2018-11-23 - QUICK POST: EMOTET INFECTION WITH GOOTKIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-11-23-Emotet-infection-with-Gootkit.pcap.zip 6.1 MB (6,050,723 bytes)
- 2018-11-23-Emotet-infection-with-Gootkit.pcap (6,681,966 bytes)
- 2018-11-23-Emotet-with-Gootkit-malware-and-artifacts.zip 387 kB (387,161 bytes)
- 2018-11-23-downloaded-Word-doc-with-macro-for-Emotet.doc (97,024 bytes)
- 2018-11-23-Emotet-malware-binary.exe (135,168 bytes)
- 2018-11-23-Gootkit-retrieved-by-Emotet-infected-host.exe (2,283,008 bytes)
- 2018-11-23-Gootkit.inf.txt (224 bytes)
NOTES:
- @xorsthingsv2, @James_inthe_box, @avman1995, and @nazywam identified the follow-up malware during this Twitter discussion after I caught a sample yesterday.
- I'm seeing a lot of new Word docs, but no new XML docs recently used by Emotet.
- I stopped seeing those XML docs as of Wednesday 2018-11-21, so the timeframe I saw the XML docs was from Friday 2018-11-16 through Tuesday 2018-11-20.
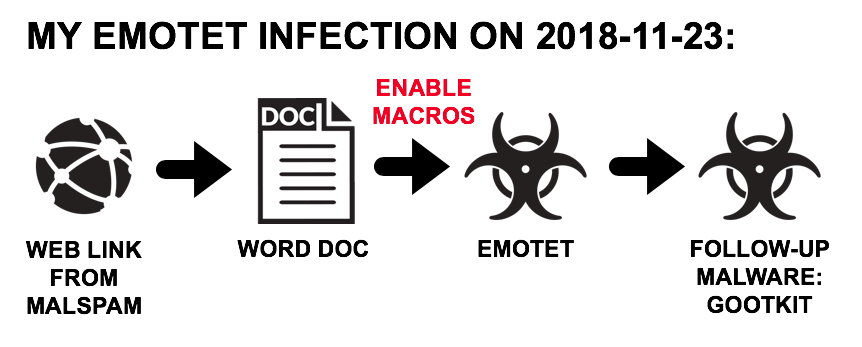
Shown above: Flow chart for recent Ursnif malspam infections I've seen.
IMAGES
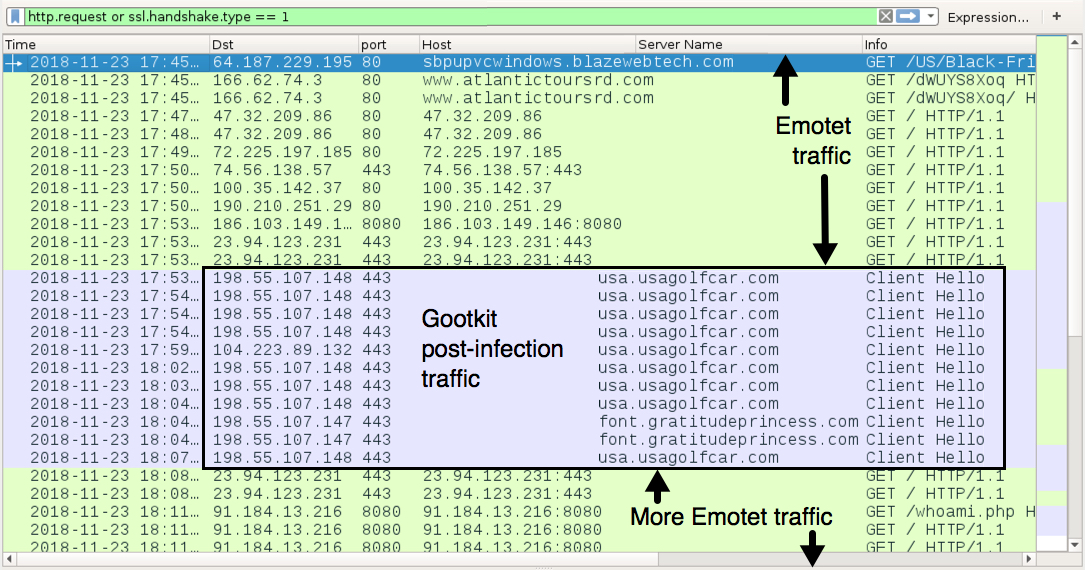
Shown above: Traffic from today's infection filtered in Wireshark.
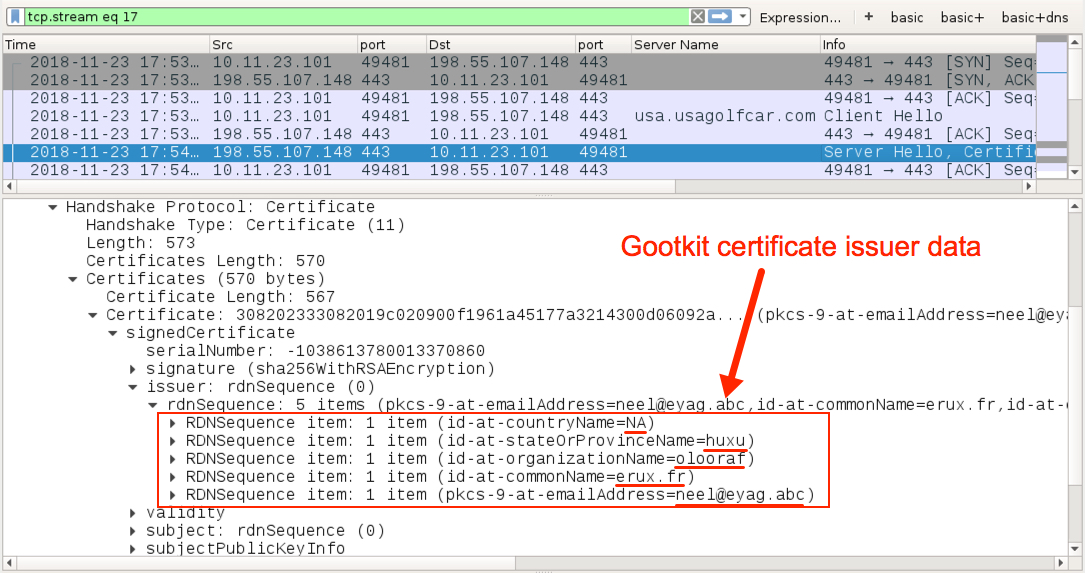
Shown above: Certificate data from the Gootkit post-infection traffic.
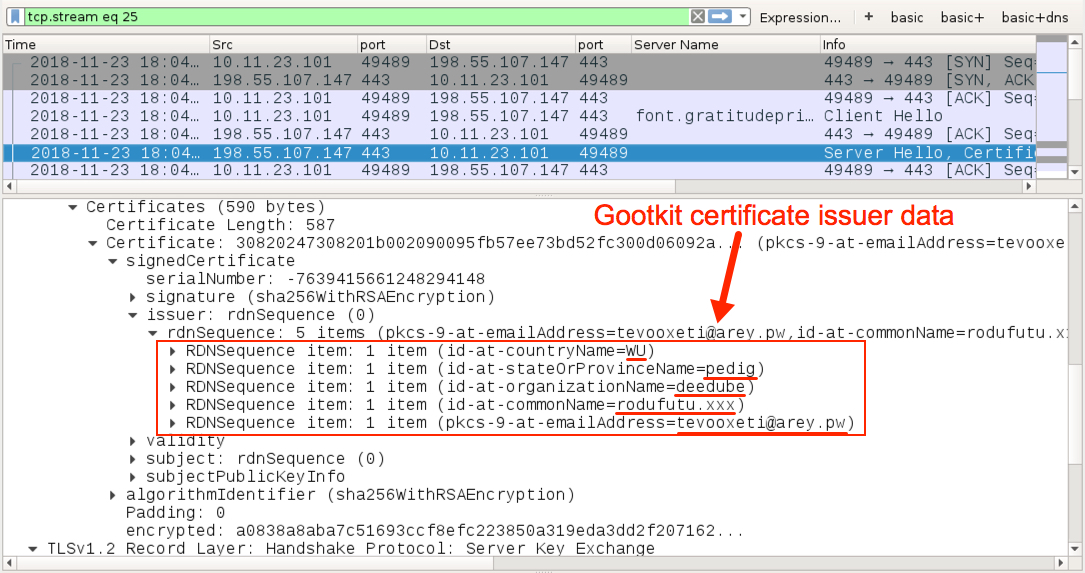
Shown above: More certificate data from the Gootkit post-infection traffic.
Click here to return to the main page.
