2018-11-26 - INFECTION FROM MALSPAM PUSHING LOKIBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the email: 2018-11-26-Lokibot-malspam-0654-UTC.eml.zip 347 kB (347,348 bytes)
- 2018-11-26-Lokibot-malspam-0654-UTC.eml (458,848 bytes)
- Zip archive of the infection traffic: 2018-11-26-Lokibot-infection-traffic.pcap.zip 4 kB (4,239 bytes)
- 2018-11-26-Lokibot-infection-traffic.pcap (8,218 bytes)
- Zip archive of the malware: 2018-11-26-malware-from-Lokibot-infection.zip 675 kB (675,086 bytes)
- 2018-11-26-Lokibot-extracted-from-attached-archive.exe (1,111,864 bytes)
- 2018-11-26-archive-file-attached-to-malspam.zip (336,998 bytes)
NOTES:
- I've seen "Lokibot" also spelled as "Loki-bot".
- Even though I can find Lokibot every day, it's still the same type of infection without any surprises, which is why I don't often blog about it.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest anything to the following domain:
- zereocompany[.]com
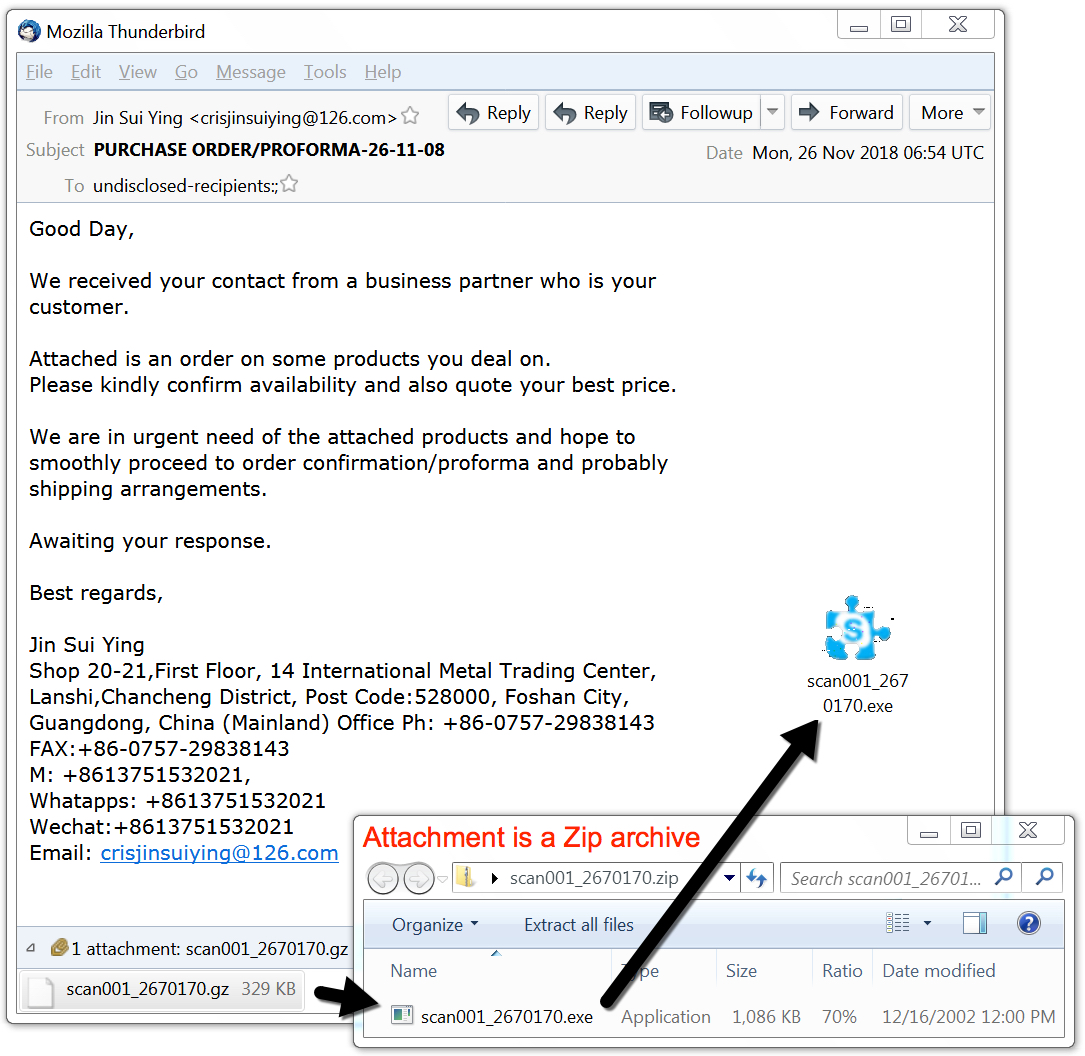
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Monday, 2018-11-26 at 06:54 UTC
- Subject: PURCHASE ORDER/PROFORMA-26-11-08
- From: Jin Sui Ying <crisjinsuiying@126[.]com>
- Received: from ngay25-10.com (csikx006233-EU-FR-IKDC2-Z5-BASIC.ikexpress[.]com [109.238.6[.]233])
- Message-ID: <f2809fdf536a980417e17cedd781bfbc@alfred[.]com>
- Attachment name: scan001_2670170.gz (actually a zip archive)
TRAFFIC
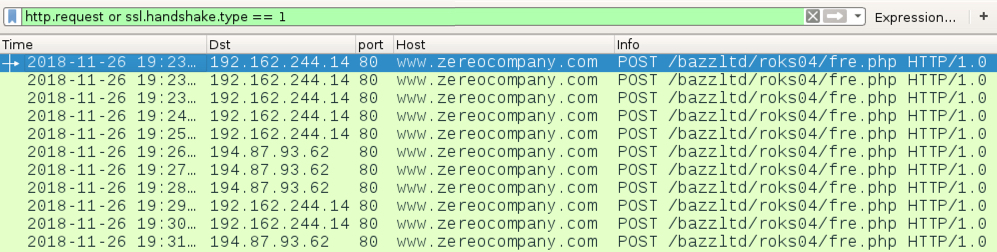
Shown above: Traffic from the infection filtered in Wireshark.
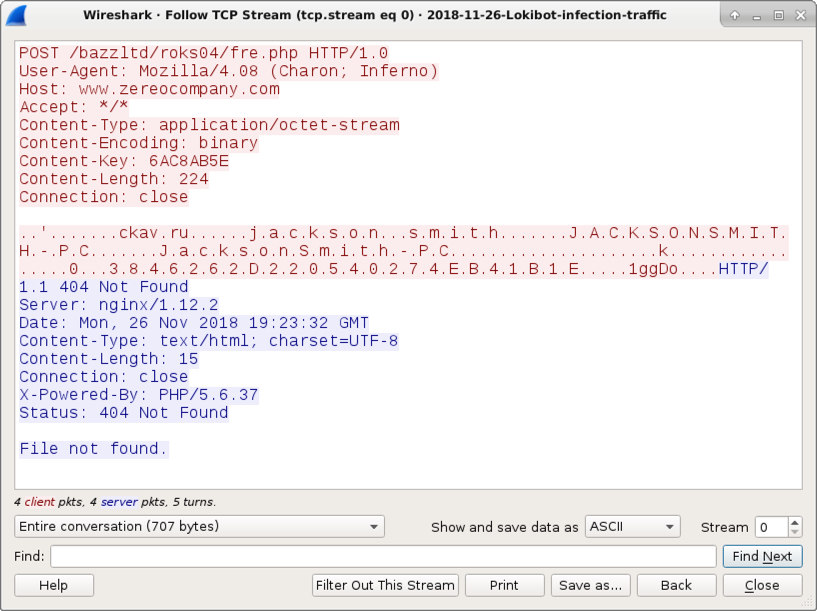
Shown above: Following the TCP stream from an HTTP request in the post-infection traffic.
INFECTION TRAFFIC:
- 192.162.244[.]14 port 80 - www.zereocompany[.]com - POST /bazzltd/roks04/fre.php HTTP/1.0
- 194.87.93[.]62 port 80 - www.zereocompany[.]com - POST /bazzltd/roks04/fre.php HTTP/1.0
MALWARE
EMAIL ATTACHMENT (ZIP ARCHIVE):
- SHA256 hash: 6fe65cd4c70581a08fd4c027ce6e670125ebe8f5544e91f417389988b8ab5547
File size: 336,998 bytes
File name: scan001_2670170.gz
EXTRACTED LOKIBOT MALWARE:
- SHA256 hash: 74f24d80ca15fd2123604c562e60908de928cd2742ba2783aeba4dae91faefb6
File size: 1,111,864 bytes
File name: scan001_2670170.exe
File location after infection: C:\Users\[username]\AppData\Roaming\D22054\40274E.exe
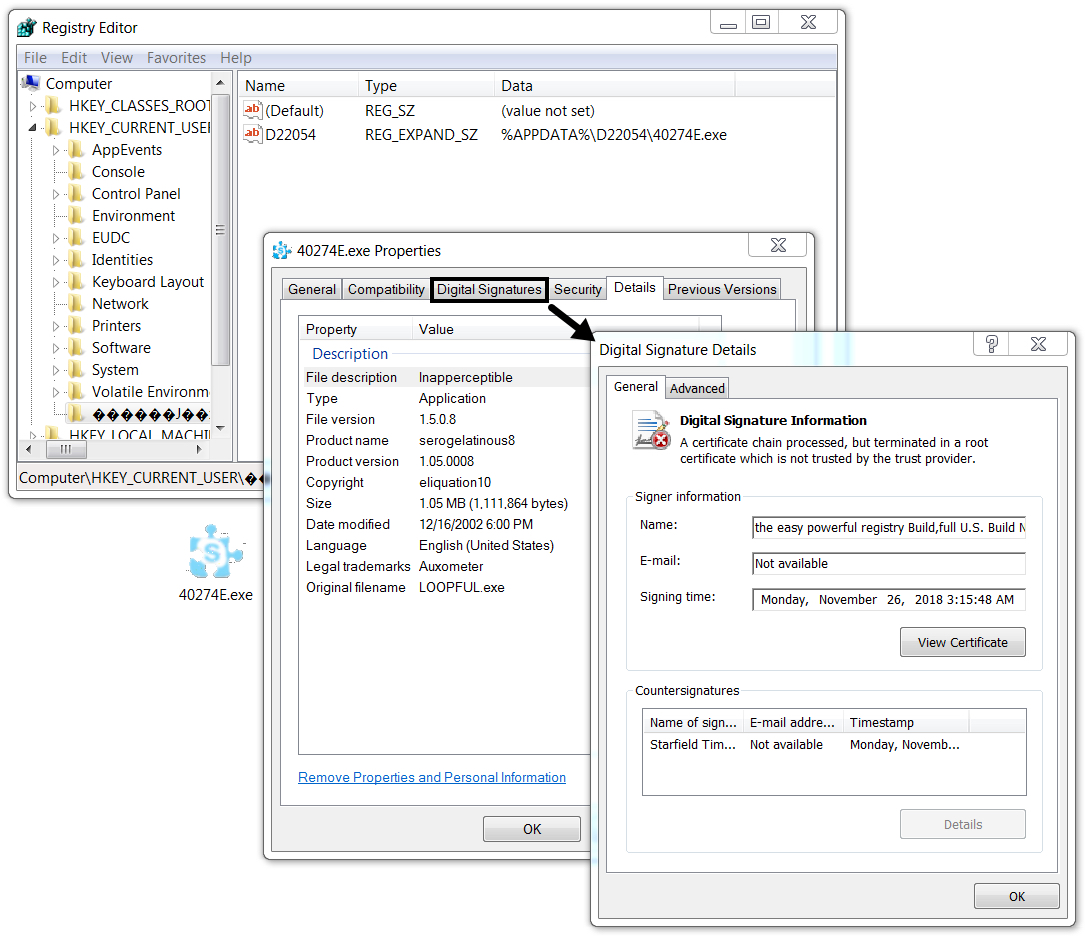
Shown above: Windows registry update to keep the Lokibot infection persistent.
Click here to return to the main page.
