2018-10-26 - QUICK POST: TRICKBOT MALSPAM GTAG: SER1025US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2018-10-26-Trickbot-spreads-from-client-to-DC-ser1025us.pcap.zip 30.7 MB (30,699,674 bytes)
- 2018-10-26-Trickbot-spreads-from-client-to-DC-ser1025us.pcap (34,150,827 bytes)
- Malware: 2018-10-26-Trickbot-malware-and-artifacts.zip 27.8 MB (27,819,449 bytes)
- 2018-10-25-downloaded-Excel-file-invoice10252018.xls (54,272 bytes)
- 2018-10-25-downloaded-Trickbot-ser1025us.exe (392,704 bytes)
- 2018-10-26-radiance.png.exe (552,960 bytes)
- 2018-10-26-table.png.exe (552,960 bytes)
- 2018-10-26-worming.png.exe (552,960 bytes)
- Client/2018-10-26-sched-task-on-client-Msnetcs.txt (3,762 bytes)
- Client/WSOG/Data/importDll64 (8,952,080 bytes)
- Client/WSOG/Data/injectDll64 (982,992 bytes)
- Client/WSOG/Data/injectDll64_configs/dinj (71,264 bytes)
- Client/WSOG/Data/injectDll64_configs/dpost (880 bytes)
- Client/WSOG/Data/injectDll64_configs/sinj (59,200 bytes)
- Client/WSOG/Data/mailsearcher64 (27,824 bytes)
- Client/WSOG/Data/mailsearcher64_configs/mailconf (240 bytes)
- Client/WSOG/Data/networkDll64 (22,704 bytes)
- Client/WSOG/Data/networkDll64_configs/dpost (880 bytes)
- Client/WSOG/Data/pwgrab64 (1,106,256 bytes)
- Client/WSOG/Data/pwgrab64_configs/dpost (880 bytes)
- Client/WSOG/Data/shareDll64 (45,280 bytes)
- Client/WSOG/Data/systeminfo64 (87,728 bytes)
- Client/WSOG/Data/tabDll64 (2,432,864 bytes)
- Client/WSOG/Data/tabDll64_configs/dpost (880 bytes)
- Client/WSOG/Data/wormDll64 (59,168 bytes)
- Client/WSOG/settings.ini (64,614 bytes)
- Client/WSOG/tetup.exe (552,960 bytes)
- Client/WSOG/tmptetup.exe (392,704 bytes)
- DC/2018-10-26-other-Trickbot-related-binary-on-controller.exe (115,712 bytes)
- DC/2018-10-26-sched-task-on-DC-Sysnetsf.txt (3,628 bytes)
- DC/2018-10-26-Trickbot-binary-on-controller-gtag-lib341.exe (552,960 bytes)
- DC/WSOG/Data/importDll64 (8,952,080 bytes)
- DC/WSOG/Data/injectDll64 (982,992 bytes)
- DC/WSOG/Data/injectDll64_configs/dinj (71,264 bytes)
- DC/WSOG/Data/injectDll64_configs/dpost (880 bytes)
- DC/WSOG/Data/injectDll64_configs/sinj (59,200 bytes)
- DC/WSOG/Data/mailsearcher64 (27,824 bytes)
- DC/WSOG/Data/mailsearcher64_configs/mailconf (240 bytes)
- DC/WSOG/Data/networkDll64 (22,704 bytes)
- DC/WSOG/Data/networkDll64_configs/dpost (880 bytes)
- DC/WSOG/Data/pwgrab64 (1,106,256 bytes)
- DC/WSOG/Data/pwgrab64_configs/dpost (880 bytes)
- DC/WSOG/Data/shareDll64 (45,280 bytes)
- DC/WSOG/Data/systeminfo64 (87,728 bytes)
- DC/WSOG/Data/wormDll64 (59,168 bytes)
- DC/WSOG/settings.ini (34,461 bytes)
- DC/WSOG/tvvfm_9b0dzh7witxpr26xpnu710mn9hzrgi0bhf8dh6uoz4mh80on9kmuoy7sli.exe (552,960 bytes)
NOTES:
- Trickbot malspam targeting the US on Thursday 2018-10-25 (gtag: ser1025us) used links for .xls files hosted on deloitteca[.]com instead of attachments in the emails.
- Although I don't have an example of these emails, someone posted a secreenshot here.
- Follow-up Trickbot binaries named radiance.png, table.png, and worming.png came from 23.94.41[.]37 today on Friday 2018-10-26.
IMAGES
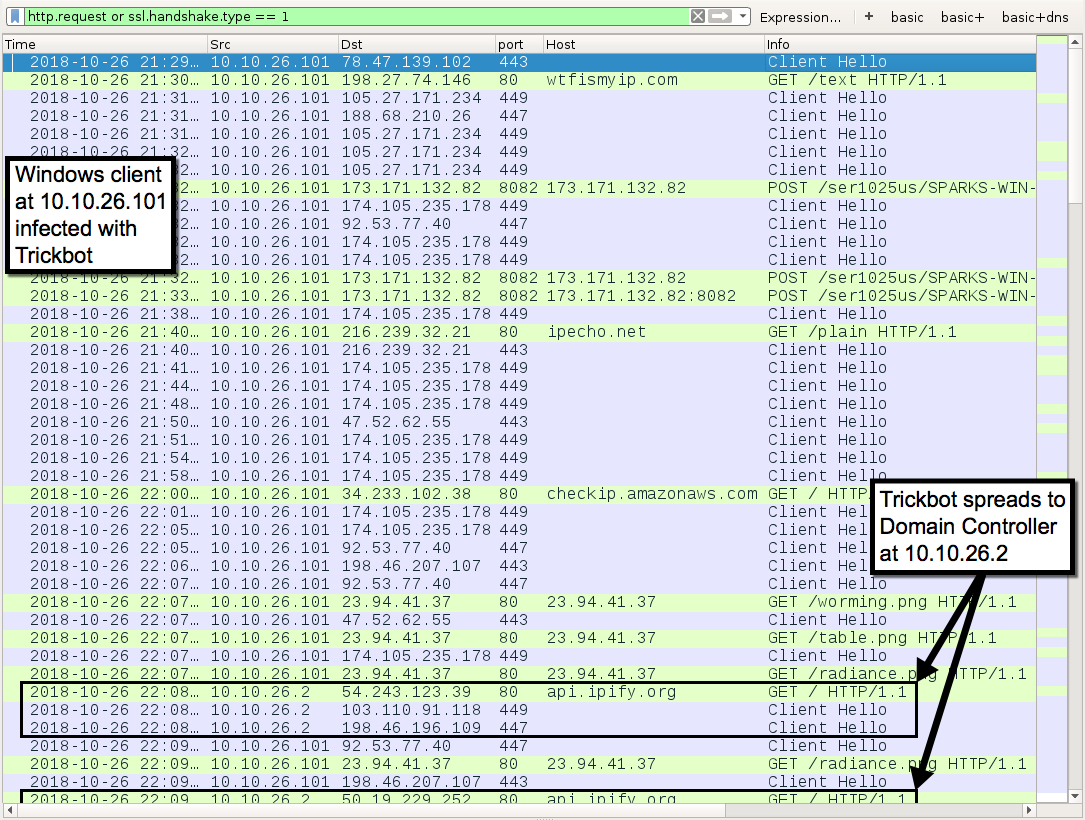
Shown above: Traffic from the infection filtered in Wireshark.
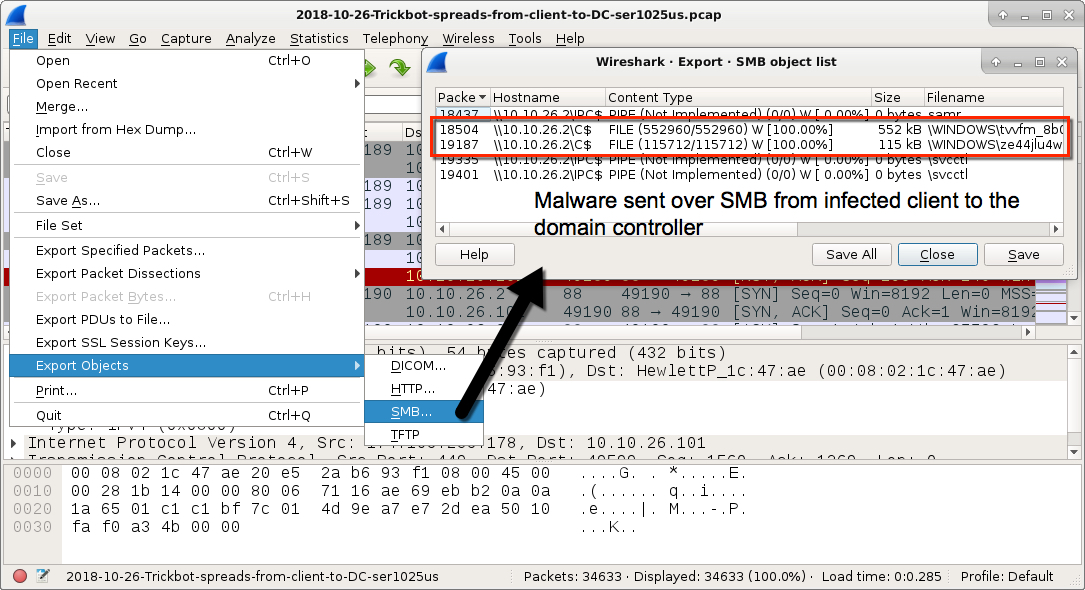
Shown above: Exporting malware sent from client to DC over SMB.
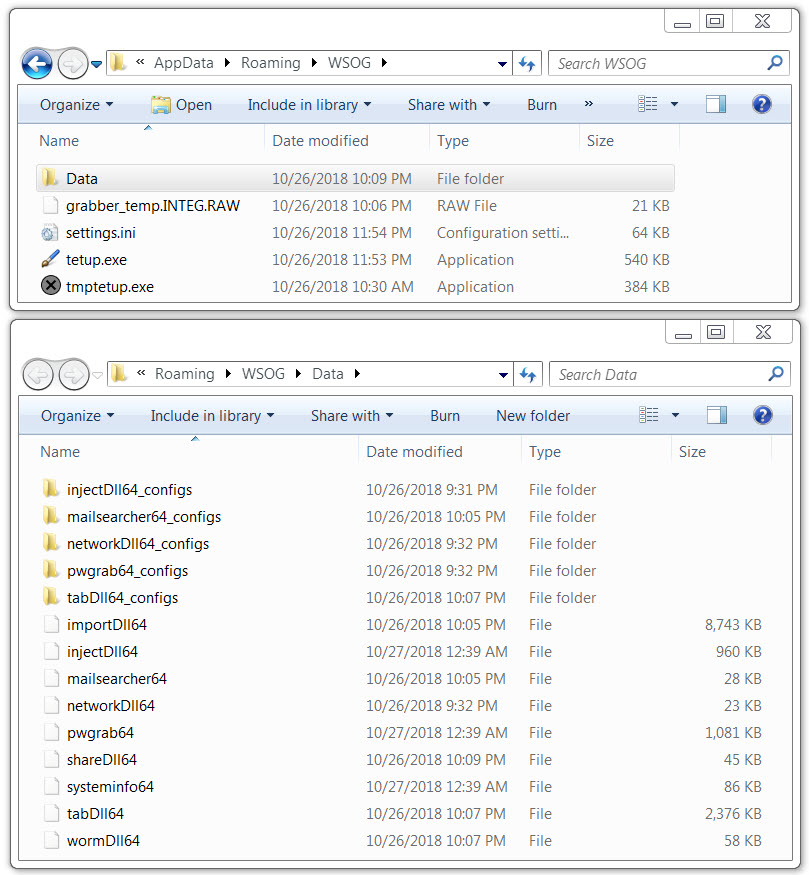
Shown above: Trickbot modules on the infected client.
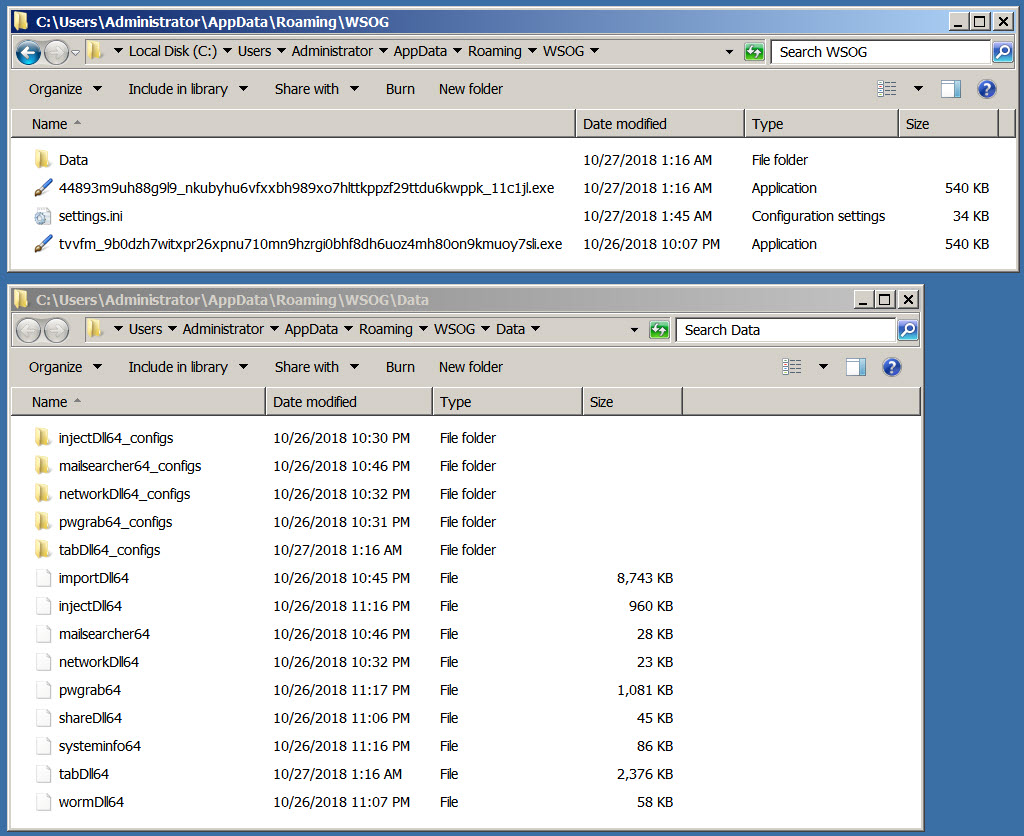
Shown above: Trickbot modules on the infected DC.
Click here to return to the main page.
