2018-10-12 - HOOKADS CAMPAIGN FALLOUT EK (3 EXAMPLES)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2018-10-12-Hookads-campaign-Fallout-EK-pcaps.zip 6.8 MB (6,826,134 bytes)
- 2018-10-12-1st-run-Hookads-campaign-Fallout-EK-sends-Minotaur-ransomware.pcap (71,422 bytes)
- 2018-10-12-2nd-run-Hookads-campaign-Fallout-EK-sends-AZORult-and-follow-up-malware.pcap (5,522,466 bytes)
- 2018-10-12-3rd-run-Hookads-campaign-Fallout-EK-sends-AZORult-and-follow-up-malware.pcap (5,913,663 bytes)
- Malware: 2018-10-12-malware-and-artifacts-from-Fallout-EK-infections.zip 511 kB (512,480 bytes)
- 2018-10-12-1st-run-Fallout-EK-landing-page.txt (52,667 bytes)
- 2018-10-12-1st-run-Hookads-campaign-payload-Minotaur-ransomware.exe (11,776 bytes)
- 2018-10-12-1st-run-Minotaur-ransomware-How_To_Decrypt_Files.txt (1,290 bytes)
- 2018-10-12-2nd-run-Fallout-EK-landing-page.txt (576,24 bytes)
- 2018-10-12-2nd-run-Hookads-campaign-payload-AZORult.exe (319,488 bytes)
- 2018-10-12-2nd-run-follow-up-malware-caused-by-AZORult.exe (421,888 bytes)
- 2018-10-12-2nd-run-scheduled-task-for-follow-up-malware-Test_Task17.xml.txt (1,547 bytes)
- 2018-10-12-example-of-traffic-to-removekingonline.pro.txt (6,220 bytes)
NOTES:
- The Hookads campaign uses malvertising that leads to a fake dating website.
- The fake dating website for today's traffic is datingittlive.info, which led to Fallout EK.
- Payload during the first run was Minotaur ransomware, which only encrypted files on a USB key connected to my test host.
- Minotaur ransomware did not encrypt anything on the C:\ drive, and it caused no post-infection traffic.
- Payload during the second and third runs was AZORult, which also caused follow-up malware.
- I could not identify the follow-up malware. It might be a new version of Ramnit, but post-infection activity doesn't match what I last documented for Ramnit in Feburary 2018.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- bitdotz[.]top
- datingittlive[.]info
- guarana[.]pw
- marryjane[.]club
- names34[.]top
- removekingonline[.]pro
- safi[.]co[.]za
TRAFFIC
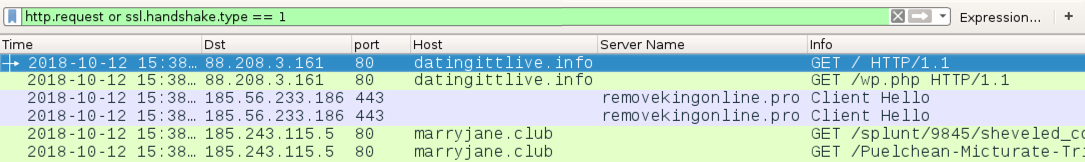
Shown above: Traffic during the first run filtered in Wireshark, where Fallout EK sent Minotaur ransomware.

Shown above: Traffic during the third run filtered in Wireshark, where Fallout EK sent AZORult and follow-up malware.

Shown above: Post-infection TCP traffic from the follow-up malware to names34[.]top (1 of 2).
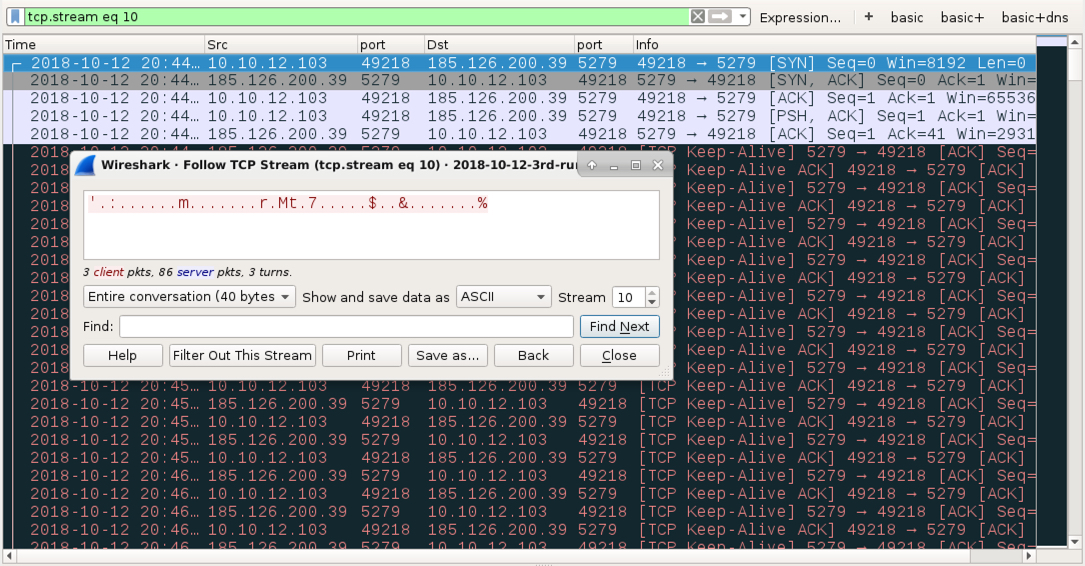
Shown above: Post-infection TCP traffic from the follow-up malware to names34[.]top (2 of 2).
FIRST RUN (MINOTAUR RANSOMWARE):
- 88.208.3[.]161 port 80 - datingittlive[.]info - GET /
- 88.208.3[.]161 port 80 - datingittlive[.]info - GET /wp.php
- 185.56.233[.]186 port 443 - removekingonline[.]pro - GET /keez/jenkereeg
- 185.243.115[.]5 port 80 - marryjane[.]club - Fallout EK
- No post-infection traffic for Minotaur ransomware
SECOND AND THIRD RUNS (AZORULT -> FOLLOW-UP MALWARE):
- 88.208.3[.]161 port 80 - datingittlive[.]info - GET /
- 88.208.3[.]161 port 80 - datingittlive[.]info - GET /wp.php
- 185.56.233[.]186 port 443 - removekingonline[.]pro - GET /keez/jenkereeg
- 193.29.58[.]71 port 80 - guarana[.]pw - Fallout EK
- 5.101.67[.]143 port 80 - bitdotz[.]top - POST /index.php (AZORult post-infection traffic)
- 5.101.67[.]143 port 80 - bitdotz[.]top - POST /index.php (AZORult post-infection traffic)
- 197.221.14[.]10 port 80 - safi[.]co[.]za - GET /winntx.exe (follow-up malware)
- 185.126.200[.]39 port 4000 - names34[.]top - Encoded/encrypted TCP traffic from follow-up malware
- 185.126.200[.]39 port 5263 - names34[.]top - Encoded/encrypted TCP traffic from follow-up malware
- NOTE: In the 3rd run, TCP traffic to 185.126.200.39 was on TCP port 4000 and 5279. The destination port for the second TCP stream to 185.126.200[.]39 was different for each infection.
MALWARE
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 26b1811024cc6164e0762dfc9be4412306ddea782f15b1763c1abd4b5fff3e07
File size: 11,776 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[4 random hex characters].tmp
File description: Hookads payload sent by Fallout EK - Minotaur ransomware (Windows EXE file)
- SHA256 hash: a70231d9459c938d409e5334a0a5a41667a85175b9c07b60294eec826ba58f18
File size: 319,488 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[4 random hex characters].tmp
File description: Hookads payload sent by Fallout EK - AZORult (Windows EXE file)
- SHA256 hash: f0b2b5e48230a5ad021890477dba75fd4c781121025bb3bf1a95cb5e948777f0
File size: 421,888 bytes
File location: hxxp[:]//safi[.]co[.]za/winntx.exe
File location: C:\Users\[username]\AppData\Local\Temp\winntx.exe
File location: C:\ProgramData\[random characters]\[random characters].exe
File description: Follow-up malware (Windows EXE file) caused by AZORult.
IMAGES

Shown above: Encrypted files on a USB stick from the Minotaur ransomware infection. And that email address for the ransom... minotaur@420blaze.it Cute.
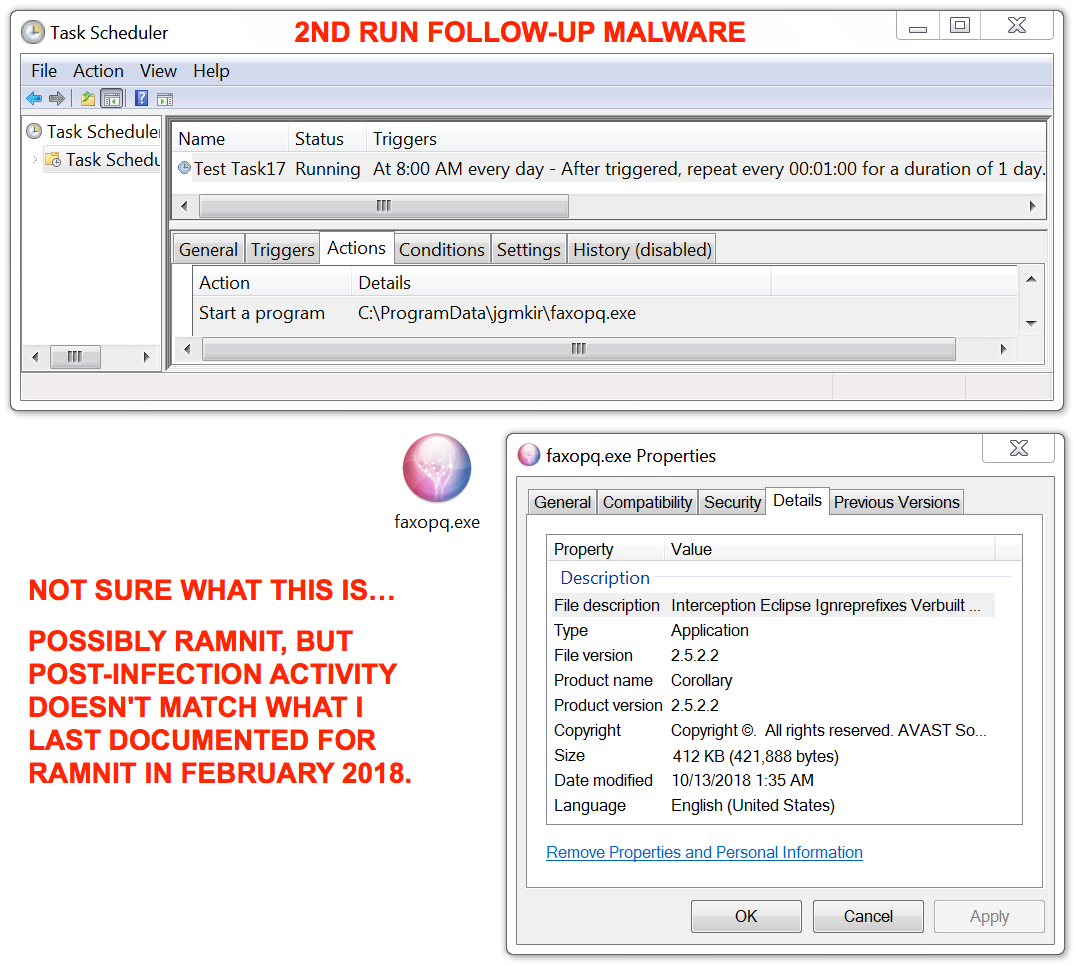
Shown above: Follow-up malware made persistent on the infected Windows host from the 3rd run (same malware seen during the 2nd run).
Click here to return to the main page.
