2018-12-27 - MALSPAM PUSHES SHADE (TROLDESH) RANSOMWARE AND OTHER MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-12-27-malspam-pushing-shade-ransomware-7-examples.zip 34.6 kB (34,570 bytes)
- 2018-12-27-shade-ransomware-infection.pcap.zip 26.1 MB (26,057,523 bytes)
- 2018-12-27-malware-associated-with-shade-ransomware-infection.zip 17.3 MB (1,726,3194 bytes)
NOTES:
- This is the same campaign I wrote about last month for this ISC diary on 2018-11-29.
- In addition to the Shade ransomware, I saw a cryptocurrency miner named nheqminer and numerous attempted logins to Wordpress sites from my infected host.
- The additional malware appears to be coming through Tor traffic shortly after the initial infection activity.

Shown above: Flow chart for recent Shade/Troldesh malspam infections.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//www.kyedoll[.]com/wp-includes/ID3/sserv.jpg
- hxxp[:]//lipertekstil[.]com/imza/sserv.jpg
- hxxps[:]//goodword[.]pro/wp-content/themes/renard/fonts/sserv.jpg
- hxxp[:]//nikanbearing[.]com/templates/protostar/images/system/sserv.jpg
- hxxp[:]//bottraxanhtini[.]com/wp-content/themes/coinpr/assets/css/sserv.jpg
- hxxp[:]//macsoft[.]shop/wp-admin/css/colors/blue/sserv.jpg
- hxxp[:]//topwintips[.]com/wp-content/themes/tipsonsoccer/assets/css/sserv.jpg
MALSPAM
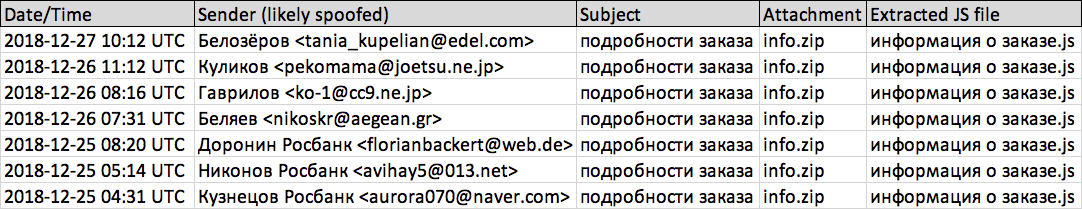
Shown above: Recent emails from this malspam.
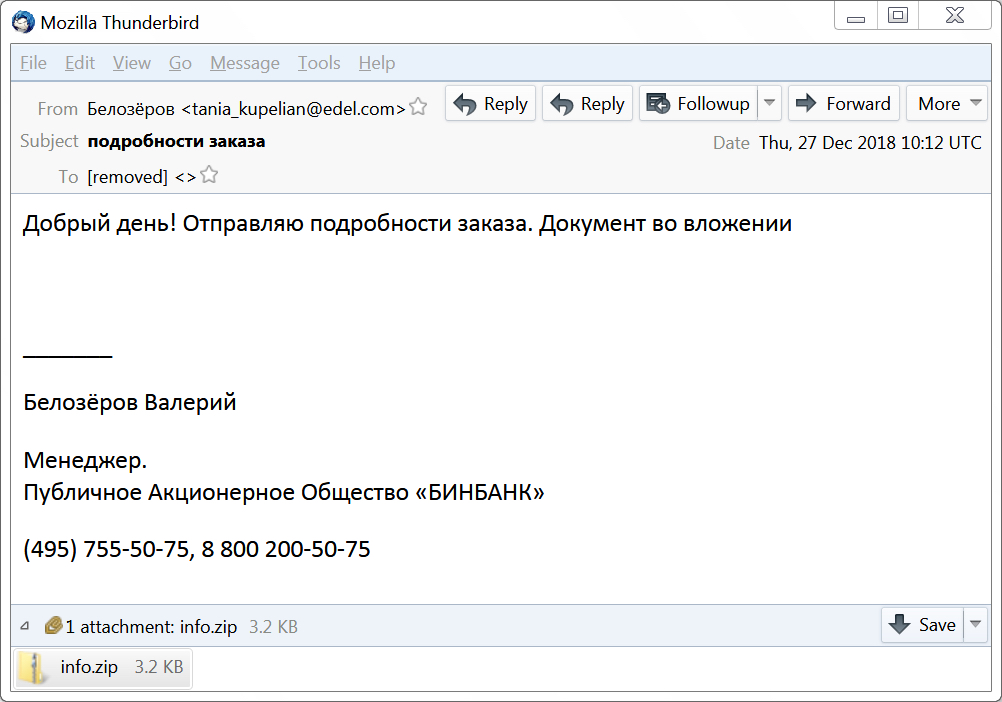
Shown above: Screenshot from an email on 2018-12-27.
EMAIL DATA FROM 7 MALSPAM EXAMPLES:
- Date/Time: As early as 2018-12-25 04:31 UTC through at least 2018-12-27 10:12 UTC
- Subject: подробности заказа
- Attachment name: info.zip
- Extracted name: информация о заказе.js
SENDERS NOTED:
- Белозёров <tania_kupelian@edel[.]com>
- Куликов <pekomama@joetsu[.]ne[.]jp>
- Гаврилов <ko-1@cc9[.]ne[.]jp>
- Беляев <nikoskr@aegean[.]gr>
- Доронин Росбанк <florianbackert@web[.]de>
- Никонов Росбанк <avihay5@013[.]net>
- Кузнецов Росбанк <aurora070@naver[.]com>

Shown above: Extracting the malicious JS file from the email attachment.
TRAFFIC
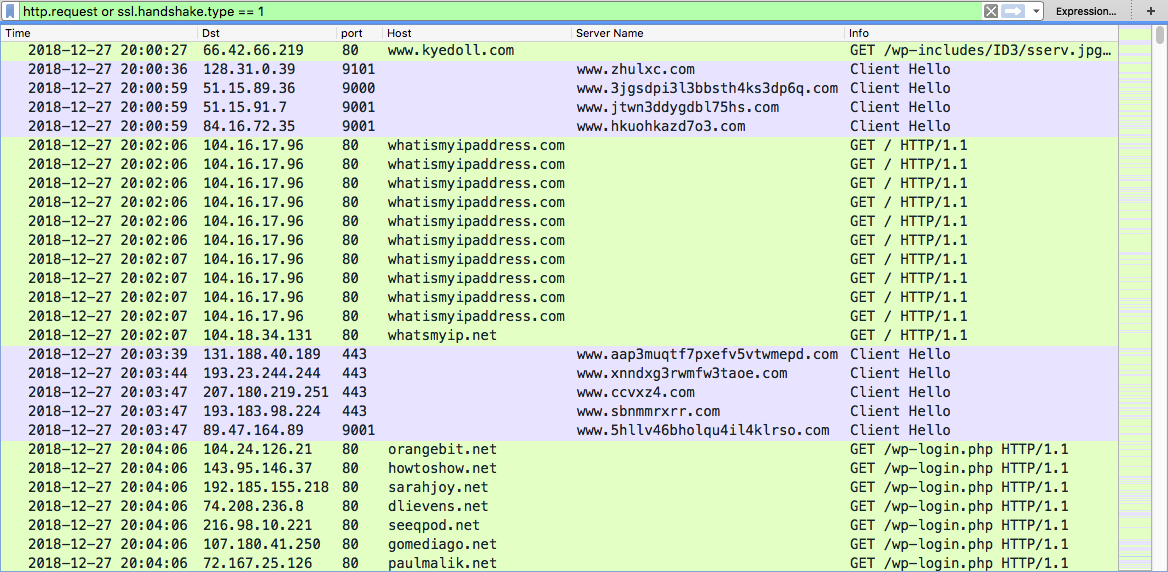
Shown above: Traffic from an infection filtered in Wireshark.
URLS GENERATED BY JS ATTACHMENTS FOR MALWARE:
- hxxp[:]//www.kyedoll[.]com/wp-includes/ID3/sserv.jpg
- hxxp[:]//lipertekstil[.]com/imza/sserv.jpg
- hxxps[:]//goodword[.]pro/wp-content/themes/renard/fonts/sserv.jpg
- hxxp[:]//nikanbearing[.]com/templates/protostar/images/system/sserv.jpg
- hxxp[:]//bottraxanhtini[.]com/wp-content/themes/coinpr/assets/css/sserv.jpg
- hxxp[:]//macsoft[.]shop/wp-admin/css/colors/blue/sserv.jpg
- hxxp[:]//topwintips[.]com/wp-content/themes/tipsonsoccer/assets/css/sserv.jpg
MALWARE
FILE ATTACHMENTS:
- 19e4bc6ca5c32011690755bf1ac57c61b1bf9d75c129eb91a07c3ae67d732e66 - info.zip
- 5e3463d89c4312084e2f65fb2d2f7645c570a4ea8e985a7a91087d2304a4cf75 - info.zip
- d77029c879b73f9f7dd3068ad106c4d0ad377ff8543ad5d41d67d43e649e9fd7 - info.zip
- 5b2a338d8e24e86057693ceb38fe12b2a4f2a762097da9a646bc3809e5b06817 - info.zip
- 62051e2dbc61ed02864344dd8650af661778d1031aaf5ed4980542c539e017c5 - info.zip
- edd5d1a65fe911c3ad1c76f5bb9f42981af3a5b8556d36f7d04ade1ae89422ae - info.zip
- 1515f56290881f9413df616aa994ee628424df2d033622572ed617efe391742d - info.zip
EXTRACTED JS FILES:
- dde78f1498360264464b80e99fd92417e1a708ad4171093f80fafa85b2f708e4 - информация о заказе.js
- fe7c78ca8d82f10ae4a7624d79fa3317ebe5b5f57bc649a68043d95d7c5d0ab7 - информация о заказе.js
- 7f69d01b627b9a628bd875b0870c05cf4d1439f359e57ce393d8deff736f9b6d - информация о заказе.js
- f49d08f9c33f280f13721810bbdb35e61c8469ace8d10a723ff867abf18a3cfa - информация о заказе.js
- 238cec6e1bfeef14d0bc78fc0d955f8d61db87be6b7e9a4cb3a068447cd1987b - информация о заказе.js
- 79d4da18a3e50c489e7d25f612e00a2193c88017e9dbca05e2ef03e889f3e814 - информация о заказе.js
- 62073a58facc8f9c7ad7cd51ab7f81942b320344c40bc3974b6b287a5da79550 - информация о заказе.js
MALWARE RETRIEVED FROM INFECTED WINDOWS HOST:
- 9fd59ba40c26b3161642d5ebb85796b4262e5d5aa5d1e5eceb919b52a8f9b00e - initial malware retrieved by JS file (1 of 2)
- 50119da56e84ae4baa207a9391a0143fe5aa66c212aeba08e2d6d864af0a0d83 - initial malware retrieved by JS file (2 of 2)
- 9ff6b78524b83d667df34eb5e00bf47dc66ca2b4bb7f9422622103311eee3d6e - malware related to Shade ransomware infection
- 026e8c1bb6fda0bd89dd2d87ef95a8920df5ba331b74c604223f75e597069ded - intaller for nheqminer (Equihash miner for NiceHash)
- 9d3bac28e24a997c2d2b3a955b7f0d57494950a0269f1bf31dc45fb1dadcdb84 - malware related to Shade ransomware infection
- 2824a8ce0e65bb185a88ff1fe5f1df202405c42b6705a420dbc07c565a44b240 - malware related to Shade ransomware infection
OTHER INFO
EMAIL FROM DECRYPTION INSTRUCTIONS:
- pilotpilot088[at]gmail[.]com
TOR DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- cryptsen7fo43rr6[.]onion[.]to
- cryptsen7fo43rr6[.]onion[.]cab
FILE EXTENSION FOR ALL ENCRYPTED FILES:
- .crypted000007
IMAGES
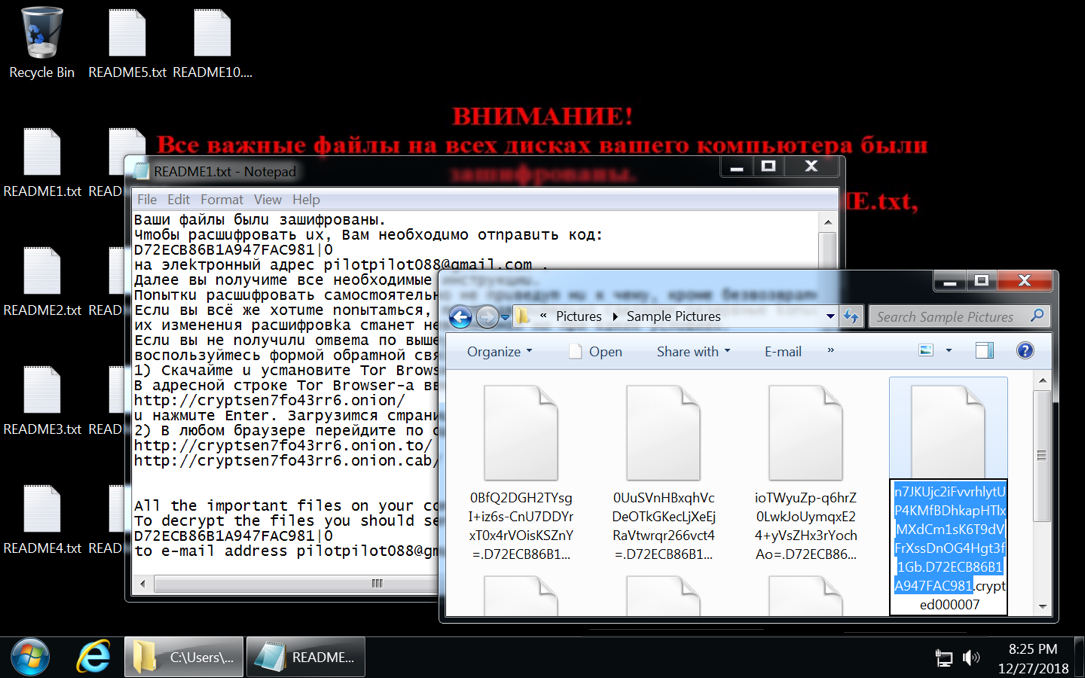
Shown above: Desktop of an infected Windows host.
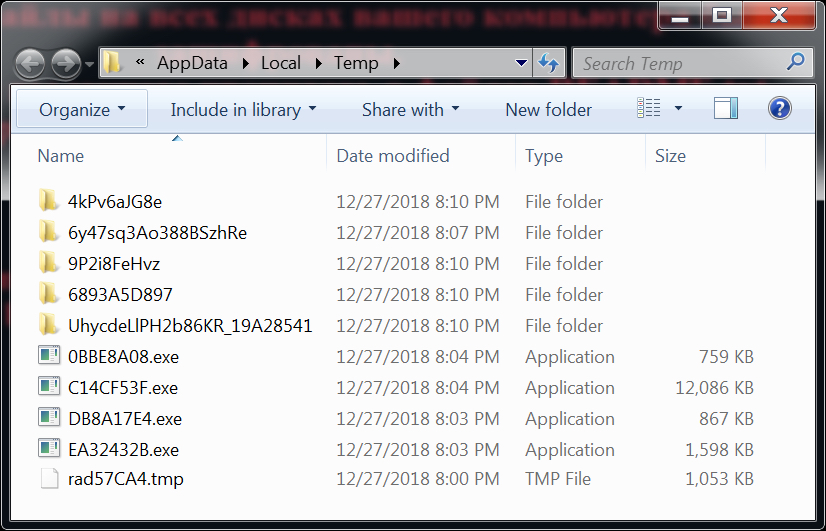
Shown above: Malware found in the user's AppData\Local\Temp folder.
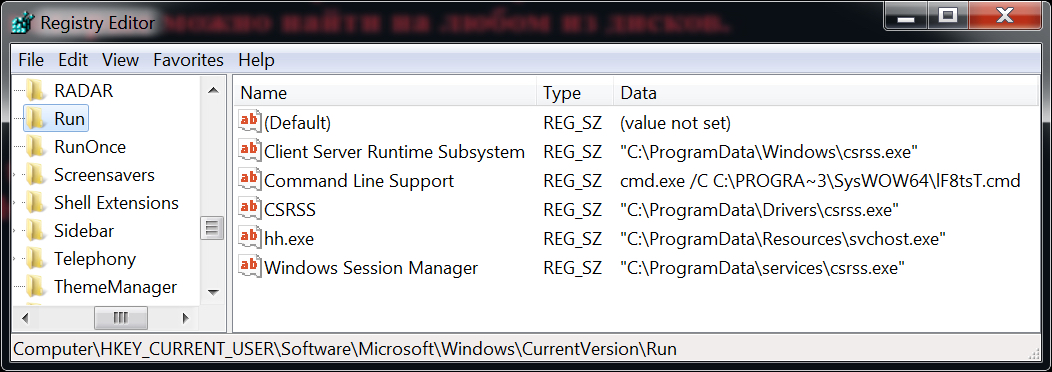
Shown above: Windows registry updates found on the infected Windows host.
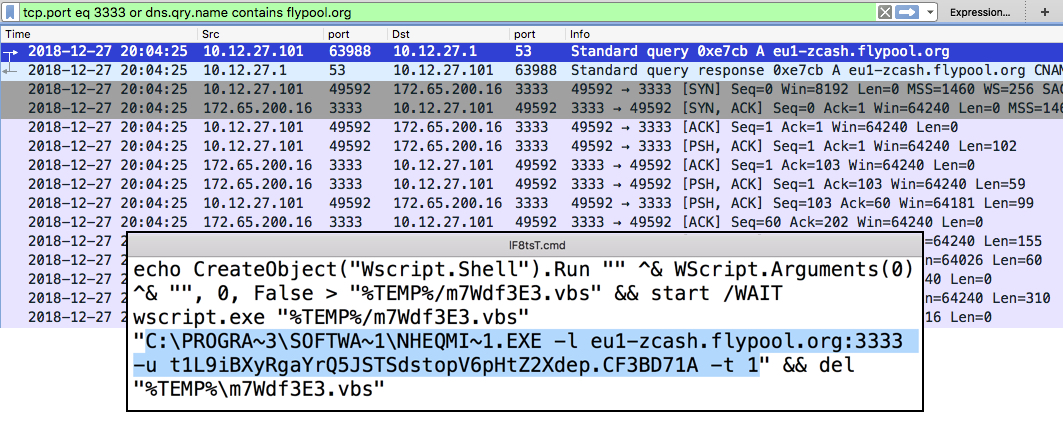
Shown above: Traffic generated by the nheqminer associated with this Shade ransomware infection.
Click here to return to the main page.
