2019-01-21 - EMOTET INFECTION WITH GOOTKIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Pcap of the infection traffic: 2019-01-21-Emotet-infection-with-Gootkit.pcap.zip 6.3 MB (6,283,535 bytes)
- 2019-01-21-Emotet-infection-with-Gootkit.pcap (7,595,455 bytes)
- Associated malware: 2019-01-21-Emotet-and-Gootkit-malware-and-artifacts.zip 462 kB (461,917 bytes)
- 2019-01-21-Emotet-EXE-retreived-by-Word-macro.exe (159,744 bytes)
- 2019-01-21-Gootkit-retrieved-by-Emotet-infected-host.exe (299,520 bytes)
- 2019-01-21-INF-file-for-Gootkit.txt (305 bytes)
- 2019-01-21-downloaded-Word-doc-with-macro-for-Emotet.doc (265,289 bytes)
NOTES:
- @cryptolaemus1 posted info on more than 200 URLs seen on 2019-01-21.
- Based on URL patterns, the majority of these URLs for the Emotet Word document are from Germany-targeted malspam.
- Today also revealed a new Word document template I haven't noticed before.

Shown above: Flow chart for today's Emotet malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domains:
- hxxp[:]//www.forma-31[.]ru/De/KVHFNE8175184/Bestellungen/Fakturierung/
- hxxp[:]//www.animoderne[.]com/kcrod7Kciuarbik_lZO
- hxxp[:]//www.animoderne[.]com/kcrod7Kciuarbik_lZO/
- hxxp[:]//ftp.spbv[.]org/yV6CuadvZ3v7G_60Tk
- hxxp[:]//ftp.spbv[.]org/yV6CuadvZ3v7G_60Tk/
- hxxp[:]//wijdoenbeter[.]be/kZ1ywr7u_rQL
- hxxp[:]//animoderne[.]com/6H7bU7fDVegZsDf_jmA
- hxxp[:]//animoderne[.]com/6H7bU7fDVegZsDf_jmA/
- hxxp[:]//realgen-marketing[.]nl/06yF2OmyV8
- hxxp[:]//realgen-marketing[.]nl/06yF2OmyV8/
- rent.golfcarexport[.]com
- sale.mandinipearls[.]com
- fri33-ay[.]com
- getlo801c[.]com
DOWNLOADED WORD DOC
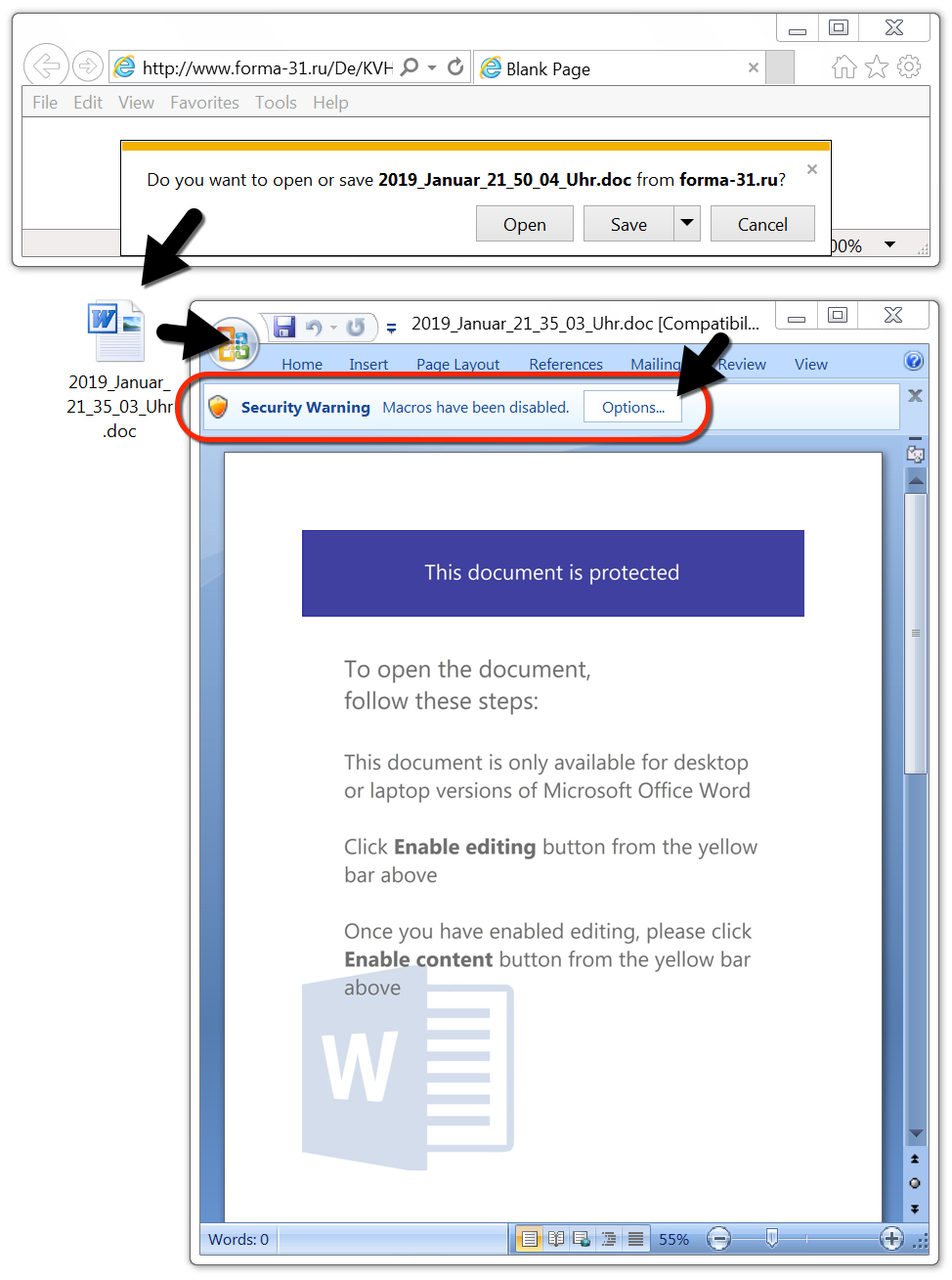
Shown above: Downloaded Word doc with macro for Emotet
TRAFFIC
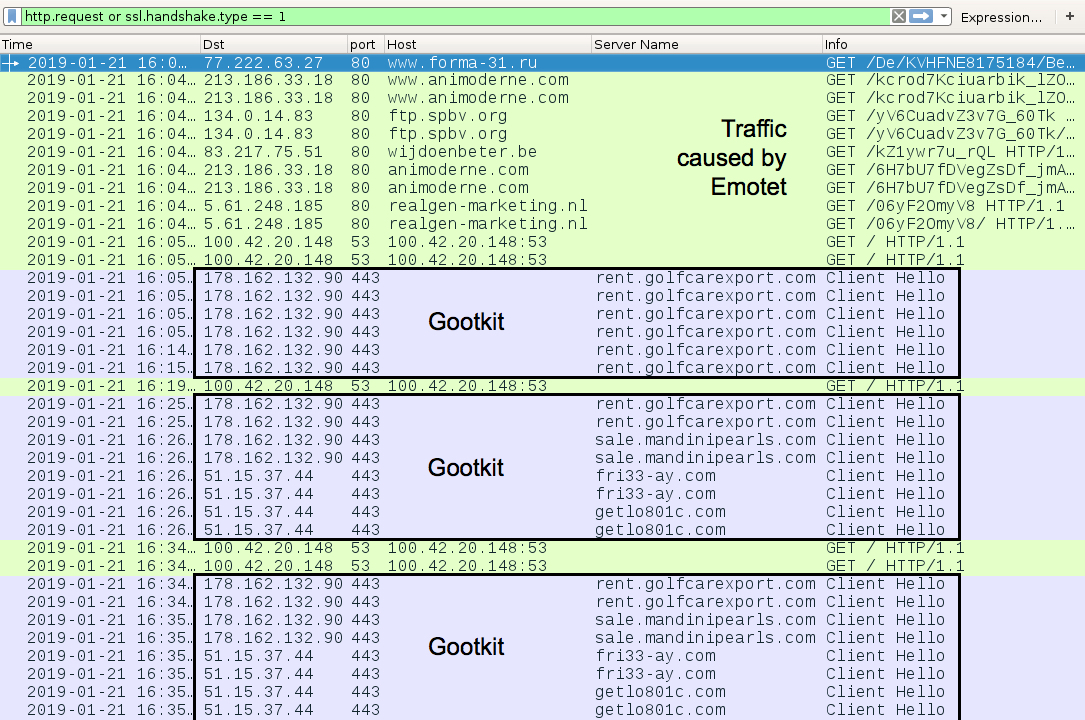
Shown above: Traffic from an infection filtered in Wireshark.
DOWNLOAD OF INITIAL WORD DOCUMENT:
- 77.222.63[.]27 port 80 - www.forma-31[.]ru - GET /De/KVHFNE8175184/Bestellungen/Fakturierung/
TRAFFIC TO RETREIVE EMOTET EXE CAUSED BY WORD MACRO:
- 213.186.33[.]18 port 80 - www.animoderne[.]com - GET /kcrod7Kciuarbik_lZO (301 Moved Permanently)
- 213.186.33[.]18 port 80 - www.animoderne[.]com - GET /kcrod7Kciuarbik_lZO/ (200 OK, shows index of dir)
- 134.0.14[.]83 port 80 - ftp.spbv[.]org - GET /yV6CuadvZ3v7G_60Tk (301 Moved Permanently)
- 134.0.14[.]83 port 80 - ftp.spbv[.]org - GET /yV6CuadvZ3v7G_60Tk/ (403 Forbidden)
- 83.217.75[.]51 port 80 - wijdoenbeter[.]be - GET /kZ1ywr7u_rQL (200 OK, but no content returned)
- 213.186.33[.]18 port 80 - animoderne[.]com - GET /6H7bU7fDVegZsDf_jmA (301 Moved Permanently)
- 213.186.33[.]18 port 80 - animoderne[.]com - GET /6H7bU7fDVegZsDf_jmA/ (200 OK, shows index of dir)
- 5.61.248[.]185 port 80 - realgen-marketing[.]nl - GET /06yF2OmyV8 (301 Moved Permanently)
- 5.61.248[.]185 port 80 - realgen-marketing[.]nl - GET /06yF2OmyV8/ (200 OK, returned Emotet EXE)
EMOTET POST-INFECTION TRAFFIC:
- 182.176.106[.]43 port 995 - attempted TCP connections, but no response from server
- 100.42.20[.]148 port 53 - 100.42.20[.]148:53 - GET / (multiple requests, encoded traffic, included Gootkit EXE)
GOOTKIT POST-INFECTION TRAFFIC:
- 178.162[.]132.90 port 443 - rent.golfcarexport[.]com - HTTPS traffic caused by Gootkit
- 178.162[.]132.90 port 443 - sale.mandinipearls[.]com - HTTPS traffic caused by Gootkit
- 51.15.37[.]44 port 443 - fri33-ay[.]com - HTTPS traffic caused by Gootkit
- 51.15.37[.]44 port 443 - getlo801c[.]com - HTTPS traffic caused by Gootkit
MALWARE
INITIAL WORD DOC:
- SHA256 hash: 1a73585dc90551822b772e3bab61a856a3ed8377b2e71326ce1b946a43cfa1f2
- File size: 265,289 bytes
- File location: hxxp[:]//www.forma-31[.]ru/De/KVHFNE8175184/Bestellungen/Fakturierung/
- Downloadedile name: 2019_Januar_21_50_04_Uhr.doc (different file names)
- File description: Downloaded Word doc with macro for Emotet
EMOTET BINARIES:
- SHA256 hash: 98e832e8d670daed18a0449113b7ae909cfce32c49f6a2a048893c95cad2bbe8
- File size: 159,744 bytes
- File location: hxxp[:]//realgen-marketing[.]nl/06yF2OmyV8/
- File location: C:\Users\[username]\AppData\Local\[random name]\[same as directory name].exe
- File description: Emotet binary retrieved by Word macro
- SHA256 hash: 52c84e9f8be452405bdc6dac12518a04509e8d34d16633e11f707f493ed4f9a7
- File size: 299,520 bytes
- File location: C:\ProgramData\[random characters].exe
- File description: Gootkit executable retrieved by Emotet-infected host
Click here to return to the main page.
