2019-02-15 - QUICK POST: EMOTET TO ICEDID (BOKBOT) TO TRICKBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- For more info, see the Crowdstrike blog post "Sin"-ful Spiders: WIZARD SPIDER and LUNAR SPIDER Sharing the Same Web
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2019-02-15-Emotet-with-IcedID-and-Trickbot.pcap.zip 22.4 MB (22,448,797 bytes)
- 2019-02-15-Emotet-with-IcedID-and-Trickbot.pcap (27,251,365 bytes)
- client/ACC2045411553.doc
- client/ProgramData/c1olrQJ4.exe
- client/ProgramData/NvMD2NMs.exe
- client/ProgramData/w32QV85W.exe
- client/ProgramData/{F06B2E6C-756C-4579-A43A-A73C778244DD}/jnpdkdkdx.exe
- client/registry-entries-for-Emotet-and-Trickbot.txt
- client/sched-task-for-IcedID.xml.txt
- client/Users/theo.loveless/AppData/Local/eapwgx/eapwgx.exe
- client/Users/theo.loveless/AppData/Roaming/44783m8uh77g8l8_nkubyhu5vfxxbh878xo6hlttkppzf28tsdu5kwppk_11c1jl.exe
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/55893n9uh88g9m9_olubyhu6vfxxbh989xp7hmttlqqzf29ttdu6lwqql_11c1km.exe
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/importDll64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/injectDll64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/injectDll64_configs/dinj
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/injectDll64_configs/dpost
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/injectDll64_configs/sinj
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/networkDll64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/networkDll64_configs/dpost
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/psfin64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/psfin64_configs/dpost
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/pwgrab64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/pwgrab64_configs/dpost
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/sharesinDll64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/systeminfo64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/tabtinDll64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/tabtinDll64_configs/dpost
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/Data/wormwinDll64
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/settings.ini
- client/Users/theo.loveless/AppData/Roaming/SysDefrag/tetuq.exe
- client/Windows/44783m8uh77g8l8_nkubyhu5vfxxbh878xo6hlttkppzf28tsdu5kwppk_11c1jl.exe
- client/Windows/lgwgf4lrucfcaa_vo6bqb08eo1nja1f4d_h2dnradrkw11hvguuphvk__7sg7rwb.exe
- client/Windows/System32/setup.exe
- server/DefragWinSysTask.xml.txt
- server/Users/Administrator/AppData/Roaming/44783m8uh77g8l8_nkubyhu5vfxxbh878xo6hlttkppzf28tsdu5kwppk_11c1jl.exe
- server/Users/Administrator/AppData/Roaming/Data/
- server/Users/Default/AppData/Roaming/44783m8uh77g8l8_nkubyhu5vfxxbh878xo6hlttkppzf28tsdu5kwppk_11c1jl.exe
- server/Users/Default/AppData/Roaming/SysDefrag/55893n9uh88g9m9_olubyhu6vfxxbh989xp7hmttlqqzf29ttdu6lwqql_11c1km.exe
- server/Users/Default/AppData/Roaming/SysDefrag/Data/importDll64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/injectDll64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/injectDll64_configs/dinj
- server/Users/Default/AppData/Roaming/SysDefrag/Data/injectDll64_configs/dpost
- server/Users/Default/AppData/Roaming/SysDefrag/Data/injectDll64_configs/sinj
- server/Users/Default/AppData/Roaming/SysDefrag/Data/networkDll64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/networkDll64_configs/dpost
- server/Users/Default/AppData/Roaming/SysDefrag/Data/psfin64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/psfin64_configs/dpost
- server/Users/Default/AppData/Roaming/SysDefrag/Data/pwgrab64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/pwgrab64_configs/dpost
- server/Users/Default/AppData/Roaming/SysDefrag/Data/sharesinDll64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/systeminfo64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/tabtinDll64
- server/Users/Default/AppData/Roaming/SysDefrag/Data/tabtinDll64_configs/dpost
- server/Users/Default/AppData/Roaming/SysDefrag/Data/wormwinDll64
- server/Users/Default/AppData/Roaming/SysDefrag/settings.ini
- server/Users/Default/AppData/Roaming/SysDefrag/tetuq.exe
- server/Windows/44783m8uh77g8l8_nkubyhu5vfxxbh878xo6hlttkppzf28tsdu5kwppk_11c1jl.exe
- server/Windows/lgwgf4lrucfcaa_vo6bqb08eo1nja1f4d_h2dnradrkw11hvguuphvk__7sg7rwb.exe
- server/Windows/System32/setup.exe
IMAGES
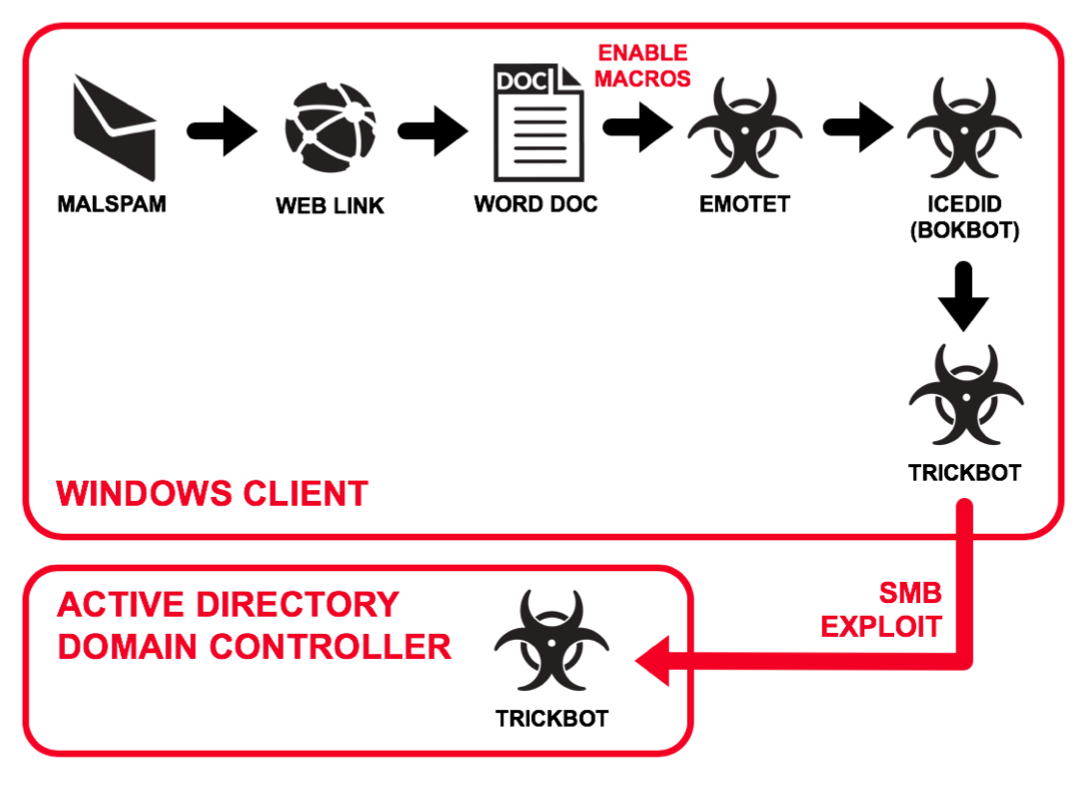
Shown above: Flow chart for today's events.
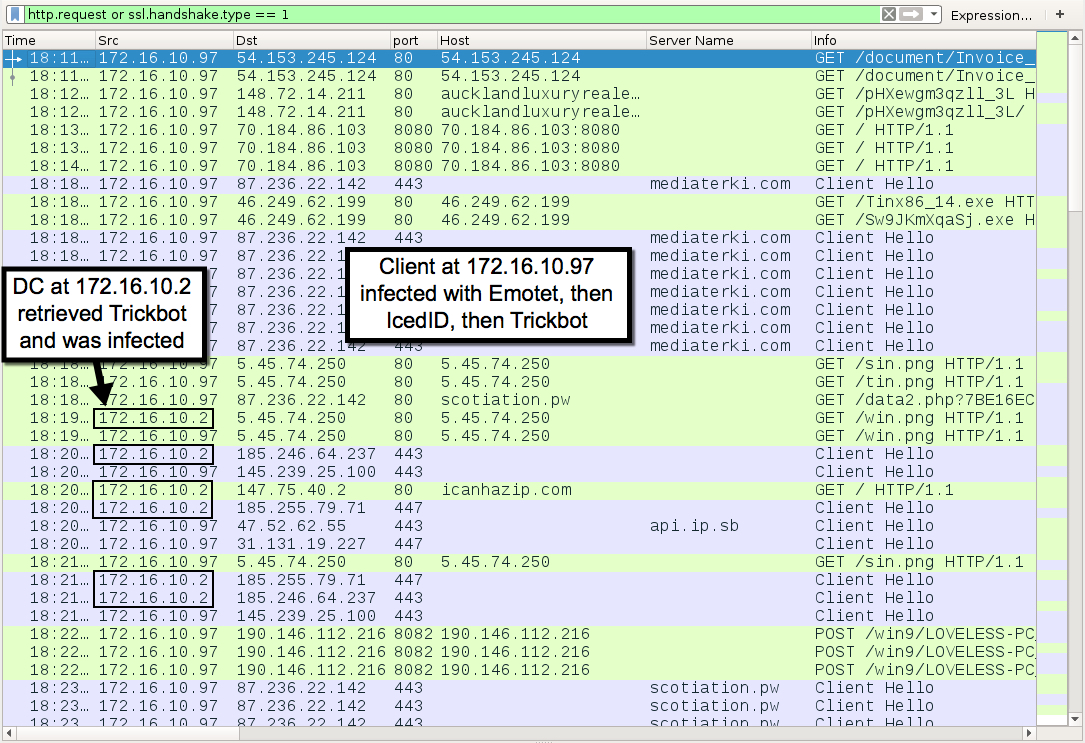
Shown above: Traffic from the infection filtered in Wireshark.
Click here to return to the main page.
