2018-12-07 - QUICK POST: EMOTET WITH ICEDID (BOKBOT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-12-07-Emotet-malspam-with-link-to-doc-1550-UTC.eml.zip 1.8 kB (1,777 bytes)
- 2018-12-07-Emotet-malspam-with-link-to-doc-1550-UTC.eml (2,565 bytes)
- 2018-12-07-Emotet-infection-with-IcedID.pcap.zip 1.9 MB (1,897,968 bytes)
- 2018-12-07-Emotet-infection-with-IcedID.pcap (2,100,997 bytes)
- 2018-12-07-Emotet-and-IcedID-malware.zip 445.6 kB (445,573 bytes)
- 2018-12-07-downloaded-Word-doc-with-macro-for-Emotet.doc (138,496 bytes)
- 2018-12-07-Emotet-malware-binary.exe (139,264 bytes)
- 2018-12-07-IcedID-made-persistent-on-infected-host.exe (184,320 bytes)
- 2018-12-07-IcedID-retrieved-by-Emotet-infected-host.exe (18,4320 bytes)
IMAGES:
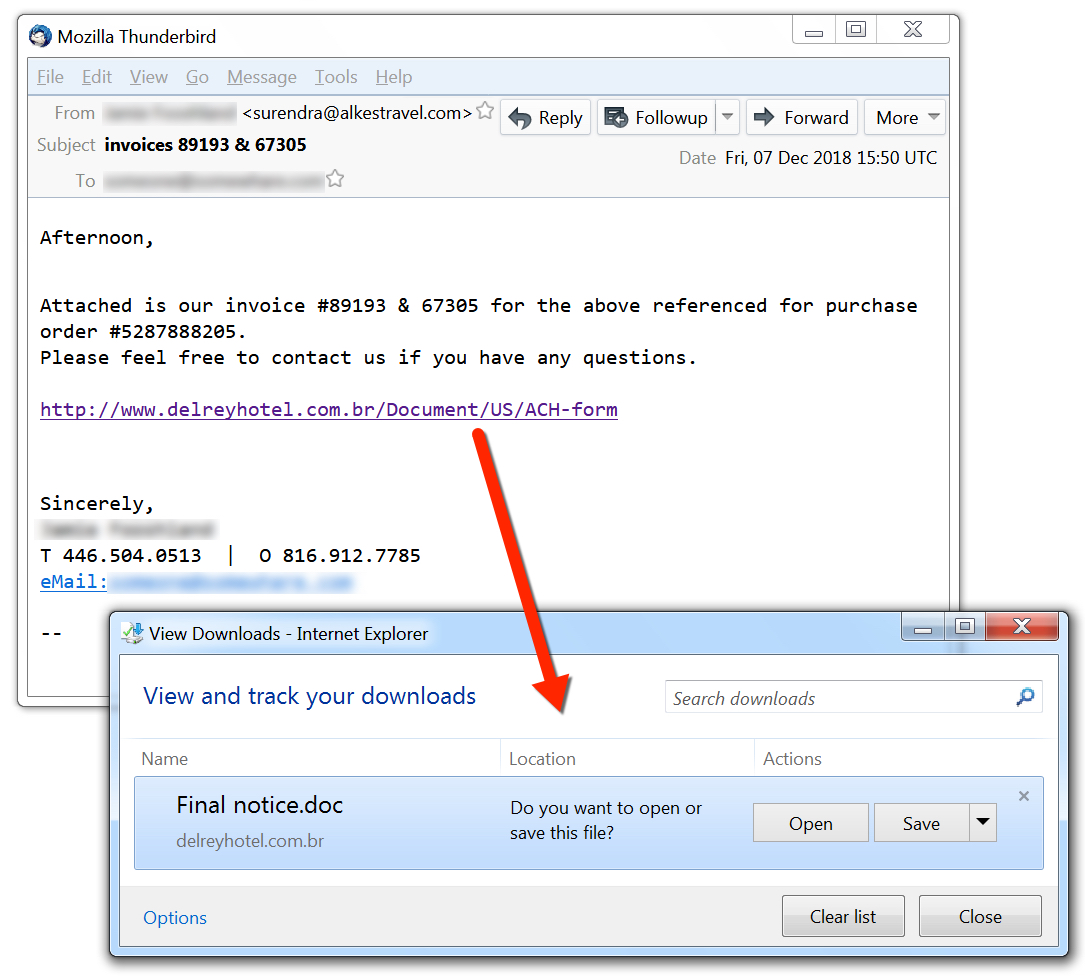
Shown above: Screenshot of the malspam with a link to the Word doc.
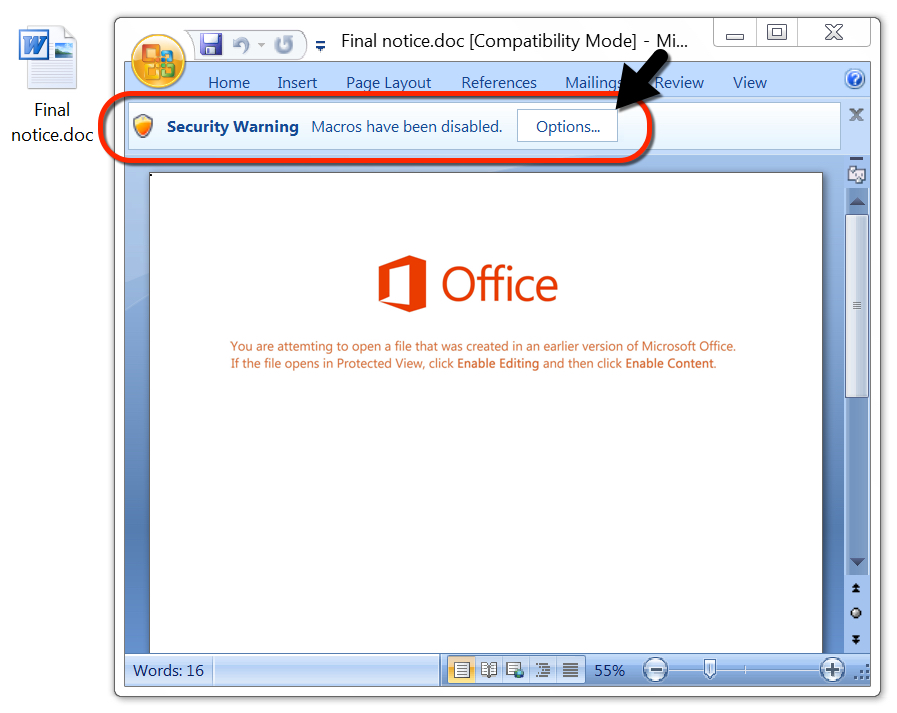
Shown above: The downloaded Word doc with malicious macro to install Emotet.
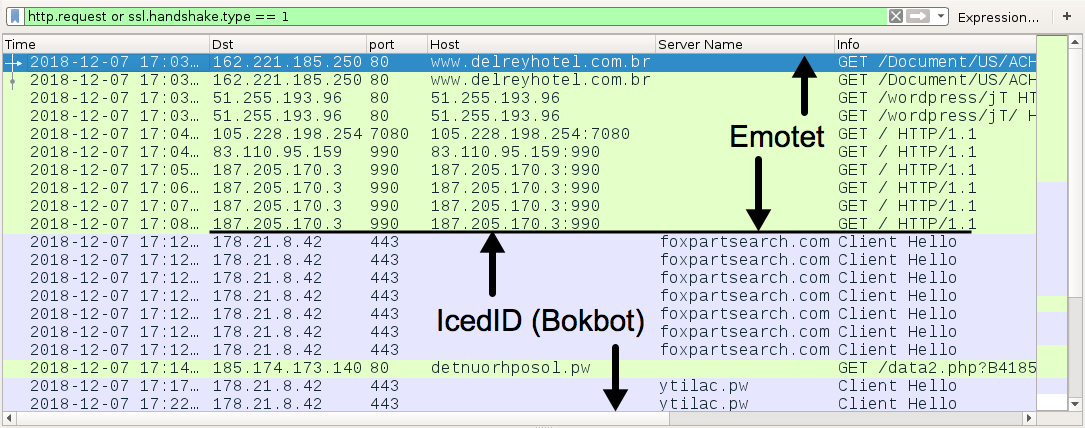
Shown above: Infection traffic filtered in Wireshark.
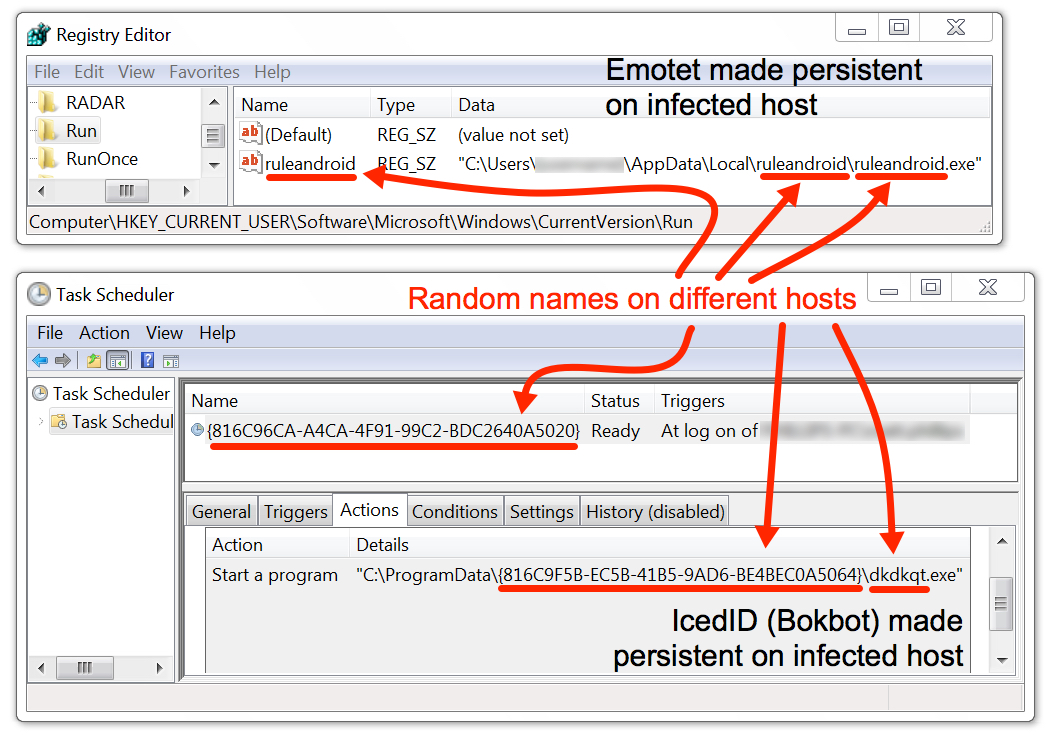
Shown above: Emotet and IcedID persistent on the infected Windows host.
Click here to return to the main page.
