2018-11-16 - EMOTET NOW USING XML FILES AS WORD DOCS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
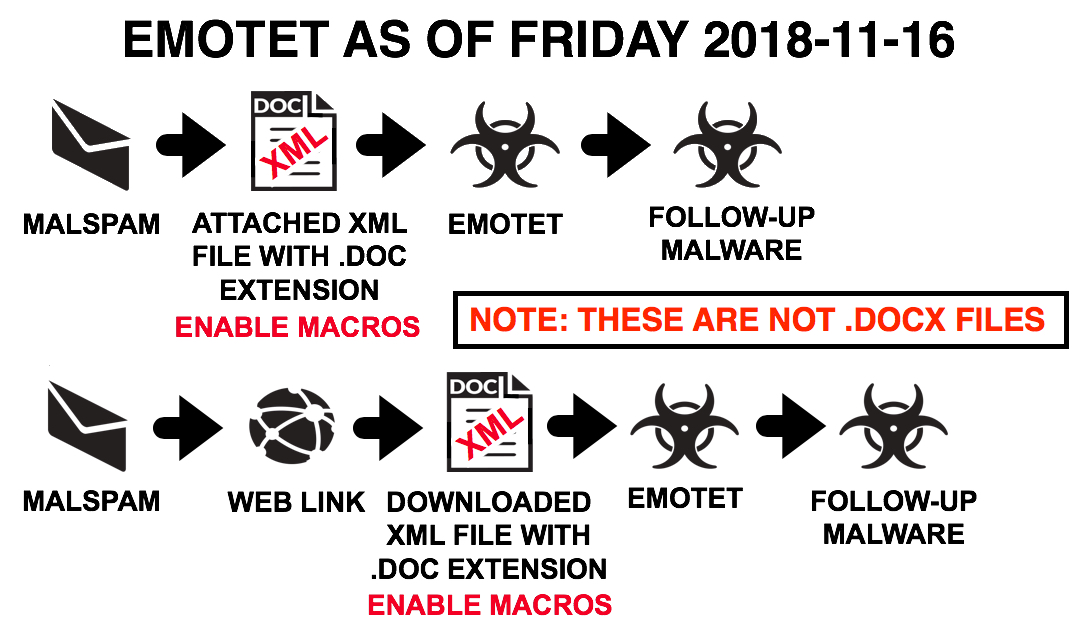
Shown above: The new Emotet infection chain.
NOTES:
- As of Friday 2018-11-16, email attachments with (and URL downloads for) Emotet docs are now XML-based.
- These new Emotet docs don't match Microsoft's XML-based DOCX format for Word docs.
- These new Emotet docs are tagged xml in VirusTotal.
- Using the "file" command in Linux shows them as: XML 1.0 document text, UTF-8 Unicode text, with very long lines, with CRLF line terminators
- These new Emotet XML docs still use a .doc extension, they open in Microsoft Word, and they look and act the same as before.
- Thanks to people like @pollo290987, @JRoosen, @Ledtech3, and others who discussed this on Twitter. (example thread)
EXAMPLES OF NEW EMOTET XML ATTACHMENTS:
- 2018-11-16 malspam: 2018-11-16-malspam-with-new-Emotet-XML-docs-8-examples.zip 644 kB (643,582 bytes)
- 2018-11-16 attachments: 2018-11-16-new-Emotet-XML-docs-8-examples.zip 445 kB (444,757 bytes)
EMOTET INFECTION TRAFFIC AND MALWARE:
- 2018-11-16 traffic: 2018-11-16-Emotet-infection-with-IcedID-and-AZORult.pcap.zip 6.3 MB (6,348,310 bytes)
- 2018-11-16-Emotet-infection-with-IcedID-and-AZORult.pcap (9,916,890 bytes)
- 2018-11-16 malware and artifacts: 2018-11-16-Emotet-and-IcedID-malware.zip 754 kB (753,523 bytes)
- 2018-11-16-Emotet-malware-binary.exe (1,212,416 bytes)
- 2018-11-16-IcedID-persistent-on-infected-Windows-host.exe (376,832 bytes)
- 2018-11-16-IcedID-retrieved-by-Emotet-infected-host.exe (376,832 bytes)
MALWARE
SHA256 HASHES FOR 8 EXAMPLES OF THE ATTACHED XML DOCUMENTS:
- 7ccfb6433cc7b3173250028d08719efd1cbe5e556cc284f73a4f88c7aae4b008 - 140,541 bytes - INV299.doc
- 0190578680e963ac41ca3e4cbb2632ec296a5c41437a0219f2cc7ce7508cb4f6 - 135,677 bytes - INV903491.doc
- 67296941ea18e73e60ea2e56e9dcd8472c993bfcd023a0598d3c8cfb3c3e046d - 144,253 bytes - Untitled-EUG-M51083.doc
- 27576e6f18fb9c9663eb357842e88aa3b74ef31fe5180adad88d3b5bd7c6dc38 - 143,485 bytes - Untitled-EXO-T0409395.doc
- 37e4a6a266f2c2605e8b5c8923512fde8518b3a36fadac8128c15dcf1aa4dd6d - 145,021 bytes - Untitled-HSN-W999901.doc
- b2da18b67f24e82ac7ba4275d1250067c0a383794765478872fc7c88181a4669 - 145,533 bytes - Untitled-HWN-H39546.doc
- e9d2eb9b6e20426564d038ef0890e4c34caf394b59ed8fef0c295778d4d5aa13 - 145,277 bytes - Untitled-LVT-63613687.doc
- 6f583e147d0b35f68113fdc69cec2b19ecf1cb07ef94752a692294758f0d3ac9 - 135,549 bytes - Untitled-LXP-S6981571.doc
SHA256 HASHES FOR THE 2018-11-16 INFECTION (WHERE I DOWNLOADED AN EMOTET EXE DIRECTLY):
- 0da56126ffb57acb5bb1a3ffa1c4c0c2605d257988b2d2964344b8f23173f615 - 1,212,416 bytes - Emotet malware binary
- d68673c8c4393dd3a7a4d40a065d8305b52ac8948863ddd8e7cfd417ee0df6fe - 376,832 bytes - IcedID retrieved by Emotet
- 4d97e3665772d4d41f7e7c0b6a7cea0c36017f444dbfb47f91de75f050412fce - 376,832 bytes - IcedID made persistent
IMAGES
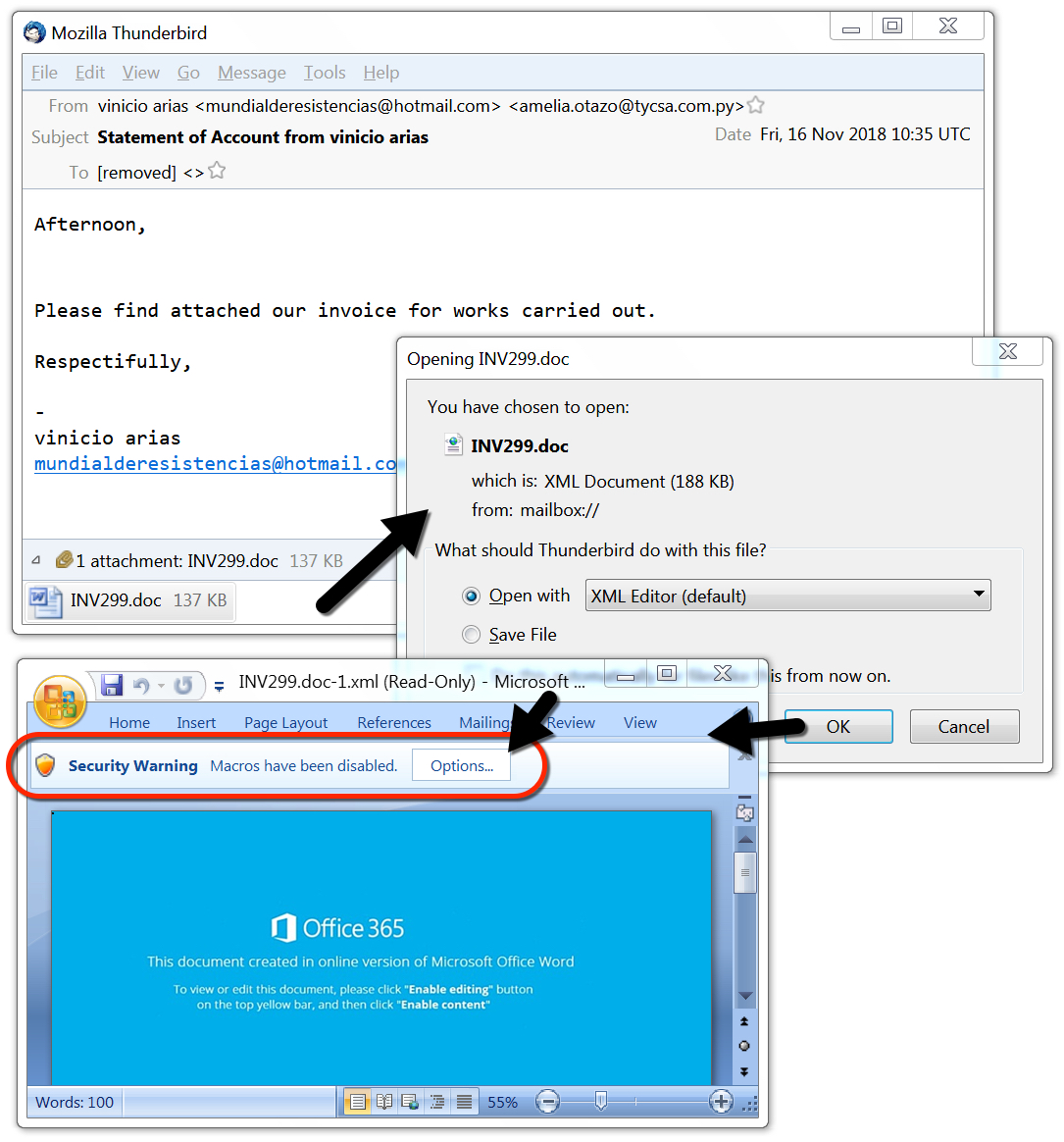
Shown above: The new Emotet XML docs still work the same way with a macro.
Click here to return to the main page.
