2019-01-16 - HANCITOR MALSPAM WITH PAYPAL THEME
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Email examples: 2019-01-16-Hancitor-malspam-47-email-examples.zip 166 kB (165,978 bytes)
- 47 .eml files ranging from 16,891 to 17,120 bytes each
- Traffic: 2019-01-16-Hancitor-infection-traffic-with-Ursnif.pcap.zip 405 kB (405,401 bytes)
- 2019-01-16-Hancitor-infection-traffic-with-Ursnif.pcap (767,878 bytes)
- Malware: 2019-01-16-malware-from-Hancitor-infected-host.zip 276 kB (275,889 bytes)
- 2019-01-16-Hancitor-binary-retrieved-by-Excel-macro.exe (94210 bytes)
- 2019-01-16-Ursnif-retrieved-by-Hancitor-infected-host.exe (236,032 bytes)
- 2019-01-16-downloaded-Excel-speadsheet-with-macro-for-Hancitor.xls (274,432 bytes)
NOTES:
- Today's blog includes indicators already tweeted/posted by @mesa_matt (link to tweet).
- As always, my thanks to everyone who keeps an eye on this malspam, reports about it near-real-time on Twitter, and helps me get copies of the malspam to share.
Shown above: Flow chart for recent Hancitor malspam infections.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- 800lasallepark[.]ca
- 800lasallepark[.]com
- auctionhauz[.]ca
- gsgroupco[.]ca
- guildwoodcondos[.]com
- lasalleparkliving[.]ca
- lasalleparkliving[.]com
- lasalleparkresidences[.]com
- ockickfit[.]com
- reserveithome[.]com
- rezerevit[.]com
- ledbabdintot[.]com
- ofheptonsfi[.]ru
- netedingof[.]ru
- hxxp[:]//jenrobin[.]com/wp-content/plugins/mailchimp-for-wp/1
- hxxp[:]//jenrobin[.]com/wp-content/plugins/mailchimp-for-wp/2
- hxxp[:]//jenrobin[.]com/wp-content/plugins/mailchimp-for-wp/3
- hxxp[:]//kevinalves[.]com/wp-content/plugins/w3-total-cache/inc/1
- hxxp[:]//kevinalves[.]com/wp-content/plugins/w3-total-cache/inc/2
- hxxp[:]//kevinalves[.]com/wp-content/plugins/w3-total-cache/inc/3
- hxxp[:]//emilyhendrie[.]com/wp-content/plugins/jetpack/modules/1
- hxxp[:]//emilyhendrie[.]com/wp-content/plugins/jetpack/modules/2
- hxxp[:]//emilyhendrie[.]com/wp-content/plugins/jetpack/modules/3
- hxxp[:]//salshakenwrap[.]com/wp-content/plugins/mailchimp/lib/1
- hxxp[:]//salshakenwrap[.]com/wp-content/plugins/mailchimp/lib/2
- hxxp[:]//salshakenwrap[.]com/wp-content/plugins/mailchimp/lib/3
- api.ex100p[.]at
- ax.ikobut[.]at
- beetfeetlife[.]bit
- core.cnboal[.]at
- extra.avareg[.]cn
- f1.cnboal[.]at
- foo.avaregio[.]at
- g2.ex100p[.]at
- in.termas[.]at
- op.basedok[.]at
- pop.muongo[.]at
- sm.dvloop[.]at
- xxx.lapoder[.]at
MALSPAM DATA
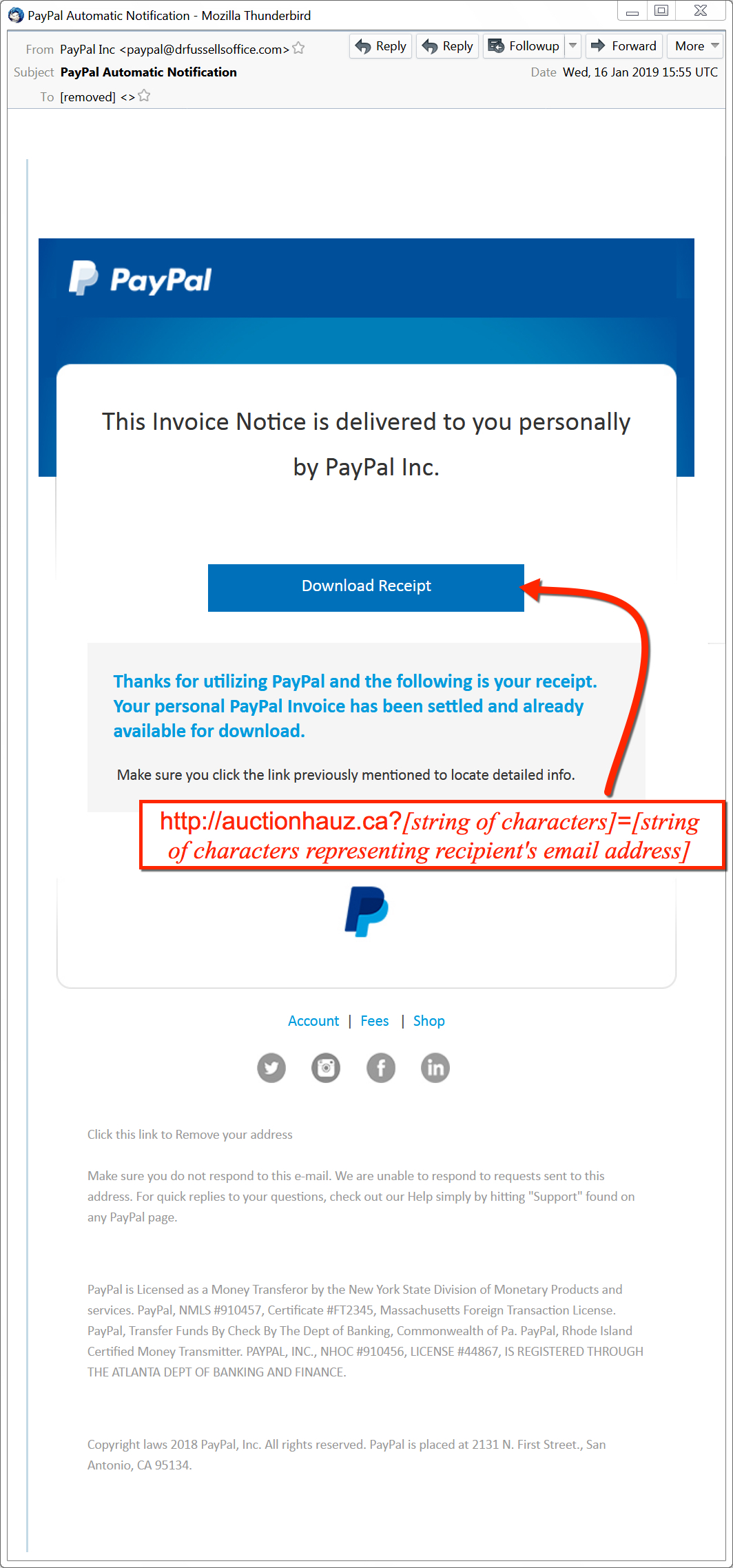
Shown above: Screenshot from one of the emails.
DATA FROM 47 EMAIL EXAMPLES:
- Date: Wed, 16 Jan 2019 as early as 15:06 UTC through at least 18:43 UTC
- From: "PayPal Inc" <paypal@drfussellsoffice[.]com>
- From: "PayPal Invoice Service" <paypal@drfussellsoffice[.]com>
- From: "PayPal Services" <paypal@drfussellsoffice[.]com>
- Subject: PayPal Message
- Subject: PayPal Invoice Message
- Subject: PayPal Invoice Notice
- Subject: PayPal Invoice Notification
- Subject: PayPal Automated Message
- Subject: PayPal Automated Notice
- Subject: PayPal Automated Notification
- Subject: PayPal Automated Invoice Message
- Subject: PayPal Automated Invoice Notice
- Subject: PayPal Automated Invoice Notification
- Subject: PayPal Automatic Message
- Subject: PayPal Automatic Notice
- Subject: PayPal Automatic Notification
- Subject: PayPal Automatic Invoice Message
- Subject: PayPal Automatic Invoice Notice
- Subject: PayPal Electronic Message
- Subject: PayPal Electronic Notice
- Subject: PayPal Electronic Notification
- Subject: PayPal Electronic Invoice Notice
- Subject: PayPal Electronic Invoice Notification
- Received: from drfussellsoffice[.]com ([12.109.16[.]58])
- Received: from drfussellsoffice[.]com ([12.45.130[.]50])
- Received: from drfussellsoffice[.]com ([139.60.59[.]98])
- Received: from drfussellsoffice[.]com ([50.239.76[.]242])
- Received: from drfussellsoffice[.]com ([65.157.99[.]75])
- Received: from drfussellsoffice[.]com ([70.102.241[.]100])
- Received: from drfussellsoffice[.]com ([70.61.145[.]82])
- Received: from drfussellsoffice[.]com ([71.14.210[.]162])
- Received: from drfussellsoffice[.]com ([72.176.162[.]206])
- Received: from drfussellsoffice[.]com ([96.76.95[.]230])
- Received: from drfussellsoffice[.]com ([152.179.144[.]130])
- Received: from drfussellsoffice[.]com ([173.246.255[.]76])
- Received: from drfussellsoffice[.]com ([192.65.138[.]25])
- Received: from drfussellsoffice[.]com ([216.130.144[.]155])
- Received: from drfussellsoffice[.]com (23-24-96-78-static.hfc.comcastbusiness[.]net [23.24.96[.]78])
- Received: from drfussellsoffice[.]com (24-181-105-27.static.leds.al.charter[.]com [24.181.105[.]27])
- Received: from drfussellsoffice[.]com (50-251-86-105-static.hfc.comcastbusiness[.]net [50.251.86[.]105])
- Received: from drfussellsoffice[.]com (68-188-71-194.static.stls.mo.charter[.]com [68.188.71[.]194])
- Received: from drfussellsoffice[.]com (96-65-154-214-static.hfc.comcastbusiness[.]net [96.65.154[.]214])
- Received: from drfussellsoffice[.]com (96-89-163-241-static.hfc.comcastbusiness[.]net [96.89.163[.]241])
- Received: from drfussellsoffice[.]com (156-019-134-170.static.chtrptr[.]net [156.19.134[.]170])
- Received: from drfussellsoffice[.]com (173-16-153-170.client.mchsi[.]com [173.16.153[.]170])
- Received: from drfussellsoffice[.]com (173-21-25-192.client.mchsi[.]com [173.21.25[.]192])
- Received: from drfussellsoffice[.]com (c-71-235-229-4.hsd1.ct.comcast[.]net [71.235.229[.]4])
- Received: from drfussellsoffice[.]com (c-73-132-138-136.hsd1.dc.comcast[.]net [73.132.138[.]136])
- Received: from drfussellsoffice[.]com (c-73-132-204-156.hsd1.dc.comcast[.]net [73.132.204[.]156])
- Received: from drfussellsoffice[.]com (cblmdm170-253-139-175.maxxsouthbb[.]net [170.253.139[.]175])
- Received: from drfussellsoffice[.]com (cpe-70-119-253-232.tx.res.rr[.]com [70.119.253[.]232])
- Received: from drfussellsoffice[.]com (cpe-74-72-138-117.nyc.res.rr[.]com [74.72.138[.]117])
- Received: from drfussellsoffice[.]com (dsl-066-037-088-090.citizip[.]com [66.37.88[.]90])
- Received: from drfussellsoffice[.]com (hb.scu-mobile[.]org [12.150.236[.]34])
- Received: from drfussellsoffice[.]com (rrcs-24-97-103-170.nys.biz.rr[.]com [24.97.103[.]170])
- Received: from drfussellsoffice[.]com (rrcs-70-63-229-90.midsouth.biz.rr[.]com [70.63.229[.]90])
- Received: from drfussellsoffice[.]com (rrcs-147-0-240-146.central.biz.rr[.]com [147.0.240[.]146])
- Received: from drfussellsoffice[.]com (rrcs-208-125-2-58.nyc.biz.rr[.]com [208.125.2[.]58])
- Received: from drfussellsoffice[.]com (static-72-68-134-154.nycmny.fios.verizon[.]net [72.68.134[.]154])
- Received: from drfussellsoffice[.]com (static-100-2-196-21.nycmny.fios.verizon[.]net [100.2.196[.]21])
- Received: from drfussellsoffice[.]com (static-100-38-139-34.nycmny.fios.verizon[.]net [100.38.139[.]34])
- Received: from drfussellsoffice[.]com (static-198-211-150-226.earthlinkbusiness[.]net [198.211.150[.]226])
- Received: from drfussellsoffice[.]com (wsip-70-182-4-198.lf.br.cox[.]net [70.182.4[.]198])
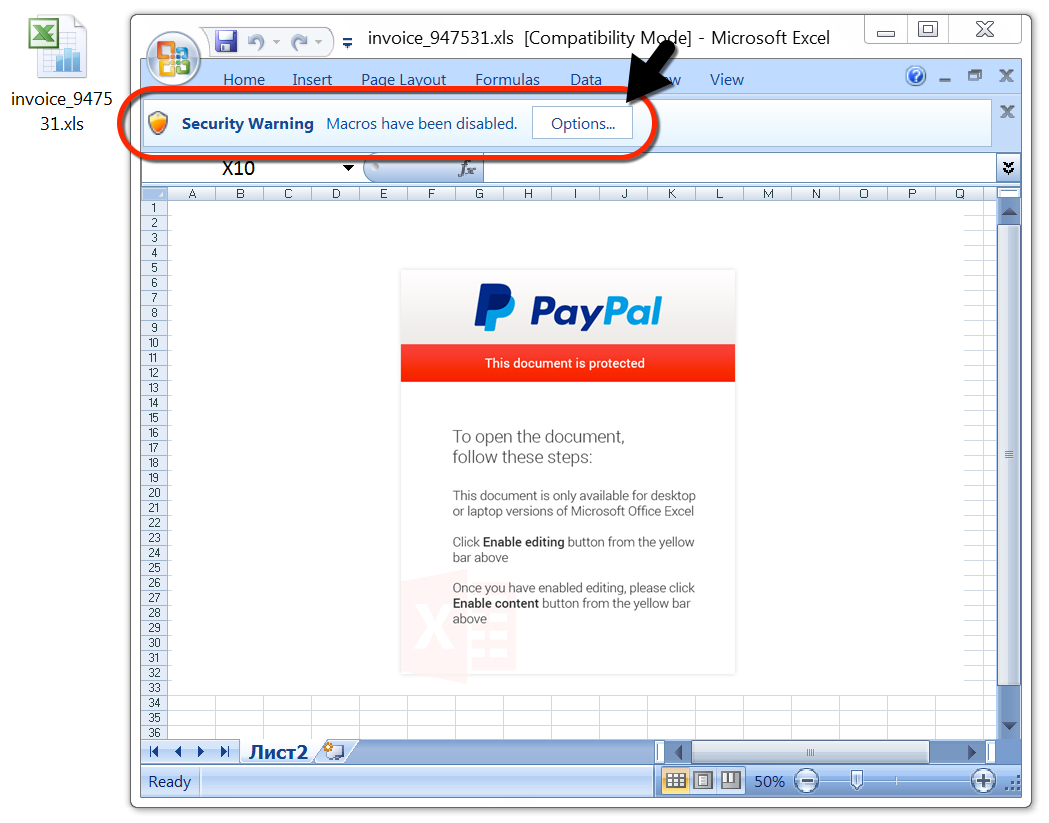
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
LINKS IN THE EMAILS TO DOWNLOAD THE WORD DOCUMENT:
- hxxp[:]//800lasallepark[.]ca?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//800lasallepark[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//auctionhauz[.]ca?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//gsgroupco[.]ca?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//guildwoodcondos[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//lasalleparkliving[.]ca?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//lasalleparkliving[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//lasalleparkresidences[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ockickfit[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//reserveithome[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//rezerevit[.]com?[string of characters]=[encoded string representing recipient's email address]
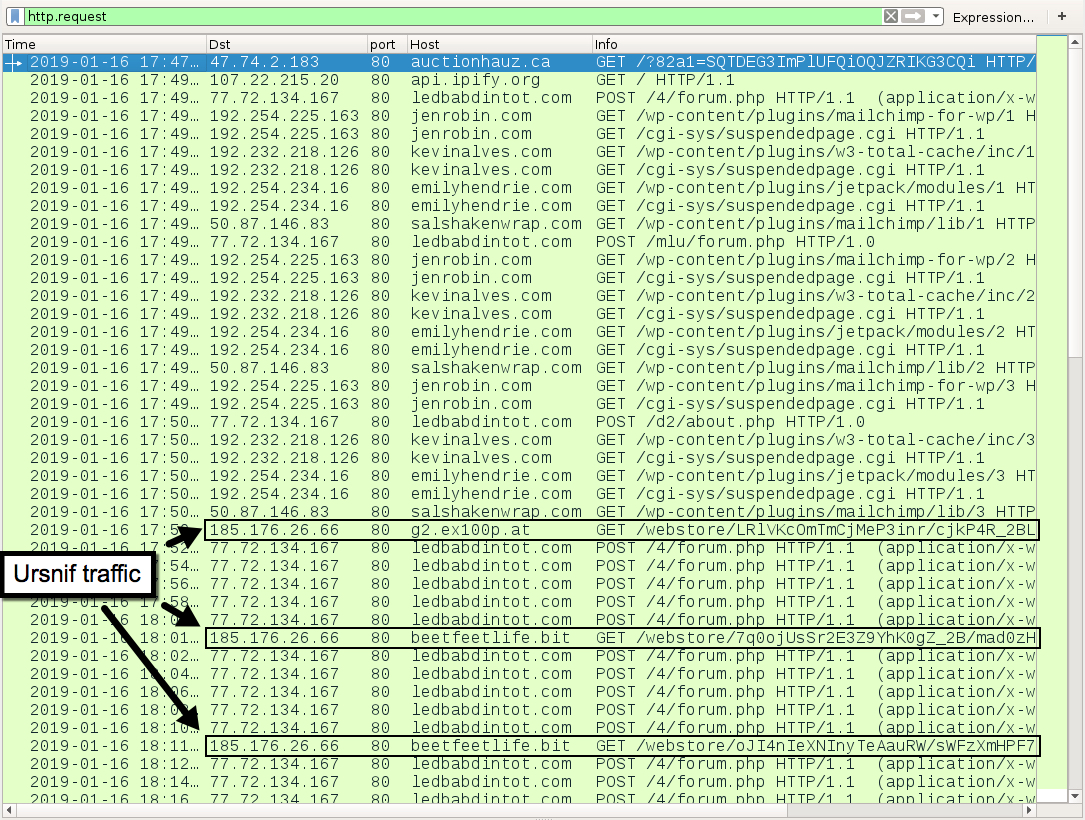
Shown above: HTTP traffic from today's infection filtered in Wireshark.
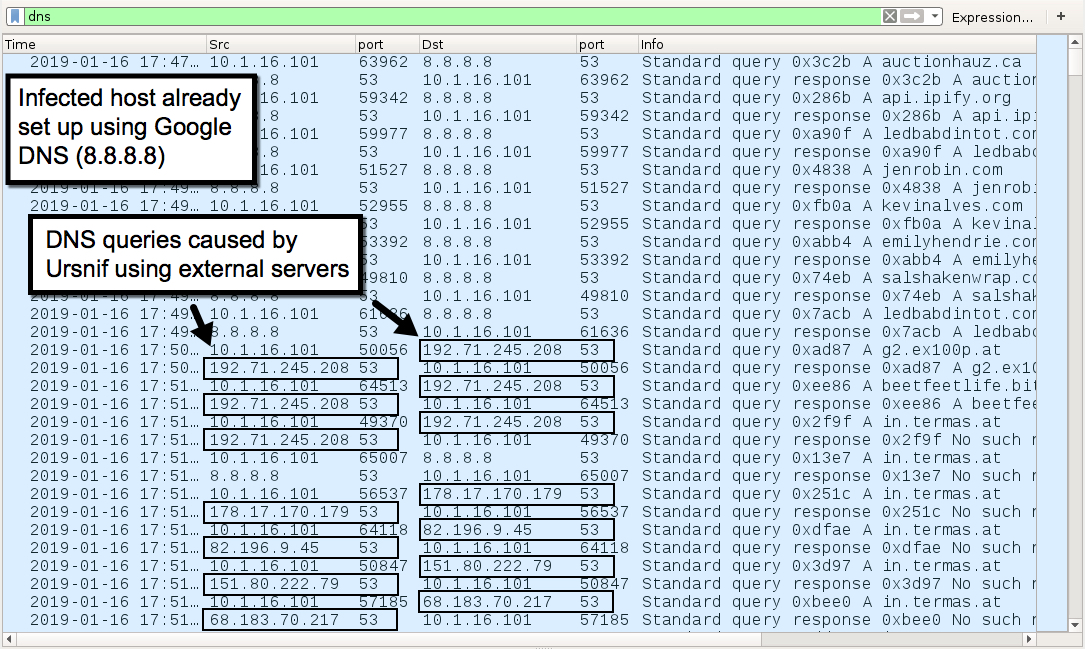
Shown above: DNS traffic from today's infection filtered in Wireshark.
INITIAL HANCITOR INFECTION TRAFFIC:
- 47.74.2[.]183 port 80 - auctionhauz[.]ca - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify.org - GET /
- 77.72.134[.]167 port 80 - ledbabdintot[.]com - POST /4/forum.php
- 77.72.134[.]167 port 80 - ledbabdintot[.]com - POST /mlu/about.php
- 77.72.134[.]167 port 80 - ledbabdintot[.]com - POST /d2/about.php
- 192.254.225[.]163 port 80 - jenrobin[.]com - GET /wp-content/plugins/mailchimp-for-wp/1
- 192.254.225[.]163 port 80 - jenrobin[.]com - GET /wp-content/plugins/mailchimp-for-wp/2
- 192.254.225[.]163 port 80 - jenrobin[.]com - GET /wp-content/plugins/mailchimp-for-wp/3
- 192.232.218[.]126 port 80 - kevinalves[.]com - GET /wp-content/plugins/w3-total-cache/inc/1
- 192.232.218[.]126 port 80 - kevinalves[.]com - GET /wp-content/plugins/w3-total-cache/inc/2
- 192.232.218[.]126 port 80 - kevinalves[.]com - GET /wp-content/plugins/w3-total-cache/inc/3
- 192.254.234[.]16 port 80 - emilyhendrie[.]com - GET /wp-content/plugins/jetpack/modules/1
- 192.254.234[.]16 port 80 - emilyhendrie[.]com - GET /wp-content/plugins/jetpack/modules/2
- 192.254.234[.]16 port 80 - emilyhendrie[.]com - GET /wp-content/plugins/jetpack/modules/3
- 50.87.146[.]83 port 80 - salshakenwrap[.]com - GET /wp-content/plugins/mailchimp/lib/1
- 50.87.146[.]83 port 80 - salshakenwrap[.]com - GET /wp-content/plugins/mailchimp/lib/2
- 50.87.146[.]83 port 80 - salshakenwrap[.]com - GET /wp-content/plugins/mailchimp/lib/3
GOZI/ISFB (URSNIF) POST-INFECTION HTTP TRAFFIC:
- 185.176.26[.]66 port 80 - g2.ex100p[.]at - GET /webstore/[long string of characters]
- 185.176.26[.]66 port 80 - beetfeetlife[.]bit - GET /webstore/[long string of characters]
GOZI/ISFB (URSNIF) POST-INFECTION DNS TRAFFIC:
- 5.189.170[.]196 port 53 (UDP) - DNS queries for Ursnif domains
- 68.183.70[.]217 port 53 (UDP) - DNS queries for Ursnif domains
- 82.196.9[.]45 port 53 (UDP) - DNS queries for Ursnif domains
- 94.247.43[.]254 port 53 (UDP) - DNS queries for Ursnif domains
- 150.249.149[.]222 port 53 (UDP) - DNS queries for Ursnif domains
- 151.80.222[.]79 port 53 (UDP) - DNS queries for Ursnif domains
- 158.69.160[.]164 port 53 (UDP) - DNS queries for Ursnif domains
- 159.89.249[.]249 port 53 (UDP) - DNS queries for Ursnif domains
- 178.17.170[.]179 port 53 (UDP) - DNS queries for Ursnif domains
- 188.165.200[.]156 port 53 (UDP) - DNS queries for Ursnif domains
- 192.71.245[.]208 port 53 (UDP) - DNS queries for Ursnif domains
- 207.148.83[.]241 port 53 (UDP) - DNS queries for Ursnif domains
- 217.144.132[.]148 port 53 (UDP) - DNS queries for Ursnif domains
- 217.144.135[.]7 port 53 (UDP) - DNS queries for Ursnif domains
GOZI/ISFB (URSNIF) DOMAINS IN THE DNS QUERIES:
- api.ex100p[.]at
- ax.ikobut[.]at
- beetfeetlife[.]bit
- core.cnboal[.]at
- extra.avareg[.]cn
- f1.cnboal[.]at
- foo.avaregio[.]at
- g2.ex100p[.]at
- in.termas[.]at
- op.basedok[.]at
- pop.muongo[.]at
- sm.dvloop[.]at
- xxx.lapoder[.]at
FILE HASHES
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: b5818529e226a30591eb4cddee881538f19509dd139e099bb056d8e8ce5ac055
File size: 274,432 bytes
File name: invoice_947531.xls (random numbers in the file name)
File description: Excel spreadsheet downloaded from a link in Hancitor malspam. Has macro to cause Hancitor infection.
- SHA256 hash: 1199b24d407ccdddf83fafaf8d63e971edaafded99214bee6b2ad4906729e4d7
File size: 94,210 bytes
File location: C:\Users\[username]\AppData\Local\Temp\6fsdFfa.com
File location: C:\Users\[username]\AppData\Local\Temp\6.pif
File description: Hancitor malware EXE retrieved by macro in downloaded Excel spreadsheet
- SHA256 hash: d31f2993ec21c24064ce1f2987e10bfe271103880777b476c0d1812423c1c4b0
File size: 236,032 bytes
File location: C:\Users\[username]AppData\Local\Temp\BNCD5C.tmp (random hex characters in file name)
File description: Gozi/ISFB (Ursnif) EXE on 2019-01-16 retreived by Hancitor-infected host
Click here to return to the main page.

