2018-12-14 - EMOTET INFECTION WITH QAKBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Malspam example: 2018-12-14-Emotet-malspam-example-with-link.eml.zip 1.5 kB (1,527 bytes)
- 2018-12-14-Emotet-malspam-example-with-link.eml (2,167 bytes)
- Pcap of the infection traffic: 2018-12-14-Emotet-infection-with-Qakbot.pcap.zip 12.1 MB (12,146,814 bytes)
- 2018-12-14-Emotet-infection-with-Qakbot.pcap (13,190,230 bytes)
- Associated malware: 2018-12-14-Emotet-and-Qakbot-malware.zip 935.6 kB (935,629 bytes)
- 2018-12-14-downloaded-Word-doc-with-macro-for-Emotet.doc (94,336 bytes)
- 2018-12-14-Emotet-malware-binary-retrieved-by-Word-macro.exe (155,648 bytes)
- 2018-12-14-Emotet-malware-binary-updated-after-initial-infection.exe (147,456 bytes)
- 2018-12-14-Emotet-malware-binary-updated-later-during-the-infection.exe (512,000 bytes)
- 2018-12-14-QakBot-malware-retreived-by-Emotet-infected-host.exe (1,067,336 bytes)
- 2018-12-14-registry-entries-created-by-Emotet-and-Qakbot.txt (944 bytes)
- 2018-12-14-scheduled-task-created-for-Qakbot.xml.txt (3,542 bytes)
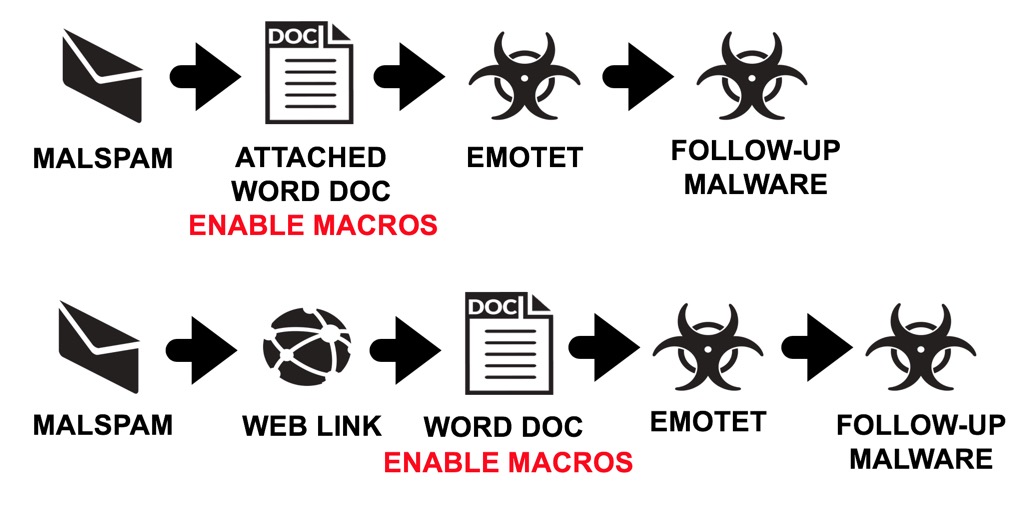
Shown above: Flow chart for recent Emotet malspam infections I've seen.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//ortugadatacorp[.]com/En_us/Clients/122018
- hxxp[:]//tortugadatacorp[.]com/En_us/Clients/122018/
- hxxp[:]//intotheharvest[.]com/uhCNWggJG
- hxxp[:]//intotheharvest[.]com/uhCNWggJG/
TRAFFIC
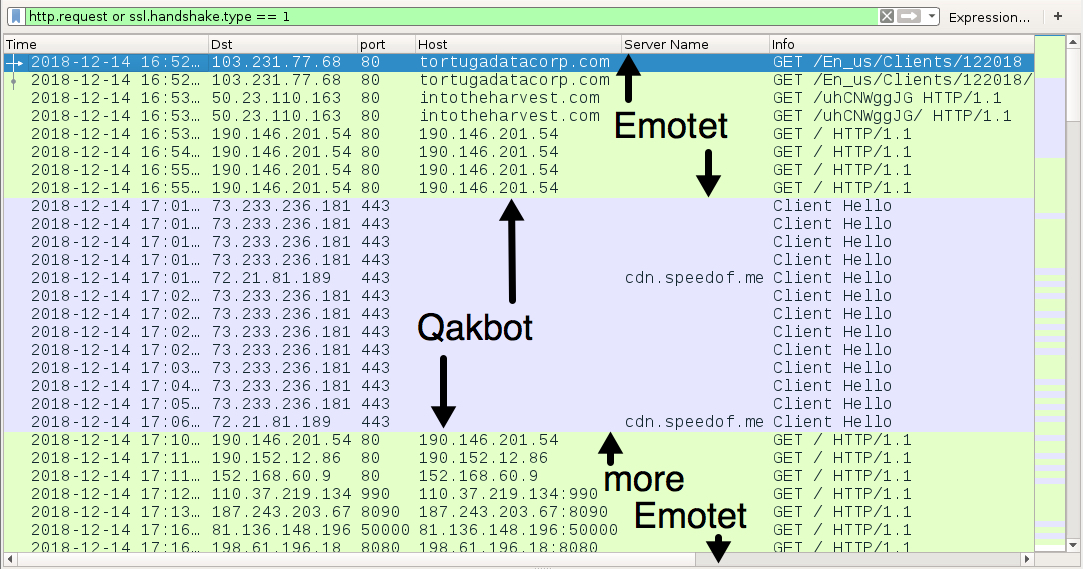
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
INITIAL EMOTET INFECTION TRAFFIC:
- 103.231.77[.]68 port 80 - tortugadatacorp[.]com - GET /En_us/Clients/122018 (URL for initial Word doc)
- 103.231.77[.]68 port 80 - tortugadatacorp[.]com - GET /En_us/Clients/122018/
- 50.23.110[.]163 port 80 - intotheharvest[.]com - GET /uhCNWggJG (URL for initial Emotet EXE)
- 50.23.110[.]163 port 80 - intotheharvest[.]com - GET /uhCNWggJG/
EMOTET POST-INFECTION TRAFFIC:
- 190.146.201[.]54 port 80 - 190.146.201[.]54 - GET /
- 190.152.12[.]86 port 80 - 190.152.12[.]86 - GET /
- 152.168.60[.]9 port 80 - 152.168.60[.]9 - GET /
- 110.37.219[.]134 port 990 - 110.37.219[.]134:990 - GET /
- 187.243.203[.]67 port 8090 - 187.243.203[.]67:8090 - GET /
- 81.136.148[.]196 port 50000 - 81.136.148[.]196:50000 - GET /
- 198.61.196[.]18 port 8080 - 198.61.196[.]18:8080 - GET /
- 217.165.236[.]108 port 7080 - 217.165.236[.]108:7080 - GET /
- 181.111.60[.]39 port 443 - 181.111.60[.]39:443 - GET /
- 181.15.92[.]18 port 80 - 181.15.92[.]18 - GET /
- 69.198.17[.]20 port 8080 - attempted TCP connections but RST from server
QAKBOT POST-INFECTION TRAFFIC:
- 73.233.236[.]181 port 443 - SSL/TLS traffic caused by Qakbot
- 69.249.141[.]152 port 443 - SSL/TLS traffic caused by Qakbot
- 72.21.81[.]189 port 443 - cdn.speedof[.]me - HTTPS/SSL/TLS traffic (not inherently malicious)
- 85.25.211[.]31 port 65400 - Qakbot post-infection traffic
- 184.90.241[.]55 port 2222 - attempted TCP connections, but no response from server
- 69.89.31[.]139 port 21 - FTP traffic (control channel) caused by Qakbot
- 69.89.31[.]139 port 41947 - FTP traffic (data channel) caused by Qakbot
MALWARE
INITIAL WORD DOC:
- SHA256 hash: 00bb4a90c611483084cb9bc695635332a32fa3cabe4782b7f1251544a5a0607c
- File size: 94,336 bytes
- File description: Word doc with macro for Emotet, downloaded from link in malspam text
EMOTET BINARIES:
- SHA256 hash: 8766fe7e95c1998f5a09306b4c94d2ef82e33e6af9b05694abbd3f970fcb1960
- File size: 155,648 bytes
- File location: hxxp[:]//intotheharvest[.]com/uhCNWggJG/
- File location: C:\Users\[username]\AppData\Local\Temp\147.exe
- File location: C:\Users\[username]\AppData\Local\limecompile\limecompile.exe (different file name and directory on different Windows hosts)
- File description: Emotet binary retrieved by Word macro
- SHA256 hash: fbff66ff8226c949f42d9ef268fee27278df5a236a0341381afbbc57e1759505
- File size: 147,456 bytes
- File location: C:\Users\[username]\AppData\Local\limecompile\limecompile.exe (different file name and directory on different Windows hosts)
- File description: Emotet binary updated after initial infection
- SHA256 hash: 44829d124b23faf1f8fe23ca1ab40fd1e7233a9208844abf3949d332f55a4c76
- File size: 512,000 bytes
- File location: C:\Users\[username]\AppData\Local\limecompile\limecompile.exe (different file name and directory on different Windows hosts)
- File description: Emotet binary updated again later during the infection
QAKBOT BINARY:
- SHA256 hash: 38e992eb852ab0c4ac03955fb0dc9bb38e64010fdf9c05331d2b02b6e05689c2
- File size: 1,067,336 bytes
- File location: C:\ProgramData\vPouzw.exe
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\Cufmznehial\auwyeop.exe
- File description: Qakbot malware retrieved by Emotet-infected Windows host
- AnyRun analysis of Qakbot EXE: https://app.any.run/tasks/d7819ce9-32c2-4763-98cc-433816695be6
- CAPE analysis of Qakbot EXE: https://cape.contextis.com/analysis/27022/
- Reverse.it analysis of Qakbot EXE: https://www.reverse.it/sample/38e992eb852ab0c4ac03955fb0dc9bb38e64010fdf9c05331d2b02b6e05689c2
CALC.EXE:
- SHA256 hash: 80c10ee5f21f92f89cbc293a59d2fd4c01c7958aacad15642558db700943fa22
- File size: 776,192 bytes
- File location: C:\Windows\SysWOW64\calc.exe
- File location: C:\ProgramData\vPouzw.exe
- File description: Not malicious, Windows system file calc.exe that replaced the original Qakbot executable file in C:\ProgramData
IMAGES
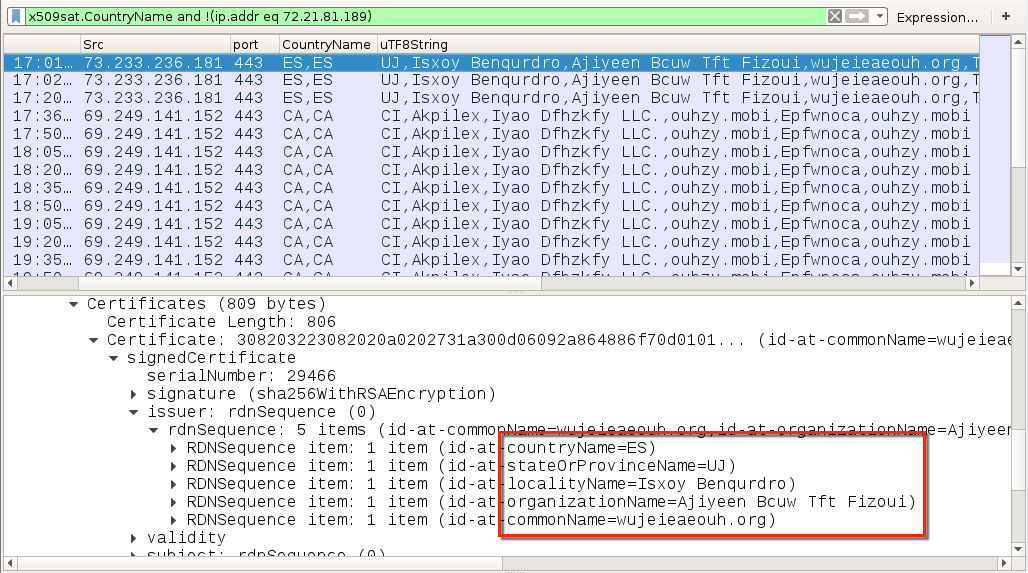
Shown above: Certificate issuer data from some of the Qakbot traffic shown in Wireshark.
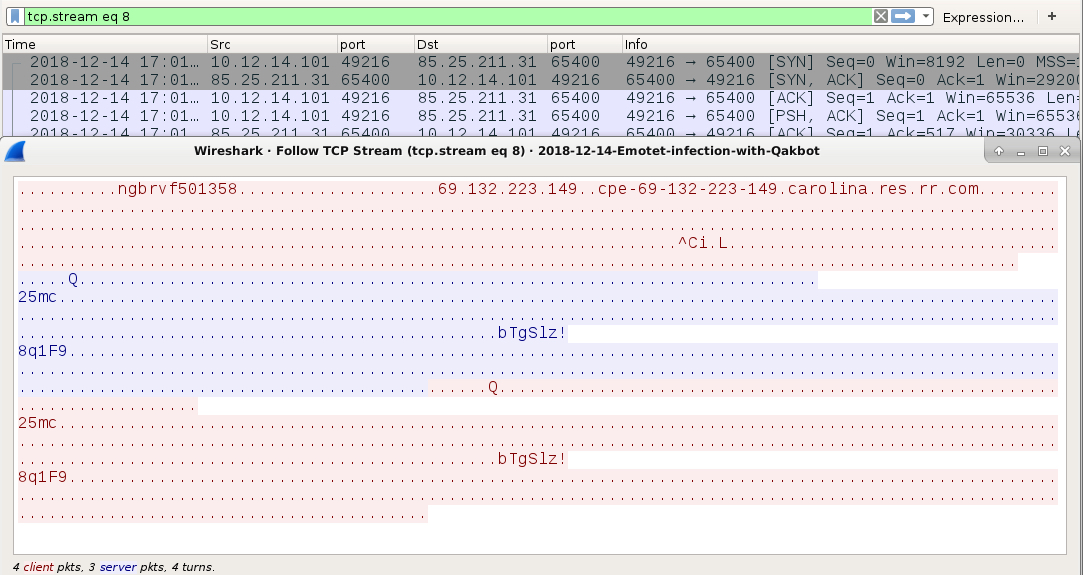
Shown above: Qakbot traffic over TCP port 65400.
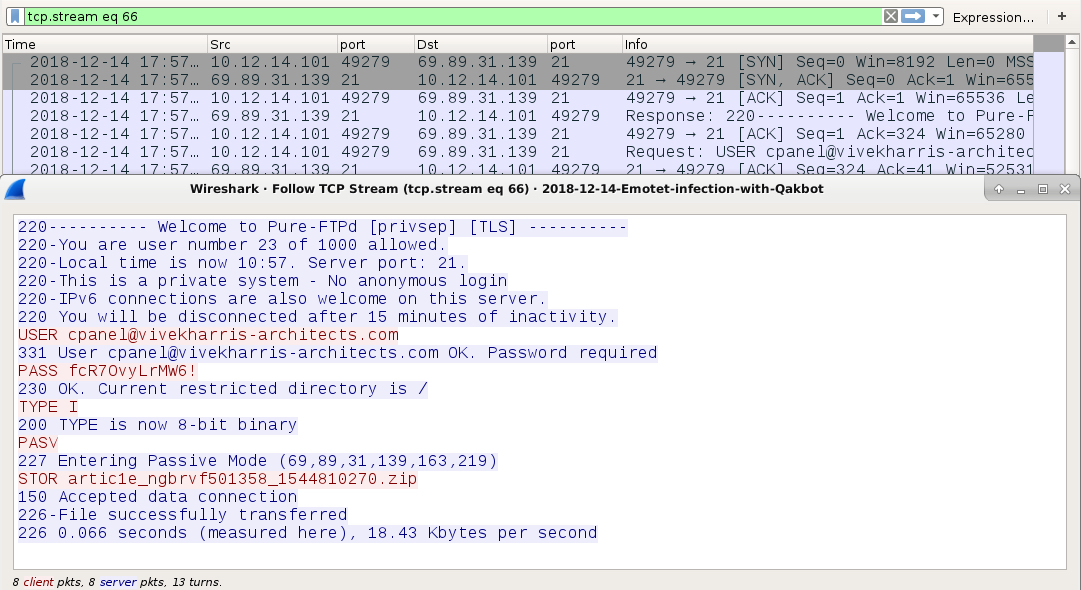
Shown above: FTP traffic (control channel) over TCP port 21.
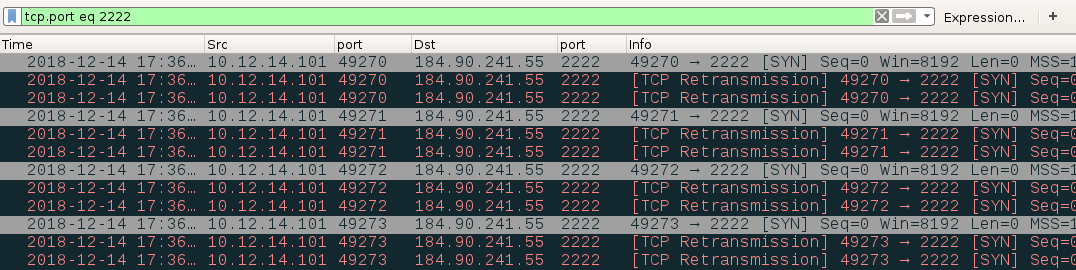
Shown above: Some additional traffic over TCP port 2222 caused by Qakbot (only attempted TCP connection attempts for my infection).
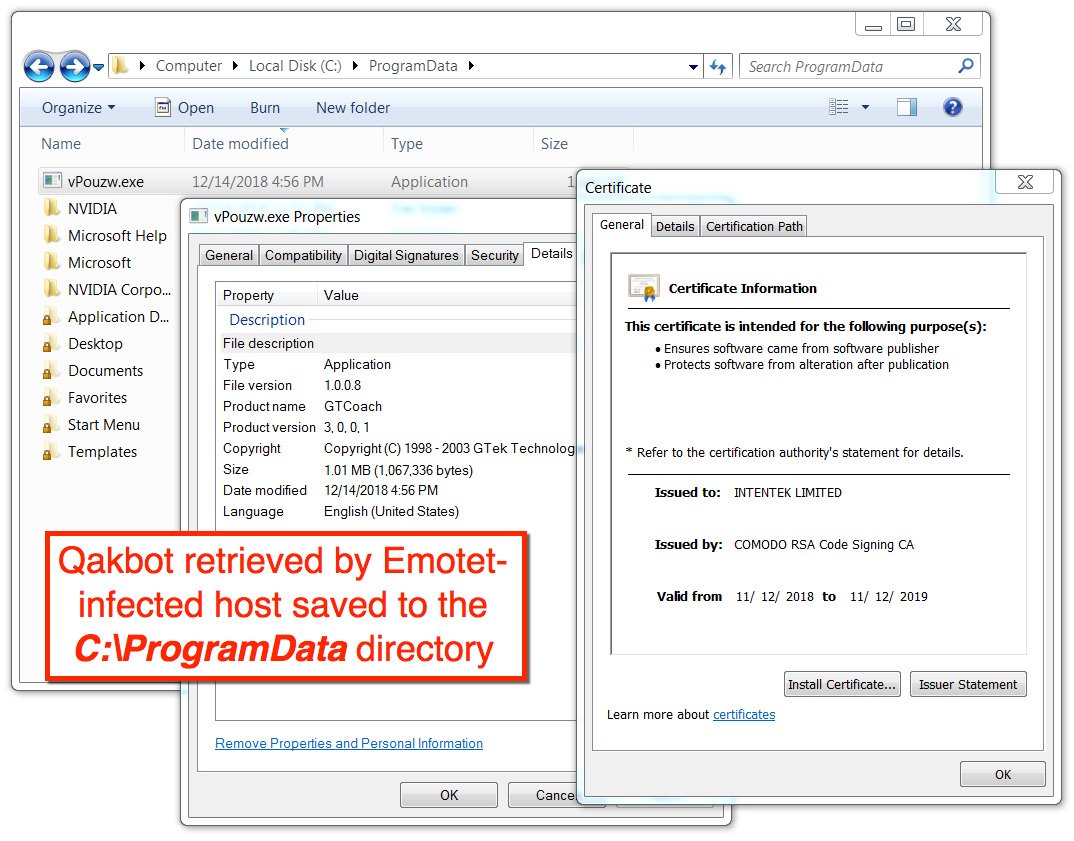
Shown above: Qakbot malware EXE retreived by the Emotet-infected Windows host.
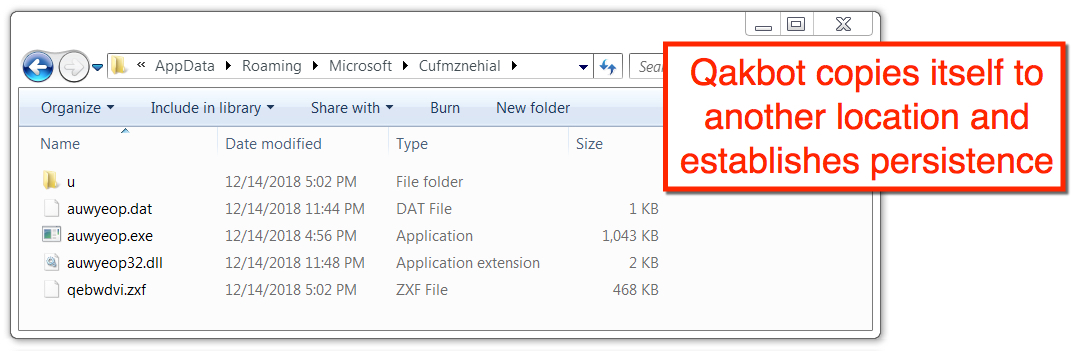
Shown above: Directory path where Qakbot moved to after it executed on the Windows host.
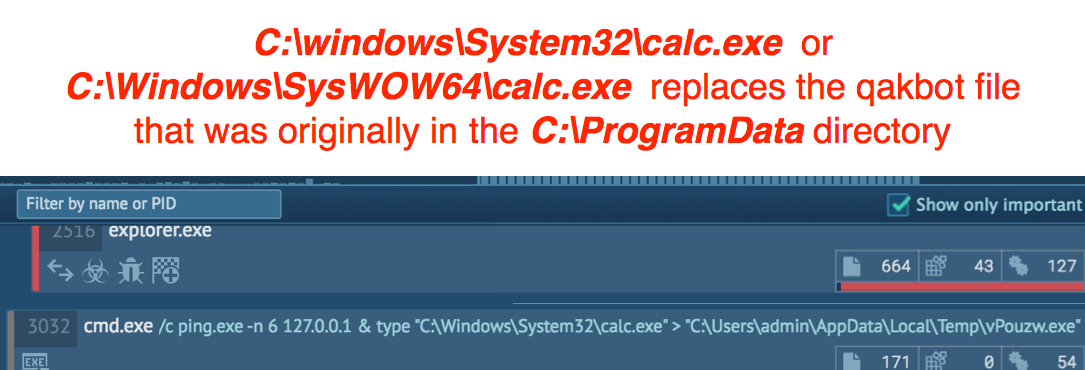
Shown above: Windows system file calc.exe (from C:\Windows\System32\calc.exe or C:\Windows\SysWOW64\calc.exe) replaces the original Qakbot file.
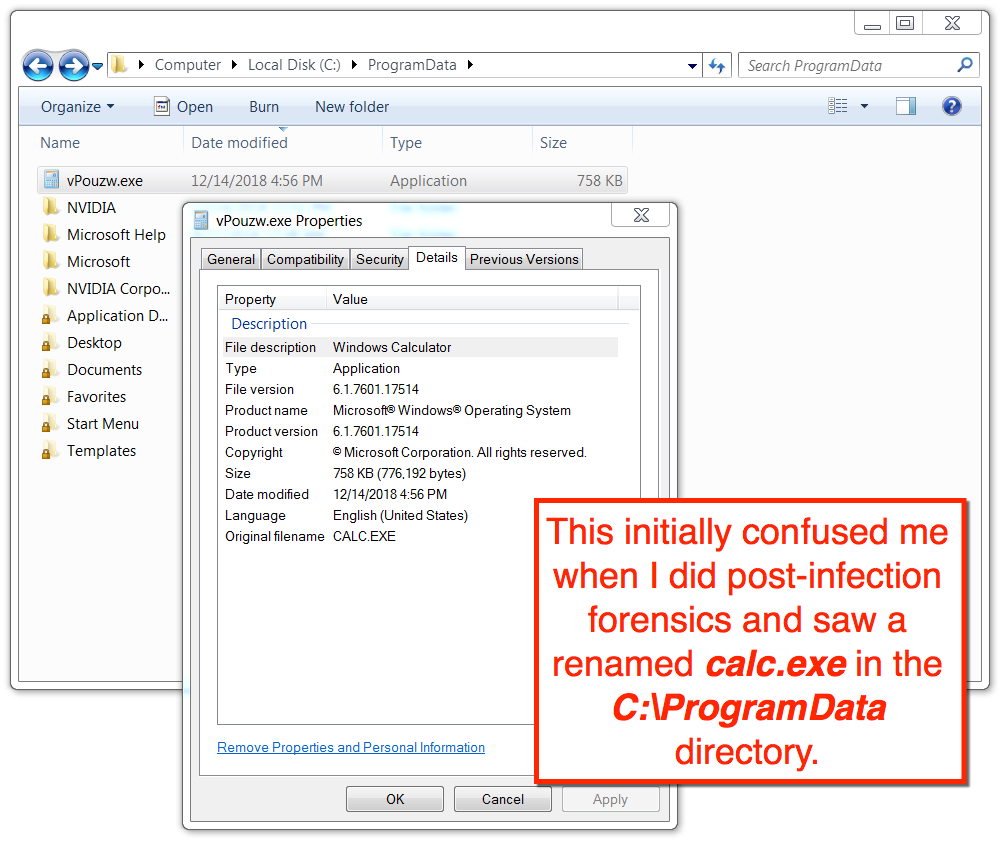
Shown above: Calc.exe file that remained in the C:\ProgramData directory.
Click here to return to the main page.
