23779
- hxxp[:]//prestoquest[.]com/v5/report/id23779
- hxxps[:]//www.eastendbuzz[.]com/vosg/report/
- hxxp[:]//46.249.59[.]67/saite/gate.php?
- hxxp[:]//185.238.1[.]188/saite/gate.php?
- hxxp[:]//185.238.1[.]189/saite/gate.php?
- hxxp[:]//185.238.1[.]190/saite/gate.php?
Date/Time: Wednesday 2018-10-10 at 16:08 UTC
From: info@viveto[.]de
Subject: Statement of claim ID 23779
Email description: URLs in the email point to a fake report page with a link to a supposed document. When a victim clicks the download button, a message appears that claims you need an update to view the document. This new link returns malicious Windows executable.
INFECTION TRAFFIC
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 23.95.97[.]32 port 80 - gfafoods[.]com - GET /v5/report/id24267
- 216.172.168[.]138 port 443 - www.eastendbuzz[.]com - GET /vosg/report/ (fake document page)
- 216.172.168[.]138 port 443 - www.eastendbuzz[.]com - GET /vosg/report/download/1539212304/update_v1201.exe (URL for fake updater)
- 185.238.1[.]189 port 80 - 185.238.1[.]189 - POST /saite/gate.php?0123456789ABCDEF012345 (404 not found)
- 185.238.1[.]190 port 80 - 185.238.1[.]190 - POST /saite/gate.php?0123456789ABCDEF012345 (404 not found)
- 185.238.1[.]188 port 80 - 185.238.1[.]188 - POST /saite/gate.php?0123456789ABCDEF012345 (404 not found)
- 46.249.59[.]67 port 80 - 46.249.59[.]67 - POST /saite/gate.php?0123456789ABCDEF012345
MALWARE
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: f5b964979b64c6a6e304bbc190fa650de8f18b3bad64567de127f80ff00d9548
File size: 448,192 bytes
File name: update_v1201.exe
File description: Downloaded Windows executable file from fake updater notification.
- SHA256 hash: d96399f12341c4bd4e505fc8a82da23620c71fdb3632775c73ea5ffce8a5310b
File size: 59,392 bytes
File description: First of 2 DLLs retrieved by fake updater malware.
- SHA256 hash: 08f6a12a8dd92351f1977de5661a5d14504aa89485ecc99ac6706a255938380d
File size: 62,464 bytes
File description: Second of 2 DLLs retrieved by fake updater malware.
IMAGES

Shown above: Fake document page after clicking link from the email.
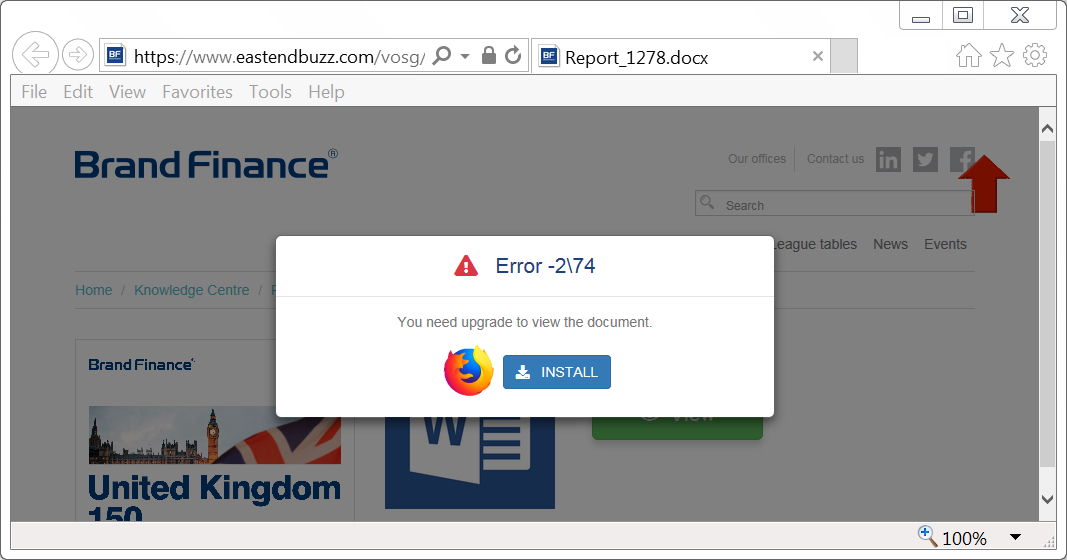
Shown above: Fake updater notification when you click on page for the document.
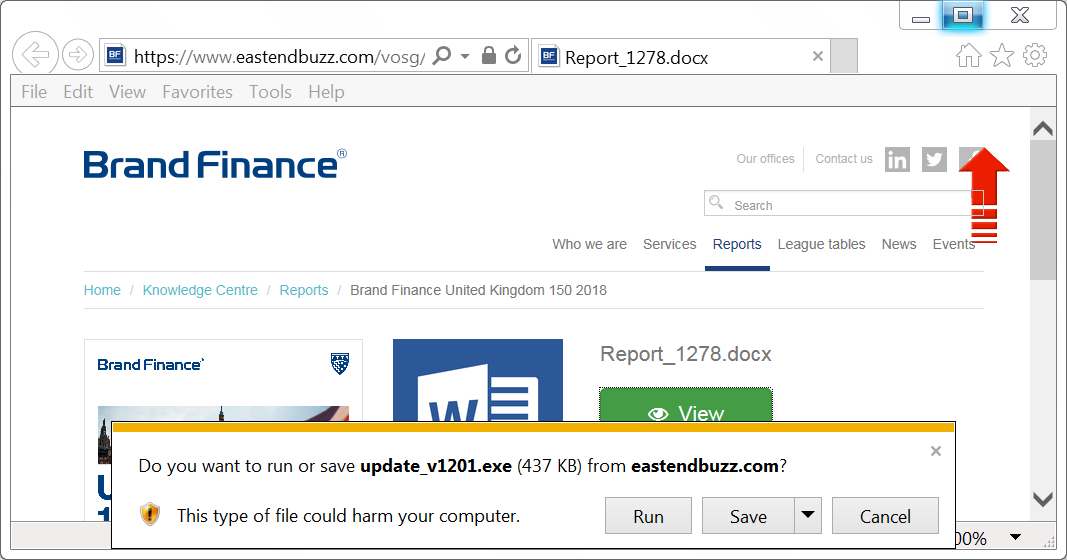
Shown above: Download notification for fake updater.
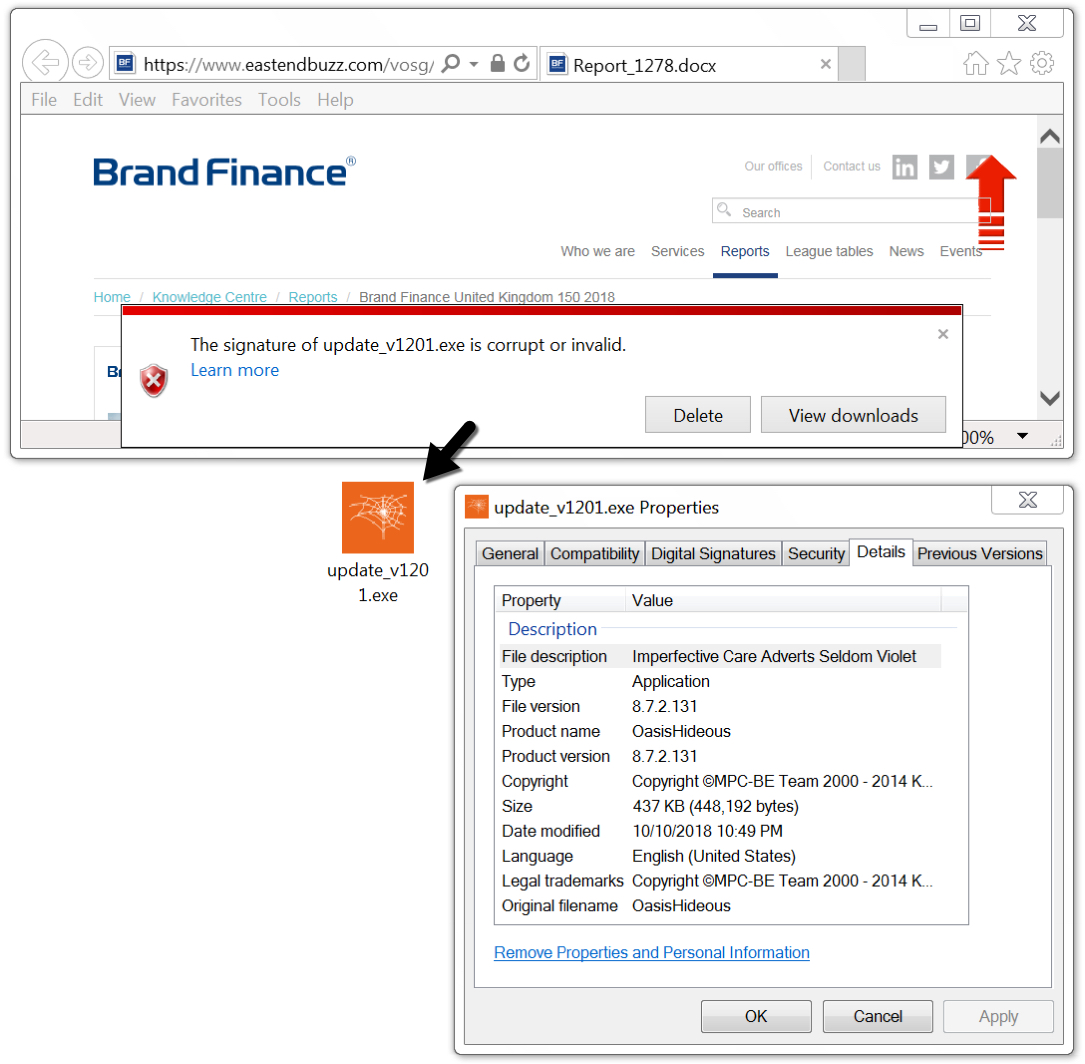
Shown above: Browser notification that digital signature of downloaded EXE file is corrupt or invalid.
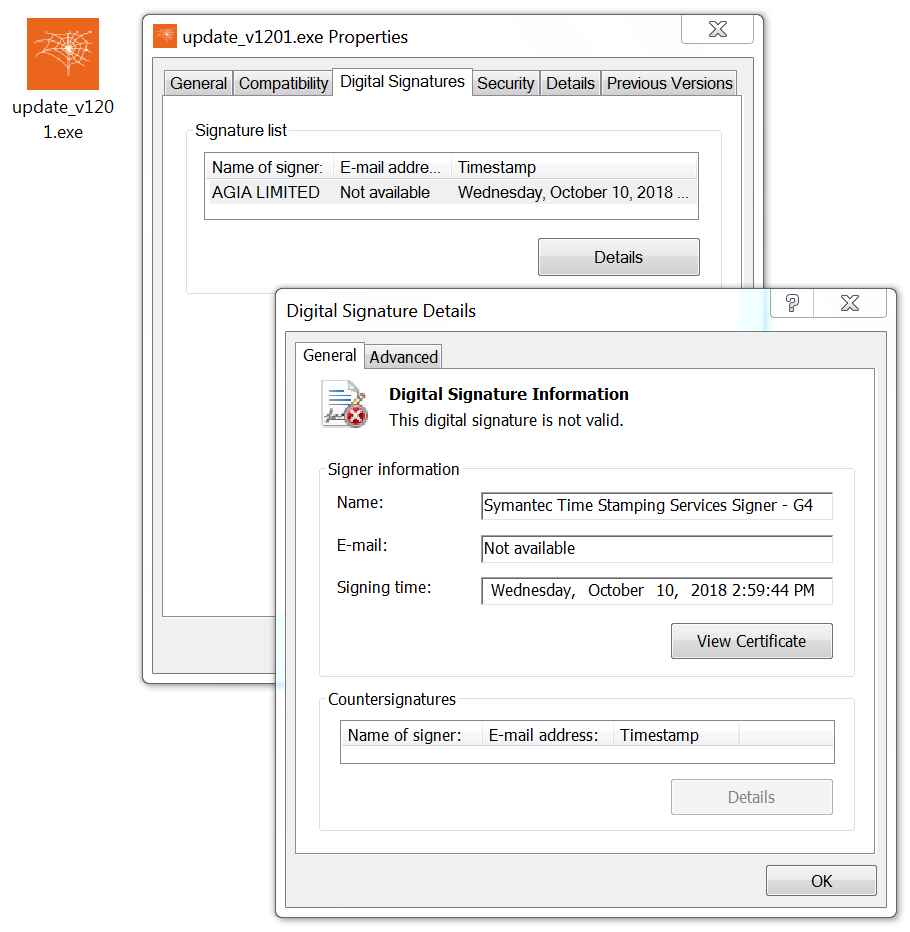
Shown above: More information on the digital signature of this malware.
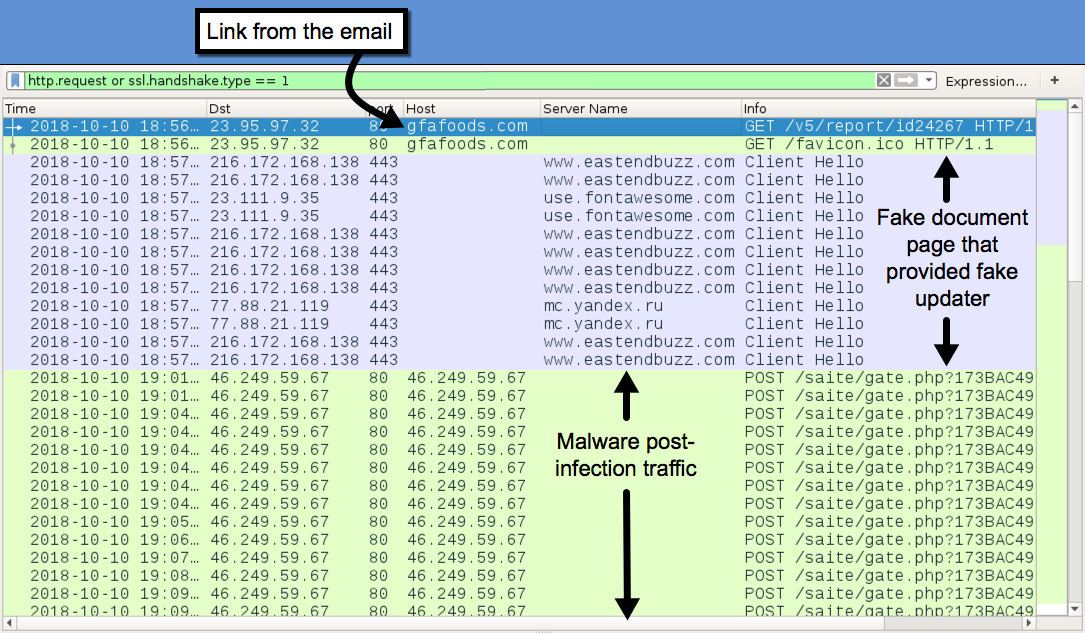
Shown above: Traffic from the infection filtered in Wireshark.
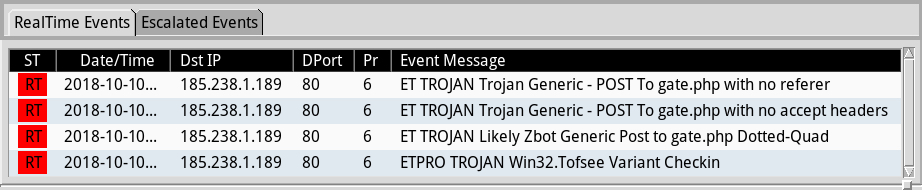
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
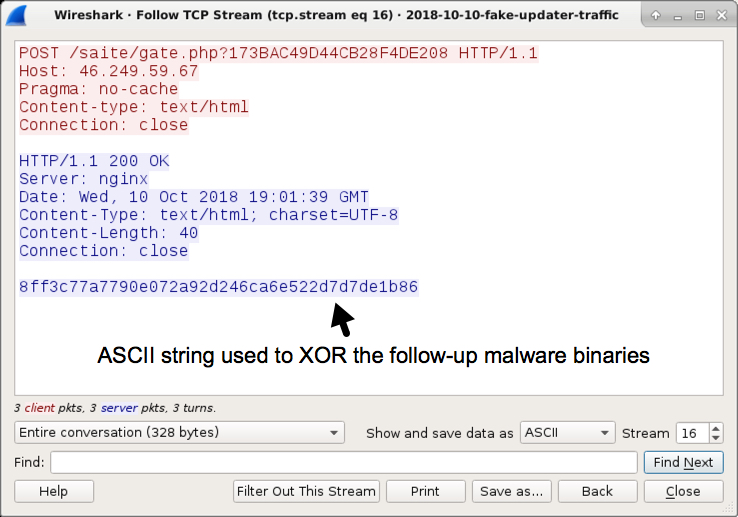
Shown above: Post-infection traffic with ASCII string used to XOR the follow-up malware binaries.
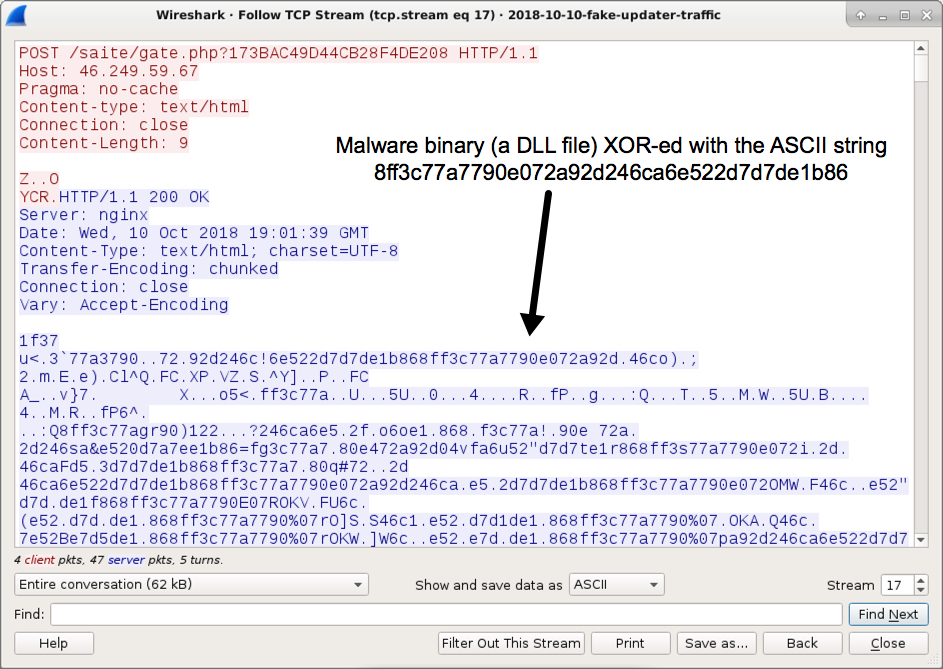
Shown above: One of the follow-up malware DLL files sent during post-infection traffic.
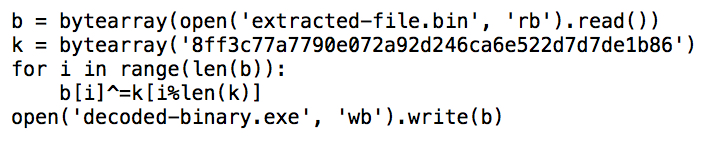
Shown above: Example of a Python script to decode follow-up binaries to get the malware DLL files.
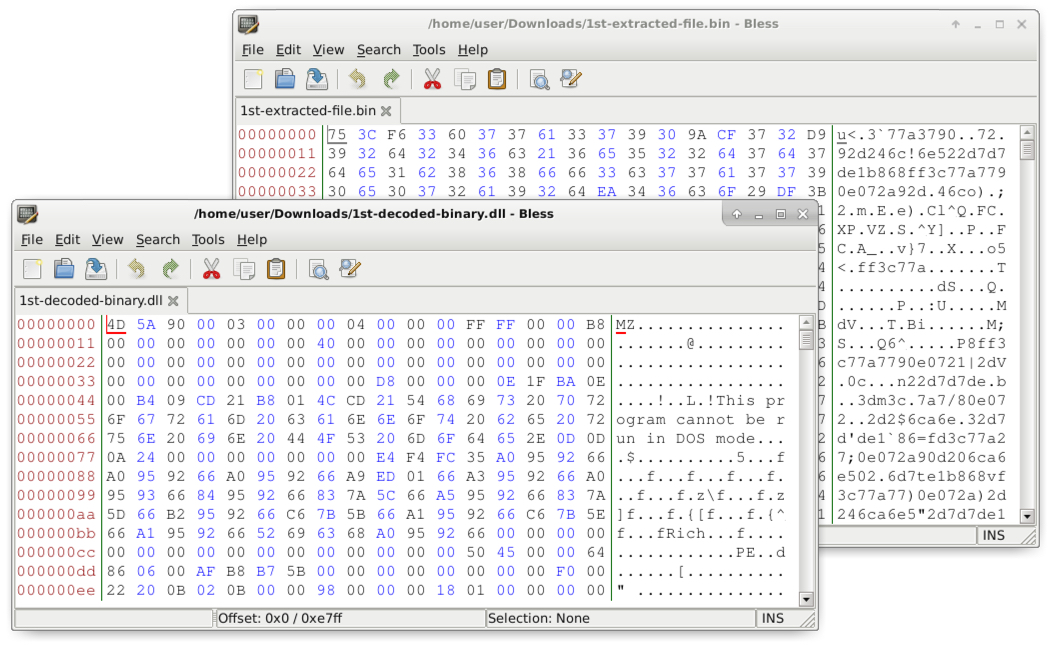
Shown above: Examples of "before" and "after" shots when decoding a binary for the DLL.
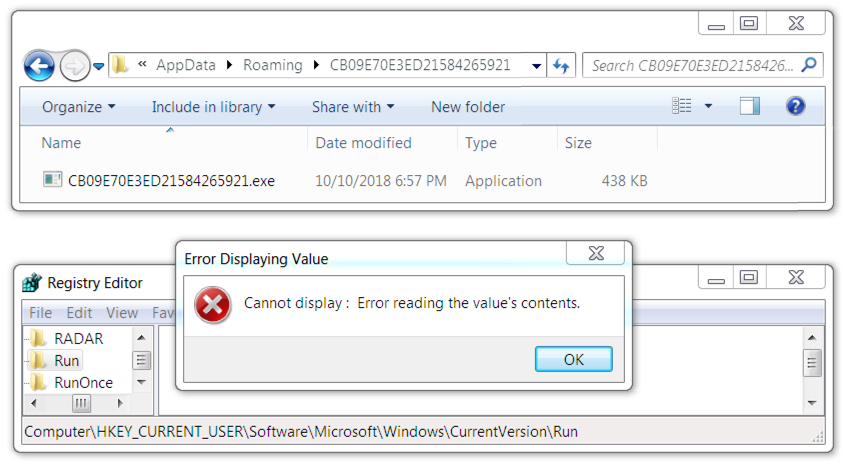
Shown above: Fake installer malware persistent on the infected Windows host.
Click here to return to the main page.
