2018-12-07 - NEW TRICKBOT MODULES BCCLIENTDLLTESTTEST64 AND NEWBCTESTNDLL64
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-12-07-Trickbot-infection-traffic-ser1207.pcap.zip 45.5 MB (45,470,323 bytes)
- 2018-12-07-malware-artifacts-and-modules-from-Trickbot-infected-client-and-DC.zip 31.6 MB (31,562,151 bytes)
NOTES:
- I generated today's Trickbot traffic (gtag: ser1207) based on info from a blog posted earlier today (link).
- In today's infection I saw two Trickbot modules I hadn't noticed before: bcClientDllTestTest64 and NewBCtestnDll64 (note the lower-case "n" in "NewBCtestnDll64")
- I also saw traffic I hadn't seen associated with Trickbot before, possibly related to socks5systemz according to the EmergingThreats alerts I got.
- Last year, @HerbieZimmerman saw the same type of actity that included traffic to changetheworld[.]bit on 2017-08-30 (link).
- I've included the Trickbot modules/config files from the infected DC and client, if anyone wants to try and decode them--the new modules were only on the DC.
IMAGES:

Shown above: Traffic from the infection filtered in Wireshark.
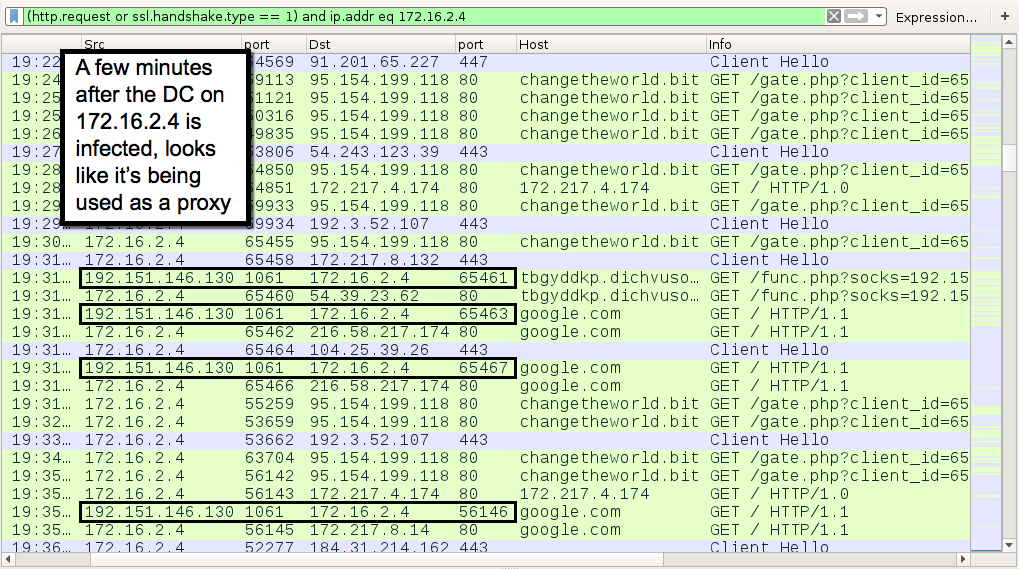
Shown above: Traffic possibly related to socks5systemz.
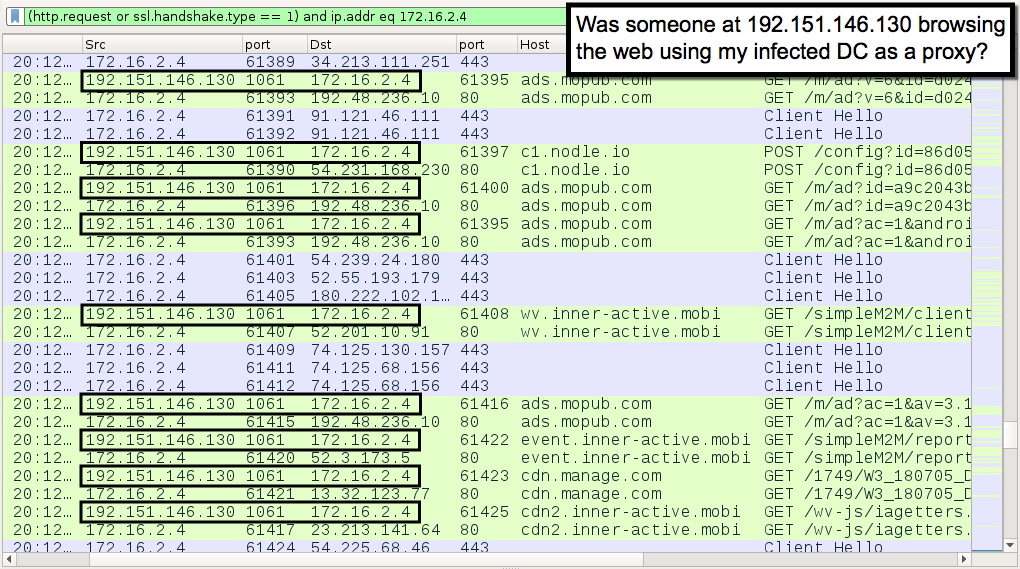
Shown above: More traffic possibly related socks5systemz, where it looks like my DC is being used as a proxy to browse something.
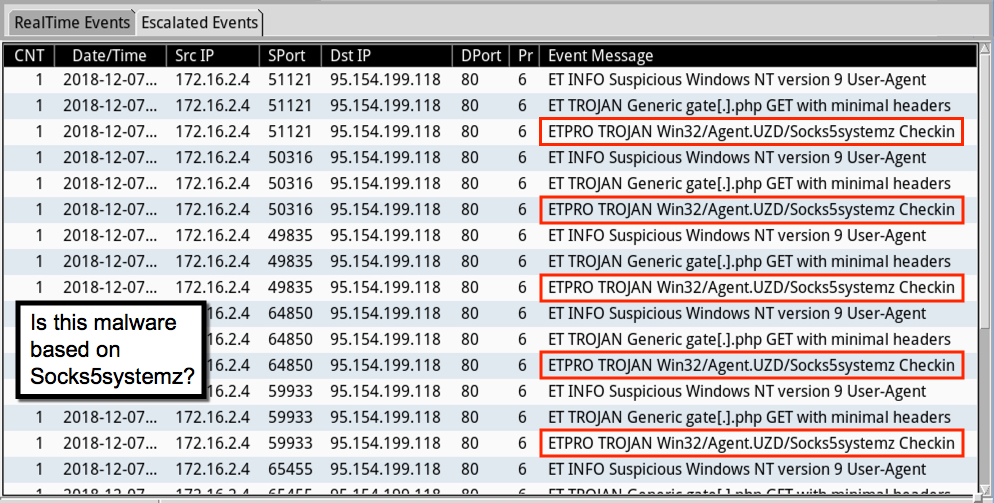
Shown above: Some alerts from the EmergingThreats Pro ruleset on Security Onion using Suricata.
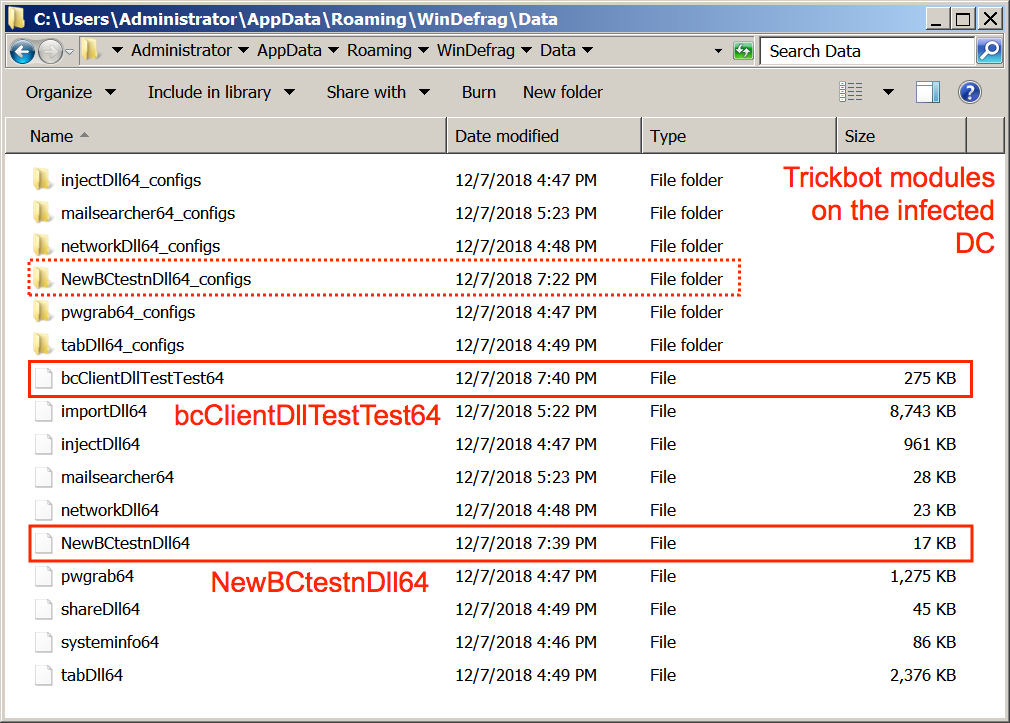
Shown above: New modules seen on the infected DC (new to me, at least).
Click here to return to the main page.
