2018-11-02 - GANDCRAB RANSOMWARE INFECTION (VERSION 5.0.4)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2018-11-02-GandCrab-ransomware-infection.pcap.zip 1.3 MB (1,260,404 bytes)
- 2018-11-02-GandCrab-ransomware-infection.pcap (2,214,579 bytes)
- Malware and artifacts: 2018-11-02-GandCrab-malware-and-artifacts.zip 1.8 MB (1,754,752 bytes)
- 2018-11-02-GandCrab-decryption-instructions.txt (2,898 bytes)
- 2018-11-02-desktop-background-for-GandCrab-infection-pidor.bmp (3,145,782 bytes)
- 2018-11-02-t.exe-from-92.63.197.48.exe (142,336 bytes)
- 2018-11-02-vnc.exe-from-92.63.197.48.exe (159,744 bytes)
NOTES
There are a number of malicious executables on 92.63.197[.]48, and at least two of these are related to GandCrab ransomware. Not sure what's causing traffic to 92.63.197[.]48, but I found a similar GandCrab infection caused by a JavaScript (.js) file seen in September 2018. It's available at:
I tested one of the executable files from 92.63.197[.]48 on a Windows host in an Active Directory environment. Today's pcap has the following characteristics:
- LAN segment: 172.16.8[.]0/24 (172.16.8[.]0 thru 172.16.8[.]255)
- Gateway: 172.16.8[.]1
- Domain Controller: 172.16.8[.]8 - GONEAWRY-DC
- Domain: goneawry[.]net
- Infected Windows host: 172.16.8[.]195
This is a full pcap with internal activity to and from the domain controller, and it includes other web raffic not directly related to the GandCrab infection. Of note, GandCrab post-infection traffic hits several apparently legitimate domains, so I'm not including that information in today's blog post.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and tor domain:
- hxxp[:]//92.63.197[.]48/vnc.exe
- hxxp[:]//92.63.197[.]48/vnc/
- gandcrabmfe6mnef[.]onion
MALWARE
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 796a87b9905c52ff7d1da91f2ff980b5dfdb9437a09624ccb4e6d8fe470ea666
- File size: 159,744 bytes
- File location: hxxp[:]//92.63.197[.]48/vnc.exe
- File location: C:\Users\[username]\AppData\Local\Temp\Windows Archive Manager.exe
- File location: C:\Users\[username]\T80870405687060\winsvcs.exe
- File description: GandCrab downloader (caused additional downloads, made persistent)
- SHA256 hash: 098aad386b0f549cefddf2001dba9f31f40d88a3618cd3a8d5589b4b0b467342
- File size: 142,336 bytes
- File location: hxxp[:]//92.63.197[.]48/vnc/t.exe
- File location: C:\Users\[username]\AppData\Local\Temp\[random string of numbers].exe
- File description: GandCrab ransomware binary (did not cause additional downloads, not made persistent)
IMAGES
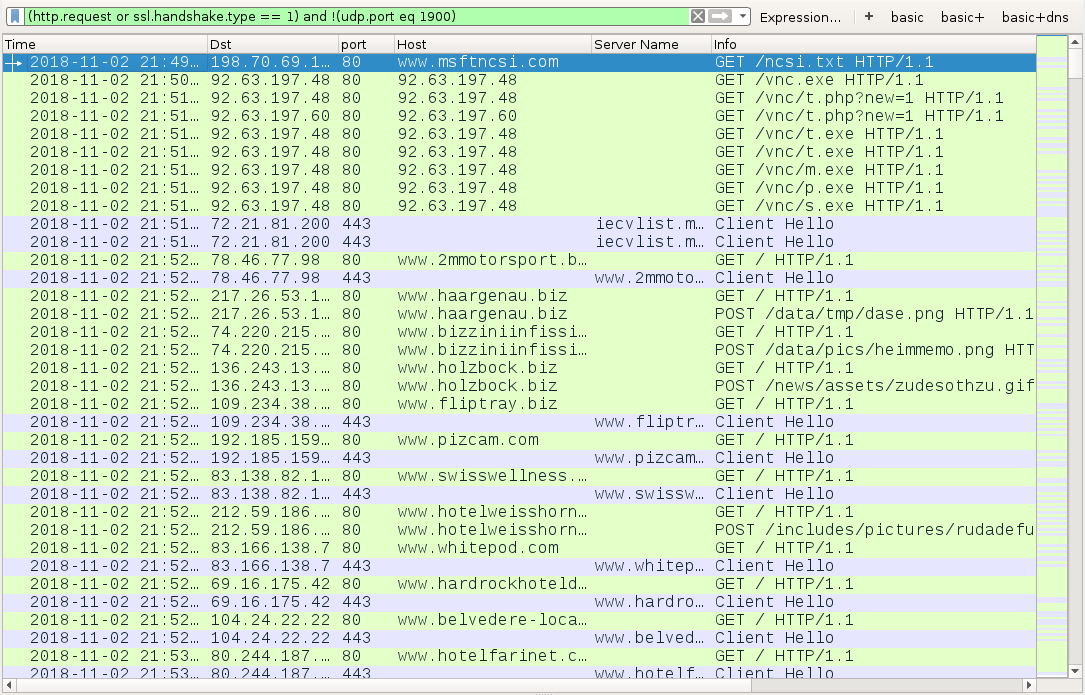
Shown above: Traffic from the infection filtered in Wireshark.
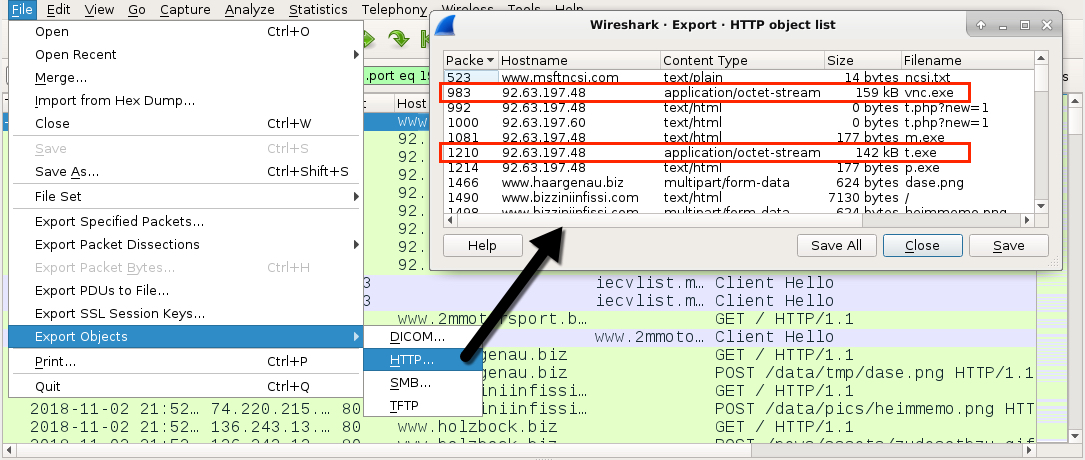
Shown above: Extracting the two GandCrab executables from the pcap using Wireshark.
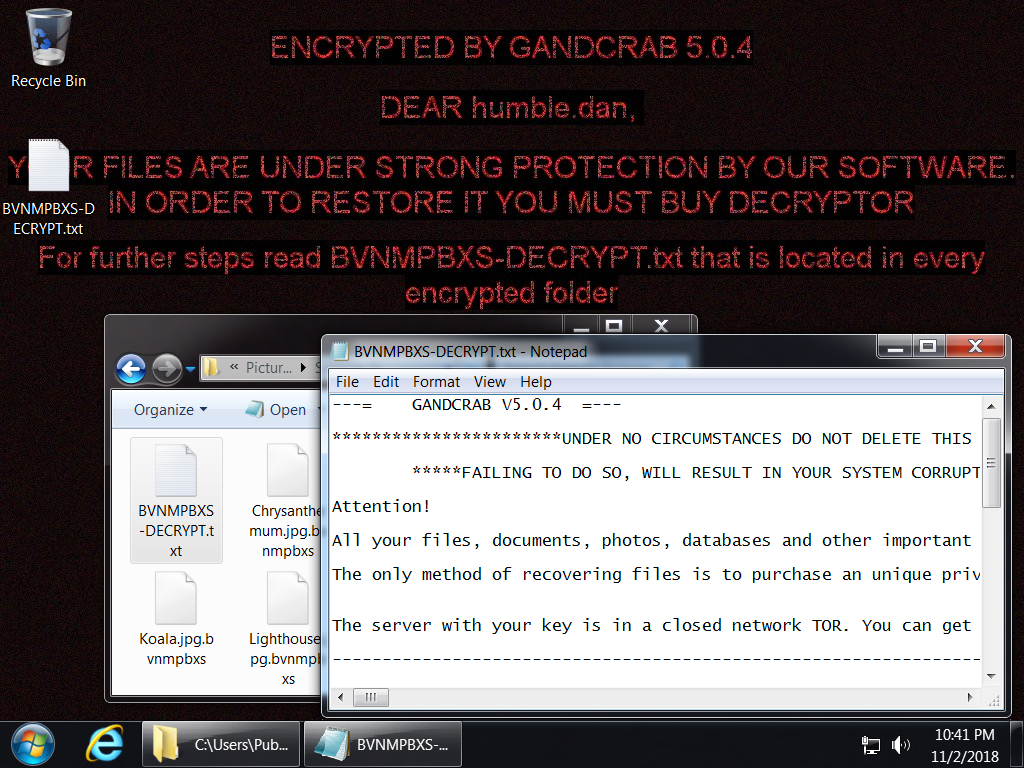
Shown above: Desktop from an infected Windows host. Of note, the file extension used on the encrypted files is different for each infection.
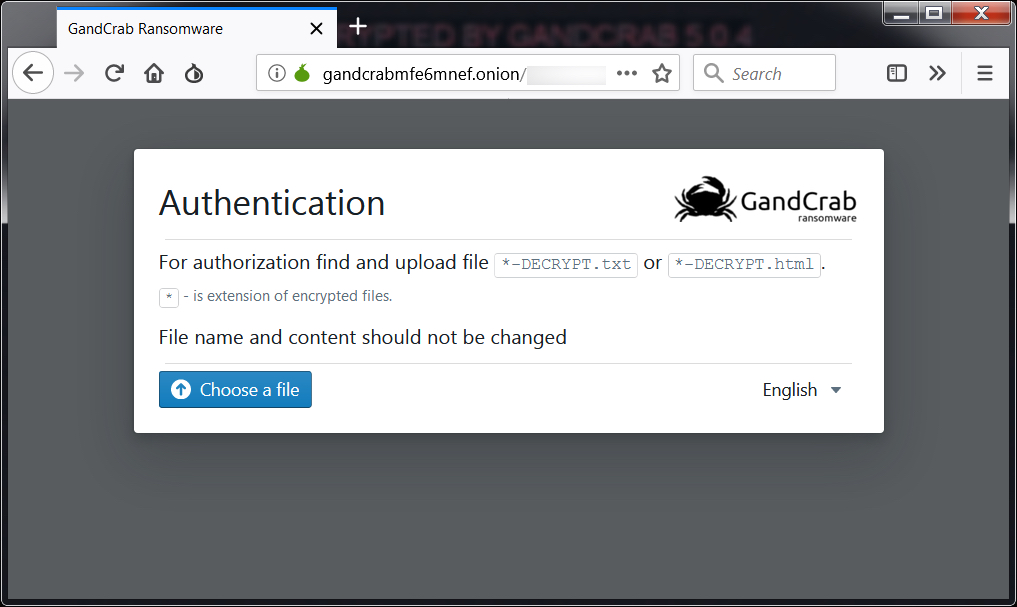
Shown above: When you first get to the GandCrab decryptor. Of note, it's a different URL for each infection.
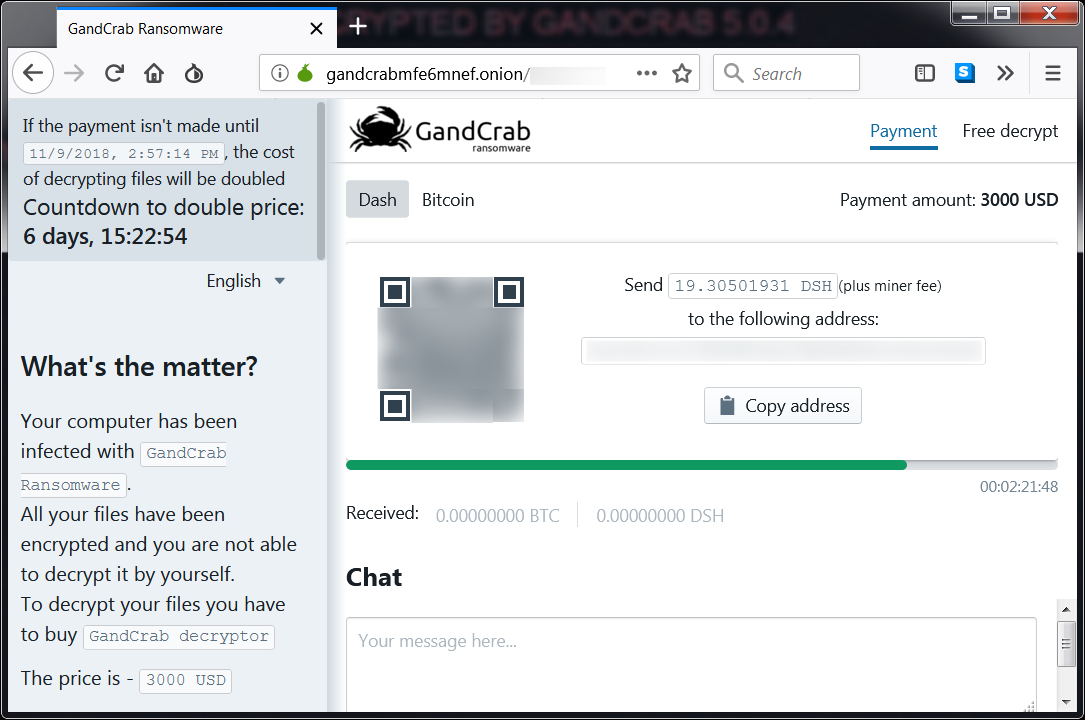
Shown above: GandCrab decryptor page. Of note, it's a different bitcoin or dash address for each infection.
Shown above: Expand the browser to see some rage comic images. What are rage comics, you ask? Check out the f7u12 subreddit for examples.
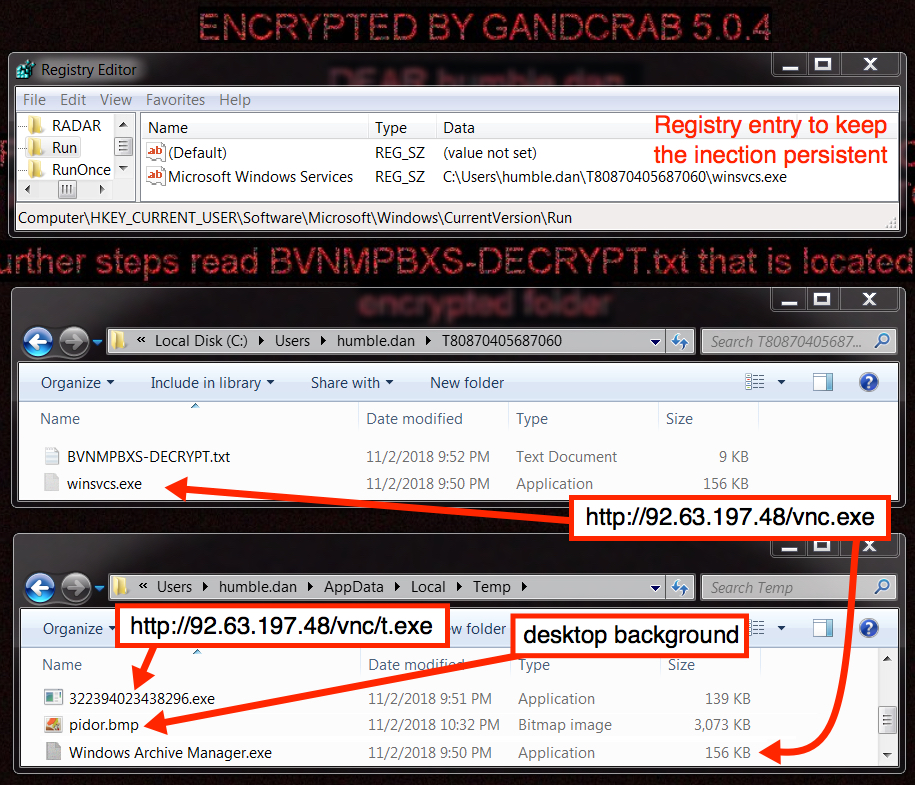
Shown above: Malware and artifacts on the infected Windows host.
Click here to return to the main page.
