2018-11-06 - EMOTET INFECTION WITH TRICKBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-11-06-Emotet-malspam-3-email-examples.zip 116 kB (116,259 bytes)
- 2018-11-06-Emotet-malspam-with-PDF-attachment.eml (29,068 bytes)
- 2018-11-06-Emotet-malspam-with-Word-attachment-1-of-2.eml (101,605 bytes)
- 2018-11-06-Emotet-malspam-with-Word-attachment-2-of-2.eml (96,946 bytes)
- 2018-11-06-Emotet-infection-with-Trickbot.pcap.zip 7.4 MB (7,410,712 bytes)
- 2018-11-06-Emotet-infection-with-Trickbot.pcap (7,919,501 bytes)
- 2018-11-06-Emotet-and-Trickbot-malware-and-artifacts.zip 716 kB (715,783 bytes)
- 2018-11-06-downloaded-Word-doc-with-macro-for-Emotet.doc (78,592 bytes)
- 2018-11-06-Emotet-malware-binary.exe (143,360 bytes)
- 2018-11-06-Trickbot-malware-binary-retrieved-by-Emotet-gtag-del90.exe (393,728 bytes)
- 2018-11-06-radiance.png-from-192.227.186.151.exe (331,776 bytes)
NOTES:
- Before this past Monday, the group behind sending Emotet malspam was quiet for about 4 weeks.
- Since this past Monday 2018-11-05, we've seen the normal amount of malspam pushing Emotet as before.
- My thanks to people like @BAXD00R, @executemalware, @JRoosen, @pancak3lullz, @ps66uk, @unixronin, @SeraphimDomain, and many others who tweet info about Emotet near-real-time.
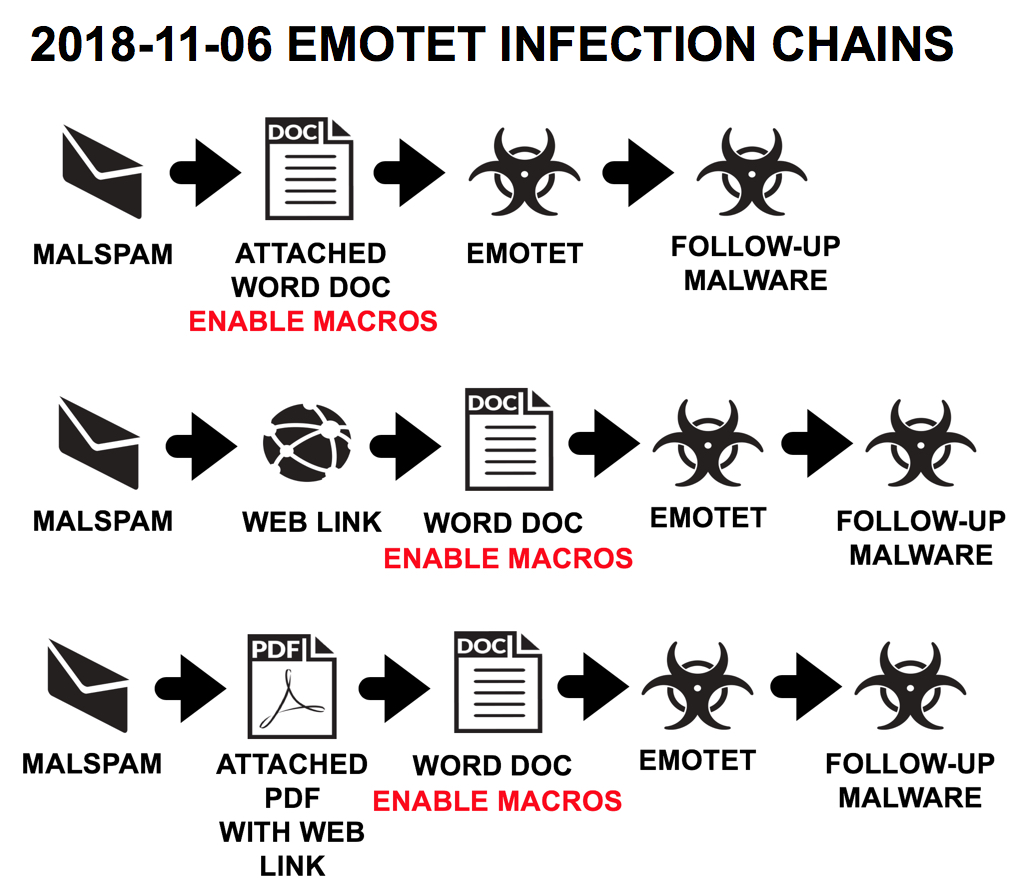
Shown above: Flow chart for recent Emotet malspam.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and partial URL:
- hxxp[:]//1stniag[.]com/Download/EN_en/Invoice-Number-44664/
- hxxp[:]//209.97.182[.]51/EN_US/Details/2018-11/
- hxxp[:]//209.97.186[.]248/En_us/Payments/11_18/
- hxxp[:]//35.167.6[.]44/0455GPLCNXSV/PAY/Commercial/
- hxxp[:]//3kepito[.]hu/En_us/Details/11_18/
- hxxp[:]//777ton[.]ru/DOC/US_us/Scan/
- hxxp[:]//adsdeedee[.]com/1358285S/BIZ/Smallbusiness/
- hxxp[:]//aes[.]co[.]th/web/wp-content/upgrade/newsletter/US/Inv-867015-PO-5O966375/
- hxxp[:]//agrarszakkepzes[.]hu/5931ZTIGS/com/US/
- hxxp[:]//alliance-rnd[.]com/EN_US/Attachments/112018/
- hxxp[:]//altaredlife[.]com/logssite/INFO/US_us/Question/
- hxxp[:]//alumni[.]poltekba[.]ac[.]id/US/Transaction_details/2018-11/
- hxxp[:]//amnisopes[.]com/En_us/Information/112018/
- hxxp[:]//appafoodiz[.]com/En_us/Clients_transactions/2018-11/
- hxxp[:]//artzkaypharmacy[.]com[.]au/4690UVTTQOXO/SWIFT/Commercial/
- hxxp[:]//azatamartik[.]org/US/Information/2018-11/
- hxxp[:]//benchmarkiso[.]com/24IYXQCHNP/biz/US/
- hxxp[:]//bgtest[.]vedel-oesterby[.]dk/3810430RP/PAYROLL/Commercial/
- hxxp[:]//blacktiemining[.]com/0YVX/SWIFT/Commercial/
- hxxp[:]//clabels[.]pt/EN_US/Clients_information/2018-11/
- hxxp[:]//corporaciondelsur[.]com[.]pe/US/Transaction_details/2018-11/
- hxxp[:]//cressy27[.]com/En_us/Documents/2018-11/
- hxxp[:]//dev[.]kevinscott[.]com[.]au/85SRSH/PAY/Personal/
- hxxp[:]//dietmantra[.]org/En_us/Clients_information/11_18/
- hxxp[:]//digirising[.]com/En_us/Transactions-details/11_18/
- hxxp[:]//eventus[.]ie/359PQLQ/biz/Personal/
- hxxp[:]//fantastika[.]in[.]ua/3616974KVTNZUT/PAYMENT/Commercial/
- hxxp[:]//felipeuchoa[.]com[.]br/wp-content/uploads/DOC/US_us/Invoice-receipt/
- hxxp[:]//fert[.]es/EN_US/Clients_information/112018/
- hxxp[:]//fglab[.]com[.]br/LLC/En_us/New-order/
- hxxp[:]//fincabonanzaquindio[.]com/En_us/Transaction_details/11_18/
- hxxp[:]//forzashowband[.]com/EN_US/Clients/2018-11/
- hxxp[:]//graywhalefoundation[.]org/US/Transactions-details/112018/
- hxxp[:]//grille-tech[.]com/hj4M3FfcISLL6fdUo/BIZ/Privatkunden/
- hxxp[:]//hartmannbossen[.]dk/En_us/Attachments/11_18/
- hxxp[:]//hawaiikaigolf[.]com/US/Clients/112018/
- hxxp[:]//hsrventures[.]com/En_us/Clients_transactions/112018/
- hxxp[:]//ichangevn[.]org/EN_US/Transactions/112018/
- hxxp[:]//lemar[.]home[.]pl/manager/En_us/Transactions-details/112018/
- hxxp[:]//lmetallurg[.]ru/831063SSI/identity/Business/
- hxxp[:]//meleyrodri[.]com/xdYdvDnPM24m9e/de/IhreSparkasse/
- hxxp[:]//mohandes724[.]com/En_us/Details/2018-11/
- hxxp[:]//nga[.]no/91985U/biz/Personal/
- hxxp[:]//nikbox[.]ru/24926SQ/identity/Commercial/
- hxxp[:]//okrenviewhotel[.]com/En_us/Details/11_18/
- hxxp[:]//pibuilding[.]com/6547LNPZL/PAYROLL/Commercial/
- hxxp[:]//pirilax[.]su/6ZW/PAYROLL/Commercial/
- hxxp[:]//raeesp[.]com/hUc77ZvQQxq/de/Privatkunden/
- hxxp[:]//riverwalkmb[.]com/US/Attachments/2018-11/
- hxxp[:]//shingari[.]ru/41381RLL/SEP/Personal/
- hxxp[:]//sociallysavvyseo[.]com/US/Payments/11_18/
- hxxp[:]//testingweb[.]in/En_us/Clients_transactions/11_18/
- hxxp[:]//tomas[.]datanom[.]fi/ovning/US/Payments/112018/
- hxxp[:]//toronto[.]rogersupfront[.]com/10613MKDPJF/SEP/Personal/
- hxxp[:]//www.fromjoy[.]fr/EN_US/Clients_transactions/112018
- hxxp[:]//www.reklame[.]ru/7665310VEYLGBNW/biz/Business/
- hxxp[:]//www.transimperial[.]ru/605FW/BIZ/US/
- hxxp[:]//xn----gtbreobjp7byc[.]xn--p1ai/32NNLUEIY/com/Commercial/
- hxxp[:]//ampdist[.]com/AEZf
- hxxp[:]//blog[.]comjagat[.]com/wp-content/mWdx
- hxxp[:]//colombiaagro[.]com[.]co/EZLOpSOF
- hxxp[:]//lipetsk-pivo[.]ru/h
- hxxp[:]//mabnanirou[.]com/oG
- hxxp[:]//micheleverdi[.]com/Fbestfz
- hxxp[:]//www.gerrithamann[.]de/hP2IldM
- hxxp[:]//www.prevencionplus[.]com/BuLyc2HKL
- hxxp[:]//www.sastudio[.]co/AU4fI
- hxxp[:]//www.upex[.]ee/vqUuJ3B7
- hxxp[:]//192.227.186[.]151/radiance.png
- hxxp[:]//192.227.186[.]151/table.png
- hxxp[:]//192.227.186[.]151/worming.png
- hxxp[:]//47.32.109[.]184/del90/
EMAILS

Shown above: Example of an email from Emotet malspam with a PDF attachment.
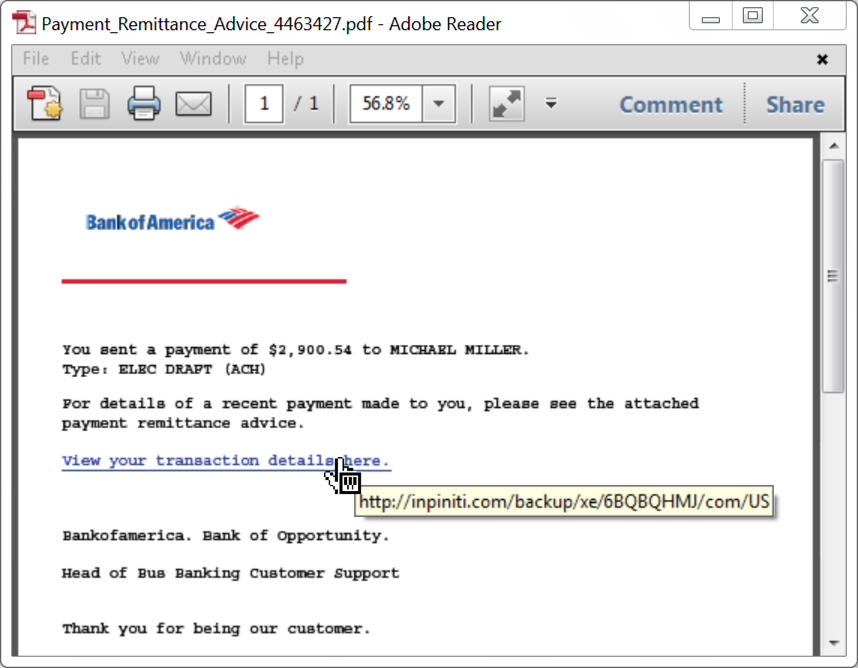
Shown above: Link in the PDF attachment to download the initial Word doc.
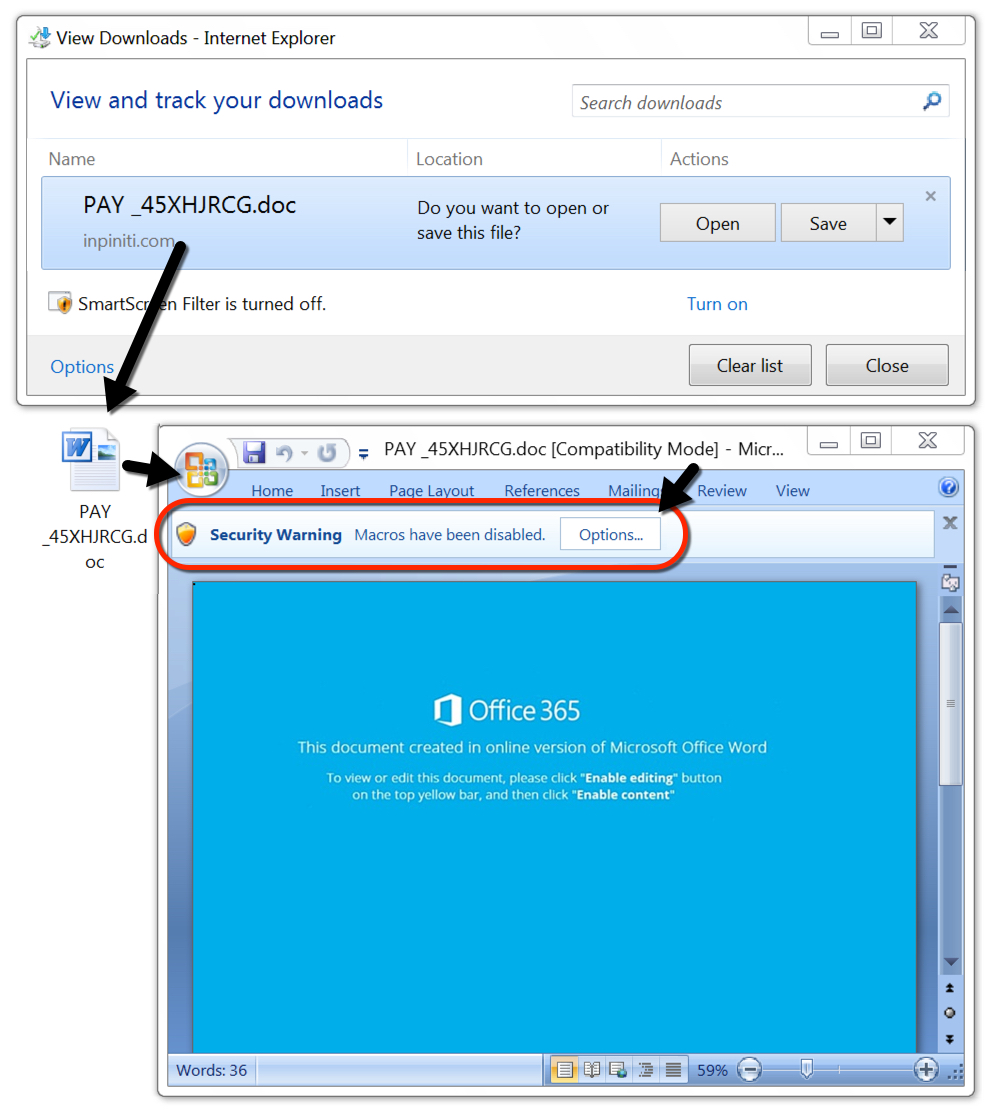
Shown above: Downloading the initial Word document and enabling macros to infect a victim's host.
TRAFFIC
URLS TO DOWNLOAD THE INITIAL WORD DOCUMENT (FROM PDF FILES OR LINKS IN THE EMAILS):
NOTE: Items marked with ** means these URLs did not deliver the malware when I checked earlier (probably taken off-line).
- hxxp[:]//1stniag[.]com/Download/EN_en/Invoice-Number-44664/
- hxxp[:]//209[.]97[.]182[.]51/EN_US/Details/2018-11/
- hxxp[:]//209[.]97[.]186[.]248/En_us/Payments/11_18/
- hxxp[:]//35[.]167[.]6[.]44/0455GPLCNXSV/PAY/Commercial/
- hxxp[:]//3kepito[.]hu/En_us/Details/11_18/
- hxxp[:]//777ton[.]ru/DOC/US_us/Scan/
- hxxp[:]//adsdeedee[.]com/1358285S/BIZ/Smallbusiness/
- hxxp[:]//aes[.]co[.]th/web/wp-content/upgrade/newsletter/US/Inv-867015-PO-5O966375/
- hxxp[:]//agrarszakkepzes[.]hu/5931ZTIGS/com/US/
- hxxp[:]//alliance-rnd[.]com/EN_US/Attachments/112018/
- hxxp[:]//altaredlife[.]com/logssite/INFO/US_us/Question/
- hxxp[:]//altarfx[.]com/Nov2018/En/Invoice-for-p/e-11/05/2018/ **
- hxxp[:]//alumni[.]poltekba[.]ac[.]id/US/Transaction_details/2018-11/
- hxxp[:]//amnisopes[.]com/En_us/Information/112018/
- hxxp[:]//appafoodiz[.]com/En_us/Clients_transactions/2018-11/
- hxxp[:]//artzkaypharmacy[.]com[.]au/4690UVTTQOXO/SWIFT/Commercial/
- hxxp[:]//azatamartik[.]org/US/Information/2018-11/
- hxxp[:]//benchmarkiso[.]com/24IYXQCHNP/biz/US/
- hxxp[:]//bgtest[.]vedel-oesterby[.]dk/3810430RP/PAYROLL/Commercial/
- hxxp[:]//blacktiemining[.]com/0YVX/SWIFT/Commercial/
- hxxp[:]//clabels[.]pt/EN_US/Clients_information/2018-11/
- hxxp[:]//corporaciondelsur[.]com[.]pe/US/Transaction_details/2018-11/
- hxxp[:]//cressy27[.]com/En_us/Documents/2018-11/
- hxxp[:]//dmas[.]es/US/Details/11_18/ **
- hxxp[:]//dev[.]kevinscott[.]com[.]au/85SRSH/PAY/Personal/
- hxxp[:]//dietmantra[.]org/En_us/Clients_information/11_18/
- hxxp[:]//digirising[.]com/En_us/Transactions-details/11_18/
- hxxp[:]//eventus[.]ie/359PQLQ/biz/Personal/
- hxxp[:]//fantastika[.]in[.]ua/3616974KVTNZUT/PAYMENT/Commercial/
- hxxp[:]//felipeuchoa[.]com[.]br/wp-content/uploads/DOC/US_us/Invoice-receipt/
- hxxp[:]//fert[.]es/EN_US/Clients_information/112018/
- hxxp[:]//fglab[.]com[.]br/LLC/En_us/New-order/
- hxxp[:]//fincabonanzaquindio[.]com/En_us/Transaction_details/11_18/
- hxxp[:]//forzashowband[.]com/EN_US/Clients/2018-11/
- hxxp[:]//gilmarnazareno[.]com[.]br/BhWwli/BIZ/Service-Center/ **
- hxxp[:]//graywhalefoundation[.]org/US/Transactions-details/112018/
- hxxp[:]//grille-tech[.]com/hj4M3FfcISLL6fdUo/BIZ/Privatkunden/
- hxxp[:]//guselceva[.]ru/39808GPKVXO/identity/Personal/ **
- hxxp[:]//hartmannbossen[.]dk/En_us/Attachments/11_18/
- hxxp[:]//hawaiikaigolf[.]com/US/Clients/112018/
- hxxp[:]//homebakerz[.]com[.]au/hG5sm76mEjQMCzGLn/SWIFT/PrivateBanking/ **
- hxxp[:]//hsrventures[.]com/En_us/Clients_transactions/112018/
- hxxp[:]//i4c[.]com[.]br/US/Transactions/2018-11/ **
- hxxp[:]//ichangevn[.]org/EN_US/Transactions/112018/
- hxxp[:]//jurist29[.]ru/2J/SWIFT/Commercial/ **
- hxxp[:]//legal-world[.]su/qmB9mXRB/de_DE/200-Jahre/ **
- hxxp[:]//lemar[.]home[.]pl/manager/En_us/Transactions-details/112018/
- hxxp[:]//lmetallurg[.]ru/831063SSI/identity/Business/
- hxxp[:]//meleyrodri[.]com/xdYdvDnPM24m9e/de/IhreSparkasse/
- hxxp[:]//mohandes724[.]com/En_us/Details/2018-11/
- hxxp[:]//nga[.]no/91985U/biz/Personal/
- hxxp[:]//nikbox[.]ru/24926SQ/identity/Commercial/
- hxxp[:]//okrenviewhotel[.]com/En_us/Details/11_18/
- hxxp[:]//pibuilding[.]com/6547LNPZL/PAYROLL/Commercial/
- hxxp[:]//pirilax[.]su/6ZW/PAYROLL/Commercial/
- hxxp[:]//raeesp[.]com/hUc77ZvQQxq/de/Privatkunden/
- hxxp[:]//riverwalkmb[.]com/US/Attachments/2018-11/
- hxxp[:]//shingari[.]ru/41381RLL/SEP/Personal/
- hxxp[:]//sociallysavvyseo[.]com/US/Payments/11_18/
- hxxp[:]//testingweb[.]in/En_us/Clients_transactions/11_18/
- hxxp[:]//tomas[.]datanom[.]fi/ovning/US/Payments/112018/
- hxxp[:]//toronto[.]rogersupfront[.]com/10613MKDPJF/SEP/Personal/
- hxxp[:]//www.24complex[.]ru/2AYX/com/Commercial/ **
- hxxp[:]//www.dermainstant[.]com/dkH4TT2/BIZ/PrivateBanking/ **
- hxxp[:]//www.dtoneycpa[.]com/En_us/Clients/2018-11/ **
- hxxp[:]//www.fromjoy[.]fr/EN_US/Clients_transactions/112018
- hxxp[:]//www.planosdesaudebrasilia[.]net[.]br/EN_US/Documents/112018/ **
- hxxp[:]//www.reklame[.]ru/7665310VEYLGBNW/biz/Business/
- hxxp[:]//www.transimperial[.]ru/605FW/BIZ/US/
- hxxp[:]//xn-----8kcbcubc0cfh6a2am9f7cg[.]xn--p1ai/815734WLPDJ/biz/Personal/ **
- hxxp[:]//xn----gtbreobjp7byc[.]xn--p1ai/32NNLUEIY/com/Commercial/
- hxxp[:]//xn--80aaxk0bn[.]xn--p1ai/36OEKNKS/ACH/Business/ **
- hxxp[:]//xn--80agpqajcme4aij[.]xn--p1ai/51TFMV/ACH/Smallbusiness/ **
- hxxp[:]//yasinau[.]ru/0KMBMkQMMptet4/de/Privatkunden/ **
- hxxp[:]//zalco[.]nl/76BWXKGCT/PAY/Business/ **
URLS GENERATED BY MACROS IN THE INITIAL WORD DOC TO DOWNLOAD THE EMOTET BINARY:
- hxxp[:]//1412studiodm[.]com/xGDA0q **
- hxxp[:]//aldo[.]jplms[.]com[.]au/eWykVvYj **
- hxxp[:]//ampdist[.]com/AEZf
- hxxp[:]//blog[.]comjagat[.]com/wp-content/mWdx
- hxxp[:]//colombiaagro[.]com[.]co/EZLOpSOF
- hxxp[:]//lipetsk-pivo[.]ru/h
- hxxp[:]//mabnanirou[.]com/oG
- hxxp[:]//micheleverdi[.]com/Fbestfz
- hxxp[:]//staging[.]bridgecode[.]co[.]uk/wQr0hzU **
- hxxp[:]//www.gerrithamann[.]de/hP2IldM
- hxxp[:]//www.prevencionplus[.]com/BuLyc2HKL
- hxxp[:]//www.sastudio[.]co/AU4fI
- hxxp[:]//www.seosyd[.]com/IyThn3I **
- hxxp[:]//www.sicfms[.]com/sybnoK9 **
- hxxp[:]//www.upex[.]ee/vqUuJ3B7
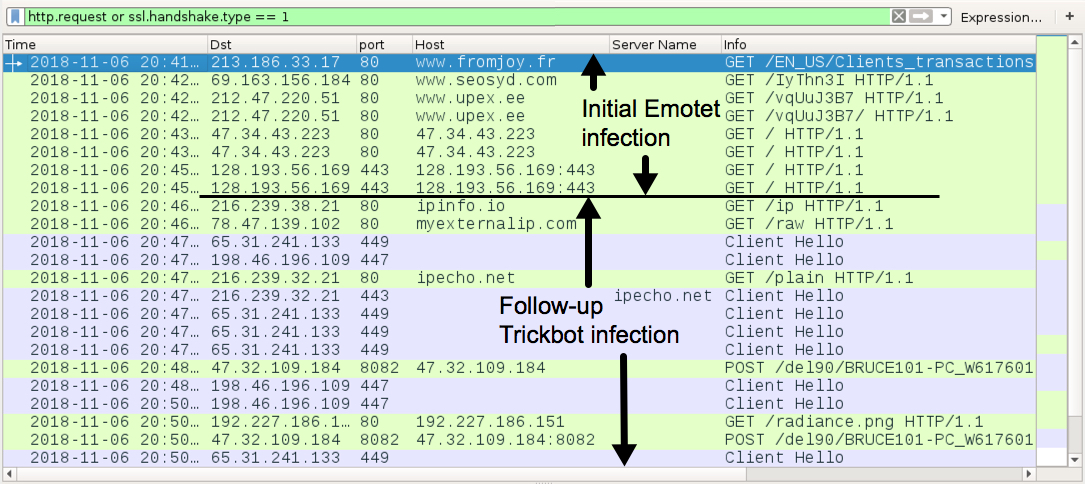
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST IN THE US:
- 213.186.33[.]17 port 80 - www.fromjoy[.]fr - GET /EN_US/Clients_transactions/112018/
- 69.163.156[.]184 port 80 - www.seosyd[.]com - GET /IyThn3I
- 212.47.220[.]51 port 80 - www.upex[.]ee - GET /vqUuJ3B7
- 212.47.220[.]51 port 80 - www.upex[.]ee - GET /vqUuJ3B7/
- 47.34.43[.]223 port 80 - 47.34.43[.]223 - GET /
- 47.225.131[.]10 port 80 - TCP connection attempts, but no response from server
- 128.193.56[.]169 port 443 - 128.193.56[.]169:443 - GET /
- port 80 - ipinfo[.]io - GET /ip (IP address check by infected host)
- port 80 - myexternalip[.]com - GET /raw (IP address check by infected host)
- 184.169.105[.]210 port 449 - TCP connection attempts, but no response from server
- 65.31.241[.]133 port 449 - HTTPS/SSL/TLS traffic caused by Trickbot
- 198.46.196[.]109 port 447 - HTTPS/SSL/TLS traffic caused by Trickbot
- port 80 - ipecho[.]net - GET /plain (IP address check by infected host)
- port 443 - ipecho[.]net - HTTPS traffic (IP address check by infected host)
- 47.32.109[.]184 port 8082 - 47.32.109[.]184 - POST /del90/[long string of characters]
- 192.227.186[.]151 port 80 - 192.227.186[.]151 - GET /radiance.png
MALWARE
MALWARE FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: fc048b04dc8a13fba792e2caa5b50f5fe95c5d78855c74cbc5c93fdf0d398853
- File size: 78,592 bytes
- File location: hxxp[:]//www.fromjoy[.]fr/EN_US/Clients_transactions/112018/
- File name: FORM-9459438630448044.doc (various names)
- File description: Downloaded Word document with macro for Emotet
- SHA256 hash: 87d0b764f2670d2373470d8becad7f26301e206f00b5f35391ab4a38e94ec524
- File size: 143,360 bytes
- File location: hxxp[:]//www.upx[.]ee/vqUuJ3B7/
- File location: C:\Users\[username]\AppData\Local\Windows\[random file name].exe
- File description: Emotet malware binary
- SHA256 hash: ea79f26437f3d0eb8a5185bcf1190ea0918c5263a2ca1336c0915fded8d4b7ad
- File size: 393,728 bytes
- File location: C:\Users\[username]\AppData\Roaming\WINYS\[random file name].exe
- File description: Trickbot malware binary retrieved by Emotet-infected Windows host (gtag: del90)
- SHA256 hash: e0eb41ccb2f33576f65ece6072b8f07af7b93ab847f3858d1b75468ed41fd2da
- File size: 331,776 bytes
- File location: hxxp[:]//192.227.186[.]151/radiance.png
- File description: Follow-up Trickbot malware binary retrieved to infect other Windows hosts
Click here to return to the main page.
