2019-01-22 - HANCITOR MALSPAM WITH FEDEX THEME
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Email examples: 2019-01-22-Hancitor-malspam-10-email-examples.txt.zip 4.2 kB (4,178 bytes)
- 2019-01-22-Hancitor-malspam-10-email-examples.txt (97,493 bytes)
- Traffic: 2019-01-22-Hancitor-infection-with-Ursnif.pcap.zip 740 kB (740,179 bytes)
- 2019-01-22-Hancitor-infection-with-Ursnif.pcap (1,012,759 bytes)
- Malware: 2019-01-22-malware-from-Hancitor-infected-host.zip 457 kB (456,664 bytes)
- 2019-01-22-downloaded-Excel-spreadsheet-with-macro-for-Hancitor.xls (468,992 bytes)
- 2019-01-22-Hancitor-dropped-by-Excel-macro.exe (77,312 bytes)
- 2019-01-22-Ursnif-retreived-by-Hancitor-infected-host.exe (153,600 bytes)
NOTES:
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
- More indicators by @James_inthe_box from today's Hancitor posted at this Pastebin link.
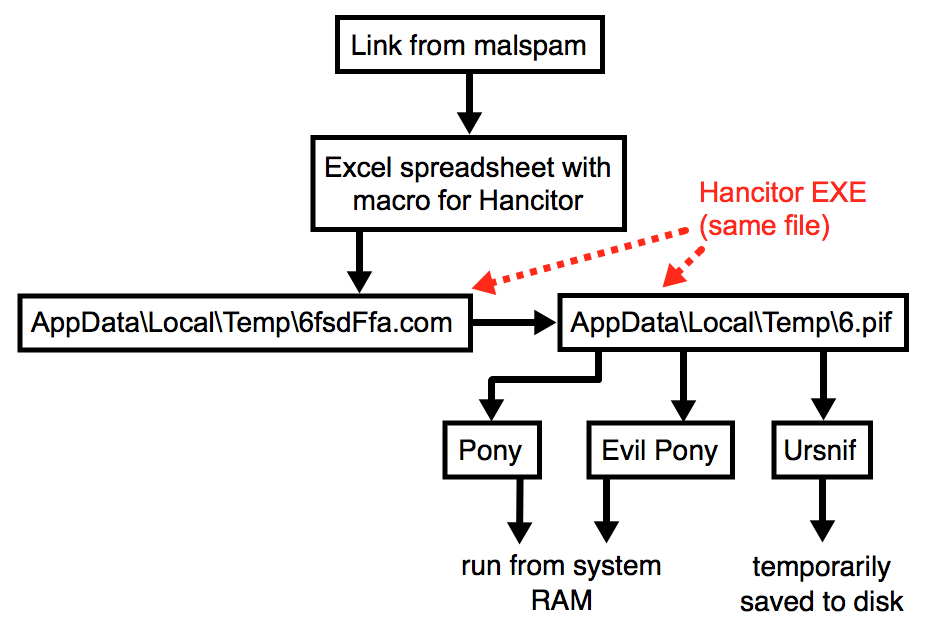
Shown above: Flow chart for recent Hancitor malspam infections.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- fishfinderland[.]com
- gunnegotiator[.]com
- gunnegotiator[.]net
- sjkfishfinders[.]com
- sjkboating[.]com
- sjkfishfinders[.]com
- sjkpools[.]com
- sjkswimming[.]com
- hxxp[:]//rushnewmedia[.]de/wp/wp-content/plugins/really-simple-captcha/1
- hxxp[:]//rushnewmedia[.]de/wp/wp-content/plugins/really-simple-captcha/2
- hxxp[:]//rushnewmedia[.]de/wp/wp-content/plugins/really-simple-captcha/3
- felighevengna[.]com
- g2.ex100p[.]at
- in.termas[.]at
MALSPAM DATA

Shown above: Screenshot from one of the emails.
DATA FROM 10 EMAIL EXAMPLES:
- Date: Tue, 22 Jan 2019 as early as 16:56 UTC through at least 19:59 UTC
- From: "FedEx" <fedex@jackphelan[.]com>
- From: "FedEx Inc." <fedex@jackphelan[.]com>
- Subject: FedEx Tracking
- Subject: Here is Your FedEx Tracking
- Subject: Here is Your FedEx Tracking Number
- Received: from jackphelan[.]com ([12.133.172[.]202])
- Received: from jackphelan[.]com ([12.220.54[.]114])
- Received: from jackphelan[.]com ([50.247.161[.]198])
- Received: from jackphelan[.]com ([65.5.84[.]226])
- Received: from jackphelan[.]com ([72.255.81[.]102])
- Received: from jackphelan[.]com ([74.129.110[.]170])
- Received: from jackphelan[.]com ([80.44.89[.]111])
- Received: from jackphelan[.]com ([97.105.164[.]46])
- Received: from jackphelan[.]com ([207.162.190[.]6])
- Received: from jackphelan[.]com ([207.162.190[.]11])
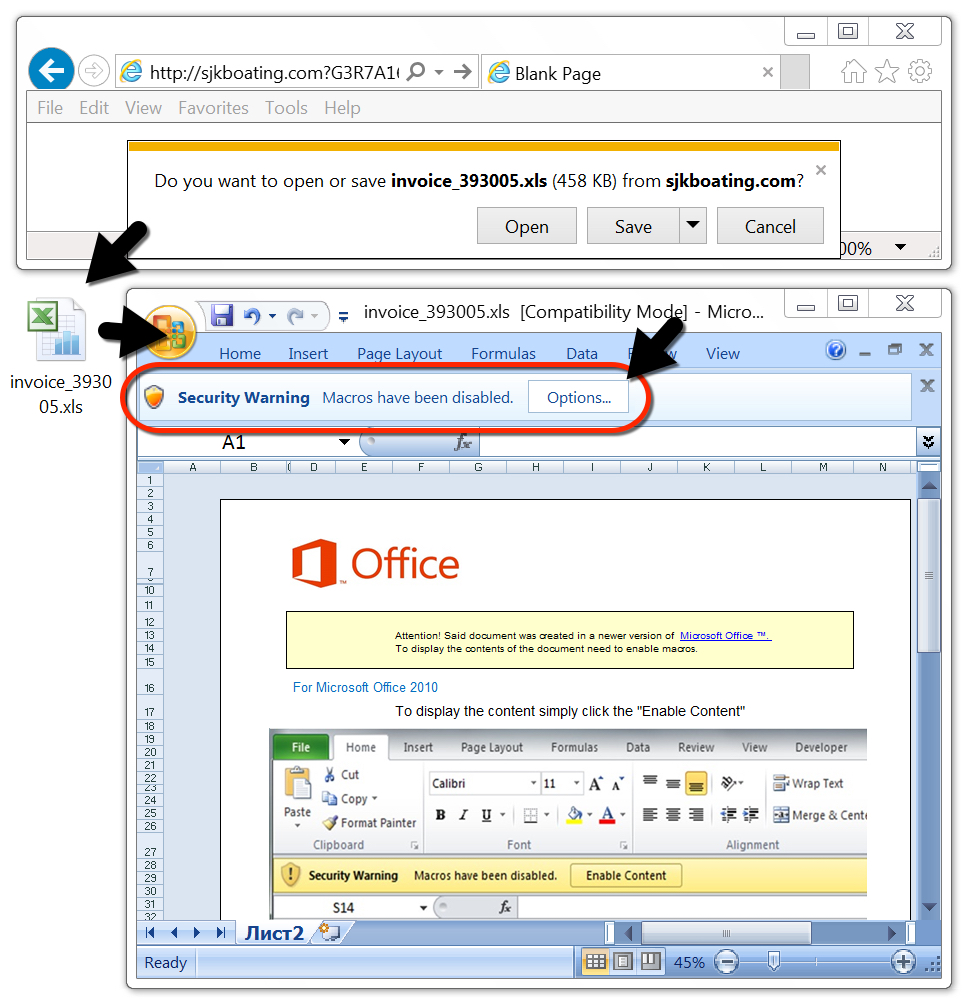
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
LINKS IN THE EMAILS TO DOWNLOAD THE WORD DOCUMENT:
- hxxp[:]//fishfinderland[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//gunnegotiator[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//gunnegotiator[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//sjkfishfinders[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//sjkboating[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//sjkfishfinders[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//sjkpools[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//sjkswimming[.]com?[string of characters]=[encoded string representing recipient's email address]
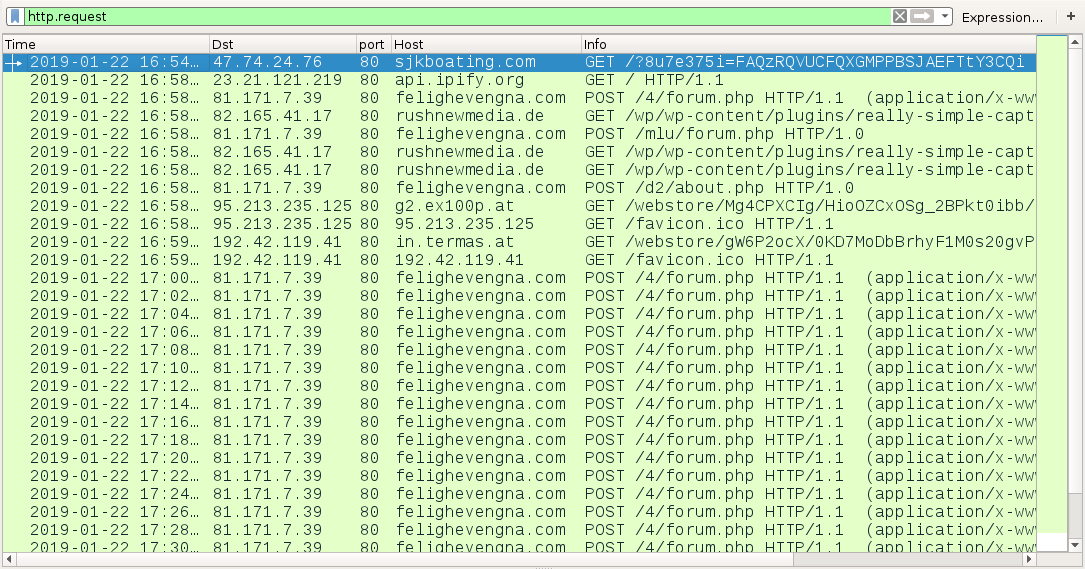
Shown above: HTTP traffic from today's infection filtered in Wireshark.
INITIAL HANCITOR INFECTION TRAFFIC:
- 47.74.24[.]76 port 80 - sjkboating[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 81.171.7[.]39 port 80 - felighevengna[.]com - POST /4/forum.php
- 81.171.7[.]39 port 80 - felighevengna[.]com - POST /mlu/about.php
- 81.171.7[.]39 port 80 - felighevengna[.]com - POST /d2/about.php
- 82.165.41[.]17 port 80 - rushnewmedia[.]de - GET /wp/wp-content/plugins/really-simple-captcha/1
- 82.165.41[.]17 port 80 - rushnewmedia[.]de - GET /wp/wp-content/plugins/really-simple-captcha/2
- 82.165.41[.]17 port 80 - rushnewmedia[.]de - GET /wp/wp-content/plugins/really-simple-captcha/3
URSNIF POST-INFECTION HTTP TRAFFIC:
- 195.213.235[.]125 port 80 - g2.ex100p[.]at - GET /webstore/[long string of characters]
- 192.42.119[.]41 port 80 - in.termas[.]at - GET /webstore/[long string of characters]
URSNIF POST-INFECTION DNS TRAFFIC:
- 192.71.245[.]208 port 53 (UDP) - DNS query for: g2.ex100p[.]at
- 192.71.245[.]208 port 53 (UDP) - DNS query for: beetfeetlife[.]bit
- 192.71.245[.]208 port 53 (UDP) - DNS query for: in.termas[.]at
FILE HASHES
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: 76b96c8d796cfcebff34d42e65e5a4ab2770fda42ea3c259097ee068660dfcc2
File size: 468,992 bytes
File name: invoice_392690.xls (random numbers in the file name)
File description: Excel spreadsheet downloaded from link in Hancitor malspam. Has macro to cause Hancitor infection.
- SHA256 hash: d16f1d82ace24ed81113f0ef315e96a2e4d8a28f848e33f59907078b9dd670a9
File size: 77,312 bytes
File location: C:\Users\[username]\AppData\Local\Temp\6fsdFfa.com
File location: C:\Users\[username]\AppData\Local\Temp\6.pif
File description: Hancitor malware EXE seen after enabling macro from downloaded Excel spreadsheet
- SHA256 hash: 4ef443dc917de8b83f54787d666f46aac66defd75d03446678e0900b214e5d2d
File size: 153,600 bytes
File location: C:\Users\[username]AppData\Local\Temp\BN7C9E.tmp (random hex characters in file name)
File description: Ursnif EXE on 2019-01-22 retreived by Hancitor-infected host
Click here to return to the main page.
