2018-10-18 - TRICKBOT MALSPAM USING LINKS, NOT ATTACHMENTS (GTAG: ANY1)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2018-10-18-Trickbot-spreads-from-client-to-DC.pcap.zip 36 MB (36,003,371 bytes)
- Malware and artifacts: 2018-10-18-Trickbot-malware-and-artifacts.zip 27 MB (27,022,801 bytes)
NOTES:
- I found a bunch of URLs returning a Word doc with macro for Trickbot on Wednesday 2018-10-17.
- These are most likely coming from malspam, but I cannot find any of the emails.
- Most of these sites hosting the Word docs are still active as of Thursday 2018-10-18.
- Today's traffic is another example of Trickbot spreading from the infected client to an Active Directory (AD) domain controller.
- Also saw AZORult during the Trickbot post-infection traffic.
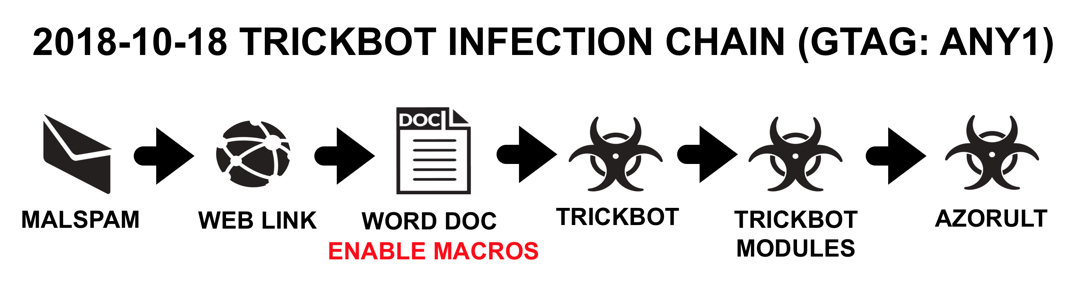
Shown above: Flowchart for today's Trickbot activity.
DOMAINS AND URLS
SITES PUSHING THE WORD DOCUMENTS:
- haisanthuytrieu[.]com
- lachinsabegh[.]com
- nongsan24h[.]com
- official-agent[.]website
- printnow[.]club
EXAMPLES OF URLS THAT RETURNED WORD DOCUMENTS:
- hxxp[:]//haisanthuytrieu[.]com/123/ORDER_04300.doc
- hxxp[:]//haisanthuytrieu[.]com/123/ORDER_267422.doc
- hxxp[:]//haisanthuytrieu[.]com/123/ORDER_684646.doc
- hxxp[:]//lachinsabegh[.]com/123/REQ_52997.doc
- hxxp[:]//lachinsabegh[.]com/123/REQ_179259.doc
- hxxp[:]//nongsan24h[.]com/1/REQ_4828.doc
- hxxp[:]//official-agent[.]website/123/ORDER_51048.doc
- hxxp[:]//printnow[.]club/123/REQ_4789.doc
- hxxp[:]//printnow[.]club/123/REQ_5911.doc
- hxxp[:]//printnow[.]club/123/REQ_7945.doc
- hxxp[:]//printnow[.]club/123/REQ_50907.doc
- hxxp[:]//printnow[.]club/123/REQ_93584.doc
- hxxp[:]//printnow[.]club/123/REQ_96240.doc
- hxxp[:]//printnow[.]club/123/REQ_156177.doc
- hxxp[:]//printnow[.]club/123/REQ_385315.doc
- hxxp[:]//printnow[.]club/123/REQ_405698.doc
- hxxp[:]//printnow[.]club/123/REQ_605500.doc
- hxxp[:]//printnow[.]club/123/REQ_644654.doc
- hxxp[:]//printnow[.]club/123/REQ_672029.doc
- hxxp[:]//printnow[.]club/123/REQ_878346.doc
- hxxp[:]//printnow[.]club/123/REQ_969031.doc
URLS FOR TRICKBOT BINARIES:
- hxxp[:]//46.173.219[.]15/pro.any
- hxxp[:]//46.173.219[.]17/pro.any
- hxxp[:]//185.251.39[.]251/radiance.png
- hxxp[:]//185.251.39[.]251/table.png
- hxxp[:]//185.251.39[.]251/worming.npg
URLS FOR AZORULT:
- hxxp[:]//printnow[.]club/au3.exe
MALWARE
DOWNLOADED WORD DOC WITH MACRO FOR TRICKBOT:
- SHA256 hash: ade60e104de69920d17776b0ebcdf5b48244c49f27ed91fae9741f7f958a2eb9
File size: 89,088 bytes
TRICKBOT MALWARE BINARY (GTAG: ANY1):
- SHA256 hash: 67fccd872795a7e1bef8b0077bc09dd67d4c3a3f5b1720ac0df77b3fb94aa96e
File size: 549,823 bytes
AZORULT:
- SHA256 hash: 1744879954a7c0f6d7a7a9f82834564870865ad28e3ca25116a7c55de163a01f
File size: 567,808 bytes
IMAGES
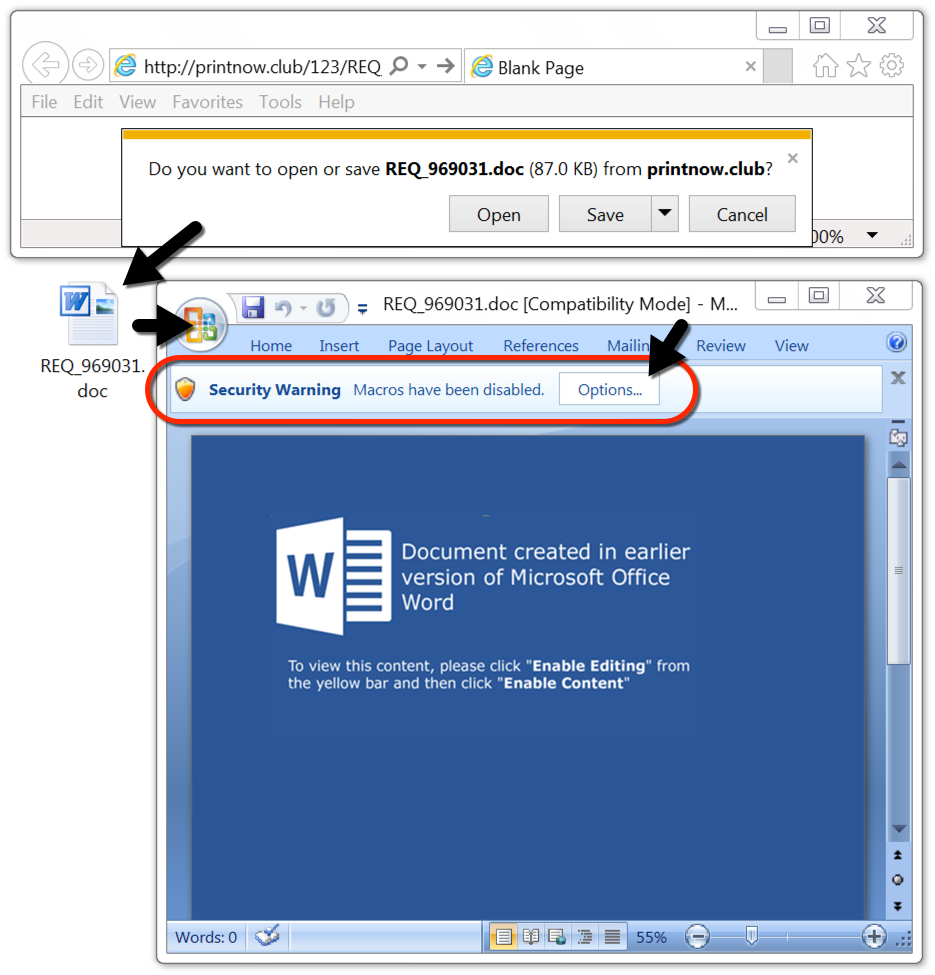
Shown above: Downloading a Word documents from one of the malspam links.
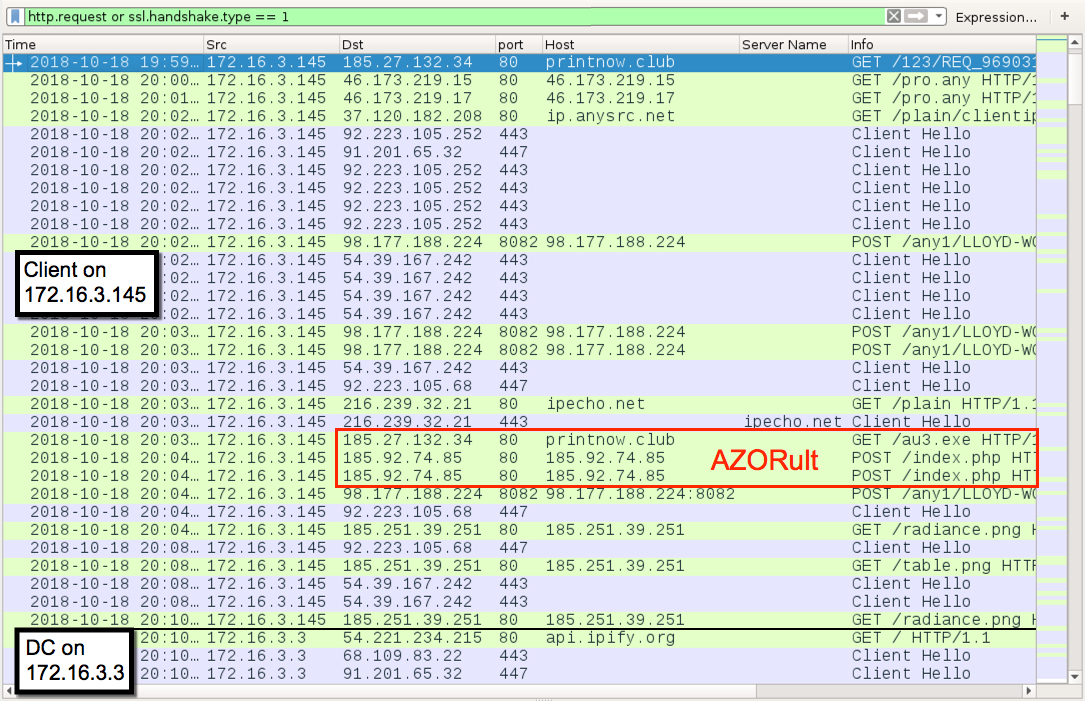
Shown above: Traffic from an infection filtered in Wireshark.
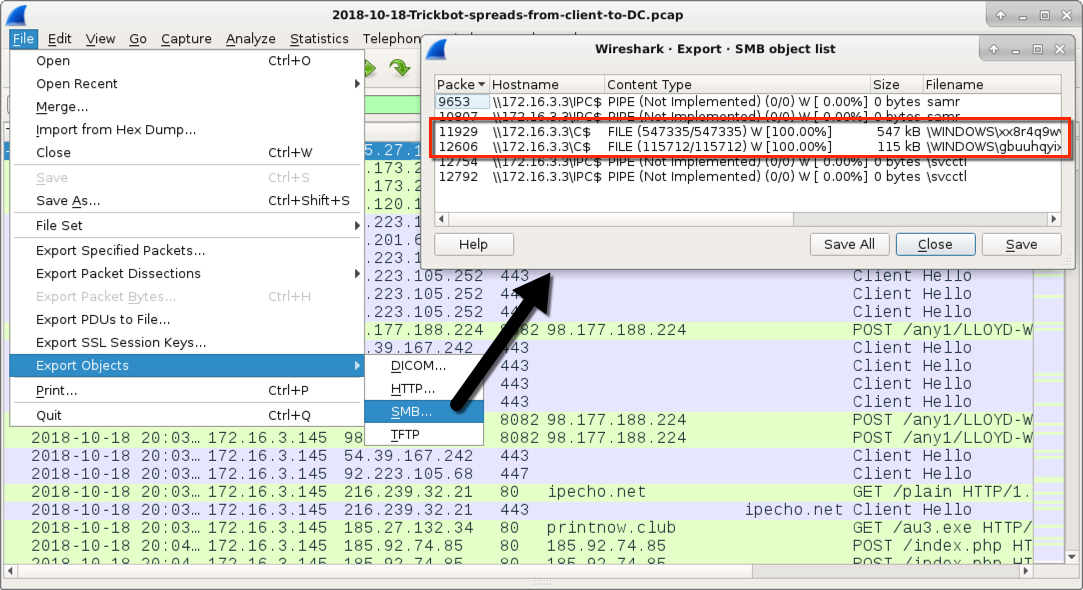
Shown above: Extracting Trickbot binaries from the SMB traffic.
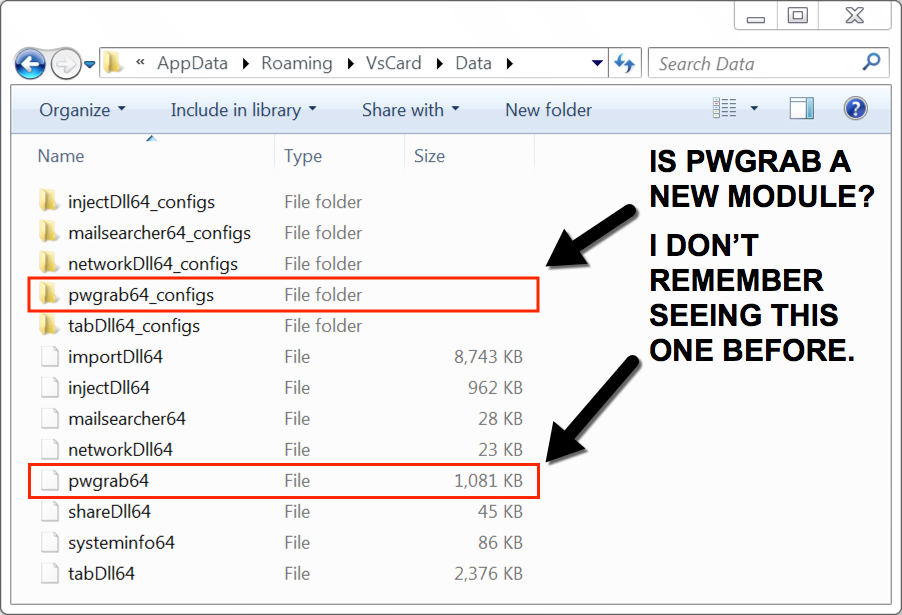
Shown above: Saw a pwgrab64 module I don't remember seeing before.
Click here to return to the main page.
