2019-02-22 - MALSPAM WITH WORD DOCS PUSHING VIDAR
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
Update: My infected Windows host showed signs of infection with Gandcrab 5.2, but this is a Vidar infection. I never found a binary for Gandcrab ransomware on my infected Windows host. See the notes section below.
ASSOCIATED FILES:
- Pcap of the infection traffic: 2019-02-22-infection-traffic-from-malspam-pushing-Vidar.pcap.zip 2.2 MB (2,242,631 bytes)
- 2019-02-22-infection-traffic-from-malspam-pushing-Vidar.pcap (4,204,649 bytes)
- Associated malware: 2019-02-22-files-from-Vidar-infection.zip 2.4 MB (2,416,289 bytes)
- malicious-word-docs/Info_Heather_Tamse.doc (70,656 bytes)
- malicious-word-docs/Info_Oleksiy_Shapovalov.doc (70,656 bytes)
- malicious-word-docs/Info_Sharon_Gough.doc (70,144 bytes)
- malicious-word-docs/Info_Tran_Nguyen.doc (70,656 bytes)
- malicious-word-docs/Info_Troy_Yochelson.doc (69,632 bytes)
- malicious-word-docs/Inquiry_Brian_Roberts.doc (69,120 bytes)
- malicious-word-docs/Report_Gould,_Carolyn.doc (70,656 bytes)
- malicious-word-docs/Report_Michael_Kaba.doc (70,144 bytes)
- malicious-word-docs/Request_Beatriz_Márquez.doc (70,144 bytes)
- malicious-word-docs/Request_Stinson,_Lisa.doc (69,632 bytes)
- malware-and-artifacts/2019-02-22-c2.bin.txt (409 bytes)
- malware-and-artifacts/2019-02-22-Gandcrab-ransomware-decyrption-instructions.txt (2,954 bytes)
- malware-and-artifacts/2019-02-22-script-from-Pastebin.txt (233,220 bytes)
- malware-and-artifacts/2019-02-22-v2.bin.exe (1,159,168 bytes)
- not-inherently-malicious/2019-02-22-freebl3.dll (334,288 bytes)
- not-inherently-malicious/2019-02-22-mozglue.dll (137,168 bytes)
- not-inherently-malicious/2019-02-22-msvcp140.dll (440,120 bytes)
- not-inherently-malicious/2019-02-22-nss3.dll (1,246,160 bytes)
- not-inherently-malicious/2019-02-22-softokn3.dll (144,848 bytes)
- not-inherently-malicious/2019-02-22-vcruntime140.dll (83,784 bytes)
NOTES:
- I can only confirm these Word documents were attachments from malspam, I cannot provide any information on the actual malspam itself.
- Thanks to @JR0driguezB and @jeromesegura, who pointed out this is a Vidar infostealer (link).
- For more info, see the January 2019 Malwarebytes blog: Vidar and GandCrab: stealer and ransomware combo observed in the wild.
- Even though my lab host was also infected with Gandcrab, I could not find a binary for the Gandcrab ransomware on the infected Windows host.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domains:
- wog92bqzqg1m9j4i3[.]website
- hxxp[:]//95.142.47[.]43/v2.bin
- hxxp[:]//95.142.47[.]43/c2.bin
- hxxp[:]//pastebin[.]com/raw/jkBxauyv
- yourseo.ac[.]ug
WORD DOCUMENT EXAMPLE
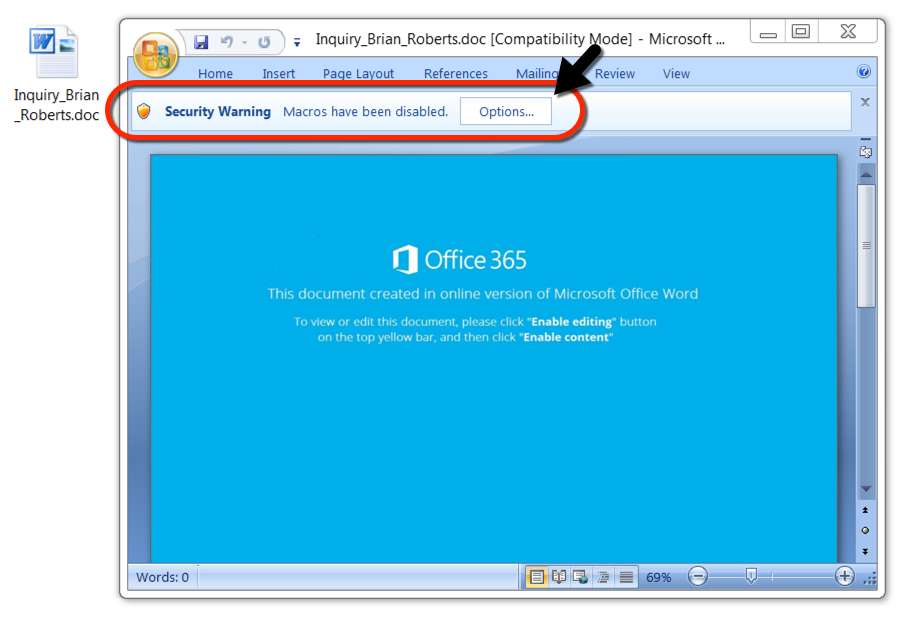
Shown above: Example of the Word docs from the malspam.
TRAFFIC
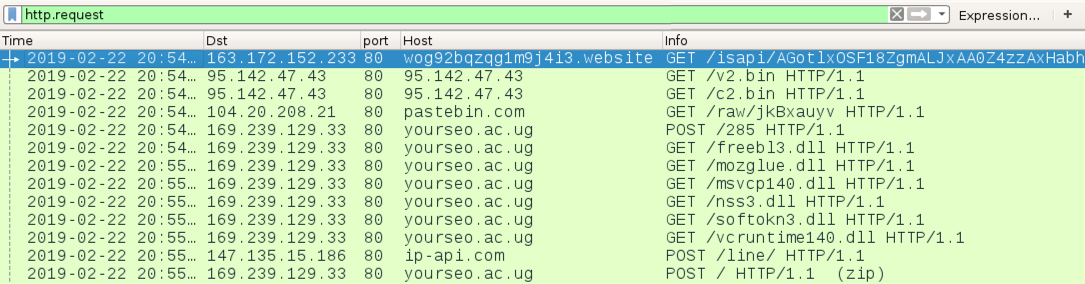
Shown above: Traffic from an infection filtered in Wireshark.
INFECTION TRAFFIC:
- 163.172.152[.]233 port 80 - wog92bqzqg1m9j4i3[.]website - GET /isapi/[long string of characters]
- 95.142.47[.]43 port 80 - 95.142.47[.]43 - GET /v2.bin
- 95.142.47[.]43 port 80 - 95.142.47[.]43 - GET /c2.bin
- port 80 port - pastebin.com - GET /raw/jkBxauyv
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - POST /285
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - GET /freebl3.dll
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - GET /mozglue.dll
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - GET /msvcp140.dll
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - GET /nss3.dll
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - GET /softokn3.dll
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - GET /vcruntime140.dll
- port 80 - ip-api.com - POST /line/
- 169.239.129[.]33 port 80 - yourseo.ac[.]ug - POST /
MALWARE
INITIAL WORD DOCS (SHA256 HASH - SIZE - FILE NAME):
- 2d6a7cc9a14b7d9764bd481abc84a06739e94a9bef7a84c6a30b0c5b65cdf463 - 70,656 bytes - Info_Heather_Tamse.doc
- e54dd6213683d48db6b86af92636817106138bc49f8cb6bebe39926ccb4f0af7 - 70,656 bytes - Info_Oleksiy_Shapovalov.doc
- 01e7207e732e67fb3280597ea39bb8ca59fba7bdede1bb4d509e0947d69a5e0a - 70,144 bytes - Info_Sharon_Gough.doc
- 19554594d13500ff0c0f5d73d07fa4ec0bf44ca2b3b2581be470cdd02919a7d0 - 70,656 bytes - Info_Tran_Nguyen.doc
- ea52d89e63297de4bfbe6bae72e3c928dfdacde64b5585c797d08dc6595c9557 - 69,632 bytes - Info_Troy_Yochelson.doc
- 1790952c31d0f142519e8d5762bd441be97cb050b353ecdc91b19a8b44ea59d5 - 69,120 bytes - Inquiry_Brian_Roberts.doc
- 58449c472d5841504af747b8558245b3416c01faae9843f8dd395000a9a6e704 - 70,656 bytes - Report_Gould,_Carolyn.doc
- 51f670520fe4b7f5d827e2f1798c45439d35fed19e9aca6ed0a21acb93527f00 - 70,144 bytes - Report_Michael_Kaba.doc
- 204d34b2c3271db299dec30ccf0ca845dcd33558b0ee86eb956db3e2a6b4d5c2 - 70,144 bytes - Request_Beatriz_Márquez.doc
- a8fa0aa5f33508d872863684f2ddec8146b3287b0de25e24516b1d9f97e39acf - 69,632 bytes - Request_Stinson,_Lisa.doc
MALWARE BINARY:
- SHA256 hash: be176c34ee14506001aa17e6570be57c79038b23789f3d407db370ad5bc2a6c6
- File size: 1,159,168 bytes
- File location: hxxp[:]//95.142.47[.]43/v2.bin
- File location: C:\Users\[username]\AppData\Roaming\1u2.exe
- File description: Vidar malware EXE retrieved by Word macro
NON-MALICIOUS DLL FILES RETRIEVED FROM YOURSEO.AC[.]UG DURING THE INFECTION:
- a770ecba3b08bbabd0a567fc978e50615f8b346709f8eb3cfacf3faab24090ba - freebl3.dll
- 3fe6b1c54b8cf28f571e0c5d6636b4069a8ab00b4f11dd842cfec00691d0c9cd - mozglue.dll
- 334e69ac9367f708ce601a6f490ff227d6c20636da5222f148b25831d22e13d4 - msvcp140.dll
- e2935b5b28550d47dc971f456d6961f20d1633b4892998750140e0eaa9ae9d78 - nss3.dll
- 43536adef2ddcc811c28d35fa6ce3031029a2424ad393989db36169ff2995083 - softokn3.dll
- c40bb03199a2054dabfc7a8e01d6098e91de7193619effbd0f142a7bf031c14d - vcruntime140.dll
IMAGES
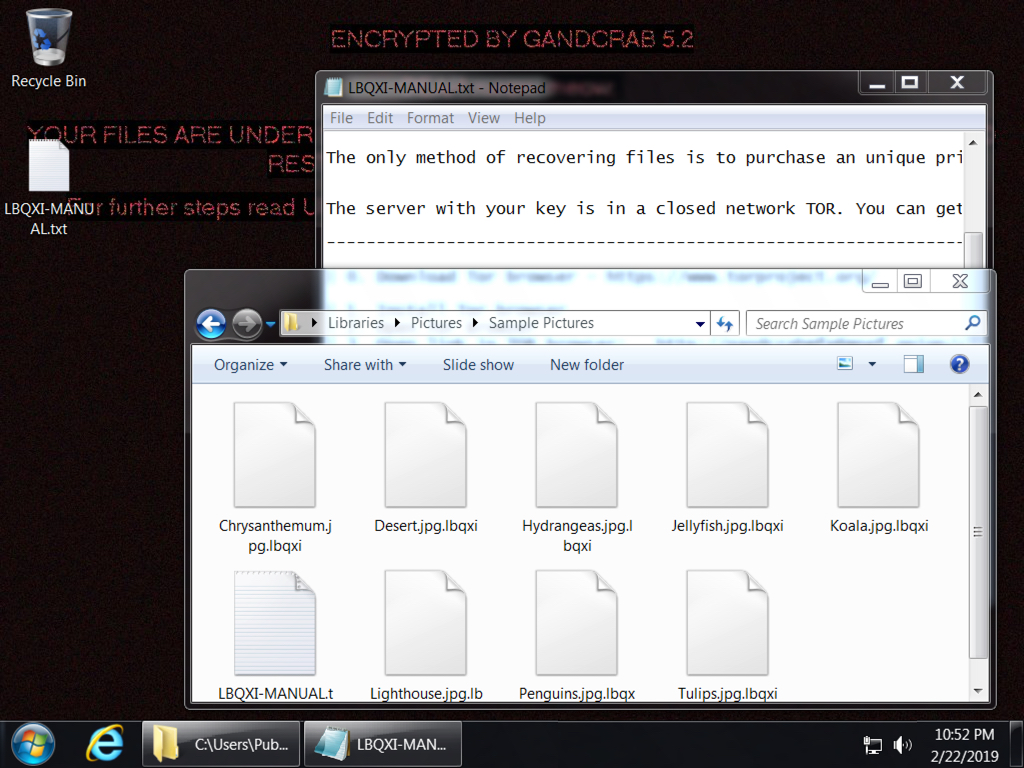
Shown above: Desktop of an infected Windows host shows a Gandcrab ransomware infection, but I didn't find a Gandrab binary on the infected host.
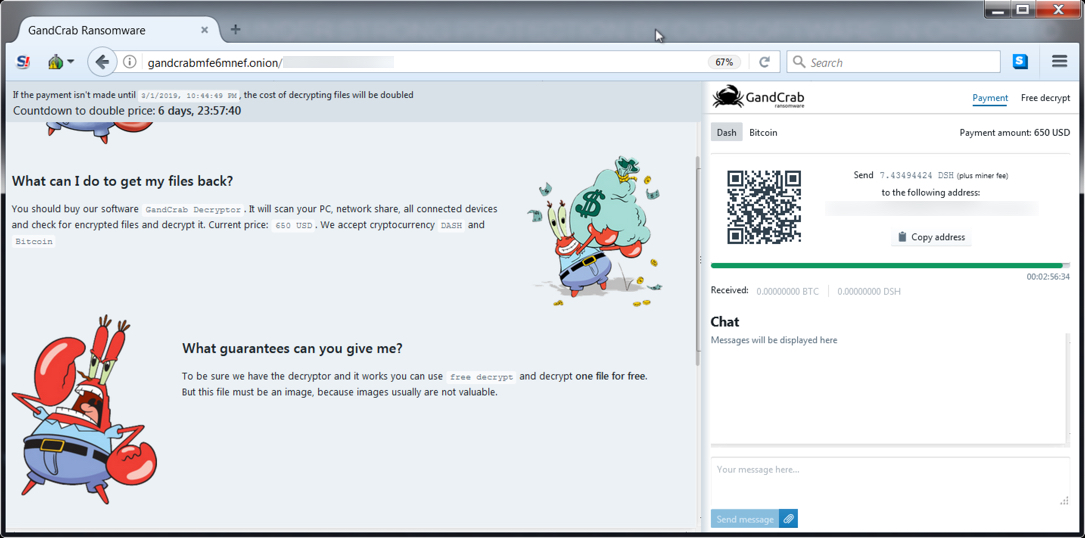
Shown above: Gandcrab ransomware decryption instructions.
Click here to return to the main page.
