2018-11-27 - URSNIF INFECTION WITH DRIDEX
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-11-27-Ursnif-infection-traffic-with-Dridex.pcap.zip 1.0 MB (1,006,970 bytes)
- 2018-11-27-Ursnif-infection-traffic-with-Dridex.pcap (1,211,674 bytes)
- 2018-11-27-malware-and-artifacts-from-Urnsif-infection.zip 2.5 MB (2,498,043 bytes)
- 2018-11-27-attached-Word-doc-with-macro-for-Ursnif.doc (89,088 bytes)
- 2018-11-27-Dridex-retrieved-by-Windows-host-infected-with-Ursnif.exe (253,952 bytes)
- 2018-11-27-Ursnif-malware-binary.exe (261,120 bytes)
- 2018-11-27-Windows-registry-entries-created-by-Ursnif-infection.txt (10,420,558 bytes)
Shown above: Flow chart for recent Ursnif malspam infections I've seen.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URL:
- klychenogg[.]com
- cochrimato[.]com
- mautergase[.]com
- hxxp[:]//95.181.198[.]231/oiioiashdqbwe.rar
TRAFFIC
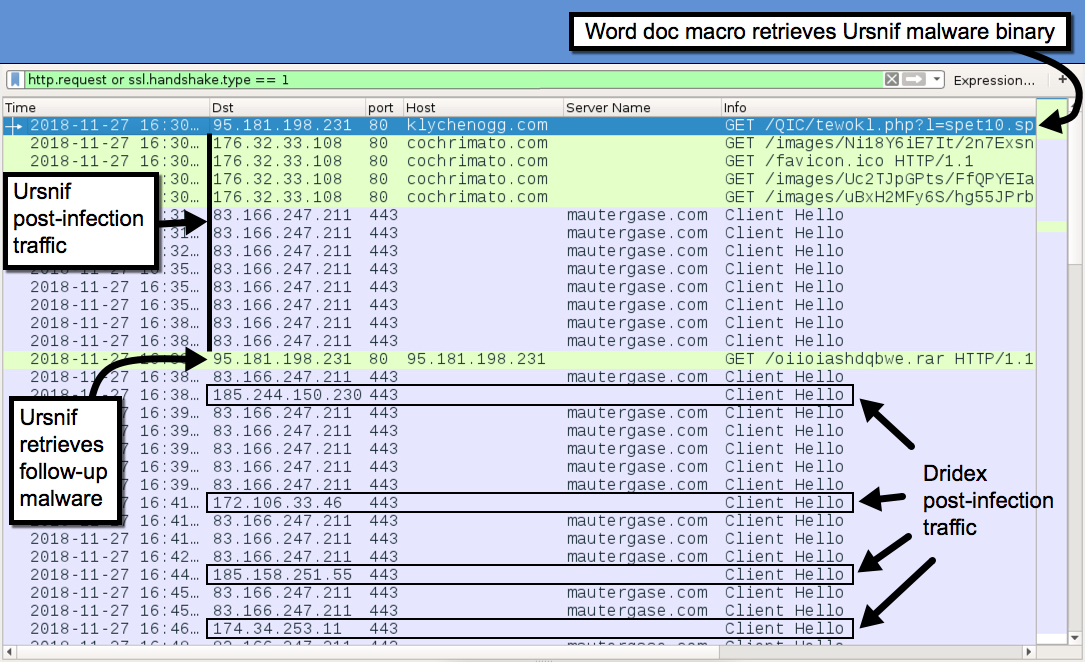
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 95.181.198[.]231 port 80 - klychenogg[.]com - GET /QIC/tewokl.php?l=spet10.spr Word macro retrieves Ursnif binary)
- 176.32.33[.]108 port 80 - cochrimato[.]com - GET /images/[long string].avi (caused by Ursnif)
- 83.166.247[.]211 port 443 - mautergase[.]com - HTTPS/SSL/TLS traffic caused by Ursnif
- 95.181.198[.]231 port 80 - 95.181.198[.]231 - GET /oiioiashdqbwe.rar (infected host retrieves Dridex)
- 185.244.150[.]230 port 443 - SSL/TLS traffic caused by Dridex
- 172.106.33[.]46 port 443 - SSL/TLS traffic caused by Dridex
- 185.158.251[.]55 port 443 - SSL/TLS traffic caused by Dridex
- 174.34.253[.]11 port 443 - SSL/TLS traffic caused by Dridex
MALWARE
MALWARE FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: dc0454a6162652abd6423b7ea2c22b1a692a867eec760f8db543cd9ffda95d5c
- File size: 89,088 bytes
- File description: malspam attachment - Word doc with macro for Ursnif
- SHA256 hash: aaa41c27d5b4a160ed2a00ba820dd6ada86ed80e76d476a8379543478e608f84
- File size: 261,120 bytes
- File location: hxxp[:]//klychenogg[.]com/QIC/tewokl.php?l=spet10.spr
- File location: C:\Users\[username]\AppData\Local\Temp\iwr.exe
- File description: Ursnif malware binary
- SHA256 hash: 07c05fa06cac8a5e585bd06c45b8738f8d0456efa319ffeb4e663a7e15f38139
- File size: 253,952 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\586688.exe
- File description: Dridex malware binary retrieved by Ursnif-infected Windows host
Click here to return to the main page.
